Powerpoint Templates and Google slides for Aggression
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Unified threat management concept ppt slide show
Unified threat management concept ppt slide showPresenting unified threat management concept ppt slide show. This is a unified threat management concept ppt slide show. This is a three stage process. The stages in this process are web security, networking security, email security.
-
 Internal threats analysis ppt powerpoint templates download
Internal threats analysis ppt powerpoint templates downloadPresenting internal threats analysis ppt powerpoint templates download. This is a internal threats analysis ppt powerpoint templates download. This is a two stage process. The stages in this process are threats, opportunities.
-
 Threat of new competitors powerpoint ideas
Threat of new competitors powerpoint ideasPresenting threat of new competitors powerpoint ideas. This is a threat of new competitors powerpoint ideas. This is a four stage process. The stages in this process are threat of new competitors, existing competitive rivalry, threat of substitution, supplier power.
-
 Threat of new competitors powerpoint presentation
Threat of new competitors powerpoint presentationPresenting threat of new competitors powerpoint presentation. This is a threat of new competitors powerpoint presentation. This is a four stage process. The stages in this process are supplier power, threat of new competitors, existing competitive rivalry, threat of substitution.
-
 Threat of substitution diagram ppt slides examples
Threat of substitution diagram ppt slides examplesPresenting threat of substitution diagram ppt slides examples. This is a threat of substitution diagram ppt slides examples. This is five stage process. The stages in this process are resource nationalism, threat of substitute, combine, adapt, eliminate.
-
 Threat evaluation template powerpoint slides presentation examples
Threat evaluation template powerpoint slides presentation examplesPresenting threat evaluation template powerpoint slides presentation examples. This is a threat evaluation template powerpoint slides presentation examples. This is a six stage process. The stages in this process are identify hazards, evaluate hazards, recommend actions, recommend actions, act to address hazards, revalidate process.
-
 Process of threat risk modeling diagram powerpoint images
Process of threat risk modeling diagram powerpoint imagesPresenting process of threat risk modeling diagram powerpoint images. This is a process of threat risk modeling diagram powerpoint images. This is a five stage process. The stages in this process are risk, impact, degree of mitigating, exploitability, damage potential, possibility, identify vulnerabilities, application overview, identify threats, decompose application.
-
 Seismic threat evaluation ppt layout presentation design
Seismic threat evaluation ppt layout presentation designPresenting seismic threat evaluation ppt layout presentation design. This is a seismic threat evaluation ppt layout presentation design. This is a four stage process. The stages in this process are intensity measure relationship, earthquake rupture forecast, specify user inputs, select ground motions.
-
 Threat calculation layout ppt background graphics
Threat calculation layout ppt background graphicsPresenting threat calculation layout ppt background graphics. This is a threat calculation layout ppt background graphics. This is six stage process. The stages in this process are identify risk, assess risk, control risk, plan action, implement, review, risk management.
-
 Aggressive pricing template powerpoint slide images
Aggressive pricing template powerpoint slide imagesPresenting aggressive pricing template powerpoint slide images. This is a aggressive pricing template powerpoint slide images. This is a four stage process. The stages in this process are value positioning, low cost, strategy, simple product.
-
 Threat audit diagram powerpoint presentation templates
Threat audit diagram powerpoint presentation templatesPresenting threat audit diagram powerpoint presentation templates. Presenting threat audit diagram powerpoint presentation templates. This is a threat audit diagram powerpoint presentation templates. This is a six stage process. The stages in this process are define risk model, gather risk data, process risk data, measure risk factors, central data review, stat monitoring.
-
 Threat profiling sample of ppt presentation
Threat profiling sample of ppt presentationPresenting threat profiling sample of ppt presentation. This is a threat profiling sample of ppt presentation. This is a four stage process. The stages in this process are threat name, related incident, threat alias, threat type.
-
 Unified threat management concept diagram presentation visuals
Unified threat management concept diagram presentation visualsPresenting unified threat management concept diagram presentation visuals. This is a unified threat management concept diagram presentation visuals. This is a six stage process. The stages in this process are vpn, content filtering, intrusion protection, spam protection, phishing protection, spyware protection.
-
 Cyber threat analysis sample diagram ppt presentation visual aids
Cyber threat analysis sample diagram ppt presentation visual aidsPresenting cyber threat analysis sample diagram ppt presentation visual aids. This is a cyber threat analysis sample diagram ppt presentation visual aids. This is a four stage process. The stages in this process are successful attack, system susceptibility, threat accessibility, threat capability.
-
 Dashboard snapshot threat tracking electronic information security
Dashboard snapshot threat tracking electronic information securityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Dashboard Snapshot Threat Tracking Electronic Information Security. Use it as a tool for discussion and navigation on Most Monthly Threat Status, Threat Dashboard, Current Risk Status, Threats Based Role, Risk By Threats, Threat Report, Threats Owners. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace current potential implications faced firm
Cyber threat management workplace current potential implications faced firmThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Threat Management Workplace Current Potential Implications Faced Firm. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial, Losses Due To Increase Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat management workplace cyber threats management dashboard Snapshot
Cyber threat management workplace cyber threats management dashboard SnapshotThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Cyber Threats Management Dashboard Snapshot. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risks Threshold Top 5 Vulnerabilities, Action Plan Breakdown, Risk Heat Map, Risk Analysis Progress using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace financial performance tracking dashboard
Cyber threat management workplace financial performance tracking dashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Receivables Analysis, Revenue And Expense Trends, Central County Deal, Main Town Dealership, Payment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace incident reporting dashboard snapshot
Cyber threat management workplace incident reporting dashboard snapshotThe firm will track the various incidents issues faced and resolved in the firm. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Incident Reporting Dashboard snapshot. Dispense information and present a thorough explanation of Tickets Resolved, Tickets Resolved By Assignee, Tickets Resolved, Tickets Resolved Assignee using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Opportunities and threats entering new markets new geos market adoption curve
Opportunities and threats entering new markets new geos market adoption curvePresent the topic in a bit more detail with this Opportunities And Threats Entering New Markets New Geos Market Adoption Curve. Use it as a tool for discussion and navigation on Market Adoption Curve. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Opportunities and threats entering new markets new geos value proposition matrix
Opportunities and threats entering new markets new geos value proposition matrixPresent the topic in a bit more detail with this Opportunities And Threats Entering New Markets New Geos Value Proposition Matrix. Use it as a tool for discussion and navigation on Mature Markets, Growth, Emerging. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web application firewall waf it kpis dashboard for threat tracking in waf
Web application firewall waf it kpis dashboard for threat tracking in wafThis slide depicts how threat risk will be monitored and threat detection will be done in the organization through web application firewall implementation. Present the topic in a bit more detail with this Web Application Firewall Waf It Kpis Dashboard For Threat Tracking In Waf. Use it as a tool for discussion and navigation on Kpis Dashboard For Threat Tracking In WAF. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Abs healthcare company records infected by minimize cybersecurity threats in healthcare company
Abs healthcare company records infected by minimize cybersecurity threats in healthcare companyThis slide shows the percentage of ABS Healthcare Company Records that are infected by Malware in the past 5 years. Deliver an outstanding presentation on the topic using this ABS Healthcare Company Records Infected By Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Abs Healthcare Company Records Infected By Malware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenge and solutions 1 malware and minimize cybersecurity threats in healthcare company
Challenge and solutions 1 malware and minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Present the topic in a bit more detail with this Challenge And Solutions 1 Malware And Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Loss, Low Accessibility, Management, Security Softwares. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenge and solutions 2 cloud threats and minimize cybersecurity threats in healthcare company
Challenge and solutions 2 cloud threats and minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an outstanding presentation on the topic using this Challenge And Solutions 2 Cloud Threats And Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Encryption, Risk Of Infiltration, Data Encryption Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenge and solutions 3 employee error minimize cybersecurity threats in healthcare company
Challenge and solutions 3 employee error minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to improper and unaware employee behavior leading to data loss and misuse. Also, some solutions are provided to solve the problem. Present the topic in a bit more detail with this Challenge And Solutions 3 Employee Error Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Security, Security Training Programs, Knowledge And Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Costs incurred to process faulty minimize cybersecurity threats in healthcare company
Costs incurred to process faulty minimize cybersecurity threats in healthcare companyThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Faulty Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.v
-
 Estimated five year targets of company minimize cybersecurity threats in healthcare company
Estimated five year targets of company minimize cybersecurity threats in healthcare companyThis slide shows the estimated future trends of ABS Healthcare Company for 5 years after the implementation of Strategies. These targets are related to number of Cybersecurity Cases, Client Satisfaction Rate, Company Revenue etc. Present the topic in a bit more detail with this Estimated Five Year Targets Of Company Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Cybersecurity Cases, Patient Satisfaction Rate, Company Revenue. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact on revenue due to increasing minimize cybersecurity threats in healthcare company
Impact on revenue due to increasing minimize cybersecurity threats in healthcare companyThis slide shows the reveanue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an outstanding presentation on the topic using this Impact On Revenue Due To Increasing Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Healthcare Company, Revenue, Revenue Trend using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current potential implications managing critical threat vulnerabilities and security threats
Current potential implications managing critical threat vulnerabilities and security threatsThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Current Potential Implications Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Increase Security Threats, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threats management managing critical threat vulnerabilities and security threats
Cyber threats management managing critical threat vulnerabilities and security threatsThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Present the topic in a bit more detail with this Cyber Threats Management Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Cyber Threats Management Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial performance tracking managing critical threat vulnerabilities and security threats
Financial performance tracking managing critical threat vulnerabilities and security threatsThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Present the topic in a bit more detail with this Financial Performance Tracking Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Revenue And Expense Trends, Receivables Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
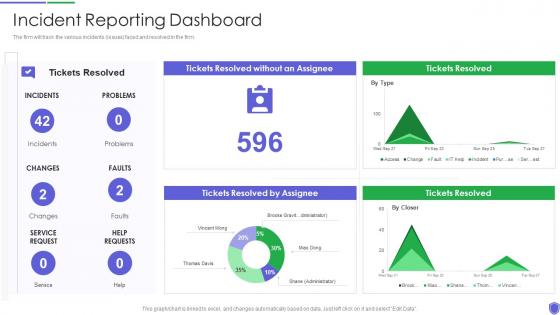 Incident reporting dashboard managing critical threat vulnerabilities and security threats
Incident reporting dashboard managing critical threat vulnerabilities and security threatsThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Incident Reporting Dashboard Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Incident Reporting Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current potential implications faced by firm as threats corporate security management
Current potential implications faced by firm as threats corporate security managementThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Current Potential Implications Faced By Firm As Threats Corporate Security Management. Use it as a tool for discussion and navigation on Employees, Increase Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threats management dashboard corporate security management
Cyber threats management dashboard corporate security managementThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Threats Management Dashboard Corporate Security Management. Dispense information and present a thorough explanation of Cyber Threats Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics associated to workplace threats corporate security management
Statistics associated to workplace threats corporate security managementThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Corporate Security Management. Use it as a tool for discussion and navigation on Cyber Attacks Costs, Organizations, Data Records. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat compliance dashboard with risk and standard control
Cyber threat compliance dashboard with risk and standard controlThe following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Introducing our Cyber Threat Compliance Dashboard With Risk And Standard Control set of slides. The topics discussed in these slides are Risk Control Issue, Review Effectiveness, Regulation Control Issue. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat dashboard with current risks and security service
Cyber threat dashboard with current risks and security serviceThe following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Presenting our well structured Cyber Threat Dashboard With Current Risks And Security Service. The topics discussed in this slide are Current Risks, Current Threats, Security Service. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security market growth with current trends
Cyber threat security market growth with current trendsThe following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Introducing our Cyber Threat Security Market Growth With Current Trends set of slides. The topics discussed in these slides are Cyber Security Market Share, Market Growth, Banking And Finance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyberterrorism it cyber terrorism faced by companies in us ppt slides deck
Cyberterrorism it cyber terrorism faced by companies in us ppt slides deckThis slide depicts the cyber terrorism faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Cyber Terrorism Faced By Companies In US Ppt Slides Deck. Dispense information and present a thorough explanation of Financial Loss Million, Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it cyber terrorism faced by various industries ppt slides model
Cyberterrorism it cyber terrorism faced by various industries ppt slides modelThis slide describes the cyber terrorism various industries face, including health, finance, media, transportation and education. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorism Faced By Various Industries Ppt Slides Model. Use it as a tool for discussion and navigation on Education, Transportation, Media, Healthcare, Government. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it dashboard for threat tracking of cyber terrorism
Cyberterrorism it dashboard for threat tracking of cyber terrorismThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Dashboard For Threat Tracking Of Cyber Terrorism. Dispense information and present a thorough explanation of Threats Per Month, Top Threat, Average Threats Detection Per Day using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it distributed denial of service ddos as cyber terrorism too
Cyberterrorism it distributed denial of service ddos as cyber terrorism tooThis slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Distributed Denial Of Service DDOS As Cyber Terrorism Too. Dispense information and present a thorough explanation of Service Denial, Disrupting Services, Ceasing Sites, 2019 To 2020 using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sandbox vr investor funding elevator pitch deck aggressive growth enables exclusive content
Sandbox vr investor funding elevator pitch deck aggressive growth enables exclusive contentPurpose of this slide is to illustrates that businesses growing aggressively have the access to exclusive content that helps in generating revenue for studio partners. Deliver an outstanding presentation on the topic using this Sandbox Vr Investor Funding Elevator Pitch Deck Aggressive Growth Enables Exclusive Content. Dispense information and present a thorough explanation of Aggressive, Growth, Enables using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sandbox vr investor funding elevator pitch deck strong economics enables aggressive growth
Sandbox vr investor funding elevator pitch deck strong economics enables aggressive growthThis slide shows that strong economics plays a vital role in providing aggressive growth to business. Here the statistics indicates that strong economics aided the company to grow rapidly across the globe. Deliver an outstanding presentation on the topic using this Sandbox Vr Investor Funding Elevator Pitch Deck Strong Economics Enables Aggressive Growth. Dispense information and present a thorough explanation of Strong Economics Enables Aggressive Growth using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Dashboard Snapshot For Threat Tracking In Information Security
Information Security Dashboard Snapshot For Threat Tracking In Information SecurityThis slide depicts the dashboard snapshot for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Information Security Dashboard For Threat Tracking In Information Security. Dispense information and present a thorough explanation of Dashboard, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
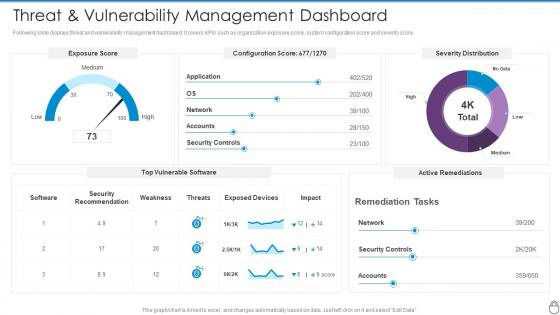 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical current potential implications faced by firm as threats
Threat management for organization critical current potential implications faced by firm as threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Threat Management For Organization Critical Current Potential Implications Faced By Firm As Threats. Dispense information and present a thorough explanation of Current Potential Implications Faced By Firm As Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management for organization critical cyber threats management dashboard
Threat management for organization critical cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives.Present the topic in a bit more detail with this Threat Management For Organization Critical Cyber Threats Management Dashboard. Use it as a tool for discussion and navigation on Average Risk Threshold, Risk Rating Breakdown, Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat management for organization critical financial performance tracking dashboard
Threat management for organization critical financial performance tracking dashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Threat Management For Organization Critical Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Financial Performance Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat management for organization critical incident reporting dashboard
Threat management for organization critical incident reporting dashboardThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Threat Management For Organization Critical Incident Reporting Dashboard. Use it as a tool for discussion and navigation on Incident Reporting Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management current potential implications faced by firm threats
Cyber security risk management current potential implications faced by firm threatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Present the topic in a bit more detail with this Cyber Security Risk Management Current Potential Implications Faced By Firm Threats. Use it as a tool for discussion and navigation on Issues Related, Employees, Data Breaches, Records Exposed, Reported Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management cyber threats management dashboard
Cyber security risk management cyber threats management dashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown, Risks, Threshold Top 5 Entities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Hacking it dashboard snapshot for threat tracking ppt slides demonstration
Hacking it dashboard snapshot for threat tracking ppt slides demonstrationThis slide depicts the dashboard snapshot for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an outstanding presentation on the topic using this Hacking It Dashboard For Threat Tracking Ppt Slides Demonstration. Dispense information and present a thorough explanation of Dashboard For Threat Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification event management dashboard sanpshot
Automating threat identification event management dashboard sanpshotThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an outstanding presentation on the topic using this Automating Threat Identification Event Management Dashboard Snapshot. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Automating threat identification information and event management dashboard
Automating threat identification information and event management dashboardThis slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an outstanding presentation on the topic using this Automating Threat Identification Information And Event Management Dashboard. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information and event management dashboard automating threat identification
Information and event management dashboard automating threat identificationThis slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Present the topic in a bit more detail with this Information And Event Management Dashboard Automating Threat Identification. Use it as a tool for discussion and navigation on Information, Management, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.





