Powerpoint Templates and Google slides for Attack
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Key Takeaways From Types Of Attacks In Blockchain Session Training Ppt
Key Takeaways From Types Of Attacks In Blockchain Session Training PptPresenting Key Takeaways from Types of Attacks in Blockchain Session. These slides are 100 Percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 DOS Attack Ppt Template Bundles
DOS Attack Ppt Template BundlesIf you require a professional template with great design, then this DOS Attack Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using sixteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard
Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking DashboardThis slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard. Dispense information and present a thorough explanation of Dashboard To Track, Cyber Phishing Attacks, Graphical Representation, Specific Time Span, Organizations Health Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age Infection Methods Utilized By Ransomware Attackers
Ransomware In Digital Age Infection Methods Utilized By Ransomware AttackersThis slide highlights the factors utilized by attackers to implement ransomware attacks, including exploiting vulnerabilities, launching brute-force credential attacks, and employing social engineering tactics. It also includes a visual representation depicting the distribution percentage of these attack vectors. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age Infection Methods Utilized By Ransomware Attackers. Dispense information and present a thorough explanation of Exploitable Vulnerabilities, Brute Force Credential Attacks, Previously Compromised Credentials, Ransomware Attackers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data security it cyber attacks experienced by company in previous financial year
Data security it cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver an outstanding presentation on the topic using this Data Security IT Cyber Attacks Experienced By Company In Previous Financial Year. Dispense information and present a thorough explanation of Cyber Attacks Experienced, FY2022, Comparatively using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
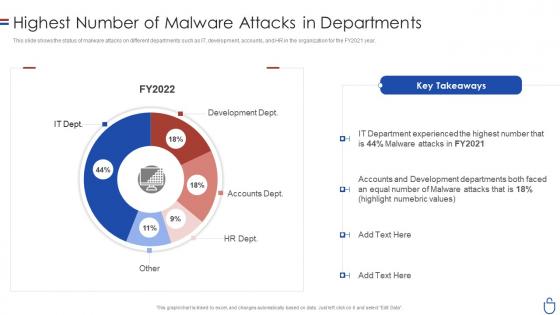 Data security it highest number of malware attacks in departments
Data security it highest number of malware attacks in departmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an outstanding presentation on the topic using this Data Security IT Highest Number Of Malware Attacks In Departments. Dispense information and present a thorough explanation of Development Dept, Accounts Dept, HR Dept using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security cyber attacks experienced by company in previous financial year
Computer system security cyber attacks experienced by company in previous financial yearThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Present the topic in a bit more detail with this Computer System Security Cyber Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks Experienced By Company In Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security highest number of malware attacks in departments
Computer system security highest number of malware attacks in departmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Present the topic in a bit more detail with this Computer System Security Highest Number Of Malware Attacks In Departments. Use it as a tool for discussion and navigation on Development Dept, Accounts Dept, HR Dept, Other, IT Dept. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention Potential Causes For Data Breach Attacks
Data Breach Prevention Potential Causes For Data Breach AttacksThis slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Potential Causes For Data Breach Attacks. This template helps you present information on eight stages. You can also present information on Unintentional Data Leakage, Keystrokes Recording, Password Guessing, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Faced By Organization Security Plan To Prevent Cyber
Cyber Attacks Faced By Organization Security Plan To Prevent CyberThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cyber Attacks Faced By Organization Security Plan To Prevent Cyber. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels
Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Dashboard For Tracking Cyber Attack Risk Levels. Use it as a tool for discussion and navigation on Infrastructure Controls, Preventive Controls, Detective Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents
Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Dashboard To Monitor Cyber Attack Incidents. Dispense information and present a thorough explanation of Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred
Security Plan To Prevent Cyber Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks, Phishing, Malware Attack, Denial Of Service, SQL Injections, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
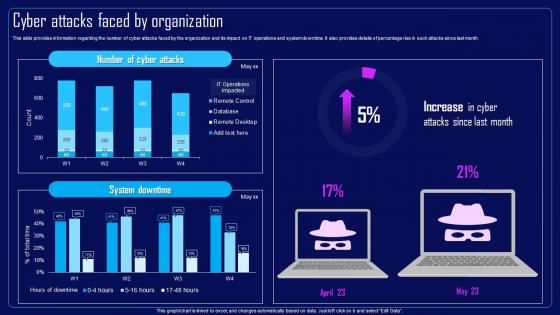 Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization
Action Plan To Combat Cyber Crimes Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks Faced By Organization, IT Operations And System Downtime, Remote Desktop using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
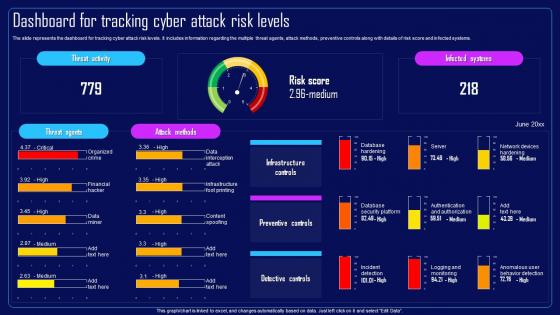 Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk Levels
Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Dashboard For Tracking, Cyber Attack Risk Levels, Risk Score And Infected Systems, Preventive Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
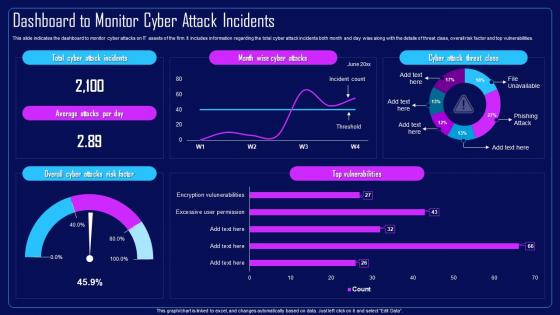 Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack Incidents
Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attacks, IT Assets Of The Firm, Risk Factor And Top Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
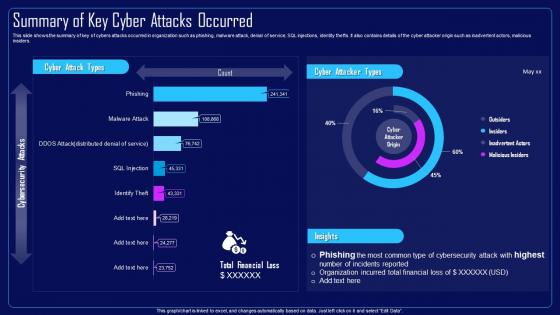 Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks Occurred
Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred In Organization, Malware Attack, Denial Of Service, SQL Injections, Inadvertent Actors, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Cyber Attacks Faced By Organization
Compressive Planning Guide Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Deliver an outstanding presentation on the topic using this Compressive Planning Guide Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks, IT Operations, System Downtime using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk Levels
Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Compressive Planning Guide Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Dashboard For Tracking, Cyber Attack Risk Levels, Preventive Controls, Risk Score And Infected Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Compressive Planning Guide Dashboard To Monitor Cyber Attack Incidents
Compressive Planning Guide Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Compressive Planning Guide Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attacks On IT Assets, Top Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Summary Of Key Cyber Attacks Occurred
Compressive Planning Guide Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Compressive Planning Guide Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cybers Attacks Occurred, Malware Attack, Denial Of Service, Inadvertent Actors, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption
Statistics Of Cloud Data Security Attacks In Organization Cloud Data EncryptionThis slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. Deliver an outstanding presentation on the topic using this Statistics Of Cloud Data Security Attacks In Organization Cloud Data Encryption. Dispense information and present a thorough explanation of Data Interception, Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secops V2 Malware Attacks On Different Departments Of Organization
Secops V2 Malware Attacks On Different Departments Of OrganizationThis slide depicts the total number of malware attacks on different departments in the organization. The purpose of this slide is to showcase the percentage of malware attacks on different business divisions, including development, HR, accounts, and IT department. Present the topic in a bit more detail with this Secops V2 Malware Attacks On Different Departments Of Organization. Use it as a tool for discussion and navigation on Malware Attacks, Development Departments, Accounts Departments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On Business
Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On BusinessThis slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On Business. Dispense information and present a thorough explanation of Analysis Of Phishing Attacks, Cyber Phishing Attacks, Malware Infections, Targets Of Phishing Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On Organizations
Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On OrganizationsThis slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On Organizations. This template helps you present information on four stages. You can also present information on Direct Financial Loss, Productivity Loss, Damaged Credibility, Phishing Cyber Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing AttacksThis slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks. Dispense information and present a thorough explanation of Phishing Scams, Phishing Attacks, Manufacturing, Food And Beverage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different BusinessesThis slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses. Use it as a tool for discussion and navigation on Attackers Conduct Scams, Vishing Technique, Internal Revenue Service Vishing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year
Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial YearThis slide depicts the financial loss experienced by the company in the last year due to different types of data privacy concerns. The purpose of this slide is to illustrate how increasing cyber scams have impacted the organization from april 2022 to april 2023. Present the topic in a bit more detail with this Encryption Implementation Strategies Cyber Attacks Impact On Organization In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Attacks, Financial Loss, Organization Experienced Loss, Data Privacy Concerns. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments
Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different DepartmentsThis slide summarizes data security attacks across different organizational departments, such as human resources, IT department, finance, marketing, operations, etc. The outlined attacks are phishing scams, malware infections, data breaches, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Overview Of Data Privacy Attacks In Different Departments. Use it as a tool for discussion and navigation on Human Resources, IT Department, Finance, Marketing, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS
IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight Internet of Things IoT password attack prevention measures. The techniques outlined in slide are limit public information, verifying the source, and no sharing of password. Deliver an outstanding presentation on the topic using this IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Information, Verify, Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS
Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT botnet attacks. Bruce force attack, Phishing, Device Bricking, and Cryptocurrency Mining are the most common types which are outlined in slide. Present the topic in a bit more detail with this Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Bricking, Mining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various types of ransomware attack which can cause financial loss to company. It covers information about Scareware, Screen Lockers, DDoS Distributed Denial of Service Extortion, Encrypting Ransomware, etc. Deliver an outstanding presentation on the topic using this Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Scareware, Lockers, Mobile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SS
Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display graphical representation of ransomware attack volume worldwide. Information covered in this slide is related to number of attack from 2015 2022 along with key intakes. Deliver an outstanding presentation on the topic using this Ransomware Attack Volume Across Globe Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Globe, Attacks, Developing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SS
Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display graphical representation of various IoT attacks faced by companies. The slide covers information about cyber attacks such as network scan, remote code execution, command injection, buffer overflow, worm, ransomware, botnet, password, phishing, etc. Present the topic in a bit more detail with this Statistics Highlighting IoT Attacks Faced Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Statistics, Injection, Execution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline multiple types of Denial of Service Dos attack. It covers information about application layer, buffer overflow, DNS Domain Name Server amplification, and ping of death. Deliver an outstanding presentation on the topic using this Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Application, Layer, Death using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate multiple types of Internet of Things IoT password attack. Phishing, Dictionary Attack, Credential Stuffing, and Keyloggers are the major attacks which are mentioned in slide. Present the topic in a bit more detail with this Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Dictionary, Credential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V
Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process
Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management ProcessThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Trends, Attacks Allowed By Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process
Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management ProcessThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such asphysical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Major Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware In Digital Age Best Practices To Prevent Ransomware Attacks
Ransomware In Digital Age Best Practices To Prevent Ransomware AttacksThis slide highlights the best practices to prevent ransomware attacks by performing certain security checks such as backup your data, keep all system and software updated . it also referring that how make your system secure. Present the topic in a bit more detail with this Ransomware In Digital Age Best Practices To Prevent Ransomware Attacks. Use it as a tool for discussion and navigation on Backup Your Data, Install Antivirus Software And Firewalls, Prevent Ransomware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware In Digital Age Global Ransomware Attack Analysis By Sector
Ransomware In Digital Age Global Ransomware Attack Analysis By SectorThis slide highlights the overview of the sectors that are highly susceptible to ransomware attacks. The purpose of this slide is to showcase the global ransomware attacks by industry, including government, technology, energy, transportation, finance, and various others. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age Global Ransomware Attack Analysis By Sector. Dispense information and present a thorough explanation of Global Ransomware Attack, Analysis By Sector, Transportation, Finance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Budget For Social Engineering Awareness Training
Social Engineering Attacks Prevention Budget For Social Engineering Awareness TrainingThis slide shows the cost breakup of social engineering awareness training program. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Deliver an outstanding presentation on the topic using this Social Engineering Attacks Prevention Budget For Social Engineering Awareness Training. Dispense information and present a thorough explanation of Social Engineering Awareness, Training Program, Training Components, Training Material Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Attacks Prevention Classification Of Social Engineering Attack Targets
Social Engineering Attacks Prevention Classification Of Social Engineering Attack TargetsThis slide outlines the various targets of social engineering scams. The major components include people with lack of knowledge, new employees, famous people, middle and senior management, bank system, vehicle systems, IT firms, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Attacks Prevention Classification Of Social Engineering Attack Targets. This template helps you present information on four stages. You can also present information on Targets Of Social Engineering Attacks, Organizations And Companies, Social Engineering Attack Targets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major Business
Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major BusinessThis slide depicts the statistics of social engineering scams in top IT players. The purpose of this slide is to outline the number of social engineering attacks happened in popular business firms, such as Microsoft, Facebook, WhatsApp, PayPal, Google, etc. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Social Engineering Attacks Experienced By Major Business. Use it as a tool for discussion and navigation on Social Engineering Attacks Experienced, Social Engineering Scams, Major Business Players. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Targeted Industries Of Social Engineering Attacks
Social Engineering Attacks Prevention Targeted Industries Of Social Engineering AttacksThis slide represents the statistics of most targeted industries of social engineering scams. The purpose of this slide is to outline the various sectors which are more prone to such attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Targeted Industries Of Social Engineering Attacks. Use it as a tool for discussion and navigation on Targeted Industries, Social Engineering Attacks, Manufacturing, Food And Beverage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks Prevention
Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks PreventionThis slide represents the statistics of different types of social engineering scams. The purpose of this slide is to outline the various social engineering attacks reported in last year, such as hacking attempts, malware, phishing, insider theft, watering hole, etc. Present the topic in a bit more detail with this Social Engineering Attacks Reported In Previous Financial Year Social Engineering Attacks Prevention. Use it as a tool for discussion and navigation on Social Engineering Attacks, Phishing, Insider Theft, Watering Hole. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Tracking Dashboard Social Engineering Attacks Prevention
Social Engineering Attacks Tracking Dashboard Social Engineering Attacks PreventionDeliver an outstanding presentation on the topic using this Social Engineering Attacks Tracking Dashboard Social Engineering Attacks Prevention. Dispense information and present a thorough explanation of Social Engineering Attacks, Tracking Dashboard, Organization Health Risk, Improvement Curve using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V
Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment
Cyber Attack Incident Tracking Dashboard Cyber Risk AssessmentThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack Incident, Tracking Dashboard This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment
Major Causes Of Cyber Crimes And Attacks Cyber Risk AssessmentThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Cyber Risk Assessment Use it as a tool for discussion and navigation on Major Reasons, Major Causes, Cyber Crimes And Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Tracking Dashboard Creating Cyber Security Awareness
Cyber Attack Incident Tracking Dashboard Creating Cyber Security AwarenessThe following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Infected Hosts, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Creating Cyber Security Awareness
Major Causes Of Cyber Crimes And Attacks Creating Cyber Security AwarenessThe following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Present the topic in a bit more detail with this Major Causes Of Cyber Crimes And Attacks Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Effective Software Testing Statistics Of Attacks On Existing It Infrastructure
Implementing Effective Software Testing Statistics Of Attacks On Existing It InfrastructureThis slide summarizes security attacks across different organizational departments, such as network operations centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Present the topic in a bit more detail with this Implementing Effective Software Testing Statistics Of Attacks On Existing It Infrastructure. Use it as a tool for discussion and navigation on Summarizes Security Attacks, Network Operations Centres, Security Operations Centres. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Prevented Attacks, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats
Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Cybersecurity Attacks In Education
Types Of Cybersecurity Attacks In EducationThis slide depicts the types of cybersecurity attacks in education. This slide aims to help education businesses adopt suitable measures to prevent cyberattacks. It includes a graphical analysis and key insights Introducing our Types Of Cybersecurity Attacks In Education set of slides. The topics discussed in these slides are Cyberattacks In Education, Education Is Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implementing Effective Tokenization Statistics Of Attacks On Existing It Infrastructure
Implementing Effective Tokenization Statistics Of Attacks On Existing It InfrastructureThis slide summarizes security attacks across different organizational departments such as healthcare, E-commerce platforms, financial services, etc. Deliver an outstanding presentation on the topic using this Implementing Effective Tokenization Statistics Of Attacks On Existing It Infrastructure. Dispense information and present a thorough explanation of Statistics Of Attacks, Existing IT Infrastructure, E Commerce Platforms, Financial Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





