Powerpoint Templates and Google slides for Computer Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incidents Follow Up Report Deploying Computer Security Incident Management
Cyber Security Incidents Follow Up Report Deploying Computer Security Incident ManagementThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer.Present the topic in a bit more detail with this Cyber Security Incidents Follow Up Report Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Confidential Information, Training Employees, Organizational Projects. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management
Cyber Security Threats Detection Techniques Deploying Computer Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc.Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Threat Intelligence, Access Regularly, Undercovers Intruders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
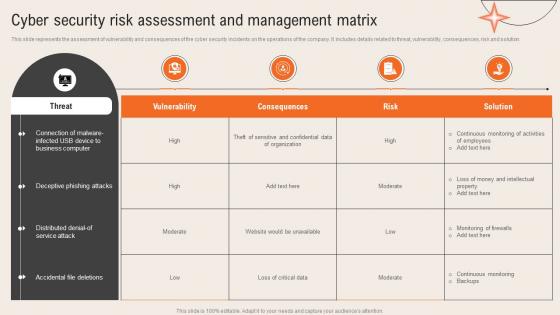 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management
Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc.Introducing Five Phases Of Cybersecurity Incident Management Deploying Computer Security Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sharing Information, Establish Policies, Response Process, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management
Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc.Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Deploying Computer Security Incident Management. This template helps you present information on five stages. You can also present information on Increased Costs, Operational Disruption, Reputational Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security Incident
Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security IncidentThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc.Introducing Key Parameters To Select Cyber Security Containment Strategy Deploying Computer Security Incident to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Potential Damages, Organizational Resources, Containment Strategy, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Deploying Computer Security Incident Management
Table Of Contents For Deploying Computer Security Incident ManagementPresent the topic in a bit more detail with this Table Of Contents For Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Key Issues Faced, Cyber Security Incident, Incident Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Cyber Security Incidents Detected By It Department Deploying Computer Security
Various Cyber Security Incidents Detected By It Department Deploying Computer SecurityThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc.Introducing Various Cyber Security Incidents Detected By It Department Deploying Computer Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Current Financial, Sabotage Incidents, Technique Legitimate, using this template. Grab it now to reap its full benefits.
-
 Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management
Ways To Detect Cyber Security Incidents Deploying Computer Security Incident ManagementThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc.Increase audience engagement and knowledge by dispensing information using Ways To Detect Cyber Security Incidents Deploying Computer Security Incident Management. This template helps you present information on four stages. You can also present information on Unusual Behavior, Privileged Accounts, Anomalies Outbound using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer Crime Security Survey In Powerpoint And Google Slides Cpb
Computer Crime Security Survey In Powerpoint And Google Slides CpbPresenting our Computer Crime Security Survey In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Computer Crime Security Survey This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Icon Showcasing Application Of Computer Vision In Digital Security
Icon Showcasing Application Of Computer Vision In Digital SecurityIntroducing our Icon Showcasing Application Of Computer Vision In Digital Security set of slides. The topics discussed in these slides are Application, Digital Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Computing Infrastructure Security Icon
Cloud Computing Infrastructure Security IconIntroducing Cloud Computing Infrastructure Security Icon to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Computing, Infrastructure, Security Icon, using this template. Grab it now to reap its full benefits.
-
 SDN Security IT Role Of SDN In Edge Computing IOT And Remote Access
SDN Security IT Role Of SDN In Edge Computing IOT And Remote AccessThis slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Introducing SDN Security IT Role Of SDN In Edge Computing IOT And Remote Access to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Role, Computing, Remote, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Deploying Computer Security
Cyber Security Incident Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident.Introducing Cyber Security Incident Deploying Computer Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Organizations Functioning, Stakeholders Responsible, Breach Awareness, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Deploying Computer Security
Cyber Security Incident Management Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Deploying Computer Security. This template helps you present information on one stage. You can also present information on Prepare Cyber, Documented Procedures, Quantify Financial using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Deploying Computer Security
Cyber Security Incident Management Team Deploying Computer SecurityThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc.Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Deploying Computer Security. Dispense information and present a thorough explanation of Communication Skills, Crisis Management, Network Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Issues Faced By Organization Deploying Computer Security
Key Issues Faced By Organization Deploying Computer SecurityThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc.Introducing Key Issues Faced By Organization Deploying Computer Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Information, Holding Sensitive, Ransomware Attacks, using this template. Grab it now to reap its full benefits.
-
 Computer Security Incident Response Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Incident Response Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Computer security incident response colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Computer Security Incident Response Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Incident Response Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Computer security incident response monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Unauthorized Computer Access Icon Causing Cyber Security Threat
Unauthorized Computer Access Icon Causing Cyber Security ThreatPresenting our set of slides with Unauthorized Computer Access Icon Causing Cyber Security Threat. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized, Computer Access.
-
 Best Computer Security System In Powerpoint And Google Slides Cpb
Best Computer Security System In Powerpoint And Google Slides CpbPresenting our Best Computer Security System In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Best Computer Security System. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Introduction To Grid Computing Security Model Grid Computing Services
Introduction To Grid Computing Security Model Grid Computing ServicesThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Introduction To Grid Computing Security Model Grid Computing Services. Dispense information and present a thorough explanation of Authentication, Delegation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Grid Computing Services Key Components Of Grid Computing Security
Grid Computing Services Key Components Of Grid Computing SecurityThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Present the topic in a bit more detail with this Grid Computing Services Key Components Of Grid Computing Security. Use it as a tool for discussion and navigation on Security, Scheduler, Data Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Cybersecurity And Cloud Computing Security
Comparative Analysis Of Cybersecurity And Cloud Computing SecurityThe purpose of the slide is to showcase the significant differences between cyber security and cloud security. It provides a comparative matrix with differentiating aspects like definition, maintenance of personal information security, liability of security breach, access to data and security threat detection. Presenting our well structured Comparative Analysis Of Cybersecurity And Cloud Computing Security. The topics discussed in this slide are Aspects, Cloud Security, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security And Cloud Computing Icon
Cyber Security And Cloud Computing IconPresenting our set of slides with Cyber Security And Cloud Computing Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Cloud Computing, Icon.
-
 Cyber Security Threats To Cloud Computing
Cyber Security Threats To Cloud ComputingThe slide showcases major cybersecurity risks that impact cloud computing services. it covers crypto jacking, data breaches, insider threats, hijacking accounts and inadequate training. Introducing our premium set of slides with Cyber Security Threats To Cloud Computing. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Crypto Jacking, Hijacking Accounts, Insecure Applications, Data Breaches. So download instantly and tailor it with your information.
-
 Icon For Cloud Computing Cyber Security Services For Smes
Icon For Cloud Computing Cyber Security Services For SmesPresenting our set of slides with Icon For Cloud Computing Cyber Security Services For Smes. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Cloud Computing, Cyber Security, Services For Smes.
-
 Key Benefits Of Cognitive Computing Cyber Security
Key Benefits Of Cognitive Computing Cyber SecurityThe purpose of the slide is to show major advantages associated with adopting a cognitive cyber security like fast detection, enhanced incident response and security automation. Introducing our premium set of slides with Key Benefits Of Cognitive Computing Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Fast Detection, Enhanced Incident Response, Security Automation. So download instantly and tailor it with your information.
-
 Ways Cloud Computing Strengthening Industrial Cyber Security And Productivity
Ways Cloud Computing Strengthening Industrial Cyber Security And ProductivityThe slide showcases the benefits associated with cloud computing at global industrial level. it shows how cloud computing is enhancing global industries productivity and cyber security and dealing with financial barriers. Introducing our premium set of slides with Ways Cloud Computing Strengthening Industrial Cyber Security And Productivity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Computing, Booting Industrial Production, Cloud Computing Industrial, Cyber Security. So download instantly and tailor it with your information.
-
 F1470 Key Components Of Grid Computing Security Grid Computing Types
F1470 Key Components Of Grid Computing Security Grid Computing TypesThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Introducing F1470 Key Components Of Grid Computing Security Grid Computing Types to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Management, Workload And Resource Management, Scheduler, using this template. Grab it now to reap its full benefits.
-
 Introduction To Grid Computing Security Model Grid Computing Types
Introduction To Grid Computing Security Model Grid Computing TypesThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Introduction To Grid Computing Security Model Grid Computing Types. Dispense information and present a thorough explanation of Intrusion Detection, Policy Management, User Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security Architecture Icon
Cloud Computing Security Architecture IconPresenting our set of slides with Cloud Computing Security Architecture Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Computing, Security Architecture Icon
-
 Security Management Computer Network In Powerpoint And Google Slides Cpb
Security Management Computer Network In Powerpoint And Google Slides CpbPresenting Security Management Computer Network In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Management Computer Network. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Green Cloud Computing Improving Security By Green Computing Technology
Green Cloud Computing Improving Security By Green Computing TechnologyThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Green Cloud Computing Improving Security By Green Computing Technology. Use it as a tool for discussion and navigation on Security, Computing, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Grid Computing Security Model Grid Computing Components
Introduction To Grid Computing Security Model Grid Computing ComponentsThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Introduction To Grid Computing Security Model Grid Computing Components. Dispense information and present a thorough explanation of Mapping Rules, Service Or Endpoint Policy, Policy Management, Key Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Components Of Grid Computing Security Grid Computing Components
Key Components Of Grid Computing Security Grid Computing ComponentsThis slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Increase audience engagement and knowledge by dispensing information using Key Components Of Grid Computing Security Grid Computing Components. This template helps you present information on five stages. You can also present information on Grid Computing, Workload, Resource Management, Data Management, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Four computers for secured network ppt slides
Four computers for secured network ppt slidesPresenting four computers for secured network ppt slides. This is a four computers for secured network ppt slides. This is a four stage process. The stages in this process are security, networking, servers.
-
 Computer with lock for total security analysis ppt slides
Computer with lock for total security analysis ppt slidesPresenting computer with lock for total security analysis ppt slides. This is a computer with lock for total security analysis ppt slides. This is a two stage process. The stages in this process are security.
-
 Global computer networking with secured firewall ppt slides
Global computer networking with secured firewall ppt slidesPresenting global computer networking with secured firewall ppt slides. This is a global computer networking with secured firewall ppt slides. This is a one stage process. The stages in this process are servers, networking.
-
 Command center computer systems security room
Command center computer systems security roomPresenting this set of slides with name - Command Center Computer Systems Security Room. This is a two stage process. The stages in this process are Command Room, Control Centre, Control Room.
-
 Information security strategy mobile computer antivirus
Information security strategy mobile computer antivirusPresenting this set of slides with name - Information Security Strategy Mobile Computer Antivirus. This is a eight stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Happiness psychology financial services pps stock computer security cpb
Happiness psychology financial services pps stock computer security cpbPresenting this set of slides with name - Happiness Psychology Financial Services Pps Stock Computer Security Cpb. This is an editable four stages graphic that deals with topics like Happiness Psychology, Financial Services, Pps Stock, Computer Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Fingerprint for computer security icon
Fingerprint for computer security iconPresenting this set of slides with name Fingerprint For Computer Security Icon. This is a one stage process. The stages in this process are Fingerprint, Security, Technology. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security incident management ppt powerpoint presentation gallery summary cpb
Computer security incident management ppt powerpoint presentation gallery summary cpbPresenting this set of slides with name Computer Security Incident Management Ppt Powerpoint Presentation Gallery Summary Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Computer Security Incident Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Web security chain and lock on computer
Web security chain and lock on computerPresenting this set of slides with name Web Security Chain And Lock On Computer. This is a one stage process. The stages in this process are Web Security, Computer, Networking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer network security solution ppt powerpoint presentation professional graphics cpb
Computer network security solution ppt powerpoint presentation professional graphics cpbPresenting this set of slides with name Computer Network Security Solution Ppt Powerpoint Presentation Professional Graphics Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Computer Network Security Solution to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Files folder of computer and lifebuoy security powerpoint templates ppt backgrounds for slides 0113
Files folder of computer and lifebuoy security powerpoint templates ppt backgrounds for slides 0113We are proud to present our files folder of computer and lifebuoy security powerpoint templates ppt backgrounds for slides 0113. Let Our Family Power Point Templates Be The Vehicle Of Your Sucessful Journey. Ride The Bus To Glory With Your Grand Ideas. Our Law Power Point Templates Are Like A Basic Christmas Tree. Decorate It With Your Beautiful Thoughts And Spread Joy And Happiness.
-
 1114 computer server with lifesaver for data security image graphics for powerpoint
1114 computer server with lifesaver for data security image graphics for powerpointWe are proud to present our 1114 computer server with lifesaver for data security image graphics for powerpoint. Display the process and concept of data security in your presentation with this exclusive image. This Powe rPoint image template contains the graphic of server and life sving ring. Use this PPT and build a stunning presentation for your viwers.
-
 Computer folder security powerpoint templates and powerpoint backgrounds 0211
Computer folder security powerpoint templates and powerpoint backgrounds 0211Microsoft PowerPoint Template and Background with yellow computer folder with shield
-
 Yellow computer folder security powerpoint templates and powerpoint backgrounds 0211
Yellow computer folder security powerpoint templates and powerpoint backgrounds 0211Microsoft PowerPoint Template and Background with yellow computer folder
-
 Secure internet access computer powerpoint templates and powerpoint backgrounds 0811
Secure internet access computer powerpoint templates and powerpoint backgrounds 0811Microsoft PowerPoint Template and Background with transparent internet browser with a large chrome key protruding out from the window
-
 Secure internet browser computer powerpoint templates and powerpoint backgrounds 0811
Secure internet browser computer powerpoint templates and powerpoint backgrounds 0811Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it
-
 Icon of virus in computer results in security failure
Icon of virus in computer results in security failurePresenting this set of slides with name Icon Of Virus In Computer Results In Security Failure. The topics discussed in these slides are Icon Virus, Computer Results, Security Failure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security compliance ppt powerpoint presentation infographics objects cpb
Computer security compliance ppt powerpoint presentation infographics objects cpbPresenting this set of slides with name Computer Security Compliance Ppt Powerpoint Presentation Infographics Objects Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Computer Security Compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Computer security compliance ppt powerpoint presentation outline show cpb
Computer security compliance ppt powerpoint presentation outline show cpbPresenting this set of slides with name Computer Security Compliance Ppt Powerpoint Presentation Outline Show Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Computer Security Compliance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Virus alert on cyber security computer system
Virus alert on cyber security computer systemPresenting this set of slides with name Virus Alert On Cyber Security Computer System. The topics discussed in these slides is Virus Alert On Cyber Security Computer System. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Virus detection on cyber security computer network
Virus detection on cyber security computer networkPresenting this set of slides with name Virus Detection On Cyber Security Computer Network. The topics discussed in these slides is Virus Detection On Cyber Security Computer Network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security value added re seller ppt powerpoint presentation file clipart cpb
Computer security value added re seller ppt powerpoint presentation file clipart cpbPresenting this set of slides with name Computer Security Value Added Re Seller Ppt Powerpoint Presentation File Clipart Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Computer Security Value Added Re Seller to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application security cloud computing ppt powerpoint presentation summary sample cpb
Application security cloud computing ppt powerpoint presentation summary sample cpbPresenting this set of slides with name Application Security Cloud Computing Ppt Powerpoint Presentation Summary Sample Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Application Security Cloud Computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





