Powerpoint Templates and Google slides for Best Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 File Integrity Monitoring Best Practices For Host And Container Security
File Integrity Monitoring Best Practices For Host And Container SecurityThis slide covers File Integrity Monitoring FIM best practices. The purpose of this template is to provide a structured approach to implementing FIM in host and container environments. It includes preparing asset inventory, detecting drift, and establishing protocols for notification, investigation, and response to security incidents. Presenting our set of slides with File Integrity Monitoring Best Practices For Host And Container Security This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Asset Inventory, Drift Detection, Investigation
-
 Best Practices For Healthcare IoT Security Impact Of IoT In Healthcare Industry IoT CD V
Best Practices For Healthcare IoT Security Impact Of IoT In Healthcare Industry IoT CD VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Deliver an outstanding presentation on the topic using this Best Practices For Healthcare IoT Security Impact Of IoT In Healthcare Industry IoT CD V. Dispense information and present a thorough explanation of Surface Visibility, Segregated Internal, Trust Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Managing ATP Cyber Security
Best Practices For Managing ATP Cyber SecurityThis slide covers the best practices for ATP cyber security. Its aim is to use the best practice available for anti threat protection for cyber security. This slide includes practices such as evaluation of security, training staff, choose effective solution, evaluate existing security, etc. Introducing our Best Practices For Managing ATP Cyber Security set of slides. The topics discussed in these slides are Assess Organisation Needs, Identify Vulnerabilities, Evaluate Existing Security, Choose Effective Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Best Practices Of Mobile Security
Key Best Practices Of Mobile SecurityThis slide depicts mobile security practices to protect devices and includes device protection passwords, install anti-malware software, avoid public wi-fi, and update software. Presenting our set of slides with name Key Best Practices Of Mobile Security. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Device Protection Passwords, Install Anti-Malware Software, Avoid Public Wi-Fi, Update Software.
-
 Best Practices For Security Gap In Network Business
Best Practices For Security Gap In Network BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with name Best Practices For Security Gap In Network Business. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prioritize Data Encryption, Regular Security Audits, Ensure Compliance.
-
 Best Practices For Accepting Card Payment Enhancing Transaction Security With E Payment
Best Practices For Accepting Card Payment Enhancing Transaction Security With E PaymentFollowing slide provides information about various best practices which can be followed while accepting card payments from customers. It includes various best practices such as confirm customer Id, provide payment receipt, provide contact information, customer feedback, and verification. Introducing Best Practices For Accepting Card Payment Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confirm Customer ID, Provide Payment Receipt, Provide Contact Information using this template. Grab it now to reap its full benefits.
-
 Best Practices For BNPL Payment Option Enhancing Transaction Security With E Payment
Best Practices For BNPL Payment Option Enhancing Transaction Security With E PaymentMentioned slide provides information best practices which can be implemented by businesses to enhance customer purchasing experience. It includes key practices such as select right solution, inform customers, collaborate BNPL to promotional activities, educate employee and trigger abandoned carts. Increase audience engagement and knowledge by dispensing information using Best Practices For BNPL Payment Option Enhancing Transaction Security With E Payment This template helps you present information on five stages. You can also present information on Right Solution, Inform Customers, Educate Employee using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices Of ACH Electronic Payment Enhancing Transaction Security With E Payment
Best Practices Of ACH Electronic Payment Enhancing Transaction Security With E PaymentFollowing slide provides information about various best practices that can be followed by businesses for preventing payment risks. It includes best practices such as segregate duties, prepare separate bank account, monitor payment, and protect banking information Introducing Best Practices Of ACH Electronic Payment Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Segregate Duties, Prepare Bank Account, Monitor Payment using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Leveraging Cryptocurrency Payment Enhancing Transaction Security With E Payment
Best Practices Of Leveraging Cryptocurrency Payment Enhancing Transaction Security With E PaymentFollowing slide provides information about various best practices which can be implemented by businesses to reduce business expenses. It includes best practices such as understand regulations, set up crypto wallet, enable payment at checkout process, and integrate crypto with accounting tools. Increase audience engagement and knowledge by dispensing information using Best Practices Of Leveraging Cryptocurrency Payment Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Understand Regulations, Enable Payment Checkout Process, Integrate Crypto, Accounting Tools using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices Of QR Code Implementation Enhancing Transaction Security With E Payment
Best Practices Of QR Code Implementation Enhancing Transaction Security With E PaymentMentioned slide provides information about best practices which can be implemented by businesses to increase sales. It includes best practices such as Include call to action, personalize QR code, check code scannability, update content regularly. Introducing Best Practices Of QR Code Implementation Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Include Call To Action, Personalize QR Code, Check Code Scannability using this template. Grab it now to reap its full benefits.
-
 Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E Payment
Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Enhancing Transaction Security With E Payment This template helps you present information on five stages. You can also present information on Enable Password, Secure Network Connection, Secure Login Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Prevent Cheque Payment Frauds Enhancing Transaction Security With E Payment
Best Practices To Prevent Cheque Payment Frauds Enhancing Transaction Security With E PaymentFollowing slide includes various practices that can be implemented by business to avoid cheque related frauds. It includes best practices such as safe storage, information fill out, positive pay services, reconciliation and segregate duties. Introducing Best Practices To Prevent Cheque Payment Frauds Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Safe Storage, Positive Pay Service, Reconciliation using this template. Grab it now to reap its full benefits.
-
 Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS V
Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Healthcare IoT Security Transforming Healthcare Industry Through Technology IoT SS V. This template helps you present information on two stages. You can also present information on Surface Visibility, Internal Networking, Trust Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS V
Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Deliver an outstanding presentation on the topic using this Best For Healthcare Iot Security Role Of Iot And Technology In Healthcare Industry IoT SS V. Dispense information and present a thorough explanation of Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Implementing Mobile Security
Best Practices For Implementing Mobile SecurityThis slide talks about the best practices for an organization to practice mobile security device which includes minimizing public wi-fi usage, public Wi-Fi, etc. Introducing our premium set of slides with name Best Practices For Implementing Mobile Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ensuring Robust Password Protection, Security Training And Education, Enforcing Transparent Policies. So download instantly and tailor it with your information.
-
 Best Practices For Mobile Security Framework
Best Practices For Mobile Security FrameworkThis slide talks about the best practices one should follow for securing mobile security framework which include multifactor authentication, security audits, etc. Presenting our set of slides with name Best Practices For Mobile Security Framework. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mobile Security Framework, Multifactor Authentication, Security Audits.
-
 Best Practices For Implementing Application Security
Best Practices For Implementing Application SecurityThis slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Implementing Application Security. This template helps you present information on five stages. You can also present information on Shift Security Left, Track Application Security Outcomes, Assess Threats, Application Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Log Management Best Practices Application Security
Security Log Management Best Practices Application SecurityThis slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc. Increase audience engagement and knowledge by dispensing information using Security Log Management Best Practices Application Security. This template helps you present information on five stages. You can also present information on Scrutinize Admin And Operators, Prevent Inappropriate Actions, Ensure Authorized Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SS
Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SSThis slide covers essential guidance on safeguarding blockchain data to ensure integrity and confidentiality such as keeping private key confidential, utilizing VPN, use of link checker, opting for trusted crypto wallets. Introducing Additional Blockchain Data Security Tips And Best Comprehensive Approach To Privacy BCT SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Private Key Confidential, Security, Blockchain, Prevent Phishing Attacks, using this template. Grab it now to reap its full benefits.
-
 Top Security Testing Best Practices Ppt Icon Graphics Pictures
Top Security Testing Best Practices Ppt Icon Graphics PicturesThis slide represents the security testing best practices such as thorough testing across development, vulnerability identification and resolution, etc. Introducing Top Security Testing Best Practices Ppt Icon Graphics Pictures to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Consistent Security Updates, Automation Tools Utilization, Vulnerability Identification And Resolution, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Information Security For Small Businesses
Best Practices Of Information Security For Small BusinessesThis slide highlights information security strategies for small enterprises. The purpose of this slide is to help managers in safeguarding users data from breaches and theft for building their reputation in the market. It includes elements such as employee training, backup, etc. Presenting our set of slides with Best Practices Of Information Security For Small Businesses. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Regular Updates, Network Security
-
 Best Practices For Email Domain Security
Best Practices For Email Domain SecurityThis slide is an overview of the best practices for email domain security which include secure email provider, strong, unique passwords and security audits. Introducing our premium set of slides with Best Practices For Email Domain Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Email Provider, Unique Passwords, Access Controls. So download instantly and tailor it with your information.
-
 Trending Email Security Best Practices
Trending Email Security Best PracticesThis slide outlines best practices followed in email security which includes use strong passwords, use proxies, regularly back up files and keep software updated. Presenting our set of slides with Trending Email Security Best Practices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Trending Email Security, Best Practices.
-
 Crypto Wallet Security And Best Practices
Crypto Wallet Security And Best PracticesThis slide outlines the crypto wallet security and best practices which include choose a secure wallet, use strong passwords, regular wallet backups, etc. Presenting our set of slides with name Crypto Wallet Security And Best Practices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Crypto Wallet, Security And Best Practices, Regular Wallet Backups.
-
 Endpoint Security Best Practices For Implementing Endpoint Security
Endpoint Security Best Practices For Implementing Endpoint SecurityThis slide discusses the best approaches for endpoint security deployment which include anti-phishing deployment, ransomware protection, etc. Introducing Endpoint Security Best Practices For Implementing Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Compliance, Improved Incident Detection, High Vulnerability To Malware, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Visualization Security In Business
Best Practices For Visualization Security In BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with Best Practices For Visualization Security In Business. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Trends, Ensure Compliance, Security Awareness.
-
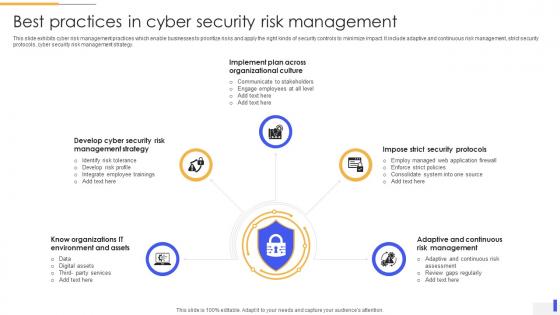 Best Practices In Cyber Security Risk Management
Best Practices In Cyber Security Risk ManagementThis slide exhibits cyber risk management practices which enable businesses to prioritize risks and apply the right kinds of security controls to minimize impact. It include adaptive and continuous risk management, strict security protocols, cyber security risk management strategy. Introducing our premium set of slides with Best Practices In Cyber Security Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Know Organizations IT Environment And Assets. Impose Strict Security Protocols, Adaptive And Continuous Risk Management . So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Best Practices For Tokenization In Data Security
Tokenization For Improved Data Security Best Practices For Tokenization In Data SecurityThe purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Increase audience engagement and knowledge by dispensing information using Tokenization For Improved Data Security Best Practices For Tokenization In Data Security. This template helps you present information on four stages. You can also present information on Effective Cybersecurity And Compliance, Broaden Data Tokenization Scope, Regularly Revise Tokenization Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Ensure Endpoint Cyber Security
Best Practices To Ensure Endpoint Cyber SecurityThis slide covers various approaches to secure computer networks and connected endpoints from potential cyber threats. The purpose of this slide is to help businesses in ensuring advanced security protection. It includes practices such as securing endpoints, employing strong password policy, practicing access control, etc. Presenting our well structured Best Practices To Ensure Endpoint Cyber Security The topics discussed in this slide are Secure Endpoints, Ensure Strong Password Policy, Practice Access Control This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Implementing Hids Cyber Security
Best Practices For Implementing Hids Cyber SecurityThis slide represents best practices for implementing HIDS cyber security which monitors IT systems for signs of suspicious activities and unusual behaviours. It includes best practices for implementing HIDS cyber security such as monitor all hosts, contextualize data, etc Introducing our premium set of slides with Best Practices For Implementing Hids Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitor All Hosts, Contextualize Data, Consider Agentless HIDS. So download instantly and tailor it with your information.
-
 Best Practices For Fintech Application Development Security
Best Practices For Fintech Application Development SecurityThe purpose of this slide is to protect users personal and financial data from vulnerabilities, including best practices such as security code, multi factor authentication, encryption, etc. Presenting our set of slides with Best Practices For Fintech Application Development Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Code, Quality Assurance, Multi Factor Authentication
-
 Best Practices For Gamification Cyber Security Training
Best Practices For Gamification Cyber Security TrainingThe purpose of this slide is to highlight gamified cybersecurity training for engaging staff and improving security practices by personalizing it to audience, making it relevant and accessible, and testing effectiveness. Presenting our set of slides with name Best Practices For Gamification Cyber Security Training. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Make Accessibility, Test Effectiveness, Tailor Training To Audience, Ensure Relevancy.
-
 Gamification Implementation In Cyber Security Recruitment Best Practices
Gamification Implementation In Cyber Security Recruitment Best PracticesThe purpose of this slide is to ensure that gamified components are consistent with organizations culture and values and create fun and competitive atmosphere for applicants including best practices such as aligning gamification with company culture and values, promoting diversity and inclusion, etc. Introducing our premium set of slides with name Gamification Implementation In Cyber Security Recruitment Best Practices. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Design Meaningful Challenges, Make Process Enjoyable, Promote Diversity And Inclusion, Cyber Security Recruitment. So download instantly and tailor it with your information.
-
 Best Cyber Deception Software ESET Endpoint Security
Best Cyber Deception Software ESET Endpoint SecurityThe purpose of this slide is to present ESET Endpoint Security as the best cyber deception software, offering advanced features for threat detection and mitigation. Presenting our set of slides with Best Cyber Deception Software ESET Endpoint Security. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encryption Software, Endpoint Management, Fraud Detection.
-
 Industry Expert Best Practices To Secure Startup Funding
Industry Expert Best Practices To Secure Startup FundingThe purpose of this slide is to showcase industry expert best practices to secure startup funding, offering insights and recommendations from experienced professionals. Elements include strategy, action plan, target audience, goal, etc. Present the topic in a bit more detail with this Industry Expert Best Practices To Secure Startup Funding. Use it as a tool for discussion and navigation on Strategy, Action Plan, Target Audience, Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Website Security Management Comprehensive E Commerce Website
Best Practices For Website Security Management Comprehensive E Commerce WebsiteThe following slide showcases best practices that can be used by businesses to protect websites from cyber-attacks and threats. It includes pointers such as incest in SSL certifications, anti-malware programs, regular backups, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Website Security Management Comprehensive E Commerce Website This template helps you present information on Four stages. You can also present information on Invest In SSL Certificate, Implement Anti Malware Programs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Physical Security Best Practices To Ensure Safety
Physical Security Best Practices To Ensure SafetyThis slide showcases best practices to maintain physical security. The practices covered are encryption, regular data backup and using passwords. Presenting our set of slides with Physical Security Best Practices To Ensure Safety. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encrypt Device, Backup Regularly, Use Passwords.
-
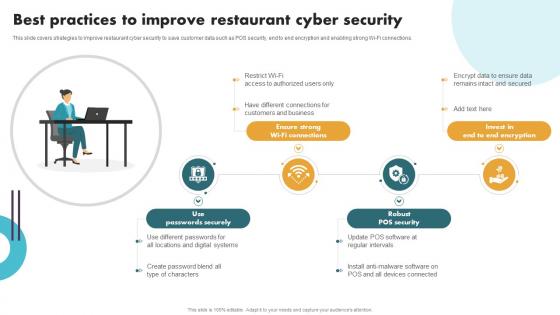 Securing Food Safety In Online Best Practices To Improve Restaurant Cyber Security
Securing Food Safety In Online Best Practices To Improve Restaurant Cyber SecurityThis slide covers strategies to improve restaurant cyber security to save customer data such as POS security, end to end encryption and enabling strong Wi-Fi connections. Introducing Securing Food Safety In Online Best Practices To Improve Restaurant Cyber Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Use Passwords Securely, Ensure Strong Wi-Fi Connections, Robust POS Security, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Blockchain Network Security
Best Practices For Blockchain Network SecurityThis slide discusses the best practices for blockchain network security which include comply with cyber security laws, prepare response plans, etc. Introducing our premium set of slides with Best Practices For Blockchain Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Comply Cybersecurity Laws, Rigorously Manage, Conduct Regular. So download instantly and tailor it with your information.
-
 Best Practices For Devops Security Automation
Best Practices For Devops Security AutomationThe slide highlights best practices for incorporating DevOps model into daily business operations, It include tips such as agile project management, automation, Continuous integration, security assessment etc. Presenting our set of slides with name Best Practices For Devops Security Automation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Container Orchestration Platforms, Implement App Security Testing, Define Security Metrics.
-
 Best Practices To Secure Blockchain Networks Using Devops
Best Practices To Secure Blockchain Networks Using DevopsThe slide highlights optimal strategies to secure blockchain networks using devOps. It cover points such as testing, automated deployment pipelines, immutable infrastructure, and patch management. Presenting our set of slides with name Best Practices To Secure Blockchain Networks Using Devops. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Patch Management, Network Security And Access Control, Immutable Infrastructure.
-
 Devops Security Best Practices For Saas Application
Devops Security Best Practices For Saas ApplicationThe slide outlines DevOps security strategies for SaaS application. It cover practices such as securing IT resources, deploying firewall, vulnerability assessment along with impact. Presenting our well structured Devops Security Best Practices For Saas Application. The topics discussed in this slide are Vulnerability Assessment, Strong Password Policy, Multi Factor Authentication. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Devops Security Best Practices To Mitigate Threat
Devops Security Best Practices To Mitigate ThreatThe slide represents release management best practices for DevOps. It cover strategies such as identifying success metrics, automate CD pipeline, maintaining staging environment, review launches etc. Presenting our set of slides with name Devops Security Best Practices To Mitigate Threat. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Secrets Management, Access Control, Microsoft Defender, Crowdstrike Falcon Horizon.
-
 Best Way Secure Passwords In Powerpoint And Google Slides Cpp
Best Way Secure Passwords In Powerpoint And Google Slides CppPresenting Best Way Secure Passwords In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Way Secure Passwords This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Best Practices To Ensure Customer Analytics Platform Security
Best Practices To Ensure Customer Analytics Platform SecurityThe below slide provides the use of various technologies to prevent cybersecurity attacks in customer data platforms. The different practices implemented are password authentication, data encryption, etc. Introducing our Best Practices To Ensure Customer Analytics Platform Security set of slides. The topics discussed in these slides are Password Authentication, Data Encryption, Platform SecurityThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Best Practices In Devops Icon
Security Best Practices In Devops IconIntroducing our premium set of slides with name Security Best Practices In Devops Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Best Practices, Devops Icon. So download instantly and tailor it with your information.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Enhance OT Cyber Security
Best Practices To Enhance OT Cyber SecurityThis slide represents various best practices that assist companies to enhance their cybersecurity of operational technology OT assets from cyber-risks. It includes best practices such as identifying OT assets, updating software, etc. Presenting our set of slides with Best Practices To Enhance OT Cyber Security This exhibits information on Two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify And Prioritize OT Assets, Update And Patch Software
-
 Best Practices For IAM Process Implementation Securing Systems With Identity
Best Practices For IAM Process Implementation Securing Systems With IdentityThis slide highlights the Identity and Access Management implementation best practices. The purpose of this slide is to discuss the steps involved these are aligning IT and business needs, shifting security methodology, creating policies and processes, etc. Present the topic in a bit more detail with this Best Practices For IAM Process Implementation Securing Systems With Identity Use it as a tool for discussion and navigation on Change Management, Create Policies And Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Ecommerce Security Measure
Best Practices For Ecommerce Security MeasureThis slide shows the various best practice adopt by ecommerce business to defend against the malicious attacks. The measures are regularly update softwares, deploy cyber security measures, etc. Introducing our premium set of slides with Best Practices For Ecommerce Security Measure. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regularly Update Softwares, Deploy Cyber Security Measures, Secure Network Management . So download instantly and tailor it with your information.
-
 Best Web Hosting Security Practices Web Hosting
Best Web Hosting Security Practices Web HostingThis slide highlights the best web hosting security practices which include SSL Encryption, SFTP Usage, application vigilance and password management. Introducing Best Web Hosting Security Practices Web Hosting to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Application Vigilance, Password Management, Security Practices using this template. Grab it now to reap its full benefits.
-
 Best Practices For Securing Web Hosting Servers
Best Practices For Securing Web Hosting ServersThis slide highlights the best practices for securing web hosting servers which include using web application firewall for blocking web attacks, opt for SFTP, etc. Introducing our premium set of slides with Best Practices For Securing Web Hosting Servers. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Deploy Antivirus Software, Malware Detection, Maintain Regular Backups. So download instantly and tailor it with your information.
-
 Best Practices To Implement NIDS For Maintaining Effective Cyber Security
Best Practices To Implement NIDS For Maintaining Effective Cyber SecurityThis Slide Represents Effective Strategies For Employing NIDS. It Aims To Help Organizations Implement NIDS To Detect, Respond And Mitigate Cyber Threats Within Networks. Introducing Our Premium Set Of Slides With Best Practices To Implement NIDS For Maintaining Effective Cyber Security. Ellicudate The Three Stages And Present Information Using This PPT Slide. This Is A Completely Adaptable Powerpoint Template Design That Can Be Used To Interpret Topics Like Proper Network Segmentation, Thorough Traffic Analysis, Signature Database Upgradation. So Download Instantly And Tailor It With Your Information.
-
 Best Strategies For Creating Security Awareness Mobile Security
Best Strategies For Creating Security Awareness Mobile SecurityThis slide represents the best strategies for creating culture of mobile security awareness which includes educate workforce on mobile security, etc. Increase audience engagement and knowledge by dispensing information using Best Strategies For Creating Security Awareness Mobile Security This template helps you present information on Five stages. You can also present information on Enable Authentication In App, Device Settings using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Security Best Practices Mobile Security
Mobile Device Security Best Practices Mobile SecurityThis slide highlights the best practices for mobile device security which includes enable user authentication, avoid public wi-fi and cloud backups. Increase audience engagement and knowledge by dispensing information using Mobile Device Security Best Practices Mobile Security This template helps you present information on Five stages. You can also present information on SAP Mobile Platform, End Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Software Update And Patch Management Best Practices Mobile Security
Software Update And Patch Management Best Practices Mobile SecurityThis slide gives an overview of best practices followed in software update and patch management which includes create asset inventory, patch management, etc. Introducing Software Update And Patch Management Best Practices Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Jailbreaking And Rooting using this template. Grab it now to reap its full benefits.
-
 Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology
Best Practices For Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide showcases the best methods for developing secure embedded systems. The purpose of this slide is to showcase the best practices for building secure embedded systems, and these are securing boot, securing enclaves with Trusted Execution Environments TEE, implementing FOTA, etc. Present the topic in a bit more detail with this Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating Systems In Market, Consumer Electronics, Industrial, Agriculture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Deployment Best Practices
Application Security Deployment Best PracticesThis slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Presenting our set of slides with Application Security Deployment Best Practices This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitor App Security Results, Manage Access Levels
-
 Best Practices To Optimise Fintech Cyber Security
Best Practices To Optimise Fintech Cyber SecurityThis slide showcases the best practices for fintech cyber security. Its aim is to follow the practices for maintaining a secure environment in fintech based companies. This slide includes authentication measure, protocol, storage and implement AI system. Introducing our premium set of slides with name Best Practices To Optimise Fintech Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Use Authentication Measures, Assess And Update Protocol, Secure Storage . So download instantly and tailor it with your information.
-
 Best Technology Strategies For Fintech Cyber Security
Best Technology Strategies For Fintech Cyber SecurityThis slide showcases the best technologies to choose for fintech security management. Its aim is to prioritise the resources and execute the best strategy. This slide includes governance, risk, crisis, service, threat, access, privacy, etc. Presenting our set of slides with name Best Technology Strategies For Fintech Cyber Security. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance Strategy, Emerging Trends, Risk Compliance, Crisis Management .





