Powerpoint Templates and Google slides for Asset Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Secure Your Digital Assets Steps To Follow For Creating A Crypto Wallet
Secure Your Digital Assets Steps To Follow For Creating A Crypto WalletThe purpose of this slide is to discuss the steps to follow while opening the crypto wallet. This slide highlights those steps, such as selecting the software app, downloading the wallet app, creating the account, transferring the assets, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Steps To Follow For Creating A Crypto Wallet. This template helps you present information on five stages. You can also present information on Crypto Wallet, Transferring The Assets, Downloading The Wallet App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Steps To Follow For Creating Crypto Wallet
Secure Your Digital Assets Steps To Follow For Creating Crypto WalletThe purpose of this slide is to discuss the steps to follow while opening the crypto wallet. This slide highlights those steps, such as selecting the software app, downloading the wallet app, creating the account, transferring the assets, etc. Introducing Secure Your Digital Assets Steps To Follow For Creating Crypto Wallet to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Crypto Wallet, Software App, Downloading The Wallet App, Transferring The Assets, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Techniques To Generate Money With Cryptocurrency
Secure Your Digital Assets Techniques To Generate Money With CryptocurrencyThe purpose of this slide is to outline the top ways of making money with cryptocurrency. This slide highlights the methods such as lending the cryptocurrency, mining, investing, trading, staking, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Techniques To Generate Money With Cryptocurrency. This template helps you present information on seven stages. You can also present information on Techniques To Generate Money, Mining, Investing, Trading, Staking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency Transactions
Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency TransactionsThis slide represents the ways we can track the transactions in the crypto market. Some essentials should be kept in mind before monitoring, such as tracking stored data with a public key is accessible, checking the senders and receivers addresses, etc. Introducing Secure Your Digital Assets Tracking Options For Monitoring Cryptocurrency Transactions to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cryptocurrency Transaction, Tracking Essentials, Timestamp, Public Blockchains, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Understanding Applications And Use Cases Of Cryptography
Secure Your Digital Assets Understanding Applications And Use Cases Of CryptographyThis slide represents the application of cryptography in the market. The purpose of this slide is to outline the implements such as computer passwords, digital currencies, secure web browsing, electronic signatures, authentications, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Understanding Applications And Use Cases Of Cryptography. This template helps you present information on six stages. You can also present information on Computer Passwords, Digital Currencies, Secure Web Browsing, Electronic Signatures, Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Use Cases Of Crypto Wallets In Market
Secure Your Digital Assets Use Cases Of Crypto Wallets In MarketThis slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc. Introducing Secure Your Digital Assets Use Cases Of Crypto Wallets In Market to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Merchant Payments, Boost Engagement And Personalization, Investment And Trading, Shared Savings And Pooling, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Various Financial Problems Solved By Cryptocurrency
Secure Your Digital Assets Various Financial Problems Solved By CryptocurrencyThis slide discusses various financial problems that are solved by cryptocurrency. This slide outlines issues such as making cross-border payments, serving non-bankers, saving on intermediation charges, remittance fees, etc. Introducing Secure Your Digital Assets Various Financial Problems Solved By Cryptocurrency to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Saving On Intermediation Charges, Preventing Identity Fraud, Making Cross Border Payments, Serving Non Bankers, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Ways Cryptocurrency Can Alter The Global Economy
Secure Your Digital Assets Ways Cryptocurrency Can Alter The Global EconomyThis slide showcases the ways cryptocurrency can alter the global economy. The purpose of this slide is to highlight different ways of altering the global economy such as reducing inflation, giving financial stability, security, creativity, etc. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Ways Cryptocurrency Can Alter The Global Economy. This template helps you present information on seven stages. You can also present information on Reduces Inflation, Financial Stability, Potential To Replace Financial System, Cryptocurrencies Became using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Secure Your Digital Assets With Crypto Wallets
Table Of Contents For Secure Your Digital Assets With Crypto WalletsIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Secure Your Digital Assets With Crypto Wallets. This template helps you present information on five stages. You can also present information on Roadmap Of Development Of Cryptocurrency, Crypto Wallet Market, Need For Crypto Wallets, Structures And Working using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets With Crypto Wallets For Table Of Content
Secure Your Digital Assets With Crypto Wallets For Table Of ContentDeliver an outstanding presentation on the topic using this Secure Your Digital Assets With Crypto Wallets For Table Of Content. Dispense information and present a thorough explanation of Ways Cryptocurrency Can Alter The Global, Various Financial Problems Solved, Cryptocurrency Transforming The World using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse Impact Of Cyber Attack On Valuable Assets Creating Cyber Security Awareness
Analyse Impact Of Cyber Attack On Valuable Assets Creating Cyber Security AwarenessThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Assets Creating Cyber Security Awareness Dispense information and present a thorough explanation of Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Classify Assets Vulnerable To Cyber Attack Creating Cyber Security Awareness
Classify Assets Vulnerable To Cyber Attack Creating Cyber Security AwarenessThe following slide depicts some major assets that are more prone to cyber-attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Introducing Classify Assets Vulnerable To Cyber Attack Creating Cyber Security Awareness to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Sales Record, Customer Database, Product Database using this template. Grab it now to reap its full benefits.
-
 Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS
Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SSThe following slide depicts details about security tokens to offer benefits to investors. It includes elements such as stocks, bonds, real world assets, improved liquidity, foster innovation, transparency, automated payments, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Blockchain Virtual Assets Security Tokens Managing Digital Wealth BCT SS This template helps you present information on Four stages. You can also present information on Improved Liquidity, Foster Innovation, Offers Transparency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Top Asset Tokenization Platforms Securitize Revolutionizing Investments With Asset BCT SS
Top Asset Tokenization Platforms Securitize Revolutionizing Investments With Asset BCT SSThe following slide illustrates brief introduction of securitize tokenization platform to allow easy primary and secondary market trading. It includes elements such as features, fee charged, supported platforms such as web, android, iPhone, etc. Present the topic in a bit more detail with this Top Asset Tokenization Platforms Securitize Revolutionizing Investments With Asset BCT SS. Use it as a tool for discussion and navigation on Platforms Supported, Monitor Security Lifecycle, Latest Investment Offerings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Top Asset Tokenization Platforms Securrency Revolutionizing Investments With Asset BCT SS
Top Asset Tokenization Platforms Securrency Revolutionizing Investments With Asset BCT SSThe following slide illustrates brief introduction of securrency tokenization platform to allow trading of physical assets with high security. It includes elements such as features, fee charged, illiquid assets, user identity, automated compliance, etc. Deliver an outstanding presentation on the topic using this Top Asset Tokenization Platforms Securrency Revolutionizing Investments With Asset BCT SS. Dispense information and present a thorough explanation of Ensures Secure User Identity, Offers High Efficiency At Low Costs, Automate Compliance Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Facility Security Icon For Asset Protection
Facility Security Icon For Asset ProtectionIntroducing our premium set of slides with name Facility Security Icon For Asset Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Facility Security, Icon For Asset Protection. So download instantly and tailor it with your information.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats
Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts some major assets that are more prone to cyber attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Sales Record, Customer Database, Product Database This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Asset Allocation Strategic Retirement Planning To Build Secure Future Fin SS
Asset Allocation Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows various asset allocation strategies which can be used by individuals while making investments in different types of assets. It includes strategies such as strategic, tactical, dynamic and risk based asset allocation. Increase audience engagement and knowledge by dispensing information using Asset Allocation Strategic Retirement Planning To Build Secure Future Fin SS. This template helps you present information on four stages. You can also present information on Strategic Asset Allocation, Tactical Asset Allocation, Dynamic Asset Allocation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Asset Backed Tokens Beginners Guide To Successfully Launch Security Token BCT SS V
Overview Of Asset Backed Tokens Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide illustrates brief introduction of asset backed tokens to build trust and gain fractional ownership along with its pros and cons. It includes elements such as stability, transparency, diversification, ambiguity, dependency, regulatory issues, etc. Present the topic in a bit more detail with this Overview Of Asset Backed Tokens Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Overview, Cons, Pros. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Policy Icon For Securing Digital Assets
Cyber Security Policy Icon For Securing Digital AssetsPresenting our set of slides with Cyber Security Policy Icon For Securing Digital Assets This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Policy Icon, Securing Digital Assets
-
 Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SS
Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SSThis slide covers key use cases of security tokens for real-world assets tokenization. It includes real estate tokenization, artwork ownership tokens, commodities tokenization, revenue-sharing agreements, etc. Increase audience engagement and knowledge by dispensing information using Crypto Tokens Unlocking Applications Of Security Tokens For Real World Assets BCT SS This template helps you present information on Five stages. You can also present information on Artwork Ownership Tokens, Revenue-Sharing Agreements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets
Tokenization For Improved Data Security Working Of Security Tokenization In Financial AssetsThis slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Introducing Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Working Of Security Tokenization, Financial Assets, Dividend Distribution, Security Token Classification, using this template. Grab it now to reap its full benefits.
-
 Cyber Security In Banking Icon To Protect Consumer Assets
Cyber Security In Banking Icon To Protect Consumer AssetsPresenting our set of slides with Cyber Security In Banking Icon To Protect Consumer Assets. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security In Banking, Icon To Protect, Consumer Assets.
-
 Securing Digital Asset Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Securing Digital Asset Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with our Network Security Technology Stack PowerPoint icon. This vibrant and eye-catching icon represents the layers of security technology used to protect networks from cyber threats. Perfect for presentations on cybersecurity, IT infrastructure, and network management. Grab your audiences attention and showcase your knowledge with this dynamic icon.
-
 Securing Digital Asset Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Securing Digital Asset Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the advanced network security technology stack. It features a sleek and modern design, making it the perfect addition to any presentation on network security. Use it to showcase the latest advancements in protecting your network and data from cyber threats.
-
 Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security
Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. Present the topic in a bit more detail with this Addressing Various Ways To Handle Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Periodic Risk Assessment, Individuals, Implement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security
Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Deliver an outstanding presentation on the topic using this Determine Sequence Phases For Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Exploitation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm Assets
Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm AssetsThis slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present the topic in a bit more detail with this Ensuring Effective Intellectual Property Security Defense Plan To Protect Firm Assets. Use it as a tool for discussion and navigation on Proprietary Information, Trademarks, Invention Agreements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace addressing asset security categorization
Cyber threat management workplace addressing asset security categorizationThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Addressing Asset Security Categorization. Dispense information and present a thorough explanation of Position, Ownership, Location, Security Categorization, Confidentiality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset components effective information security risk management process
Asset components effective information security risk management processFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost.Present the topic in a bit more detail with this Asset Components Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Impact Rating On Business, Criticality Rating, Failure Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security asset criticality of identified system components
Effective information security asset criticality of identified system componentsFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver an outstanding presentation on the topic using this Effective Information Security Asset Criticality Of Identified System Components. Dispense information and present a thorough explanation of Host Computers, Impact Rating, Business, Criticality Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing asset security managing critical threat vulnerabilities and security threats
Addressing asset security managing critical threat vulnerabilities and security threatsThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Introducing Addressing Asset Security Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ownership, Location, Confidentiality, Integrity, using this template. Grab it now to reap its full benefits.
-
 Addressing asset security categorization corporate security management
Addressing asset security categorization corporate security managementThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Corporate Security Management. Use it as a tool for discussion and navigation on Ownership, Location, Confidentiality, Integrity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Asset management information security ppt powerpoint presentation inspiration outfit cpb
Asset management information security ppt powerpoint presentation inspiration outfit cpbPresenting our Asset Management Information Security Ppt Powerpoint Presentation Inspiration Outfit Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Asset Management Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Criticality Assessment Of Identified Assets Information Security Program
Cybersecurity Criticality Assessment Of Identified Assets Information Security ProgramFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Present the topic in a bit more detail with this Cybersecurity Criticality Assessment Of Identified Assets Information Security Program. Use it as a tool for discussion and navigation on Criticality Assessment Of Identified Assets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Categorization Worksheet For Assets Owned Organization
Information Security Program Categorization Worksheet For Assets Owned OrganizationThis slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Information Security Program Categorization Worksheet For Assets Owned Organization. Use it as a tool for discussion and navigation on Categorization, Worksheet, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Asset Criticality Of Identified System
Risk Management Framework For Information Security Asset Criticality Of Identified SystemFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Risk Management Framework For Information Security Asset Criticality Of Identified System. Use it as a tool for discussion and navigation on Host Computers, Impact Rating, Criticality Rating, Failure Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber
Checklist For Effectively Managing Asset Security Risk Based Methodology To CyberFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Increase audience engagement and knowledge by dispensing information using Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on System Monitoring, Data Backup, Security Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach
Checklist For Effectively Managing Asset Security Introducing A Risk Based ApproachFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Introducing Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on System Monitoring, Virus Scanning, System Monitoring using this template. Grab it now to reap its full benefits.
-
 Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security
Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber SecurityFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Deliver an outstanding presentation on the topic using this Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Infrastructure Hardware, Routers And Switches, Server Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security
Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least.Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on System Redundancy, Incident Response Plan, Security Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical addressing asset security categorization
Threat management for organization critical addressing asset security categorizationThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Threat Management For Organization Critical Addressing Asset Security Categorization. Use it as a tool for discussion and navigation on Security Categorization, Confidentiality, Executive Laptop. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management addressing asset security categorization
Cyber security risk management addressing asset security categorizationThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Introducing Cyber Security Risk Management Addressing Asset Security Categorization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Position, Ownership, Location, Security Categorization, Integrity, Confidentiality, Availability, Value , using this template. Grab it now to reap its full benefits.
-
 Information Security And Iso 27001 It Asset Disposal Checklist
Information Security And Iso 27001 It Asset Disposal ChecklistThis slide displays IT asset disposal checklist. It includes information such as system requirement, its compliance and remarks. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 It Asset Disposal Checklist. Dispense information and present a thorough explanation of It Asset Disposal Checklist using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Asset Security Categorization Vulnerability Administration At Workplace
Addressing Asset Security Categorization Vulnerability Administration At WorkplaceThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Vulnerability Administration At Workplace. Use it as a tool for discussion and navigation on Location, Availability, Categorization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Line Credit Secured Assets Ppt Powerpoint Presentation Layouts Graphics Cpb
Line Credit Secured Assets Ppt Powerpoint Presentation Layouts Graphics CpbPresenting Line Credit Secured Assets Ppt Powerpoint Presentation Layouts Graphics Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Line Credit Secured Assets. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Introducing security at workplace to ensure assets safety building organizational security strategy plan
Introducing security at workplace to ensure assets safety building organizational security strategy planThis slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Introducing Introducing Security At Workplace To Ensure Assets Safety Building Organizational Security Strategy Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Organizational, Strategy, using this template. Grab it now to reap its full benefits.
-
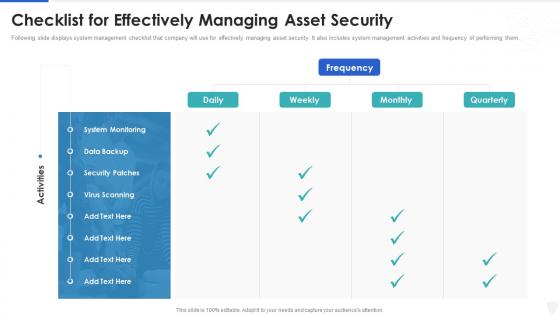 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Marketable Securities Assets Liabilities Ppt Powerpoint Presentation Styles Graphic Images Cpb
Marketable Securities Assets Liabilities Ppt Powerpoint Presentation Styles Graphic Images CpbPresenting Marketable Securities Assets Liabilities Ppt Powerpoint Presentation Styles Graphic Images Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Marketable Securities Assets Liabilities. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets
Incident Response Playbook Performing Cyber Training Exercises For Securing The AssetsPurpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets. This template helps you present information on four stages. You can also present information on Network Administrators, Security Controls, Mid Level Managers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Investment Securities Current Assets In Powerpoint And Google Slides Cpb
Investment Securities Current Assets In Powerpoint And Google Slides CpbPresenting our Investment Securities Current Assets In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Investment Securities Current Assets. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information Security
Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information SecurityThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets Deliver an outstanding presentation on the topic using this Analyzing The Impact On Assets Due To Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Revenue, Information, Importance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset Identification For Information Risk Assessment And Management Plan For Information Security
Asset Identification For Information Risk Assessment And Management Plan For Information SecurityThis slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack Deliver an outstanding presentation on the topic using this Asset Identification For Information Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Sales Records, Customers Database, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process Of Cyber Security Asset Management
Process Of Cyber Security Asset ManagementThe following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Introducing our premium set of slides with name Process Of Cyber Security Asset Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Asset Inventory, Synchronization, Response, Security Gaps. So download instantly and tailor it with your information.
-
 Roadmap Of Cyber Security Asset Assessment And Security Policy Development
Roadmap Of Cyber Security Asset Assessment And Security Policy DevelopmentThe following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Presenting our set of slides with name Roadmap Of Cyber Security Asset Assessment And Security Policy Development. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Audit, Awareness, Assessment, Build, Deployment.
-
 Security Asset In Powerpoint And Google Slides Cpb
Security Asset In Powerpoint And Google Slides CpbPresenting our Security Asset In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Security Asset This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
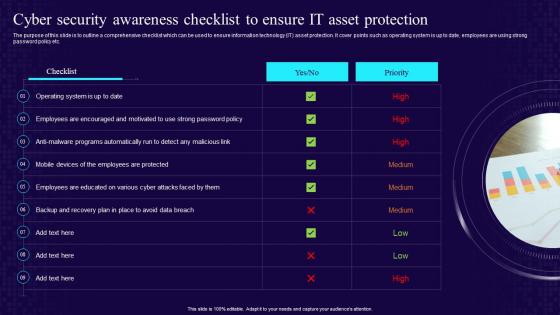 Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection
Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset ProtectionThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Awareness Checklist, IT Asset Protection, using this template. Grab it now to reap its full benefits.
-
 Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management
Analyzing The Impact On Assets Due To Information Breach Information Security Risk ManagementThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Present the topic in a bit more detail with this Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management. Use it as a tool for discussion and navigation on Impact On Revenue, Analyzing, Information Breach. This template is free to edit as deemed fit for your organization. Therefore download it now





