Powerpoint Templates and Google slides for Assault
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
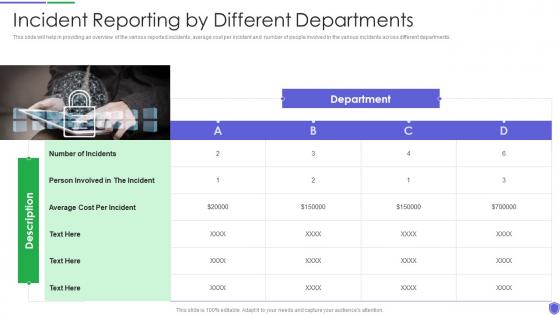 Incident reporting by different managing critical threat vulnerabilities and security threats
Incident reporting by different managing critical threat vulnerabilities and security threatsThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Increase audience engagement and knowledge by dispensing information using Incident Reporting By Different Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on one stages. You can also present information on Incident Reporting By Different Departments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key activities checklist associated to managing critical threat vulnerabilities and security threats
Key activities checklist associated to managing critical threat vulnerabilities and security threatsThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Introducing Key Activities Checklist Associated To Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Collect, Review And Analyze, Develop Strategic Framework, using this template. Grab it now to reap its full benefits.
-
 Managing critical threat vulnerabilities and security threats addressing various ways to handle
Managing critical threat vulnerabilities and security threats addressing various ways to handleThis slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. Increase audience engagement and knowledge by dispensing information using Managing Critical Threat Vulnerabilities And Security Threats Addressing Various Ways To Handle. This template helps you present information on four stages. You can also present information on Risk Assessment, End User, Networks And Individuals using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing critical threat vulnerabilities and security threats determine sequence phases
Managing critical threat vulnerabilities and security threats determine sequence phasesThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Managing Critical Threat Vulnerabilities And Security Threats Determine Sequence Phases to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Delivery, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Managing critical threat vulnerabilities and security threats table of contents
Managing critical threat vulnerabilities and security threats table of contentsIncrease audience engagement and knowledge by dispensing information using Managing Critical Threat Vulnerabilities And Security Threats Table Of Contents. This template helps you present information on four stages. You can also present information on Impact Assessment, Dashboard, Budget Assessment, Leveraging Workforce, Assets Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roles and responsibilities to managing critical threat vulnerabilities and security threats
Roles and responsibilities to managing critical threat vulnerabilities and security threatsThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Introducing Roles And Responsibilities To Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employee Responsibilities, Manager Responsibilities, Unit Responsibilities, Human Resources Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Selecting secured threat management managing critical threat vulnerabilities and security threats
Selecting secured threat management managing critical threat vulnerabilities and security threatsThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Security Incident, Automated Workflows, Access Rights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics associated to workplace managing critical threat vulnerabilities and security threats
Statistics associated to workplace managing critical threat vulnerabilities and security threatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Increase audience engagement and knowledge by dispensing information using Statistics Associated To Workplace Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on five stages. You can also present information on Cyber Attacks Cost, Organizations Face, Data Records using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table of contents managing critical threat vulnerabilities and security threats
Table of contents managing critical threat vulnerabilities and security threatsIntroducing Table Of Contents Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario Assessment, Digital Assets, Physical Security, using this template. Grab it now to reap its full benefits.
-
 Technological assessment of managing critical threat vulnerabilities and security threats
Technological assessment of managing critical threat vulnerabilities and security threatsThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Technological Assessment Of Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Industry Standard, Firms Standard, Customer Satisfaction Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management action managing critical threat vulnerabilities and security threats
Threat management action managing critical threat vulnerabilities and security threatsThe threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an outstanding presentation on the topic using this Threat Management Action Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Threat Identification, Threat Treatment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management action plan risk ppt powerpoint formates icons slides
Threat management action plan risk ppt powerpoint formates icons slidesThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Risk Ppt Powerpoint Formates Icons Slides. Use it as a tool for discussion and navigation on Risk Treated, Risk Rating, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various types of workplace violence managing critical threat vulnerabilities and security threats
Various types of workplace violence managing critical threat vulnerabilities and security threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Workplace Violence Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on six stages. You can also present information on Threatening Behavior Stalking, Physical Assault, Harassment And Intimidation, Property Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace employee assistance managing critical threat vulnerabilities and security threats
Workplace employee assistance managing critical threat vulnerabilities and security threatsThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Workplace Employee Assistance Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Clinical Services, Online Resources, Offline Resources, Employer Services, using this template. Grab it now to reap its full benefits.
-
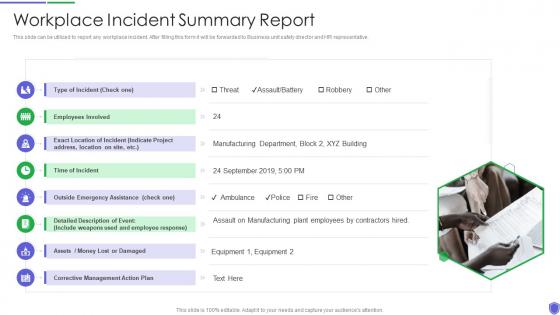 Workplace incident summary managing critical threat vulnerabilities and security threats
Workplace incident summary managing critical threat vulnerabilities and security threatsThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Increase audience engagement and knowledge by dispensing information using Workplace Incident Summary Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on one stages. You can also present information on Employees, Corrective Management, Time Of Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing cyber threats in various industries corporate security management
Addressing cyber threats in various industries corporate security managementThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an outstanding presentation on the topic using this Addressing Cyber Threats In Various Industries Corporate Security Management. Dispense information and present a thorough explanation of Healthcare, Manufacturing, Government, Industry using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing indicators associated to insider cyber threats corporate security management
Addressing indicators associated to insider cyber threats corporate security managementThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Increase audience engagement and knowledge by dispensing information using Addressing Indicators Associated To Insider Cyber Threats Corporate Security Management. This template helps you present information on three stages. You can also present information on Traits, Demeanor, Goals using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Addressing natural calamities posing threat to organization corporate security management
Addressing natural calamities posing threat to organization corporate security managementThis slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Present the topic in a bit more detail with this Addressing Natural Calamities Posing Threat To Organization Corporate Security Management. Use it as a tool for discussion and navigation on Threat Management Checklist. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing threat management team training schedule corporate security management
Addressing threat management team training schedule corporate security managementThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver an outstanding presentation on the topic using this Addressing Threat Management Team Training Schedule Corporate Security Management. Dispense information and present a thorough explanation of Hypotheticals, Benefits Of Exercise, Audience, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing various ways to handle insider cyber threats corporate security management
Addressing various ways to handle insider cyber threats corporate security managementThis slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Introducing Addressing Various Ways To Handle Insider Cyber Threats Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Management Policies, Implement Active Remediation, Investigate Remote Access Policies, Deactivate Orphaned User Accounts, using this template. Grab it now to reap its full benefits.
-
 Addressing ways to handling financial threats corporate security management
Addressing ways to handling financial threats corporate security managementThis slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Increase audience engagement and knowledge by dispensing information using Addressing Ways To Handling Financial Threats Corporate Security Management. This template helps you present information on five stages. You can also present information on Abundant Cash Requirement, Key Financial Statements, Overheads Analysis, Currency Hedging using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget for effective threat management at workplace corporate security management
Budget for effective threat management at workplace corporate security managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management At Workplace Corporate Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Information Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative assessment of various threat agents corporate security management
Comparative assessment of various threat agents corporate security managementThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Threat Agents Corporate Security Management. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency plan for cyber threat handling corporate security management
Contingency plan for cyber threat handling corporate security managementThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Increase audience engagement and knowledge by dispensing information using Contingency Plan For Cyber Threat Handling Corporate Security Management. This template helps you present information on one stages. You can also present information on Contingency Considerations, Contingency Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Corporate security management addressing various ways to handle insider cyber threats
Corporate security management addressing various ways to handle insider cyber threatsThis slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. Introducing Corporate Security Management Addressing Various Ways To Handle Insider Cyber Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Periodic Risk Assessment, Inform End User, Render Least, Networks And Individuals, using this template. Grab it now to reap its full benefits.
-
 Corporate security management determine sequence phases for threat attack
Corporate security management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Delivery, Exploitation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Corporate security management threat management action plan threat
Corporate security management threat management action plan threatThe threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Increase audience engagement and knowledge by dispensing information using Corporate Security Management Threat Management Action Plan Threat. This template helps you present information on two stages. You can also present information on Threat Identification, Threat Treatment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack actions corporate security management
Determine sequence phases for threat attack actions corporate security managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Actions Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Determine several threat actors profile corporate security management
Determine several threat actors profile corporate security managementThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Corporate Security Management. Use it as a tool for discussion and navigation on Determine Several Threat Actors Profile. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine threat management team structure corporate security management
Determine threat management team structure corporate security managementThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Increase audience engagement and knowledge by dispensing information using Determine Threat Management Team Structure Corporate Security Management. This template helps you present information on two stages. You can also present information on Legal Advisor, HR Advisor, Medical Advisor, Security Manager using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine threat scenario analysis corporate security management
Determine threat scenario analysis corporate security managementThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Corporate Security Management. Dispense information and present a thorough explanation of Command And Control, Actions And Objectives, Reconnaissance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different kinds of insider digital threats corporate security management
Different kinds of insider digital threats corporate security managementThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Introducing Different Kinds Of Insider Digital Threats Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Insider, Negligent Or Careless Insider, Third Party Insider, using this template. Grab it now to reap its full benefits.
-
 Impact analysis for effective threat management in corporate security management
Impact analysis for effective threat management in corporate security managementThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Corporate Security Management. Use it as a tool for discussion and navigation on Impact Analysis For Effective Threat Management In Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact analysis of successful threat management corporate security management
Impact analysis of successful threat management corporate security managementThis slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Introducing Impact Analysis Of Successful Threat Management Corporate Security Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Customer Satisfaction Rate, Incident Management, Risk Management, using this template. Grab it now to reap its full benefits.
-
 Selecting secured threat management software corporate security management
Selecting secured threat management software corporate security managementThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Software Corporate Security Management. Dispense information and present a thorough explanation of Information Security Prevention, API Integration, Automated Workflows using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management action plan risk corporate security management
Threat management action plan risk corporate security managementThe threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Threat Management Action Plan Risk Corporate Security Management. Use it as a tool for discussion and navigation on Threat Management Action Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various types of workplace violence and threats corporate security management
Various types of workplace violence and threats corporate security managementThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Workplace Violence And Threats Corporate Security Management. This template helps you present information on six stages. You can also present information on Threatening Behavior, Physical Assault, Property Damage, Harassment And Intimidation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Physical security threats ppt powerpoint presentation outline templates cpb
Physical security threats ppt powerpoint presentation outline templates cpbPresenting Physical Security Threats Ppt Powerpoint Presentation Outline Templates Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Physical Security Threats. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat drivers and emerging managing cyber risk in a digital age
Threat drivers and emerging managing cyber risk in a digital ageMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Introducing Threat Drivers And Emerging Managing Cyber Risk In A Digital Age to increase your presentation threshold. Encompassed with threee stages, this template is a great option to educate and entice your audience. Dispence information on Internet Of Things, Artificial Intelligence, Human Machine Interface, using this template. Grab it now to reap its full benefits.
-
 Threat vulnerability asset matrix managing cyber risk in a digital age
Threat vulnerability asset matrix managing cyber risk in a digital ageMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Threat Vulnerability Asset Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ai based automation of cyber threat security controls
Ai based automation of cyber threat security controlsThe following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Introducing our AI Based Automation Of Cyber Threat Security Controls set of slides. The topics discussed in these slides are Cyber Threat Security, Automated Control Management, Control And Vulnerability Reporting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison of cyber threat security vendors with pricing and use case
Comparison of cyber threat security vendors with pricing and use caseMentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Presenting our well structured Comparison Of Cyber Threat Security Vendors With Pricing And Use Case. The topics discussed in this slide are Financial Services, Cyber Security, Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber security risk management framework for threat protection
Cyber security risk management framework for threat protectionThis slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting our set of slides with Cyber Security Risk Management Framework For Threat Protection. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Governance, Security Assessment, Independent Audit.
-
 Cyber security threat management system
Cyber security threat management systemThe following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Introducing our Cyber Security Threat Management System set of slides. The topics discussed in these slides are Threat Containment And Remediation, Identify Management, Application Visibility And Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat approaches for security protection
Cyber threat approaches for security protectionThe following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Presenting our well structured Cyber Threat Approaches For Security Protection. The topics discussed in this slide are Cybersecurity Threat, Social Engineering, Traditional Approach. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat hunting program with process and tools
Cyber threat hunting program with process and toolsThe following slide highlights the cyber threat hunting program including people, process and with four different levels to minimize risks and threats. Introducing our Cyber Threat Hunting Program With Process And Tools set of slides. The topics discussed in these slides are Cyber Threat Hunting, Cyber Security Tool, Cyber Threat Training. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat icon indicating malware attack
Cyber threat icon indicating malware attackIntroducing our premium set of slides with Cyber Threat Icon Indicating Malware Attack. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Icon Indicating Malware Attack. So download instantly and tailor it with your information.
-
 Cyber threat intelligence services for enterprise security
Cyber threat intelligence services for enterprise securityThis slide highlights the services of cyber threat intelligence with incident management, cyber analytics, and vulnerability management and infrastructure management. Presenting our set of slides with Cyber Threat Intelligence Services For Enterprise Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure Management, Vulnerability Management, Cyber Analytics.
-
 Cyber threat report with risk indicator and affected systems
Cyber threat report with risk indicator and affected systemsPresenting our well structured Cyber Threat Report With Risk Indicator And Affected Systems. The topics discussed in this slide are Risk Level, Risk Indication, Potential Affected Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security company users and protection
Cyber threat security company users and protectionThe following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Introducing our Cyber Threat Security Company Users And Protection set of slides. The topics discussed in these slides are Pricing, Company, Users. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security icon to capture sensitive information
Cyber threat security icon to capture sensitive informationIntroducing our premium set of slides with Cyber Threat Security Icon To Capture Sensitive Information. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Security Icon To Capture Sensitive Information. So download instantly and tailor it with your information.
-
 Cyber threat security maturity model with protection levels
Cyber threat security maturity model with protection levelsThe following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Presenting our well structured Cyber Threat Security Maturity Model With Protection Levels. The topics discussed in this slide are Security Management Technology, Threat Management Platform, Threat Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Cyber threat security planning with educate and retest stage
Cyber threat security planning with educate and retest stageThe following slide highlights the cyber threat security planning to minimize threats in organizations. It include six stages to deploy cyber threat to organization. Introducing our premium set of slides with Cyber Threat Security Planning With Educate And Retest Stage. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Deploy, Retest, Educate. So download instantly and tailor it with your information.
-
 Cyber threat strategies for security protection
Cyber threat strategies for security protectionThis slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Presenting our set of slides with Cyber Threat Strategies For Security Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Program, Software Protocols, End Point Protection.
-
 Key cyber security threat to organizations
Key cyber security threat to organizationsThis slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Introducing our premium set of slides with Key Cyber Security Threat To Organizations. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Malware, Phishing, SQL Injection. So download instantly and tailor it with your information.
-
 Roadmap for developing cyber threat program
Roadmap for developing cyber threat programThe following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Presenting our set of slides with Roadmap For Developing Cyber Threat Program. This exhibits information on nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement And Integrate, Risk Assessment, Identify Vulnerabilities.
-
 Validated online lifecycle threat ppt powerpoint presentation inspiration portfolio cpb
Validated online lifecycle threat ppt powerpoint presentation inspiration portfolio cpbPresenting our Validated Online Lifecycle Threat Ppt Powerpoint Presentation Inspiration Portfolio Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Validated Online Lifecycle Threat. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Weakness threat difference ppt powerpoint presentation layouts ideas cpb
Weakness threat difference ppt powerpoint presentation layouts ideas cpbPresenting our Weakness Threat Difference Ppt Powerpoint Presentation Layouts Ideas Cpb PowerPoint template design. This PowerPoint slide showcases nine stages. It is useful to share insightful information on Weakness Threat Difference . This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.





