Powerpoint Templates and Google slides for Business Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security Threat
Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about communication plan for the recovery team. It includes key elements such as meeting agenda, meeting coordinator, things to communicate, meeting mode, and target audience. Present the topic in a bit more detail with this Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Incident Details, Impact Assessment, Recovery Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security Threat
Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about recovery team structure and number of members across different team for business recovery. It includes teams such as executive, communication, crisis management, impact assessment, etc. Present the topic in a bit more detail with this Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Business Continuity Expert, Assessment, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates a sample email template that can be used by the company to inform stakeholders about security incidents. It includes key elements such as incident details, impacted data, potential impact, and our actions. Present the topic in a bit more detail with this Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Government, Executives, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security Threat
Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber hacking incidents on business key areas such as financial, operational area, company reputation, and market value. Introducing Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial Impact, Operational Impact, Legal Impact, using this template. Grab it now to reap its full benefits.
-
 Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security Threat
Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber response plan applications on business performance. It includes key areas of impact such as reputation, operations, and market value of company Increase audience engagement and knowledge by dispensing information using Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Operational Impact, Reputation Impact, Legal Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Business Recovery Plan To Overcome Cyber Security Threat
Icons Slide For Business Recovery Plan To Overcome Cyber Security ThreatDeliver an outstanding presentation on the topic using this Icons Slide For Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat
Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the key components of cyber security threat response plan. It includes key elements such as identify attack source, limit damage, damage scope assessment, consulting, clean up system, and future action plan. Increase audience engagement and knowledge by dispensing information using Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on six stages. You can also present information on Identify The Attack Source, Limit Additional Damage, Damage Scope Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat
Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cyber attack incidents. It includes information about incident date, impact, and incident information comprising loss of customer name, address, phone number, birth date, etc. Increase audience engagement and knowledge by dispensing information using Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Ransomware, Information, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security Threat
Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the implementation of a network segmentation strategy to reduce cyber damage. It further includes key benefits of network segmentation such as improved performance, protect vulnerable devices, and limit damage. Present the topic in a bit more detail with this Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Improve Performance, Protect Devices, Reduce Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat
Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various solutions that can be adopted for business cyber-attack management. It includes key solutions such as staff training, collaboration with experts, and develop business recovery plan. Deliver an outstanding presentation on the topic using this Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Solution Scope, Solution Duration, Requisites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat
Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various methods of data backups that should be implemented by a company to avoid data loss. It includes data backup types such as full, incremental, differential, and mirror. Present the topic in a bit more detail with this Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Techniques, Application, Incremental. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat
Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals set for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Introducing Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mean Time To Contain, Mean Time To Resolve, Mean Time To Recover, using this template. Grab it now to reap its full benefits.
-
 Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security Threat
Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information software updation best practices to follow. It includes key practices such as updation operating system, uninstall unnecessary software, and leverage patch systems. Increase audience engagement and knowledge by dispensing information using Software Updation To Avoid Security Breach Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Leverage Patching System, Uninstall Unnecessary Software, Update Operating System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Business Recovery Plan To Overcome Cyber Security Threat
Table Of Contents Business Recovery Plan To Overcome Cyber Security ThreatIntroducing Table Of Contents Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario, Potential Solutions, Business Recovery Plan , using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Business Overview With Goals And Service Offerings
Securing Food Safety In Online Business Overview With Goals And Service OfferingsThis slide covers restaurant business overview along with its goals and services offered such as dine in, takeout and pickup, delivery service, online orders and happy hours. Present the topic in a bit more detail with this Securing Food Safety In Online Business Overview With Goals And Service Offerings. Use it as a tool for discussion and navigation on Goals, Cuisines Offered, Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Case Study Restaurant Business Adopting Third Party
Securing Food Safety In Online Case Study Restaurant Business Adopting Third PartyThis slide covers case study of restaurant enhancing food delivery efficiency and reducing order errors by integrating third party delivery applications. Introducing Securing Food Safety In Online Case Study Restaurant Business Adopting Third Party to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reduced Delivery Times, Increases Customer Satisfaction Score, Increase In Delivery Orders, using this template. Grab it now to reap its full benefits.
-
 Securing Food Safety In Online Current Business Model Canvas Of Restaurant
Securing Food Safety In Online Current Business Model Canvas Of RestaurantThis slide covers restaurant business model canvas includes partners associated, activities involved, value propositions and revenue streams of business. Present the topic in a bit more detail with this Securing Food Safety In Online Current Business Model Canvas Of Restaurant. Use it as a tool for discussion and navigation on Key Partners, Key Activities, Value Propositions, Customer Relationships. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Integrating SIEM Cyber Security In Business
Impact Of Integrating SIEM Cyber Security In BusinessThis slide showcases the benefits of incorporation SIEM cyber security. Its objective is to propose a better threat detection system. This slide includes threat detection, staff and less spend. Introducing our premium set of slides with name Impact Of Integrating SIEM Cyber Security In Business. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Better Threat Detection, Fewer Staff, Less Spend. So download instantly and tailor it with your information.
-
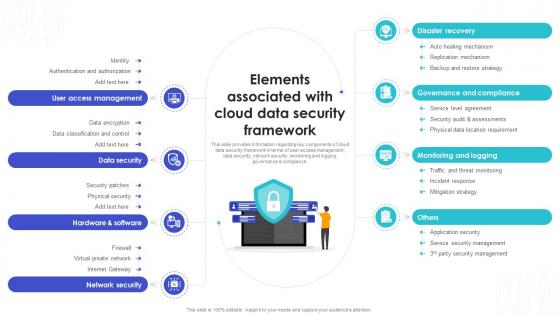 Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS
Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding key components of cloud data security framework in terms of user access management, data security, network security, monitoring and logging, governance and compliance.Increase audience engagement and knowledge by dispensing information using Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Disaster Recovery, User Access Management, Data Security, Network Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS
Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding focusing on proactive security for successful data loss prevention execution. It will include initiatives such as infiltration, exfiltration, automated protection, etc.Increase audience engagement and knowledge by dispensing information using Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Exhibited Behavior, Objective, Customization, High Risk Events using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Identity And Access Management On Business Securing Systems With Identity
Impact Of Identity And Access Management On Business Securing Systems With IdentityThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Deliver an outstanding presentation on the topic using this Impact Of Identity And Access Management On Business Securing Systems With Identity Dispense information and present a thorough explanation of Enhanced Security, Cost Savings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Salient Features Of Mobile Security For Businesses Mobile Security
Salient Features Of Mobile Security For Businesses Mobile SecurityThis slide highlights the key features of mobile security for enterprises which include provides centralized management, blocks malicious web content, etc. Introducing Salient Features Of Mobile Security For Businesses Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Patch Approvals, Customizable Exclusions using this template. Grab it now to reap its full benefits.
-
 Fintech Business Cyber Security Icon
Fintech Business Cyber Security IconIntroducing our premium set of slides with name Fintech Business Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Fintech Business, Cyber Security. So download instantly and tailor it with your information.
-
 Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures
Business Survey Highlighting Challenges In Managing Implementing E Commerce Security MeasuresThis slide highlights common challenges that businesses face while managing ecommerce frauds. It include problems such as identifying fraud attacks, gap un fraud tool functionalities, lack of internal resources etc. Introducing Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Fraud Attacks, Updating Fraud Risk Model, Sufficient Internal Resources, using this template. Grab it now to reap its full benefits.
-
 Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases gap analysis which can help companies realize their need assessment position by calculating current and desired state, assisting them plan action items. Present the topic in a bit more detail with this Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Parameters, Current State, Impact, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Impact Of Web Security Deployment On Business
Web Security Upgradation Impact Of Web Security Deployment On BusinessThis slide showcases the after web security impact on industries which include security, reduced cyber threats in web, etc. Introducing Web Security Upgradation Impact Of Web Security Deployment On Business to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Decrease In Cyber Threats, Legal Consultations, Internet Safety Standards, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Timeline For Web Security Deployment In Business
Web Security Upgradation Timeline For Web Security Deployment In BusinessThis slide outlines the timeline for implementing web security in an organization which include assessment, planning, etc. Introducing Web Security Upgradation Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Email Security Implementation Impact On Businesses
Email Security Best Practices Email Security Implementation Impact On BusinessesThis slide illustrates the business impact of implementing email security policies. The parameters described in this slide are improved data protection, reduced phishing attacks, increased employee productivity, enhanced brand reputation, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Security Implementation Impact On Businesses. Use it as a tool for discussion and navigation on Improved Data Protection, Reduced Phishing Attacks, Increased Employee Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Measures Of Email Account Security For Businesses
Email Security Best Practices Measures Of Email Account Security For BusinessesThe purpose of this slide is to discuss the strategies for businesses to secure the email accounts of their employees. These measures are employee training, implementing email security policies and using email encryption techniques. Introducing Email Security Best Practices Measures Of Email Account Security For Businesses to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Email Security Policies, Email Encryption, using this template. Grab it now to reap its full benefits.
-
 Business Benefits Of Implementing Web Security Solution
Business Benefits Of Implementing Web Security SolutionThis slide outlines the pros of web security in business which include safeguarding sensitive data, securing private information, etc. Introducing Business Benefits Of Implementing Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Sensitive Data, Secure Private Information, Prevent Costly Service Disruptions, using this template. Grab it now to reap its full benefits.
-
 Impact Of Web Security On Different Businesses
Impact Of Web Security On Different BusinessesThis slide showcases the various factors that have improved which include security, reduced cyber threats in web, and so on. Introducing Impact Of Web Security On Different Businesses to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Decrease In Cyber Threats, Businesses Face Comparatively Less Expenses, Increased Security, using this template. Grab it now to reap its full benefits.
-
 Timeline For Web Security Deployment In Business
Timeline For Web Security Deployment In BusinessThis slide outlines the different steps performed while deploying web security, including assessment, planning, and so on. Introducing Timeline For Web Security Deployment In Business to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Assessment And Planning, Infrastructure Security, Secure Development Practices, using this template. Grab it now to reap its full benefits.
-
 Business Security Configuration Management Icon
Business Security Configuration Management IconPresenting our well structured Business Security Configuration Management Icon. The topics discussed in this slide are Business Security Configuration Management Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Define Security Token Project Business Model Ultimate Guide Smart BCT SS V
Define Security Token Project Business Model Ultimate Guide Smart BCT SS VThe following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. Deliver an outstanding presentation on the topic using this Define Security Token Project Business Model Ultimate Guide Smart BCT SS V. Dispense information and present a thorough explanation of Key Elements, Project Name, Tokenization Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Product Opportunity Canvas For Home Security Business
Product Opportunity Canvas For Home Security BusinessThe slide portrays product opportunity assessment canvas for home security company. It include elements such as product summary, features, customer segments, revenue stream etc. Introducing our Product Opportunity Canvas For Home Security Business set of slides. The topics discussed in these slides are Competitive Landscape, Critical Success Factors, Revenue Streams. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Impact Of Deepfake Threats On Business Security
Impact Of Deepfake Threats On Business SecurityThe purpose of this slide is to illustrate impact of deepfake threats on business security. It covers various implications such as asset thefts, financial and reputational losses. Introducing our premium set of slides with name Impact Of Deepfake Threats On Business Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Financial Losses, Reputational Losses, Asset Thefts. So download instantly and tailor it with your information.
-
 Business security management consulting sample ppt powerpoint layout
Business security management consulting sample ppt powerpoint layoutPresenting business security management consulting sample ppt powerpoint layout. This is a business security management consulting sample ppt powerpoint layout. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.
-
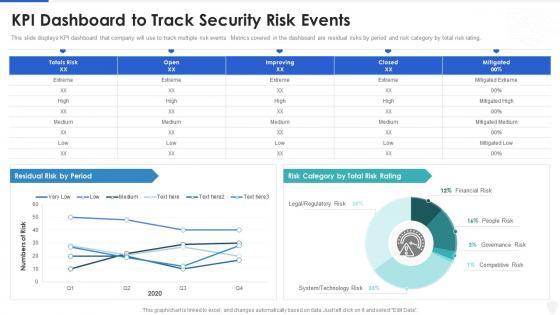 Cybersecurity and digital business risk management kpi dashboard to track security risk events
Cybersecurity and digital business risk management kpi dashboard to track security risk eventsPresent the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Kpi Dashboard To Track Security Risk Events. Use it as a tool for discussion and navigation on KPI Dashboard To Track Security Risk Events. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Analytics Dashboard Slide For Computer Security Infographic Template
Business Analytics Dashboard Slide For Computer Security Infographic TemplateThis is our Business Analytics Dashboard Slide For Computer Security Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully-editable visual content.
-
 Security Hacker Impact Of Ethical Hackers On Business Ppt Summary
Security Hacker Impact Of Ethical Hackers On Business Ppt SummaryThis slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc. Present the topic in a bit more detail with this Security Hacker Impact Of Ethical Hackers On Business Ppt Summary. Use it as a tool for discussion and navigation on Ethical Hackers, Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Column Chart Security Services Business Profile Ppt Mockup
Column Chart Security Services Business Profile Ppt MockupPresent the topic in a bit more detail with this Column Chart Security Services Business Profile Ppt Mockup. Use it as a tool for discussion and navigation on Column Chart, Product. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Analysis Security Services Business Profile Ppt Professional
Competitive Analysis Security Services Business Profile Ppt ProfessionalThis slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Present the topic in a bit more detail with this Competitive Analysis Security Services Business Profile Ppt Professional. Use it as a tool for discussion and navigation on Category, Customer Retention, Competitive Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 CSR Initiatives And Spending Security Services Business Profile Ppt Rules
CSR Initiatives And Spending Security Services Business Profile Ppt RulesThis slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver an outstanding presentation on the topic using this CSR Initiatives And Spending Security Services Business Profile Ppt Rules. Dispense information and present a thorough explanation of Spend Distribution, Activities, Initiatives And Spending using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ebitda And Margin Security Services Business Profile Ppt Ideas
Ebitda And Margin Security Services Business Profile Ppt IdeasThis slide highlights the EBITDA and margin of security guard and manpower services company which showcases five-year data through combination chart. Present the topic in a bit more detail with this Ebitda And Margin Security Services Business Profile Ppt Ideas. Use it as a tool for discussion and navigation on Ebitda And Margin. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Line Chart Security Services Business Profile Ppt Clipart
Line Chart Security Services Business Profile Ppt ClipartPresent the topic in a bit more detail with this Line Chart Security Services Business Profile Ppt Clipart. Use it as a tool for discussion and navigation on Line Chart, Sales In Percentage, Financial Years. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Revenue And Net Profit Security Services Business Profile Ppt Diagrams
Revenue And Net Profit Security Services Business Profile Ppt DiagramsThis slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Present the topic in a bit more detail with this Revenue And Net Profit Security Services Business Profile Ppt Diagrams. Use it as a tool for discussion and navigation on Revenue, Net Profit. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Revenue By Customer Type Security Services Business Profile Ppt Slides
Revenue By Customer Type Security Services Business Profile Ppt SlidesThis slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an outstanding presentation on the topic using this Revenue By Customer Type Security Services Business Profile Ppt Slides. Dispense information and present a thorough explanation of Revenue, Customer Type using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sales Revenue By Region And Services Security Services Business Profile Ppt Graphics
Sales Revenue By Region And Services Security Services Business Profile Ppt GraphicsThis slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Present the topic in a bit more detail with this Sales Revenue By Region And Services Security Services Business Profile Ppt Graphics. Use it as a tool for discussion and navigation on Sales Revenue, Region And Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Improvement Plan Impact On Business
Cyber Security Improvement Plan Impact On BusinessThis slide shows difference between before and after implementing cyber security improvement plan in business. It includes types phishing attacks, malware attacks, data breaches, etc. Introducing our Cyber Security Improvement Plan Impact On Business set of slides. The topics discussed in these slides are Phishing Attacks, Malware Attacks, Data Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Profitability Comparison Of Business Investments In Securities
Profitability Comparison Of Business Investments In SecuritiesThis slide shows graphical report to analyze market timing and fluctuations in returns to gain maximum from the funds invested in share market. It includes details about most profitable ones, average and least growth. Presenting our well-structured Profitability Comparison Of Business Investments In Securities. The topics discussed in this slide are Profitability Comparison, Business Investments, Securities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Security Dashboard For Overtime Status Breakdown
Business Security Dashboard For Overtime Status BreakdownThis slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting. Introducing our Business Security Dashboard For Overtime Status Breakdown set of slides. The topics discussed in these slides are Business Security, Dashboard Overtime, Status Breakdown. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitoring Business Security Weekly Performance
Monitoring Business Security Weekly PerformanceThis slide covers monitoring business security weekly performance dashboard which includes organizational financial saving and incident engagement. Introducing our Monitoring Business Security Weekly Performance set of slides. The topics discussed in these slides are Monitoring Business, Security Weekly, Performance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS
ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SSThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc.Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Risk Categories, Control Review, Control Review Effectiveness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SS
Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SSThis slide provides information regarding potential business and research collaboration initiated by Amazon. The focus of Amazon is to cooperate with credible, knowledgeable, innovative industry partners who share similar vision such as microsoft, ford, etc. Introducing Significant Business Research How Amazon Is Securing Competitive Edge Across Globe Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implemented, Security Systems, Capability, using this template. Grab it now to reap its full benefits.
-
 Business Data Security And Privacy Assessment Survey Form Survey SS
Business Data Security And Privacy Assessment Survey Form Survey SSFollowing slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Introducing our Business Data Security And Privacy Assessment Survey Form Survey SS set of slides. The topics discussed in these slides are Security Tools Used, Allocated For Tools, Security Software Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS V
ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this ICT Business Security KPI Dashboard ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Standard Control Issues, Control Issues By Regulation, Risk Categories. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS V
Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Key ICT Security Measures Used By Businesses ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Responsible Person, Number Of Respondents, Businesses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Access rights business security lock image
Access rights business security lock imagePresenting this set of slides with name - Access Rights Business Security Lock Image. Fully creative and editable Access Rights Business Security Lock Image PPT template, you can modify font, color, background of the presentation. You can use your company logo and name in PPT slides. The slides are compatible with Google Slides and Microsoft software and can be downloaded as JPEG or PDF format. The PPT quality is good; quality remains unchanged even on wide screen view. High quality visuals make PPT more effective.





