Powerpoint Templates and Google slides for Cloud Security Working
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Seven petal secure authentication cloud communications process workflow
Seven petal secure authentication cloud communications process workflowIntroduce your topic and host expert discussion sessions with this Seven Petal Secure Authentication Cloud Communications Process Workflow. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the seventeen slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working. Use it as a tool for discussion and navigation on Deployment Overview And Working, Web Servers They Visit, Forward Proxy Method Is A Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Architecture And Working Of SD Wide Area Network Cloud Security Model
Architecture And Working Of SD Wide Area Network Cloud Security ModelThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Increase audience engagement and knowledge by dispensing information using Architecture And Working Of SD Wide Area Network Cloud Security Model. This template helps you present information on three stages. You can also present information on Working, Architecture, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall As A Service FWaaS Working And Security Features Cloud Security Model
Firewall As A Service FWaaS Working And Security Features Cloud Security ModelThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing Firewall As A Service FWaaS Working And Security Features Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet, Internet, Network, using this template. Grab it now to reap its full benefits.
-
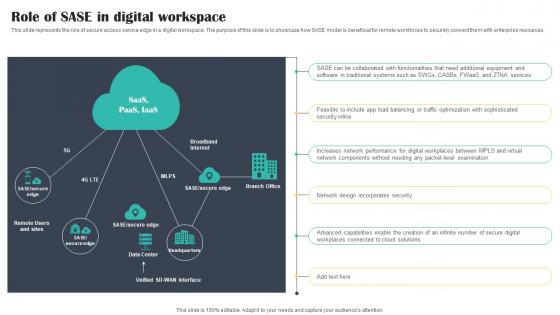 Role Of SASE In Digital Workspace Cloud Security Model
Role Of SASE In Digital Workspace Cloud Security ModelThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Introducing Role Of SASE In Digital Workspace Cloud Security Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Software, Optimization, Examination, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateways SWG Setup And Working Cloud Security Model
Secure Web Gateways SWG Setup And Working Cloud Security ModelThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using Secure Web Gateways SWG Setup And Working Cloud Security Model. This template helps you present information on eight stages. You can also present information on Implemented, Classifications, Programs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Secure Access Service Edge Cloud Security Model
Working Of Secure Access Service Edge Cloud Security ModelThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Working Of Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Network, Security, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Zero Trust Network Access Cloud Security Model
Working Of Zero Trust Network Access Cloud Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Working, Network, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Cloud Access Security Broker Working Process
Sase Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, an remediation. Deliver an outstanding presentation on the topic using this Sase Security Cloud Access Security Broker Working Process. Dispense information and present a thorough explanation of Remediation, Classification, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Secure Access Service Edge Sase
Cloud Access Security Broker Working Process Secure Access Service Edge SaseThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Information, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Functions Of Cloud Firewall System
Firewall Network Security Working Functions Of Cloud Firewall SystemThis slide talks about the different working functions that help cloud-based firewall systems to protect the user network and devices from malicious activities. The purpose of this slide is to showcase the various tasks of cloud firewalls, including packet filtering, stateful inspection, and proxy service. Introducing Firewall Network Security Working Functions Of Cloud Firewall System to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Stateful Inspection, Proxy Service, Packet Filtering using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Working Process CASB Cloud Security
Cloud Access Security Broker Working Process CASB Cloud SecurityThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process CASB Cloud Security. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Forward Proxy Deployment Overview And Working CASB Cloud Security
Forward Proxy Deployment Overview And Working CASB Cloud SecurityThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Increase audience engagement and knowledge by dispensing information using Forward Proxy Deployment Overview And Working CASB Cloud Security. This template helps you present information on eight stages. You can also present information on Forward Proxy Deployment, Internet And Origin Server, According To The Internet Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises
Cloud Architecture And Security Review Model For Workload Placement For On And Off PremisesThis slide covers the workload placement such as Workloads shown on the left are marked as off premises which are more suitable for a public cloud where as those on the right are for on premises appropriate for a private cloud and those in the middle are for a hybrid cloud. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises. Dispense information and present a thorough explanation of Model For Workload, Placement, On And Off Premises using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Information Security How Does Cloud Security Work Data Planning
Cloud Information Security How Does Cloud Security Work Data PlanningThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Increase audience engagement and knowledge by dispensing information using Cloud Information Security How Does Cloud Security Work Data Planning This template helps you present information on five stages. You can also present information on Implement Information, Authentication Process, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Cloud Information Security
How Does Cloud Security Work Cloud Information SecurityThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Cloud Information Security This template helps you present information on five stages. You can also present information on Information Security, Wireless Security, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Data Security Cloud Information Security
How Does Cloud Security Work Data Security Cloud Information SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.Introducing How Does Cloud Security Work Data Security Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Accessibility, Knowledge, Organized Documented using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Information Security
How Does Cloud Security Work Governance Cloud Information SecurityThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Information Security This template helps you present information on four stages. You can also present information on Authentication, Access Management, Verification Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Identity And IAM Cloud Information Security
How Does Cloud Security Work Identity And IAM Cloud Information SecurityThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Present the topic in a bit more detail with this How Does Cloud Security Work Identity And IAM Cloud Information Security Use it as a tool for discussion and navigation on Requirements, Transparency, Governance This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Cloud Security Work Legal Compliance Cloud Information Security
How Does Cloud Security Work Legal Compliance Cloud Information SecurityThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Information Security This template helps you present information on eight stages. You can also present information on Firewalls Ensure, Organization Security, Permitting Limited using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
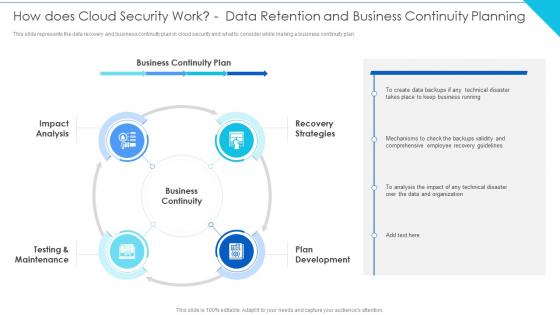
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Security
Cloud Computing Security How Does Cloud Security Work Data SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing Cloud Computing Security How Does Cloud Security Work Data Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Application Security, Physical Security, Internet Security, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Governance
Cloud Computing Security How Does Cloud Security Work GovernanceThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Governance. This template helps you present information on five stages. You can also present information on Data Governance, Security, Technology, Ownership using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Identity And Access Management
Cloud Computing Security How Does Cloud Security Work Identity And Access ManagementThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing Cloud Computing Security How Does Cloud Security Work Identity And Access Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Access Management, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Legal Compliance
Cloud Computing Security How Does Cloud Security Work Legal ComplianceThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Legal Compliance. This template helps you present information on eight stages. You can also present information on Transparency, Regulations, Governance, Compliance, Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Ppt Introduction
Cloud Computing Security How Does Cloud Security Work Ppt IntroductionThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Introducing Cloud Computing Security How Does Cloud Security Work Ppt Introduction to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Access Management, Cloud Security, Business Continuity Planning, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Cloud Data Protection
How Does Cloud Security Work Cloud Data ProtectionThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Introducing How Does Cloud Security Work Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Data Security, Access Management, Business Continuity Planning, Cloud Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Data Retention And Business Cloud Data Protection
How Does Cloud Security Work Data Retention And Business Cloud Data ProtectionThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Data Retention And Business Cloud Data Protection. This template helps you present information on four stages. You can also present information on Impact Analysis, Business Continuity, Plan Development, Recovery Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 How Does Cloud Security Work Data Security Cloud Data Protection
How Does Cloud Security Work Data Security Cloud Data ProtectionThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing How Does Cloud Security Work Data Security Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Wireless Security, Internet Security, Application Security, Network Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Data Protection
How Does Cloud Security Work Governance Cloud Data ProtectionThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Data Protection. This template helps you present information on five stages. You can also present information on Knowledge, Quality, Security, Accessibility, Data Governance using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 How Does Cloud Security Work Identity And Access Management Cloud Data Protection
How Does Cloud Security Work Identity And Access Management Cloud Data ProtectionThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing How Does Cloud Security Work Identity And Access Management Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Access Management, Authentication, Authorization, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Legal Compliance Cloud Data Protection
How Does Cloud Security Work Legal Compliance Cloud Data ProtectionThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Data Protection. This template helps you present information on eight stages. You can also present information on Secure Data, Organizations, Compliance using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration
SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint DemonstrationThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE IT Cloud Access Security Broker Working Process Ppt Powerpoint Demonstration. This template helps you present information on one stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Working Process Ppt Ideas Grid
Cloud Access Security Broker Working Process Ppt Ideas GridThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Ppt Ideas Grid. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB Forward Proxy Deployment Overview And Working. Dispense information and present a thorough explanation of Overview, Forward Proxy, Internet using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud based security work ppt powerpoint presentation summary pictures cpb
Cloud based security work ppt powerpoint presentation summary pictures cpbPresenting this set of slides with name Cloud Based Security Work Ppt Powerpoint Presentation Summary Pictures Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cloud Based Security Work to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cloud based security work ppt powerpoint presentation professional deck cpb
Cloud based security work ppt powerpoint presentation professional deck cpbPresenting this set of slides with name Cloud Based Security Work Ppt Powerpoint Presentation Professional Deck Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cloud Based Security Work to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 How does cloud security work cloud security it ppt themes
How does cloud security work cloud security it ppt themesThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.Introducing How Does Cloud Security Work Cloud Security IT Ppt Themes to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Access Management, Business Continuity Planning, using this template. Grab it now to reap its full benefits.
-
 How does cloud security work data retention and business continuity planning cloud security it
How does cloud security work data retention and business continuity planning cloud security itThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Security IT. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How does cloud security work data security cloud security it ppt slides
How does cloud security work data security cloud security it ppt slidesThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.Introducing How Does Cloud Security Work Data Security Cloud Security IT Ppt Slides to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Application Security, Network Security, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 How does cloud security work governance cloud security it ppt rules
How does cloud security work governance cloud security it ppt rulesThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Security IT Ppt Rules. This template helps you present information on five stages. You can also present information on Knowledge, Owner Ship, Accessibility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How does cloud security work identity and access management i am cloud security it
How does cloud security work identity and access management i am cloud security itThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Introducing How Does Cloud Security Work Identity And Access Management I am Cloud Security IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Access Management, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 How does cloud security work legal compliance cloud security it ppt rules
How does cloud security work legal compliance cloud security it ppt rulesThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Security IT Ppt Rules. This template helps you present information on eight stages. You can also present information on Governance, Regulations, Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



