Powerpoint Templates and Google slides for Aggression
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Strategies To Prevent System Hacking Threats
Strategies To Prevent System Hacking ThreatsThis slide highlights approaches to ensure protection against potential hacking threats. The purpose of this slide is to help businesses in defending internet connected devices from malevolent attacks, identity theft, data breaches and financial losses by cybercriminals. It covers strategies such as software update, strong password policy and HTTP encryption. Presenting our well structured Strategies To Prevent System Hacking Threats The topics discussed in this slide are Alphanumeric Passwords, Ensuring Unique Passwords, Updating Operating. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Approaches For Aquatic Biological Diversity Threats
Approaches For Aquatic Biological Diversity ThreatsThis slide showcases the major techniques to protect aquatic biodiversity from threats. It include details such as exotic species extinction,water pollution,etc. Introducing our Approaches For Aquatic Biological Diversity Threats set of slides. The topics discussed in these slides are Protects Water Diversity,Increases Public Awareness,Enhances Regional Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Primary Types Of Mobile Security Threats
Primary Types Of Mobile Security ThreatsThis slide discusses the various types of mobile security threats which include phishing, malware and ransomware, crypto jacking and outdated operating system. Introducing our premium set of slides with name Primary Types Of Mobile Security Threats. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing, Malware And Ransomware, Outdated Operating Systems, Crypto Jacking. So download instantly and tailor it with your information.
-
 Techniques To Counter Mobile Security Threats
Techniques To Counter Mobile Security ThreatsThis slide highlights the techniques to counter mobile security threats which include remote wipe for lost devices, segment storage to prevent malware, etc. Presenting our set of slides with name Techniques To Counter Mobile Security Threats. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement Network Security, Techniques To Counter, Mobile Security Threats.
-
 SWOT Analysis Threats KPMG Company Profile Ppt Topics CP SS
SWOT Analysis Threats KPMG Company Profile Ppt Topics CP SSThis slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Introducing SWOT Analysis Threats KPMG Company Profile Ppt Topics CP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Intense Competition, Economic Downturn, Legal And Regulatory Risks, using this template. Grab it now to reap its full benefits.
-
 Our Threats Vestas Company Profile CP SS
Our Threats Vestas Company Profile CP SSThe following slide showcases the threats to Vestas company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as competition, government policies and regulatory changes. Introducing Our Threats Vestas Company Profile CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Government Policies, Economic Downturn using this template. Grab it now to reap its full benefits.
-
 Implementing Effective Tokenization Existing IT Security Infrastructure Threats
Implementing Effective Tokenization Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Present the topic in a bit more detail with this Implementing Effective Tokenization Existing IT Security Infrastructure Threats. Use it as a tool for discussion and navigation on Compliance Challenges, Resource Intensiveness, Faced Security Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emergency Preparedness Steps For Cyber Threat Mitigation
Emergency Preparedness Steps For Cyber Threat MitigationThis slide represents steps for emergency preparedness for cyber risk mitigation including steps such as identifying critical data, assess risks, developing team, etc. Introducing our premium set of slides with Emergency Preparedness Steps For Cyber Threat Mitigation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assess Risks, Create Procedures, Develop Team. So download instantly and tailor it with your information.
-
 SWOT Analysis Threats Online Retailer Company Profile CP SS V
SWOT Analysis Threats Online Retailer Company Profile CP SS VThis slide showcase SWOT Strengths, Weaknesses, Opportunities and Threats analysis of ecommerce giant that helps in converting company weakness into strengths and threats into opportunities Introducing SWOT Analysis Threats Online Retailer Company Profile CP SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weaknesses, Opportunities using this template. Grab it now to reap its full benefits.
-
 Our Threats Music And Entertainment Company Profile CP SS V
Our Threats Music And Entertainment Company Profile CP SS VThe following slide showcases the threats to Spotify company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as data privacy regulations, technology disruptions and piracy. Increase audience engagement and knowledge by dispensing information using Our Threats Music And Entertainment Company Profile CP SS V. This template helps you present information on three stages. You can also present information on Data Privacy Regulations, Technology Disruptions, Piracy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparison Of Cybersecurity Apps For Threat Detection
Comparison Of Cybersecurity Apps For Threat DetectionThis slide represents comparison table for cybersecurity applications for online risk mitigation including Wireshark, Metasploit, and Entersoft apps. Introducing our premium set of slides with Comparison Of Cybersecurity Apps For Threat Detection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Protocol Analysis, Security Assessment, Infrastructure Security Analysis. So download instantly and tailor it with your information.
-
 Top Web Application Security Threats Ppt File Example Topics
Top Web Application Security Threats Ppt File Example TopicsThis slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Deliver an outstanding presentation on the topic using this Top Web Application Security Threats Ppt File Example Topics. Dispense information and present a thorough explanation of Cross Site Request Forgery, Insecure Direct Object References, Web Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V
Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS VThis slide showcases various data sources that are leveraged by ChatGPT for threat intelligence to tack cyber attack on organization. Various data sources for threat intelligence are security blogs, social media and security forums. Introducing Gathering And Analyzing Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Blogs, Security Forums, Security Media, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V
Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS VThis slide showcases threat intelligence overview which can help organization to tackle the cyber attack. It also highlights key importance of threat intelligence that are tackle ongoing attacks, make informed decisions, formulate threat mitigation strategies etc. Present the topic in a bit more detail with this Overview And Importance Of Threat Intelligence Opportunities And Risks Of ChatGPT AI SS V. Use it as a tool for discussion and navigation on Security Operation Center, Security Analyst, Computer Security Incident Response Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Threats Impacting Information Security
Potential Threats Impacting Information SecurityThis slide highlights possible vulnerabilities to data security. The purpose of this template is to help businesses in overcoming various challenges in protecting data for creating a safer environment. It includes elements such as malware, phishing, data breaches, etc. Introducing our Potential Threats Impacting Information Security set of slides. The topics discussed in these slides are General Data Protection, Health Insurance Portability, Security Management Act FISMA. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Integrating Threat Intelligence With Cybersecurity
Best Practices For Integrating Threat Intelligence With CybersecurityThis slide depicts the best practices for integrating cyber threat intelligence with cybersecurity. The purpose of this slide is to help the business successfully integrate threat intelligence with cybersecurity. It includes automation of data processing,, establishment of threat intelligence sharing policies, etc. Presenting our set of slides with Best Practices For Integrating Threat Intelligence With Cybersecurity This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ensure Integration, Current System, Automate Data Processing
-
 Challenges Faced During Business Cyber Threat Intelligence
Challenges Faced During Business Cyber Threat IntelligenceThis slide showcases the challenges faced during business cyber threat intelligence. The purpose of this slide is to help the business overcome these challenges through the use of provided solutions. It includes challenges such as improper management of information, streamlined integration, etc. Introducing our premium set of slides with Challenges Faced During Business Cyber Threat Intelligence Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Description, Challenges, Solutions So download instantly and tailor it with your information.
-
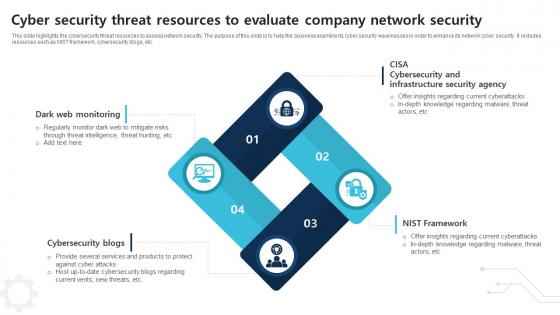 Cyber Security Threat Resources To Evaluate Company Network Security
Cyber Security Threat Resources To Evaluate Company Network SecurityThis slide highlights the cybersecurity threat resources to assess network security. The purpose of this slide is to help the business examine its cyber security weaknesses in order to enhance its network cyber security. It includes resources such as NIST framework, cybersecurity blogs, etc. Introducing our premium set of slides with Cyber Security Threat Resources To Evaluate Company Network Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Dark Web Monitoring, Cybersecurity Blogs, Nist Framework So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Framework To Safeguard Business Networks
Cyber Threat Intelligence Framework To Safeguard Business NetworksThis slide depicts the cyber threat intelligence framework utilized to safeguard business networks. The purpose of this slide is to help the business properly integrate cyber threat intelligence. It includes elements such as strategic CTI, tactical CTI, etc. Presenting our set of slides with Cyber Threat Intelligence Framework To Safeguard Business Networks This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Operational CTI, Strategic CTI
-
 Cyber Threat Intelligence Icon To Detect Digital Attacks
Cyber Threat Intelligence Icon To Detect Digital AttacksIntroducing our premium set of slides with Cyber Threat Intelligence Icon To Detect Digital Attacks Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Intelligence Icon, Detect Digital Attacks So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Icon To Enhance Cybersecurity
Cyber Threat Intelligence Icon To Enhance CybersecurityPresenting our set of slides with Cyber Threat Intelligence Icon To Enhance Cybersecurity This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Threat Intelligence Icon, Enhance Cybersecurity
-
 Cyber Threat Intelligence Vendor Comparative Analysis
Cyber Threat Intelligence Vendor Comparative AnalysisThis slide showcases the cyber threat intelligence vendor comparative analysis. The purpose of this slide is to help the business make an informed purchase decision regarding vendor services. It includes comparison on the basis of description, pricing and ratings Introducing our Cyber Threat Intelligence Vendor Comparative Analysis set of slides. The topics discussed in these slides are Vendor, Description, Pricing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Sources For Cyber Threat Intelligence During Cybersecurity
Sources For Cyber Threat Intelligence During CybersecurityThis slide showcases the sources for cyber threat intelligence during cyber security. The purpose of this slide is to establish rigid security through the use of cyber threat intelligence. It includes open source intelligence, internal intelligence, etc. Presenting our well structured Sources For Cyber Threat Intelligence During Cybersecurity The topics discussed in this slide are CTI Information Source, Description, Examples This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Steps For Cyber Threat Intelligence Lifecycles
Steps For Cyber Threat Intelligence LifecyclesThis slide depicts the steps for cyber threat intelligence lifecycles. The purpose of this slide is to help the business successfully implement cyber threat intelligence practices. It includes steps such as requirements, collection, processing, etc. Introducing our premium set of slides with Steps For Cyber Threat Intelligence Lifecycles Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Requirements, Collection, Processing So download instantly and tailor it with your information.
-
 Types Of Cyber Threat Intelligence To Safeguard Business
Types Of Cyber Threat Intelligence To Safeguard BusinessThis slide depicts the steps for cyber threat intelligence lifecycles. The purpose of this slide is to help the business successfully implement cyber threat intelligence practices. It includes steps such as requirements, collection, processing, etc. Presenting our set of slides with Types Of Cyber Threat Intelligence To Safeguard Business This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strategic Intelligence, Tactical Intelligence, Operational Intelligence
-
 Use Cases Of Cyber Threat Intelligence Framework To Establish Cybersecurity
Use Cases Of Cyber Threat Intelligence Framework To Establish CybersecurityThis slide depicts the use cases of cyber threat intelligence framework to establish cybersecurity. The purpose of this slide is to help the business appropriately utilize cyber threat intelligence framework in order to enhance its network security. It includes cyber risk management, security operations center, etc. Introducing our premium set of slides with Use Cases Of Cyber Threat Intelligence Framework To Establish Cybersecurity Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Risk Management, Vulnerability Management, Security Operations Center So download instantly and tailor it with your information.
-
 Cyber Security Online Threat Control Icon
Cyber Security Online Threat Control IconPresenting our set of slides with Cyber Security Online Threat Control Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Online Threat Control Icon
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Web Security Audit Controls To Reduce Threats
Web Security Audit Controls To Reduce ThreatsThis slide represents various security control methods to minimize threats to web security. The purpose of this slide is to help businesses in developing strategy for data protection. It provides techniques to minimize web security threats such as SQL injection, ransomware, denial of service attacks and phishing. Introducing our Web Security Audit Controls To Reduce Threats set of slides. The topics discussed in these slides are Ransomware, Service Attacks, Phishing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS
Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SSThis slide showcases vulnerability assessment disclosure and threat intelligence on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about continuous monitoring, correlation, disclosure, etc. Introducing Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Continuous Monitoring, Correlation With Metadata, Disclosure Implementation, using this template. Grab it now to reap its full benefits.
-
 Our Threats Data Analytics And Storage Company Profile CP SS V
Our Threats Data Analytics And Storage Company Profile CP SS VThe following slide showcases the threats to Snowflake company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition market competition and technology disruptions. Introducing Our Threats Data Analytics And Storage Company Profile CP SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Weakness, Opportunities using this template. Grab it now to reap its full benefits.
-
 SWOT Analysis Threats Retail Store Company Profile Ppt Show Background Designs CP SS V
SWOT Analysis Threats Retail Store Company Profile Ppt Show Background Designs CP SS VFollowing slides includes information about company threats from external environment. It includes threats such as economic uncertainties, competitors supply chain disruption, etc. Increase audience engagement and knowledge by dispensing information using SWOT Analysis Threats Retail Store Company Profile Ppt Show Background Designs CP SS V This template helps you present information on four stages. You can also present information on Strengths, Weaknesses, Opportunities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icon For Email Security Threats And Attacks
Icon For Email Security Threats And AttacksIntroducing our premium set of slides with Icon For Email Security Threats And Attacks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Email Security, Threats And Attacks. So download instantly and tailor it with your information.
-
 Company SWOT Analysis To Identify Threats Leveraging Effective CRM Tool In Real Estate Company
Company SWOT Analysis To Identify Threats Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers SWOT analysis for a real estate company, aiming to identify inherent strengths, weaknesses, potential threats, and opportunities. It includes comprehensive understanding of the companys current standing and strategic considerations for the future. Introducing Company SWOT Analysis To Identify Threats Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strengths, Threats, Opportunities, Weaknesses, using this template. Grab it now to reap its full benefits.
-
 Our Threats Data Warehouse Service Company CP SS V
Our Threats Data Warehouse Service Company CP SS VThe following slide showcases the threats to Snowflake company and showcases external factors that can be a hurdle in business growth and development. It showcases elements such as market competition market competition and technology disruptions. Increase audience engagement and knowledge by dispensing information using Our Threats Data Warehouse Service Company CP SS V This template helps you present information on four stages. You can also present information on Opportunities, Strategic Collaboration, Industry Growth using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace Incident Report For Verbal Threat
Workplace Incident Report For Verbal ThreatThe purpose of this slide is to address a workplace incident report involving a verbal threat during a team meeting, emphasizing the companys commitment to a safe and respectful work environment. Introducing our Workplace Incident Report For Verbal Threat set of slides. The topics discussed in these slides are Impact, Action Steps. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SWOT Threats Apparel Company Profile CP SS V
SWOT Threats Apparel Company Profile CP SS VThis slide showcase SWOT Strengths, Weaknesses, Opportunities and Threats analysis of Zara company that helps in converting company weakness into strengths and threats into opportunities Introducing SWOT Threats Apparel Company Profile CP SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strength, Weakness, Opportunities using this template. Grab it now to reap its full benefits.
-
 Website Penetration Testing Icon For Threat Prevention
Website Penetration Testing Icon For Threat PreventionIntroducing our premium set of slides with Website Penetration Testing Icon For Threat Prevention. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Website Penetration Testing, Icon Threat Prevention. So download instantly and tailor it with your information.
-
 Website Penetration Testing Standards For Threat Identification
Website Penetration Testing Standards For Threat IdentificationThis slide covers standards that facilitate penetration testing and helps in threat identification. It covers standards that promotes payment security, cyber safety , information system security, etc. Presenting our set of slides with Website Penetration Testing Standards For Threat Identification. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information System, Application Control, Network Mapping.
-
 SWOT Analysis Threats Food Ordering Website Company Profile CP SS V
SWOT Analysis Threats Food Ordering Website Company Profile CP SS VMentioned slide provides information about threats faced by company. It includes threats such as competitors, technological disruption, and regulatory changes. Increase audience engagement and knowledge by dispensing information using SWOT Analysis Threats Food Ordering Website Company Profile CP SS V This template helps you present information on three stages. You can also present information on Competition, Technology Disruptions, Regulatory Changes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Existing IT Security Infrastructure Threats
Application Security Implementation Plan Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Existing IT Security Infrastructure Threats. Dispense information and present a thorough explanation of Broken Authentication, Cross Site Scripting, Denial Of Service, Infrastructure Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Bfsi Sector Cybersecurity Threats In Big Data Analytics
Bfsi Sector Cybersecurity Threats In Big Data AnalyticsThis slide highlights cybersecurity in BFSI sector big data analytics threats. This includes phishing attacks, cyber physical attacks, internet of things attacks and threats by third party involved. Introducing our premium set of slides with name Bfsi Sector Cybersecurity Threats In Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Physical Attacks, Internet Of Things Attacks, Threats By Third Party Involved. So download instantly and tailor it with your information.
-
 Threat Detection Icon Indicator Visualization Security
Threat Detection Icon Indicator Visualization SecurityIntroducing our premium set of slides with Threat Detection Icon Indicator Visualization Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection, Indicator Visualization Security. So download instantly and tailor it with your information.
-
 Operation Continuity Plan For Cybersecurity Threats
Operation Continuity Plan For Cybersecurity ThreatsThis slide represents an operation continuity plan for businesses including cybersecurity threats such as injections, broken authentication, and cross-site scripting. Presenting our well structured Operation Continuity Plan For Cybersecurity Threats. The topics discussed in this slide are Supervisors, Broken Authentication, Cross-Site Scripting. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 How ChatGPT Can Strengthen Threat Intelligence Impact Of Generative AI SS V
How ChatGPT Can Strengthen Threat Intelligence Impact Of Generative AI SS VThis slide showcases ChatGPT usage for threat intelligence for tackling cyber attacks on organizations. Its key elements are generate threat reports, analyze threat intelligence data and answer threat related queries. Introducing How ChatGPT Can Strengthen Threat Intelligence Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Generate Threat Reports, Intelligence Data, Related Queries, using this template. Grab it now to reap its full benefits.
-
 Overview And Importance Of Threat Intelligence Impact Of Generative AI SS V
Overview And Importance Of Threat Intelligence Impact Of Generative AI SS VThis slide showcases threat intelligence overview which can help organization to tackle the cyber attack. It also highlights key importance of threat intelligence that are tackle ongoing attacks, make informed decisions, formulate threat mitigation strategies etc. Introducing Overview And Importance Of Threat Intelligence Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Motive And Behavior, Tackle Cyber Attack, Intelligence Data, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Management Strategies To Mitigate Threats
Cyber Security Management Strategies To Mitigate ThreatsThis slide highlights different strategies that can help businesses in reducing cyber security threats. It further covers attributes such as priority level, description, mitigating strategies, etc. Presenting our well structured Cyber Security Management Strategies To Mitigate Threats. The topics discussed in this slide are Information Disclosure, Service Denial, Tampering. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 4 Threats To Cybersecurity In Automobile Industry
4 Threats To Cybersecurity In Automobile IndustryThis slide highlights cyber safety concerns in automotive sector. The purpose of this slide is to provide businesses with the required knowledge regarding various malware attacks in vehicles. It includes elements such as software, unauthorized access, etc. Presenting our set of slides with 4 Threats To Cybersecurity In Automobile Industry This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized Access, Supply Chain, Software
-
 Impact Analysis Of Cyber Security Threats In Automotive Industry
Impact Analysis Of Cyber Security Threats In Automotive IndustryThis slide highlights influence assessment cyber security risks in automobile industry. The purpose of this slide is to aid businesses in evaluating potential consequences of digital factors. It includes elements such as data privacy, supply chain disruption, etc. Introducing our premium set of slides with Impact Analysis Of Cyber Security Threats In Automotive Industry Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Privacy, Intellectual Property, Supply Chain Disruption So download instantly and tailor it with your information.
-
 Swot Analysis Threats General Electric Company Profile CP SS
Swot Analysis Threats General Electric Company Profile CP SSThis slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Increase audience engagement and knowledge by dispensing information using SWOT Analysis Threats General Electric Company Profile CP SS. This template helps you present information on four stages. You can also present information on Government Restrictions, Large Competitors, Exchange using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SWOT Analysis Threats Manufacturing Company Profile CP SS
SWOT Analysis Threats Manufacturing Company Profile CP SSThis slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Introducing SWOT Analysis Threats Manufacturing Company Profile CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Technological Disruptions, Regulatory Challenges, using this template. Grab it now to reap its full benefits.
-
 SWOT Threats Property Company Profile CP SS V
SWOT Threats Property Company Profile CP SS VThis slide showcase threats of swot analysis conducted for real estate organization. It includes threats such as interest rate fluctuations, natural disasters etc. Introducing SWOT Threats Property Company Profile CP SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strength, Weakness, Opportunity using this template. Grab it now to reap its full benefits.
-
 Threats Eliminated By Hids Cyber Security
Threats Eliminated By Hids Cyber SecurityThis slide represents threats eliminated by HIDS cyber security which detects suspicious activities and generates alerts when they are detected. It includes threats eliminated by HIDS cyber security such as malicious attacks, asymmetric routing, etc. Presenting our set of slides with Threats Eliminated By Hids Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malicious Attacks, Asymmetric Routing, Buffer Overflow Attacks.
-
 Radio Frequency Identification Security Concerns And Threats
Radio Frequency Identification Security Concerns And ThreatsThis slide outlines the security concerns and threats related to RFID tags, such as tracking, denial of service, RFID sniffing, insert attacks, spoofing, etc.Introducing Radio Frequency Identification Security Concerns And Threats to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Physical Attacks, Repudiation, Replay Attacks, Insert Attacks, using this template. Grab it now to reap its full benefits.
-
 Honeypot Cyber Deception Strategies To Trick Threat Actors
Honeypot Cyber Deception Strategies To Trick Threat ActorsThe purpose of this slide is to showcase honeypot cyber deception strategies designed to deceive and deter threat actors including spam email traps, decoy databases, and malware honeypots. Introducing our premium set of slides with Honeypot Cyber Deception Strategies To Trick Threat Actors. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Decoy Database, Malware Honeypots, Potential Impact. So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Challenges And Solutions
Cyber Threat Intelligence Challenges And SolutionsThis slide showcases challenges and solutions of cyber threat intelligence which prioritize security efforts and update management without gaps. It includes elements such as CTI levels, tactical, operational, strategic, challenges and solutions. Introducing our Cyber Threat Intelligence Challenges And Solutions set of slides. The topics discussed in these slides are Challenges, Solutions, Tactical Threat Intelligence. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threat Intelligence Checklist Report
Cyber Threat Intelligence Checklist ReportThis slide showcases checklist report of cyber threat intelligence which helps to identify and prevent attacks by providing information on attackers. It includes elements such as objectives, stakeholders, allocation, data source, response integration, risk assessment and compliance. Presenting our well structured Cyber Threat Intelligence Checklist Report. The topics discussed in this slide are Cyber Threat Intelligence, Checklist Steps . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Intelligence Functions And Roles
Cyber Threat Intelligence Functions And RolesThis slide showcases functions and roles of cyber threat intelligence which helps in evaluating security postures of infrastructure through CTI. It includes elements such as security, IT analysis, security operations center, computer security incident response team and executive management. Introducing our Cyber Threat Intelligence Functions And Roles set of slides. The topics discussed in these slides are Responsibilities, Benefits, Role, Function. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threat Intelligence Global Capsize Forecast
Cyber Threat Intelligence Global Capsize ForecastThis slide depicts cyber threat intelligence market size worldwide which indicates improving growth, defense and detection of organisations. It includes elements such as cyber threat intelligence, increasing frequency, government entities, private sector organisations. Presenting our well structured Cyber Threat Intelligence Global Capsize Forecast. The topics discussed in this slide are Significant Growth, Intelligence, Solutions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Intelligence Icon For IOT
Cyber Threat Intelligence Icon For IOTIntroducing our Cyber Threat Intelligence Icon For IOT set of slides. The topics discussed in these slides are Cyber Threat Intelligence Icon, IOT. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





