Powerpoint Templates and Google slides for Business Security Implementation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V
Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Implementation Of Information Ict Business Security Kpi Dashboard Strategy SS V. Use it as a tool for discussion and navigation on Issues By Control Type, Standard Control Issues. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V
Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Ict Business Security Kpi Dashboard Strategy SS V Use it as a tool for discussion and navigation on Organisational Capability Framework, Performance Appraisal, Feedback System This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V
Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Present the topic in a bit more detail with this Strategic Plan To Implement Key Ict Security Measures Used By Businesses Strategy SS V Use it as a tool for discussion and navigation on Data Sets And Compliance, IT Service Planning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures
Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security MeasuresThis slide portrays the common types of fraud attacks experienced by ecommerce businesses in recent years. It include frauds such as card testing, phishing, account takeover and the reason of attacks. Deliver an outstanding presentation on the topic using this Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures
Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security MeasuresThis slide represents the impact of fraud attacks on ecommerce companies. It provide information about chargeback fee, high network fee, delayed expansion or investment. Deliver an outstanding presentation on the topic using this Ecommerce Fraud Impact On Business Operations Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Card Payment, Manage Fraud, Businesses Delay Investment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures
Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security MeasuresThis slide showcases financial challenges faced by the company related to cybersecurity attacks, referable for businesses facing similar situation. It cover losses caused due to lack of awareness about attacks. Present the topic in a bit more detail with this Financial Impact Of Ecommerce Fraud On Business Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Key Insights, Ecommerce Business, Key Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
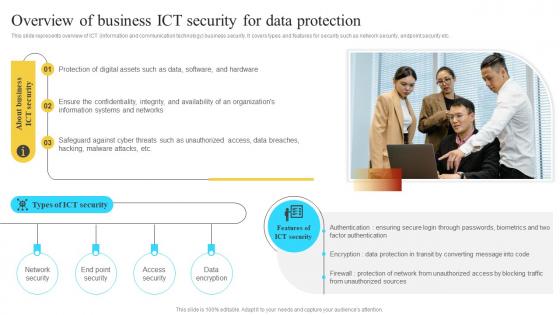 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Database Encryption Methods For Business Security
Encryption Implementation Strategies Database Encryption Methods For Business SecurityThis slide discusses the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources. The database encryption levels are application-level encryption, plug-in method, TDE, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Database Encryption Methods For Business Security. Use it as a tool for discussion and navigation on Database Encryption Methods, Business Security, Sales And Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment
Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E PaymentMentioned slide provides information about strategies which can be implemented by businesses before going cashless. It includes strategies such as determine customer preferences, select payment processor, offer payment options, implement CRM software. Present the topic in a bit more detail with this Strategies To Implement Cashless Payment In Business Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Determine Customer Preference, Select Payment Processor, Implement CRM Tool This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Major Impact Of Application Security On Business
Application Security Implementation Plan Major Impact Of Application Security On BusinessThis slide showcases the after application security impact on business along with factors that have improved the overall performance. Introducing Application Security Implementation Plan Major Impact Of Application Security On Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats Surge, Security Increase, Reduced Attacks On Applications, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat
Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about business cyber security attack recovery plan. It includes key steps such as setting time based recovery goals, impact and risk assessment, build recovery team, communication plan, recovery strategies implementation, etc. Introducing Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Communication Plan, Recovery Strategies Implementation, using this template. Grab it now to reap its full benefits.
-
 Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures
Business Survey Highlighting Challenges In Managing Implementing E Commerce Security MeasuresThis slide highlights common challenges that businesses face while managing ecommerce frauds. It include problems such as identifying fraud attacks, gap un fraud tool functionalities, lack of internal resources etc. Introducing Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Fraud Attacks, Updating Fraud Risk Model, Sufficient Internal Resources, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Email Security Implementation Impact On Businesses
Email Security Best Practices Email Security Implementation Impact On BusinessesThis slide illustrates the business impact of implementing email security policies. The parameters described in this slide are improved data protection, reduced phishing attacks, increased employee productivity, enhanced brand reputation, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Security Implementation Impact On Businesses. Use it as a tool for discussion and navigation on Improved Data Protection, Reduced Phishing Attacks, Increased Employee Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Benefits Of Implementing Web Security Solution
Business Benefits Of Implementing Web Security SolutionThis slide outlines the pros of web security in business which include safeguarding sensitive data, securing private information, etc. Introducing Business Benefits Of Implementing Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Sensitive Data, Secure Private Information, Prevent Costly Service Disruptions, using this template. Grab it now to reap its full benefits.
-
 ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS
ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SSThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc.Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Risk Categories, Control Review, Control Review Effectiveness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Facilities Offered By Implementation Of Security Centre Building Business Analytics Architecture
Facilities Offered By Implementation Of Security Centre Building Business Analytics ArchitectureThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Introducing Facilities Offered By Implementation Of Security Centre Building Business Analytics Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malware Detection And Investigation, Phishing Detection And Prevention, Investigations By HR, Risk Mitigation Of Left Employees, using this template. Grab it now to reap its full benefits.
-
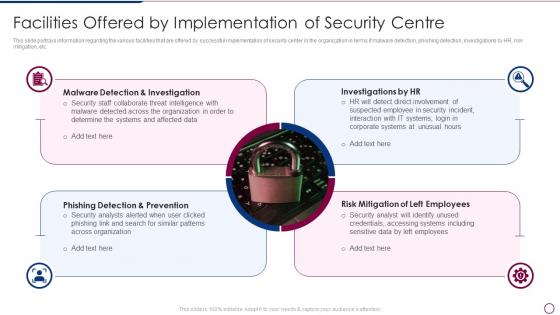 Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security Centre
Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security CentreThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security Centre. This template helps you present information on four stages. You can also present information on Investigation, Implementation, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist To Implement Cloud Security In Business Cloud Information Security
Checklist To Implement Cloud Security In Business Cloud Information SecurityThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.Introducing Checklist To Implement Cloud Security In Business Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Impact Analysis, Recovery Strategies, Plan Development using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business
Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In BusinessThis slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business. This template helps you present information on three stages. You can also present information on Monitor Data Activities, User Behavior, Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Checklist To Implement Cloud Security In Business
Cloud Computing Security Checklist To Implement Cloud Security In BusinessThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Cloud Computing Security Checklist To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Logging And Monitoring, Data Encryption, Backup And Data Recovery, Policies And Procedures, Networking, using this template. Grab it now to reap its full benefits.
-
 30 60 90 Days Plan To Implement Cloud Security In Business
30 60 90 Days Plan To Implement Cloud Security In BusinessThis slide defines the 30,60 and 90-days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. Introducing 30 60 90 Days Plan To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Data Access, Operations Performed, Cloud Services, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses
Implementation Steps Enable Data Security Crm System Implementation Guide For BusinessesThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Compliance, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot
Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Present the topic in a bit more detail with this Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot. Use it as a tool for discussion and navigation on Operations, Integrated, Workstation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business
Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping BusinessThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business. Use it as a tool for discussion and navigation on Strategy, Authentication, Appropriate Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Security Policy And Program Implementation
Business Security Policy And Program ImplementationThis slide covers business security policy and program implementation which includes business impact and effectiveness. Presenting our well structured Business Security Policy And Program Implementation. The topics discussed in this slide are Policy Program, Implementation, Business Impact. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Security Program Implementation With Review
Business Security Program Implementation With ReviewThis slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors. Presenting our set of slides with name Business Security Program Implementation With Review. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Program Review, Security Option, Control Assessment.
-
 Overview Of Business Email Compromise Attack Implementing Security Awareness Training
Overview Of Business Email Compromise Attack Implementing Security Awareness TrainingThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Increase audience engagement and knowledge by dispensing information using Overview Of Business Email Compromise Attack Implementing Security Awareness Training. This template helps you present information on four stages. You can also present information on Business, Compromise Attack, Risk Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Techniques To Successfully Prevent Business Implementing Security Awareness Training
Various Techniques To Successfully Prevent Business Implementing Security Awareness TrainingThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Implementing Security Awareness Training. This template helps you present information on one stage. You can also present information on Sender Policy Framework, Strong Process For Wire Transfers, Strong Password Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key ICT Security Measures Used By Businesses Implementation Of ICT Strategic Plan Strategy SS
Key ICT Security Measures Used By Businesses Implementation Of ICT Strategic Plan Strategy SSThis slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc.Present the topic in a bit more detail with this Key ICT Security Measures Used By Businesses Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Prevent Unauthorized, Information Breach, Business Disruption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS
Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SSThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc.Present the topic in a bit more detail with this Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Factor Authentication, Organizations Information, Ensure Confidentiality. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business
Firewall Implementation For Cyber Security Post Firewall Implementation Impact On BusinessThis slide represents the impact of firewall implementation on the organization. The purpose of this slide is to showcase the decline in various cyber security threats such as malware, worms, Daniel of Service, botnets, and phishing attacks. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business. Dispense information and present a thorough explanation of Post Firewall Implementation, Data Breaching Threats, Daniel Of Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business security implementation ppt powerpoint presentation pictures background cpb
Business security implementation ppt powerpoint presentation pictures background cpbPresenting this set of slides with name Business Security Implementation Ppt Powerpoint Presentation Pictures Background Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Business Security Implementation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 3 months business security service technology implementation roadmap
3 months business security service technology implementation roadmapPresenting 3 Months Business Security Service Technology Implementation Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 5 year business security service technology implementation roadmap
5 year business security service technology implementation roadmapPresenting 5 Year Business Security Service Technology Implementation Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 6 months business security service technology implementation roadmap
6 months business security service technology implementation roadmapPresenting 6 Months Business Security Service Technology Implementation Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Half yearly business security service technology implementation roadmap
Half yearly business security service technology implementation roadmapPresenting Half Yearly Business Security Service Technology Implementation Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Quarterly business security service technology implementation roadmap
Quarterly business security service technology implementation roadmapPresenting Quarterly Business Security Service Technology Implementation Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 30 60 90 days plan to implement cloud security in business cloud security it ppt grid
30 60 90 days plan to implement cloud security in business cloud security it ppt gridIntroducing 30 60 90 Days Plan To Implement Cloud Security In Business Cloud Security IT Ppt Grid to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, using this template. Grab it now to reap its full benefits.
-
 Checklist to implement cloud security in business cloud security it ppt tips
Checklist to implement cloud security in business cloud security it ppt tipsThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.Introducing Checklist To Implement Cloud Security In Business Cloud Security IT Ppt Tips to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Access Control, Logging And Monitoring, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Impact Of Implementing SaaS Security In Business
Impact Of Implementing SaaS Security In BusinessThis slide showcases the impact of software as a service SaaS security in developing business. This includes key elements such as scalability, security, customization, maintenance, availability, cost ,etc. Presenting our well structured Impact Of Implementing SaaS Security In Business. The topics discussed in this slide are Integrating Applications, Before Implement, Post Implement. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.



