Powerpoint Templates and Google slides for Computational
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Confidential Computing Hardware Future Of Confidential Computing Technology
Confidential Computing Hardware Future Of Confidential Computing TechnologyThis slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Future Of Confidential Computing Technology. This template helps you present information on five stages. You can also present information on Confidential Computing Technology, Demonstrate, Cloud Environment, Prerequisite For Commercial Sectors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
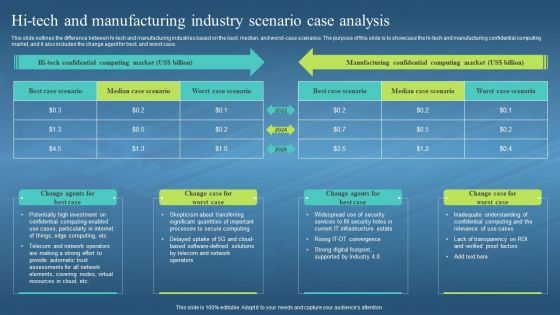 Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case Analysis
Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case AnalysisThis slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Introducing Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case Analysis to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on HI Tech And Manufacturing Industries, Worst Case Scenarios, It Infrastructure Estate, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing
Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing. This template helps you present information on four stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks, Physical Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee
Confidential Computing Hardware Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Introducing Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Inclavare, Confidential Containers, Tee Environment, Kubernetes Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB
Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCBThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB. This template helps you present information on two stages. You can also present information on Operating System, Virtual Machine Monitor, Hardware, Cloud Vendors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Introduction To Confidential Computing Technology
Confidential Computing Hardware Introduction To Confidential Computing TechnologyThis slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Present the topic in a bit more detail with this Confidential Computing Hardware Introduction To Confidential Computing Technology. Use it as a tool for discussion and navigation on Confidential Computing, Cloud Computing Method, CPU Environment While Processing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Key Features Of Confidential Computing Platform
Confidential Computing Hardware Key Features Of Confidential Computing PlatformThis slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Key Features Of Confidential Computing Platform. This template helps you present information on four stages. You can also present information on Confidential Computing Platform, Confidential Virtual Machines, Confidential Space, Confidential Google Kubernetes Engine Node using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Multi Team Construction And Cooperation In Inclavare
Confidential Computing Hardware Multi Team Construction And Cooperation In InclavareThis slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Multi Team Construction And Cooperation In Inclavare. Dispense information and present a thorough explanation of Efficient Multitasking, Multiple File System Support, Memory Safety, Cloud Container Service Team using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture
Confidential Computing Hardware Multiparty Privacy Preserving Computation ArchitectureThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Design, Multiparty Computing, Confidential Computing, Blockchain With Azure Virtual Machine, Blockchain As A Service, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Need For Confidential Computing In Cloud Environment
Confidential Computing Hardware Need For Confidential Computing In Cloud EnvironmentThis slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Need For Confidential Computing In Cloud Environment. This template helps you present information on six stages. You can also present information on Computing Memory, Competitors Or Cloud Providers, Memory Dump Attacks, Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Occlum System Architecture And Features
Confidential Computing Hardware Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Operational And Technical Assurance Of Data Privacy
Confidential Computing Hardware Operational And Technical Assurance Of Data PrivacyThis slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Present the topic in a bit more detail with this Confidential Computing Hardware Operational And Technical Assurance Of Data Privacy. Use it as a tool for discussion and navigation on Operational Assurance, Technical Assurance, Data Privacy, Integration And Continuous Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Overview Of Confidential Computing Technologies
Confidential Computing Hardware Overview Of Confidential Computing TechnologiesThis slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Overview Of Confidential Computing Technologies. This template helps you present information on six stages. You can also present information on Homomorphic Encryption, Trusted Execution Environment, Federated Learning, Synthetic Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing
Confidential Computing Hardware Primary Approaches To Obtain Confidential ComputingThis slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing. Dispense information and present a thorough explanation of Operating System, Hypervisor, Restrict Local Administrator, Cloud Administrator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications
Confidential Computing Hardware Process Of Using Intel SGX Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on SGX Based Trusted Applications, Installing The Environment, Developing, Computing And Building, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case Analysis
Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case AnalysisThis slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case Analysis. This template helps you present information on four stages. You can also present information on Restrictive Government Expenditure, Persisting Epidemic Impacts, Delayed Economic Recovery, Technologies Utilizing Public Funds using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Role Of Hardware In Confidential Computing Technology
Confidential Computing Hardware Role Of Hardware In Confidential Computing TechnologyThis slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Introducing Confidential Computing Hardware Role Of Hardware In Confidential Computing Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Environment, Service Admins And Providers, Operating System, Device Driver, Peripheral Vendors, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Shim Rune Workflow In Inclavare Containers
Confidential Computing Hardware Shim Rune Workflow In Inclavare ContainersThis slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Present the topic in a bit more detail with this Confidential Computing Hardware Shim Rune Workflow In Inclavare Containers. Use it as a tool for discussion and navigation on Shim Rune Workflow And Working, Shim Rune Components, Signature Service, Enclave Dynamic Library. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Technical Stack For Evaluating Confidential Computing
Confidential Computing Hardware Technical Stack For Evaluating Confidential ComputingThis slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Technical Stack For Evaluating Confidential Computing. Dispense information and present a thorough explanation of Application Software Vendors, Infrastructure Providers, Hardware Vendors, Cryptographic Building Blocks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Technologies Used To Protect Data In Use
Confidential Computing Hardware Technologies Used To Protect Data In UseThis slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present the topic in a bit more detail with this Confidential Computing Hardware Technologies Used To Protect Data In Use. Use it as a tool for discussion and navigation on Protect The Information In Processing, Security And Scalability, Homomorphic Encryption, Multi Party Computation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing Services
Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing ServicesThis slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Trust Boundary Across Azure Confidential Computing Services. Dispense information and present a thorough explanation of Trust Boundary Architecture, Azure Confidential Computing Services, Demonstrate The Trust Boundary, Sensitive Data, Sensitive Application Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform
Confidential Computing Hardware Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform. This template helps you present information on three stages. You can also present information on Protects Guest Memory, Provide Virtual Machine Isolation, Secure Memory Encryption, Encrypted State Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware What Is Fully Homomorphic Encryption FHE
Confidential Computing Hardware What Is Fully Homomorphic Encryption FHEThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Introducing Confidential Computing Hardware What Is Fully Homomorphic Encryption FHE to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Fully Homomorphic Encryption, Strict Regulatory Compliance, Enhanced Cloud Security, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware What Is Trusted Execution Environment Tee In Confidential
Confidential Computing Hardware What Is Trusted Execution Environment Tee In ConfidentialThis slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware What Is Trusted Execution Environment Tee In Confidential. This template helps you present information on five stages. You can also present information on Code Confidentiality, Authenticated Launch, Programmability, Confidential Computing Consortium using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Working Of Confidential Computing Technology
Confidential Computing Hardware Working Of Confidential Computing TechnologyThis slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Present the topic in a bit more detail with this Confidential Computing Hardware Working Of Confidential Computing Technology. Use it as a tool for discussion and navigation on Confidential Computing Technology, Protect Businesses, Performing Computations, Operating System, Cloud Providers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Segments Overview Confidential Computing Hardware
Confidential Computing Market Segments Overview Confidential Computing HardwareThis slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Present the topic in a bit more detail with this Confidential Computing Market Segments Overview Confidential Computing Hardware. Use it as a tool for discussion and navigation on Microprocessors And Microcontrollers, Application Development Services, Managed Services For Confidential Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Use Cases And Ecosystem Confidential Computing Hardware
Confidential Computing Use Cases And Ecosystem Confidential Computing HardwareThis slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Deliver an outstanding presentation on the topic using this Confidential Computing Use Cases And Ecosystem Confidential Computing Hardware. Dispense information and present a thorough explanation of Ecosystem Of Confidential Computing, Key Management Systems, Secure Cloud Migration, Database Protection, Data Services For Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icons Slide For Confidential Computing Hardware Ppt Icon Example Introduction
Icons Slide For Confidential Computing Hardware Ppt Icon Example IntroductionIntroducing our well researched set of slides titled Icons Slide For Confidential Computing Hardware Ppt Icon Example Introduction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Overview Of Confidential Computing Consortium Confidential Computing Hardware
Overview Of Confidential Computing Consortium Confidential Computing HardwareThis slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Present the topic in a bit more detail with this Overview Of Confidential Computing Consortium Confidential Computing Hardware. Use it as a tool for discussion and navigation on Different Technical Projects, Technical Project, Governing Board, Responsible For Budget Decisions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer Data Intelligence Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Data Intelligence Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colored PowerPoint icon is a perfect representation of Data Intelligence. It is a great visual aid to help explain the concept of data analysis and how it can be used to make informed decisions. It is a great tool to help visualize the power of data and its potential.
-
 Computer Data Intelligence Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Data Intelligence Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Intelligence is perfect for presentations. It features a black and white image of a brain with a graph and a magnifying glass to represent data analysis. Its a great visual to illustrate the concept of data intelligence.
-
 Network Collaboration Cloud Computing In Powerpoint And Google Slides Cpb
Network Collaboration Cloud Computing In Powerpoint And Google Slides CpbPresenting Network Collaboration Cloud Computing In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Collaboration Cloud Computing. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer Website Loading Speed Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Website Loading Speed Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis vibrant PowerPoint icon is a great visual representation of website speed. It features a colourful wheel with a lightning bolt, indicating the speed of a website. Perfect for presentations on website performance, speed optimization, and more.
-
 Computer Website Loading Speed Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Website Loading Speed Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is an ideal graphic for illustrating website speed. Its simple design and neutral colors make it easy to integrate into any presentation. Perfect for illustrating the importance of website speed in todays digital world.
-
 Computing Website Speed Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computing Website Speed Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis vibrant PowerPoint icon is a great visual representation of website speed. It features a colourful wheel with a lightning bolt, indicating the speed of a website. Perfect for presentations on website performance, speed optimization, and more.
-
 Computing Website Speed Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computing Website Speed Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is an ideal graphic for illustrating website speed. Its simple design and neutral colors make it easy to integrate into any presentation. Perfect for illustrating the importance of website speed in todays digital world.
-
 Cloud Computing Library Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Computing Library Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon from Cloud Library is perfect for adding a modern touch to your presentation. It features a vibrant, eye catching design that will stand out and draw attention to your slides. Download now and make your presentation truly unique.
-
 Cloud Computing Library Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Computing Library Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon from Cloud Library is perfect for adding a professional touch to your presentations. Its simple, stylish and versatile, making it easy to customize and integrate into your slides. Its sure to make your presentation stand out.
-
 Online Computer Reading Book Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Online Computer Reading Book Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for presentations on online reading. It features a book with a laptop, showing the connection between digital and traditional reading. Its a great way to illustrate the importance of reading in the digital age.
-
 Online Computer Reading Book Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Online Computer Reading Book Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is perfect for online reading. It features a book with a magnifying glass, representing the act of reading. It is a great visual aid to emphasize the importance of reading and learning.
-
 Clear Computer Inbox Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Clear Computer Inbox Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a simple and effective way to delete emails from your inbox. It is designed to be intuitive and easy to use, allowing you to quickly remove emails and keep your inbox organised. It is a great tool for streamlining your workflow and keeping your inbox clutter free.
-
 Clear Computer Inbox Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Clear Computer Inbox Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations and documents. It shows a trash can with an arrow pointing to it, symbolizing the delete inbox action. It is simple, modern, and easy to use, making it an ideal choice for any project.
-
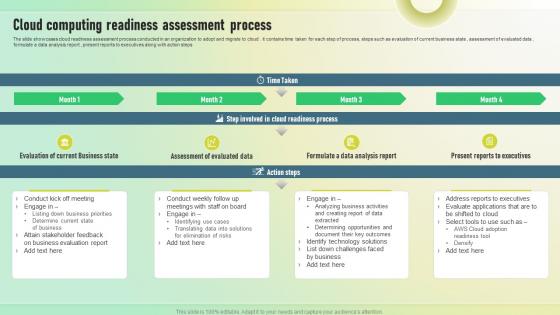 Cloud Computing Readiness Assessment Process
Cloud Computing Readiness Assessment ProcessThe slide showcases cloud readiness assessment process conducted in an organization to adopt and migrate to cloud. it contains time taken for each step of process, steps such as evaluation of current business state, assessment of evaluated data, formulate a data analysis report, present reports to executives along with action steps. Introducing our premium set of slides with Cloud Computing Readiness Assessment Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assessment Of Evaluated Data, Data Analysis Report, Readiness Process. So download instantly and tailor it with your information.
-
 Computer Depreciation Schedule In Powerpoint And Google Slides Cpb
Computer Depreciation Schedule In Powerpoint And Google Slides CpbPresenting Computer Depreciation Schedule In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Computer Depreciation Schedule. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer Memory In Powerpoint And Google Slides Cpb
Computer Memory In Powerpoint And Google Slides CpbPresenting our Computer Memory In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Computer Memory This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Computer Return Policy In Powerpoint And Google Slides Cpb
Best Computer Return Policy In Powerpoint And Google Slides CpbPresenting our Best Computer Return Policy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Best Computer Return Policy. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Financial Statements And Valuation For Computer Repair And Maintenance Business Plan In Excel BP XL
Financial Statements And Valuation For Computer Repair And Maintenance Business Plan In Excel BP XLAre you worried about conveying complex data to your target audience without leaving them confused. Well, our tailor made Financial Statements And Valuation For Computer Repair And Maintenance Business Plan In Excel BP XL template will bring an end to all your worries. This template is fully editable and thus you can tweak it in line with your individual preferences and audience needs. Being a multi purpose design, every time there are circumstantial differences, our template will stand up to the occasion. Made with utmost precision we have followed a top down approach Industry company while curating these excel sheets. The curated excel sheet presents five year projection from 2023 to 2027. Covering the important aspects like details on pay back period, DCF Valuation, Scenario, Break even analysis, and financial statements, this sheet is all that you need to elucidate your organizations specifics. The excel goes well with various number of softwares including major Microsoft versions and Google spreadsheets. You can play with the figures especially the blue ones and fine tune the same to suit your sector specific catering. With our assistance, you can be assured of focusing on the core activities, while completely putting the burden of template designing on our shoulders.
-
 Financial Statements Modeling And Valuation For Computer Accessories Business Plan In Excel BP XL
Financial Statements Modeling And Valuation For Computer Accessories Business Plan In Excel BP XLAre you worried about conveying complex data to your target audience without leaving them confused. Well, our tailor made Financial Statements Modeling And Valuation For Computer Accessories Business Plan In Excel BP XL template will bring an end to all your worries. This template is fully editable and thus you can tweak it in line with your individual preferences and audience needs. Being a multi purpose design, every time there are circumstantial differences, our template will stand up to the occasion. Made with utmost precision we have followed a top down approach Industry company while curating these excel sheets. The curated excel sheet presents five year projection from 2023 to 2027. Covering the important aspects like details on pay back period, DCF Valuation, Scenario, Break even analysis, and financial statements, this sheet is all that you need to elucidate your organizations specifics. The excel goes well with various number of softwares including major Microsoft versions and Google spreadsheets. You can play with the figures especially the blue ones and fine tune the same to suit your sector specific catering. With our assistance, you can be assured of focusing on the core activities, while completely putting the burden of template designing on our shoulders.
-
 Financial Statements Modeling And Valuation For Computer Repair Shop Business Plan In Excel BP XL
Financial Statements Modeling And Valuation For Computer Repair Shop Business Plan In Excel BP XLAre you worried about conveying complex data to your target audience without leaving them confused. Well, our tailor made Financial Statements Modeling And Valuation For Computer Repair Shop Business Plan In Excel BP XL template will bring an end to all your worries. This template is fully editable and thus you can tweak it in line with your individual preferences and audience needs. Being a multi purpose design, every time there are circumstantial differences, our template will stand up to the occasion. Made with utmost precision we have followed a top down approach Industry company while curating these excel sheets. The curated excel sheet presents five year projection from 2023 to 2027. Covering the important aspects like details on pay back period, DCF Valuation, Scenario, Break even analysis, and financial statements, this sheet is all that you need to elucidate your organizations specifics. The excel goes well with various number of softwares including major Microsoft versions and Google spreadsheets. You can play with the figures especially the blue ones and fine tune the same to suit your sector specific catering. With our assistance, you can be assured of focusing on the core activities, while completely putting the burden of template designing on our shoulders.
-
 Financial Statements Modeling And Valuation For Computer Software Business Plan In Excel BP XL
Financial Statements Modeling And Valuation For Computer Software Business Plan In Excel BP XLAre you worried about conveying complex data to your target audience without leaving them confused. Well, our tailor made Financial Statements Modeling And Valuation For Computer Software Business Plan In Excel BP XL template will bring an end to all your worries. This template is fully editable and thus you can tweak it in line with your individual preferences and audience needs. Being a multi purpose design, every time there are circumstantial differences, our template will stand up to the occasion. Made with utmost precision we have followed a top down approach Industry company while curating these excel sheets. The curated excel sheet presents five year projection from 2023 to 2027. Covering the important aspects like details on pay back period, DCF Valuation, Scenario, Break even analysis, and financial statements, this sheet is all that you need to elucidate your organizations specifics. The excel goes well with various number of softwares including major Microsoft versions and Google spreadsheets. You can play with the figures especially the blue ones and fine tune the same to suit your sector specific catering. With our assistance, you can be assured of focusing on the core activities, while completely putting the burden of template designing on our shoulders.
-
 Bricks Game In Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Bricks Game In Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for your next presentation. Representing a brick from the classic game, it will add a fun and playful touch to your slides. Its easy to use and comes in a range of colours to suit any project.
-
 Bricks Game In Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Bricks Game In Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for presentations related to the classic game of Bricks. It features a single-colored image of a brick wall, perfect for adding a nostalgic touch to any presentation.
-
 Computer Science Bot Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Science Bot Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts a friendly robot, perfect for adding a modern tech touch to any presentation. The icon is bright and inviting, ideal for creating a positive atmosphere.
-
 Computer Science Bot Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Science Bot Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon depicts a robotic figure with a circular head, two arms, and two legs. It is a perfect choice for presentations about robots, automation, and artificial intelligence.
-
 Pros Cons Cloud Computing TechTarget In Powerpoint And Google Slides Cpb
Pros Cons Cloud Computing TechTarget In Powerpoint And Google Slides CpbPresenting our Pros Cons Cloud Computing TechTarget In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Pros Cons Cloud Computing TechTarget This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 E Waste Recycling Computer Components Colored Icon In Powerpoint Pptx Png And Editable Eps Format
E Waste Recycling Computer Components Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon depicts a chip recycling bin. It is a perfect visual representation for presentations on the importance of chip recycling and proper disposal of electronic waste.
-
 E Waste Recycling Computer Components Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
E Waste Recycling Computer Components Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for representing chip recycling. It features a recycle symbol with a chip in the center, signifying the importance of chip recycling in the modern world.
-
 IoT Edge Computing Technology For Comprehensive Guide For IoT Edge IOT SS
IoT Edge Computing Technology For Comprehensive Guide For IoT Edge IOT SSFollowing slide showcases IoT edge use cases through asset and devices management in organization to improve operational efficiency. It includes elements such as description, distributed firm updates, connected devices diagnostics, etc.Increase audience engagement and knowledge by dispensing information using IoT Edge Computing Technology For Comprehensive Guide For IoT Edge IOT SS. This template helps you present information on three stages. You can also present information on Distributed Firmware, Device Configuration, Connected Devices Diagnostics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Advantages Of Edge Computing In IoT Comprehensive Guide For IoT Edge IOT SS
Key Advantages Of Edge Computing In IoT Comprehensive Guide For IoT Edge IOT SSFollowing slide exhibits benefits of edge computing for internet of things IoT to ensure fast and reliable data processing. It includes pointers such as reduced latency, scalability, enhanced security, cost savings, etc.Introducing Key Advantages Of Edge Computing In IoT Comprehensive Guide For IoT Edge IOT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Increases Business, Data Recovery Through, Processing Capabilities, using this template. Grab it now to reap its full benefits.
-
 Key Components Of IoT Edge Computing Comprehensive Guide For IoT Edge IOT SS
Key Components Of IoT Edge Computing Comprehensive Guide For IoT Edge IOT SSFollowing slide exhibits ley components associated with IOT and edge computing to facilitate effective integration and data processing. It includes elements such as data management and analytics,, connectivity, communication, etc. Increase audience engagement and knowledge by dispensing information using Key Components Of IoT Edge Computing Comprehensive Guide For IoT Edge IOT SS. This template helps you present information on four stages. You can also present information on Connectivity Communication, Storage Management, Data Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





