Powerpoint Templates and Google slides for Business Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Delivering ICT Services For Enhanced Business Security Powerpoint Presentation Slides Strategy CD V
Delivering ICT Services For Enhanced Business Security Powerpoint Presentation Slides Strategy CD VDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Delivering ICT Services For Enhanced Business Security Powerpoint Presentation Slides Strategy CD V is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Business Recovery Plan To Overcome Cyber Security Threat Powerpoint Presentation Slides
Business Recovery Plan To Overcome Cyber Security Threat Powerpoint Presentation SlidesStep up your game with our enchanting Business Recovery Plan To Overcome Cyber Security Threat Powerpoint Presentation Slides deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it is available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Security Services Business Profile Powerpoint Presentation Slides
Security Services Business Profile Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Security Services Business Profile Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of fourty five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Business Information Security Powerpoint Ppt Template Bundles
Business Information Security Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Business Information Security Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using thirty two slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyber Security Policies For Businesses Training Ppt
Cyber Security Policies For Businesses Training PptPresenting Cyber Security Policies for Businesses. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Business Security Powerpoint Ppt Template Bundles
Business Security Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Business Security Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Business Benefits Flexibility Data Security Resource Sharing Agility
Business Benefits Flexibility Data Security Resource Sharing AgilityKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Issue Impact Solution Marketing Business Network Security Internal Expansion
Issue Impact Solution Marketing Business Network Security Internal ExpansionIntroduce your topic and host expert discussion sessions with this Issue Impact Solution Marketing Business Network Security Internal Expansion. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Cycle Input Output Business Expansion Process Security Improvement Automation
Cycle Input Output Business Expansion Process Security Improvement AutomationIf you require a professional template with great design, then this Cycle Input Output Business Expansion Process Security Improvement Automation is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Protect Icon Financial Investment Business Insurance Environment Security
Protect Icon Financial Investment Business Insurance Environment SecurityDeliver a credible and compelling presentation by deploying this Protect Icon Financial Investment Business Insurance Environment Security. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Protect Icon Financial Investment Business Insurance Environment Security PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Global Security Insurance Company Business Operations Illustrating Features
Global Security Insurance Company Business Operations Illustrating FeaturesDeliver a credible and compelling presentation by deploying this Global Security Insurance Company Business Operations Illustrating Features. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Global Security Insurance Company Business Operations Illustrating Features PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Data management maturity information security business growth architecture
Data management maturity information security business growth architectureDeliver a credible and compelling presentation by deploying this Data Management Maturity Information Security Business Growth Architecture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Data Management Maturity Information Security Business Growth Architecture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS V
ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Delivering ICT Services For Enhanced Business Strategy SS V. Use it as a tool for discussion and navigation on Standard Control Issues, Control Review Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS V
Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Key ICT Security Measures Used By Businesses Delivering ICT Services For Enhanced Business Strategy SS V. Use it as a tool for discussion and navigation on Security Measure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V
Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V. Use it as a tool for discussion and navigation on Issues By Control Type, Standard Control Issues. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V
Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Deliver an outstanding presentation on the topic using this Implementation Of Information Key Ict Security Measures Used By Businesses Strategy SS V. Dispense information and present a thorough explanation of Survey Goal, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V
Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V Use it as a tool for discussion and navigation on Organisational Capability Framework, Performance Appraisal, Feedback System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V
Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V Use it as a tool for discussion and navigation on Data Sets And Compliance, IT Service Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top 5G Network Security Concerns In Business
Top 5G Network Security Concerns In BusinessThis slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Introducing our Top 5G Network Security Concerns In Business set of slides. The topics discussed in these slides are Scope Management, Network Access. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V
Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents It covers details regarding issues by control type, risk categories, etc Deliver an outstanding presentation on the topic using this Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V Dispense information and present a thorough explanation of Risk Categories, Control Review Status, Standard Control Issues using the slides given This template can be altered and personalized to fit your needs It is also available for immediate download So grab it now
-
 Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS V
Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS VThis slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Present the topic in a bit more detail with this Extensive Business Strategy Overview Of Key KPMG Cyber Security Considerations Strategy SS V. Use it as a tool for discussion and navigation on Cyber Security Considerations, Description, Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of BNLP Payment Of Business Performance Enhancing Transaction Security With E Payment
Impact Of BNLP Payment Of Business Performance Enhancing Transaction Security With E PaymentMentioned slide demonstrates the impact of Buy Now Pay Later payment option adoption on business goals. It includes key performance indicators such as new customer engagement, market share, order level and conversion rate. Deliver an outstanding presentation on the topic using this Impact Of BNLP Payment Of Business Performance Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Customer, Business, Installment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of Credit And Debit Payment On Business Enhancing Transaction Security With E Payment
Impact Of Credit And Debit Payment On Business Enhancing Transaction Security With E PaymentMentioned slide demonstrates impact of multiple card payment adoption on business growth. It includes key metrics such as business sales, customer satisfaction, convenience and expense tracking accuracy. Present the topic in a bit more detail with this Impact Of Credit And Debit Payment On Business Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Business Sales, Payment, Business This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of QR Code Application On Business Enhancing Transaction Security With E Payment
Impact Of QR Code Application On Business Enhancing Transaction Security With E PaymentMentioned slide demonstrates impact of QR code payment method adoption on business performance. It includes key metrics such as payment speed, customer convenience, security, and accessibility. Present the topic in a bit more detail with this Impact Of QR Code Application On Business Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Payment Speed, Account Details, Customer This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E Payment
Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E PaymentMentioned slide showcases various payment methods used by businesses for sales and purchase of goods and services. It includes payment methods such as debit cards, mobile wallet, credit card, cash, etc. Present the topic in a bit more detail with this Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Service, Payment, Debit Cards This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS
Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SSThis slide showcases common internet of things IoT threats in the company, referable for related businesses. It provides details about network scan, command injection, SQL, zero-day, etc. Present the topic in a bit more detail with this Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Security Awareness, Quality Threat Modeling Tools, Weak Passwords, Authentication Practices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber response plan impact on business finances over the years. It includes key reasons of reduced cyber-attack costing such as Deliver an outstanding presentation on the topic using this Cyber Impact On Business Expenses Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Business, Finances, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat
Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates cyber incident tracking dashboard. It showcase number of open cases, resolved incidents, open tickets, resolved tickets, number of incidents per incident type and incidents by cyber attack type. Deliver an outstanding presentation on the topic using this Cyber Monitoring Dashboard Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Monitoring, Dashboard, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the incident assessment checklist. It includes key assessment areas such as incident documentation, communication, incident response team activation, containment of threats, etc. Present the topic in a bit more detail with this Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Response Team, Contain Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat
Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides a graphical presentation of cyber attacks and costs per incident. It includes key elements such as cost per incident, attack rate by month, cost of incident by assets, and time taken to detect and resolve the attack. Deliver an outstanding presentation on the topic using this Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Dashboard, Reported Incidents, Graphical Presentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat
Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about key roles, responsibilities, and accountability across the different team in the recovery plan. It includes key team such as executive, crisis management, business continuity experts, etc. Deliver an outstanding presentation on the topic using this Designated Team Roles And Responsibilities Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Executive Team, Crisis Management, Business Continuity Expert using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
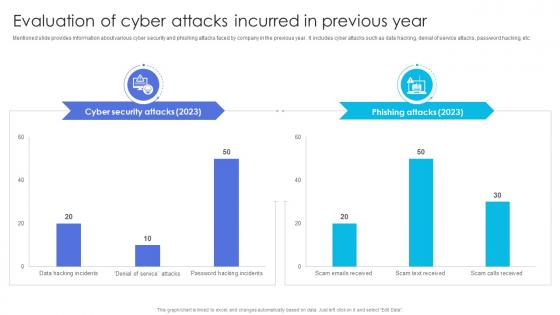 Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat
Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various cyber security and phishing attacks faced by company in the previous year. It includes cyber attacks such as data hacking, denial of service attacks, password hacking, etc. Deliver an outstanding presentation on the topic using this Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Information, Service, Evaluation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about incident status page leverage to communicate with internal stakeholders. It includes key elements such as target audience, incident page sample, and best practices. Present the topic in a bit more detail with this Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Stakeholders, Resolution Adopted. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat
Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various strategies adopted by company for preventing cyber attacks. It includes key threats such as ransomware, malware, phishing, and denial of service. Deliver an outstanding presentation on the topic using this Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Strategies, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
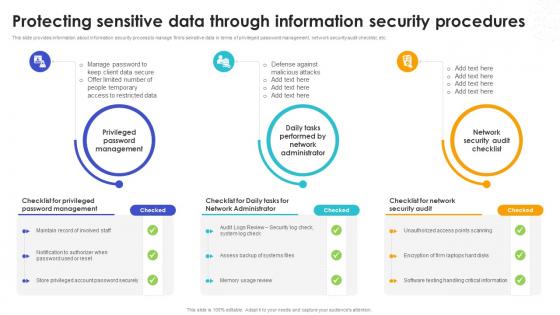 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
 Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures
Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security MeasuresThis slide portrays the common types of fraud attacks experienced by ecommerce businesses in recent years. It include frauds such as card testing, phishing, account takeover and the reason of attacks. Deliver an outstanding presentation on the topic using this Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures
Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security MeasuresThis slide represents the impact of fraud attacks on ecommerce companies. It provide information about chargeback fee, high network fee, delayed expansion or investment. Deliver an outstanding presentation on the topic using this Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Card Payment, Manage Fraud, Businesses Delay Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures
Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security MeasuresThis slide showcases financial challenges faced by the company related to cybersecurity attacks, referable for businesses facing similar situation. It cover losses caused due to lack of awareness about attacks. Present the topic in a bit more detail with this Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Key Insights, Ecommerce Business, Key Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Beneficial Impact Of IOT Security On Business
Beneficial Impact Of IOT Security On BusinessThis slide showcases benefits of implementing IoT security solutions in company. Major benefits covered are reduced malicious attacks, increased cost savings, improved customer trust and enhanced system reliability. Introducing our Beneficial Impact Of IOT Security On Business set of slides. The topics discussed in these slides are Key Insights, Encryption, Application Security, Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Circle With 4 Quadrants Organization Security Allowance Business Operational Marketing Strategies
Circle With 4 Quadrants Organization Security Allowance Business Operational Marketing StrategiesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of ten slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Employee resign business services opportunity social security communication
Employee resign business services opportunity social security communicationIf you require a professional template with great design, then this Employee Resign Business Services Opportunity Social Security Communication is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using ten slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Security Business Analyst Work In Powerpoint And Google Slides Cpb
Security Business Analyst Work In Powerpoint And Google Slides CpbPresenting our Security Business Analyst Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Business Analyst Work This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secured Business Credit Card Personal Guarantee In Powerpoint And Google Slides Cpb
Secured Business Credit Card Personal Guarantee In Powerpoint And Google Slides CpbPresenting our Secured Business Credit Card Personal Guarantee In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secured Business Credit Card Personal Guarantee. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model
Role Of ZTNA To Improve Business Operations And Security Zero Trust Security ModelThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Deliver an outstanding presentation on the topic using this Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced User Experience, Remote Workforce Protection, Improve Data Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Define Security Token Project Business Model Security Token Offerings BCT SS
Define Security Token Project Business Model Security Token Offerings BCT SSThe following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. Present the topic in a bit more detail with this Define Security Token Project Business Model Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Project, Overview, Tokenization Model, Revenue Streams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Business Security System In Powerpoint And Google Slides Cpb
Best Business Security System In Powerpoint And Google Slides CpbPresenting our Best Business Security System In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Best Business Security System. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Business Security Camera System In Powerpoint And Google Slides Cpb
Best Business Security Camera System In Powerpoint And Google Slides CpbPresenting our Best Business Security Camera System In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Best Business Security Camera System This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches
Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data BreachesThis slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches. This template helps you present information on three stages. You can also present information on Strengthen Access Controls, Implement Continuous Monitoring, Implement Data Encryption, Continue Employee Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Security Software To Protect Business From Data Breach
Data Breach Prevention Security Software To Protect Business From Data BreachThe purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Security Software To Protect Business From Data Breach. This template helps you present information on three stages. You can also present information on Security Information And Event Management, Amends Permissions As Needed, Security Software To Protect Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Report Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Business Report Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Data Security Action Plan Checklist Icon is a vibrant and colourful PowerPoint icon that is perfect for illustrating data security action plans. It is a great visual aid to help explain the importance of data security and the steps needed to ensure it.
-
 Business Report Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Business Report Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Security Action Plan Checklist is perfect for presentations on data security and planning. It features a checklist to ensure all security measures are taken and provides a visual representation of the importance of data security.
-
 Importance Of Secure Web Gateway For Businesses Network Security Using Secure Web Gateway
Importance Of Secure Web Gateway For Businesses Network Security Using Secure Web GatewayThis slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Deliver an outstanding presentation on the topic using this Importance Of Secure Web Gateway For Businesses Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Businesses, Encapsulation, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Strong Network Security Foundation In Business Strategy
Building Strong Network Security Foundation In Business StrategyThis slide showcases different methods of network security. The main purpose of this slide is to keep clients data safely from getting hacked or getting in the hands of rivals. This includes strategies such as holistic approach, data monitoring, risk assessment, etc. Presenting our set of slides with Building Strong Network Security Foundation In Business Strategy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Holistic Approach, Risk Assessments.
-
 Agenda Delivering ICT Services For Enhanced Business Security Strategy SS V
Agenda Delivering ICT Services For Enhanced Business Security Strategy SS VIncrease audience engagement and knowledge by dispensing information using Agenda Delivering ICT Services For Enhanced Business Security Strategy SS V. This template helps you present information on five stages. You can also present information on Process And Retention Rate, Configuration Management, Effective Business Performance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V
Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security Delivering ICT Services For Enhanced Business Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Find And Track Devices, Operating System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Delivering ICT Services For Enhanced Business Security Table Of Contents Strategy SS V
Delivering ICT Services For Enhanced Business Security Table Of Contents Strategy SS VIncrease audience engagement and knowledge by dispensing information using Delivering ICT Services For Enhanced Business Security Table Of Contents Strategy SS V. This template helps you present information on one stages. You can also present information on ICT Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Delivering ICT Services For Enhanced Business Security Strategy SS V
Icons Slide Delivering ICT Services For Enhanced Business Security Strategy SS VIntroducing our well researched set of slides titled Icons Slide Delivering ICT Services For Enhanced Business Security Strategy SS V. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V
Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Deliver an outstanding presentation on the topic using this Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V. Dispense information and present a thorough explanation of Access Control Method, Description using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Commonly Types Of ICT Securities Used Delivering ICT Services For Enhanced Business Strategy SS V
Most Commonly Types Of ICT Securities Used Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Increase audience engagement and knowledge by dispensing information using Most Commonly Types Of ICT Securities Used Delivering ICT Services For Enhanced Business Strategy SS V. This template helps you present information on four stages. You can also present information on Network Security, Access Security, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V
Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Introducing Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats, Security Breaches, Virtual Private, using this template. Grab it now to reap its full benefits.




