Powerpoint Templates and Google slides for Arcs
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Types Of Architecture For Launching Brand Strategy For Increasing Company Presence MKT SS V
Types Of Architecture For Launching Brand Strategy For Increasing Company Presence MKT SS VThis slide showcases architecture which can help to launch new brand and organize them internally. It showcases two types of brand architecture that are branded house and house of brands for new product launch and gain market share Deliver an outstanding presentation on the topic using this Types Of Architecture For Launching Brand Strategy For Increasing Company Presence MKT SS V. Dispense information and present a thorough explanation of Architecture, Products, Marketing Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Architecture Water House Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Architecture Water House Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts a house with a water droplet in front of it, representing the importance of water conservation. It is perfect for presentations on sustainability and the environment.
-
 Architecture Water House Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Architecture Water House Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon depicts a house with a water droplet on its roof. It is perfect for presentations on topics such as water conservation, climate change, and sustainability. It is a great visual to emphasize the importance of protecting our planet.
-
 Firewall As A Service Fwaas Architecture Of Firewall As A Service Fwaas Technology
Firewall As A Service Fwaas Architecture Of Firewall As A Service Fwaas TechnologyThis slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Present the topic in a bit more detail with this Firewall As A Service Fwaas Architecture Of Firewall As A Service Fwaas Technology. Use it as a tool for discussion and navigation on Architecture Of Fwaas, Network Traffic Flow, External An External Firewall, Advanced WAF. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology
Firewall As A Service Fwaas Working And Architecture Of Firewall Security TechnologyThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Present the topic in a bit more detail with this Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology. Use it as a tool for discussion and navigation on Operator Workstation, Administrator Workstation, Control Systems, Data Acquisition, Internal Databases And Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Database Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Database Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of a cloud database. It is designed to help you easily identify and access your cloud-based data storage. It is a great way to store and manage your data securely and efficiently.
-
 Cloud Database Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Database Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a perfect visual representation of a cloud database. It is a simple, yet powerful design that conveys the concept of data storage in the cloud. It is a great choice for presentations and other projects.
-
 Cloud Based IoT Waste Management Architecture
Cloud Based IoT Waste Management ArchitectureThe below slide explains the cloud based IoT waste management infrastructure that helps to collect and analyze the data on different waste. The different steps involved are GPS data collection, waste management application, cloud internet, etc. Introducing our Cloud Based IoT Waste Management Architecture set of slides. The topics discussed in these slides are Cloud Internet, Cite Cloud. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Vehicle Tracking System Architecture In Powerpoint And Google Slides Cpb
Vehicle Tracking System Architecture In Powerpoint And Google Slides CpbPresenting Vehicle Tracking System Architecture In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vehicle Tracking System Architecture. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Scrum Development Task Board Architecture
Scrum Development Task Board ArchitectureThis slide outlines the scrum task board tool that helps to visualize all the items in sprint backlog. It includes key structure of task board such as backlog, to do, in progress, review and done. Presenting our well structured Scrum Development Task Board Architecture. The topics discussed in this slide are Translate Landing Page, Identify Business Users.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Scale Acceleration Architecture In Powerpoint And Google Slides Cpb
Cloud Scale Acceleration Architecture In Powerpoint And Google Slides CpbPresenting our Cloud Scale Acceleration Architecture In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cloud Scale Acceleration Architecture. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 IOT Ecosystems Architecture Framework For Smart Agriculture Impact Of IOT On Various Industries IOT SS
IOT Ecosystems Architecture Framework For Smart Agriculture Impact Of IOT On Various Industries IOT SSThis slide presents the framework model for applying IoT techniques to an smart agriculture ecosystem. It includes significant phases such as real time monitoring, sensor and communication technology, networking, and data processing. Present the topic in a bit more detail with this IOT Ecosystems Architecture Framework For Smart Agriculture Impact Of IOT On Various Industries IOT SS. Use it as a tool for discussion and navigation on Real Time Monitoring, Sensors And Communication, Networking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Customer Billing System Architecture Framework Automation For Customer Database
Customer Billing System Architecture Framework Automation For Customer DatabaseFollowing slide highlights structure of billing system that helps to understand working process of network. It includes system components such as billing engine, rating engine, discount procedure, credit control etc.Present the topic in a bit more detail with this Customer Billing System Architecture Framework Automation For Customer Database. Use it as a tool for discussion and navigation on Discount Procedure, Credit Control, Report Generation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Big Data Analysis Architecture For Traditional Database System
Big Data Analysis Architecture For Traditional Database SystemThis slide represents architecture of big data analysis for traditional database systems. It further includes Data sources, data storage, batch processing, real time message ingestion, stream processing, analytical data store, analysis and reporting, etc. Introducing our Big Data Analysis Architecture For Traditional Database System set of slides. The topics discussed in these slides are Data Sources, Data Storage, Batch Processing, Stream Processing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Components Of Edge Analytics In Iot Architecture
Components Of Edge Analytics In Iot ArchitectureThis slide covers the components of edge analytics in the IoT edge architecture. This template aims to highlight the key components involved in edge analytics and roles in enabling real time data analysis at the edge. It includes sensors, actuators, smart devices, smart gateways, and edge analytics software.Presenting our well structured Components Of Edge Analytics In Iot Architecture. The topics discussed in this slide are Smart Gateways, Smart Devices, Edge Storage. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Architecture Of Healthcare IOT Framework Impact Of IOT On Various Industries IOT SS
Architecture Of Healthcare IOT Framework Impact Of IOT On Various Industries IOT SSThis slide presents the framework model for the implementation of IoT in healthcare architecture. It includes sensor patches, wearable applications, networks, cloud storage, physicians, medical researchers, health insurance companies, etc. Present the topic in a bit more detail with this Architecture Of Healthcare IOT Framework Impact Of IOT On Various Industries IOT SS. Use it as a tool for discussion and navigation on Publisher, Cloud Storage, Network, Subscriber. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architecture Bricks Wall Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Architecture Bricks Wall Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for adding visual interest to presentations. It features a brick wall design in a variety of bright colours, making it a great way to draw attention and add a unique touch to any presentation.
-
 Architecture Bricks Wall Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Architecture Bricks Wall Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a perfect way to add visual interest to your presentation. It features a single, solid-colored brick wall with a subtle texture and a realistic 3D effect. The icon is easy to use and can be quickly inserted into your slides to bring a unique and eye-catching look to your presentation.
-
 As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model
As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Present the topic in a bit more detail with this As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Based Approach Of ZTNA Architecture Zero Trust Security Model
Client Based Approach Of ZTNA Architecture Zero Trust Security ModelThis slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Present the topic in a bit more detail with this Client Based Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Process, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 External Components Of Zero Trust Network Architecture Zero Trust Security Model
External Components Of Zero Trust Network Architecture Zero Trust Security ModelThis slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Deliver an outstanding presentation on the topic using this External Components Of Zero Trust Network Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Documentation, Potential using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model
F1585 Zero Trust Network Access Architectural Models Zero Trust Security ModelThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Architectural, Resources, Verification, using this template. Grab it now to reap its full benefits.
-
 F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model
F1586 Zero Trust Network Access Architecture Overview Zero Trust Security ModelThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Present the topic in a bit more detail with this F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model. Use it as a tool for discussion and navigation on Resources, Architecture, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Logical Components Of Zero Trust Architecture Zero Trust Security Model
Logical Components Of Zero Trust Architecture Zero Trust Security ModelThis slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Deliver an outstanding presentation on the topic using this Logical Components Of Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Components, Architecture, Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Other ZTNA Architecture Deployment Approaches Zero Trust Security Model
Other ZTNA Architecture Deployment Approaches Zero Trust Security ModelThis slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Deliver an outstanding presentation on the topic using this Other ZTNA Architecture Deployment Approaches Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced Identity Governance, Micro Segmentation, Software Defined Network Perimeters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security Model
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security ModelThis slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Deliver an outstanding presentation on the topic using this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Approach, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present the topic in a bit more detail with this Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model
Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security ModelThis slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Implementation, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap
Confidential Cloud Computing Confidential Computing Architecture Implementation RoadmapThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Architecture Vs Database Introduction To Blockchain Technology BCT SS
Blockchain Architecture Vs Database Introduction To Blockchain Technology BCT SSDeliver an outstanding presentation on the topic using this Blockchain Architecture Vs Database Introduction To Blockchain Technology BCT SS. Dispense information and present a thorough explanation of Operations, Strength, Mutability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SS
Introduction To Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers a brief overview of the hybrid blockchain structure. It also includes major advantages such as resilient to attack, scalable, cost effective, and flexibility, and disadvantages such as lack of incentives, limited transparency, and more complex. Introducing Introduction To Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Flexible, Specific, Public, using this template. Grab it now to reap its full benefits.
-
 Introduction To Private Blockchain Architecture Introduction To Blockchain Technology BCT SS
Introduction To Private Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers a brief overview of the private blockchain structure. It also includes major advantages such as faster transactions, and higher security, and disadvantages such as trust concerns and high vulnerability. Increase audience engagement and knowledge by dispensing information using Introduction To Private Blockchain Architecture Introduction To Blockchain Technology BCT SS. This template helps you present information on two stages. You can also present information on Transactions, Network, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Public Blockchain Architecture Introduction To Blockchain Technology BCT SS
Introduction To Public Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers a brief overview of the public blockchain structure. It also includes major advantages such as decentralization and transparency and disadvantages such as slow network speed and risk of attacks. Deliver an outstanding presentation on the topic using this Introduction To Public Blockchain Architecture Introduction To Blockchain Technology BCT SS. Dispense information and present a thorough explanation of Transparency, Accountability, Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Types Of Blockchain Architectures Introduction To Blockchain Technology BCT SS
Major Types Of Blockchain Architectures Introduction To Blockchain Technology BCT SSThis slide covers the four major categories of blockchain structures such as public, private, consortium, and hybrid. It also includes the difference in each model on the basis of accessibility, suitability, and examples. Present the topic in a bit more detail with this Major Types Of Blockchain Architectures Introduction To Blockchain Technology BCT SS. Use it as a tool for discussion and navigation on Accessibility, Suitability, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Cases Of Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SS
Use Cases Of Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers major use cases of hybrid blockchain structure. It includes areas of implementation such as financial services, supply chain management, healthcare, and voting. Introducing Use Cases Of Hybrid Blockchain Architecture Introduction To Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial, Management, Healthcare, using this template. Grab it now to reap its full benefits.
-
 Use Cases Of Private Blockchain Architecture Introduction To Blockchain Technology BCT SS
Use Cases Of Private Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers major use cases of private blockchain structure. It includes areas of implementation such as internal auditing, voting, assessment management and logistics management. Increase audience engagement and knowledge by dispensing information using Use Cases Of Private Blockchain Architecture Introduction To Blockchain Technology BCT SS. This template helps you present information on four stages. You can also present information on Internal, Voting, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Public Blockchain Architecture Introduction To Blockchain Technology BCT SS
Use Cases Of Public Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers major use cases of the public blockchain framework. It includes use cases such as displacing traditional financial systems and decentralized finance. Introducing Use Cases Of Public Blockchain Architecture Introduction To Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Traditional, Financial, Supporting, using this template. Grab it now to reap its full benefits.
-
 Uses Cases Of Consortium Blockchain Architecture Introduction To Blockchain Technology BCT SS
Uses Cases Of Consortium Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers major use cases of consortium blockchain structure. It includes areas of implementation such as logistics, insurance and healthcare, banking and finance, and open source platforms. Increase audience engagement and knowledge by dispensing information using Uses Cases Of Consortium Blockchain Architecture Introduction To Blockchain Technology BCT SS. This template helps you present information on four stages. You can also present information on Logistics, Banking, Finance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What Is Blockchain Architecture Introduction To Blockchain Technology BCT SS
What Is Blockchain Architecture Introduction To Blockchain Technology BCT SSThis slide covers a brief introduction to blockchain architecture. It also includes major components of blockchain structure such as nodes, transaction, block, chain and miners. Introducing What Is Blockchain Architecture Introduction To Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Transaction, Performing, Organizes, using this template. Grab it now to reap its full benefits.
-
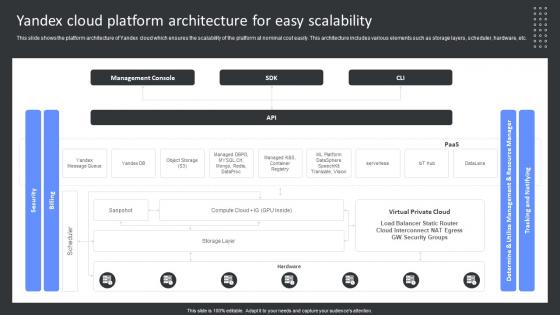 Yandex Cloud Platform Architecture For Easy Scalability Yandex Cloud SaaS Platform Implementation
Yandex Cloud Platform Architecture For Easy Scalability Yandex Cloud SaaS Platform ImplementationThis slide shows the platform architecture of Yandex cloud which ensures the scalability of the platform at nominal cost easily. This architecture includes various elements such as storage layers, scheduler, hardware, etc. Present the topic in a bit more detail with this Yandex Cloud Platform Architecture For Easy Scalability Yandex Cloud SaaS Platform Implementation. Use it as a tool for discussion and navigation on Management, Scalability, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architectural Innovation Examples In Powerpoint And Google Slides Cpb
Architectural Innovation Examples In Powerpoint And Google Slides CpbPresenting Architectural Innovation Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Architectural Innovation Examples. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Confidential Computing Architecture And Realms Working Confidential Computing Hardware
Confidential Computing Architecture And Realms Working Confidential Computing HardwareThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Computing Architecture And Realms Working Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Working Of Realms, Demonstrate, Operating System, Realm Manager, Hypervisor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware
Confidential Computing Architecture Based On Azure Services Confidential Computing HardwareThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Azure Confidential Computing Services, Typical Approaches, Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware
Confidential Computing Architecture Implementation Roadmap Confidential Computing HardwareThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Roadmap, Confidential Computing Architecture, Demonstrate, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow
Confidential Computing Hardware Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow. Dispense information and present a thorough explanation of Architecture Of Container Service, Kubernetes Trusted, Execution Environment Version, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee
Confidential Computing Hardware Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Introducing Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Inclavare, Confidential Containers, Tee Environment, Kubernetes Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture
Confidential Computing Hardware Multiparty Privacy Preserving Computation ArchitectureThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Design, Multiparty Computing, Confidential Computing, Blockchain With Azure Virtual Machine, Blockchain As A Service, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Occlum System Architecture And Features
Confidential Computing Hardware Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
-
 Data AI Artificial Intelligence Data AI Platform Multiple Layer Architecture AI SS
Data AI Artificial Intelligence Data AI Platform Multiple Layer Architecture AI SSThe slide showcases Data.AI platforms architecture with components like Data.AI intelligence market insights, Data.AI ascend advertising strategy, Data.AI connectplus data collection and analysis, data experience real-time analysis, data science big data analysis, and data foundation data collection from various sources. Present the topic in a bit more detail with this Data AI Artificial Intelligence Data AI Platform Multiple Layer Architecture AI SS. Use it as a tool for discussion and navigation on Data AI Platforms, Architecture With Components, Data AI Intelligence, Data Collection And Analysis, Big Data Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of Filtering Techniques Architecture Of Course Recommendations On Linkedin Learning
Applications Of Filtering Techniques Architecture Of Course Recommendations On Linkedin LearningThis slide highlights the architecture of LinkedIns course recommendation system. The purpose of this slide is to explain the working of LinkedIns course recommender. The main components include user information, model handling, recommendation engine, etc. Present the topic in a bit more detail with this Applications Of Filtering Techniques Architecture Of Course Recommendations On Linkedin Learning. Use it as a tool for discussion and navigation on Online Recommendations, Recommendation Engine, Course Recommendations, Model Handling And Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of Filtering Techniques System Architecture Of Hybrid Recommendation System
Applications Of Filtering Techniques System Architecture Of Hybrid Recommendation SystemThis slide represents the system architecture of hybrid recommender system. The purpose of this slide is to illustrate the working of a hybrid recommender. The key points include input, information processing, predicted recommendation list and top recommended items. Deliver an outstanding presentation on the topic using this Applications Of Filtering Techniques System Architecture Of Hybrid Recommendation System. Dispense information and present a thorough explanation of Collaborative Filtering, Data Cleaning, Data Integration, Data Transformation, Pattern Similarity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Service Oriented Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Service Oriented Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for illustrating micro services. It features a 3D cube with a bright blue background and a multi-coloured cube inside. It is a great visual representation of the concept of micro services.
-
 Service Oriented Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Service Oriented Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great way to illustrate the concept of Micro Services in a presentation. It features a simple, modern design with a single color, making it easy to integrate into any presentation. Its perfect for illustrating the concept of Micro Services in a clear and concise way.
-
 Event Driven Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Event Driven Architecture Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for illustrating micro services. It features a 3D cube with a bright blue background and a multi-coloured cube inside. It is a great visual representation of the concept of micro services.
-
 Event Driven Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Event Driven Architecture Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great way to illustrate the concept of Micro Services in a presentation. It features a simple, modern design with a single color, making it easy to integrate into any presentation. Its perfect for illustrating the concept of Micro Services in a clear and concise way.
-
 Architectural Construction Map Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Architectural Construction Map Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for presentations. It features a bright, vibrant colour palette and is sure to make your slides stand out. Its easy to use and can be used to add a touch of personality to your presentation.
-
 Architectural Construction Map Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Architectural Construction Map Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is perfect for displaying construction planning maps. It features a high-quality, detailed image of a construction planning map in black and white. Use this icon to illustrate the planning process for any construction project.





