Powerpoint Templates and Google slides for After Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
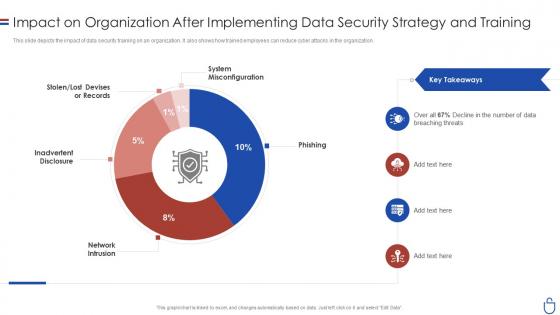 Data security it impact on organization after implementing data security strategy
Data security it impact on organization after implementing data security strategyThis slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver an outstanding presentation on the topic using this Data Security IT Impact On Organization After Implementing Data Security Strategy. Dispense information and present a thorough explanation of Phishing, Network Intrusion, Inadvertent Disclosure, System Misconfiguration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security impact on organization after implementing computer security strategy and training
Computer system security impact on organization after implementing computer security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Increase audience engagement and knowledge by dispensing information using Computer System Security Impact On Organization After Implementing Computer Security Strategy And Training. This template helps you present information on five stages. You can also present information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway
Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web GatewayThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Before Vs After Implementing Secure Web Gateway Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Productivity, Enforcement, Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Security Income After Retirement In Powerpoint And Google Slides Cpb
Social Security Income After Retirement In Powerpoint And Google Slides CpbPresenting Social Security Income After Retirement In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Security Income After Retirement. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure Your Digital Assets Before Vs After Crypto Wallets Integration
Secure Your Digital Assets Before Vs After Crypto Wallets IntegrationThis slide represents the before versus after crypto wallets integration for business operations. The purpose of this slide is to showcase how integration of crypto wallets has removed the third party vendors from digital transactions. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Before Vs After Crypto Wallets Integration. This template helps you present information on five stages. You can also present information on Crypto Wallets Integration, Digital Transactions, Bitcoin Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops Implementation
Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops ImplementationThis slide showcases the comparative analysis of the before versus after DevSecOps implementation. The purpose of this slide is to discuss the different performance aspects and how DevSecOps has proved beneficial for these aspects. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops Implementation. Dispense information and present a thorough explanation of Collaboration And Communication, Development Cycles, Operational Costs, Infrastructure Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Gateway Security IT Before Vs After Implementing Secure Web
Internet Gateway Security IT Before Vs After Implementing Secure WebThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Before Vs After Implementing Secure Web. Use it as a tool for discussion and navigation on Security, Visibility, Compliance, Productivity, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Before Vs After Implementation Of Application Security
Before Vs After Implementation Of Application SecurityThis slide discusses the overview of authorization in application security for authorized access of resource. Introducing Before Vs After Implementation Of Application Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Implement Encryption Protocols, Patch Management System, Vulnerable Authentication Mechanisms, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Implementing Security Testing
Before Vs After Implementing Security TestingThis slide represents the before vs. after implementing security testing based on several known vulnerabilities, high-risk vulnerability, low-risk vulnerability, etc. Deliver an outstanding presentation on the topic using this Before Vs After Implementing Security Testing. Dispense information and present a thorough explanation of High Risk Vulnerabilities, Medium Risk Vulnerabilities, Low Risk Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Of Cyber Security Framework Implementation
Before Vs After Of Cyber Security Framework ImplementationThis slide discusses the before vs after impact of cyber security framework implementation based on aspects like security posture, incident response, etc. Present the topic in a bit more detail with this Before Vs After Of Cyber Security Framework Implementation. Use it as a tool for discussion and navigation on Incident Response, Cyber Security, Framework Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Before Vs After Implementing Of Endpoint Security
Endpoint Security Before Vs After Implementing Of Endpoint SecurityThis slide showcases the comparative analysis of the before versus after implementation of endpoint security situation of an organization. Increase audience engagement and knowledge by dispensing information using Endpoint Security Before Vs After Implementing Of Endpoint Security. This template helps you present information on four stages. You can also present information on Enhanced Compliance, Improved Incident Detection, High Vulnerability To Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security
Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data SecurityThis slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Before Vs After Implementing Tokenization In Data Security. Dispense information and present a thorough explanation of Compliance With Regulations, Reduced Insider Threats, Exposure Of Sensitive Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Before Vs After Implementation Of Application Security
Application Security Implementation Plan Before Vs After Implementation Of Application SecurityThis slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Before Vs After Implementation Of Application Security. Dispense information and present a thorough explanation of Lack Of Encryption, Vulnerable Authentication, Absence Of Regular Security Updates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Impact Of Identity And Access Management Securing Systems With Identity
Before Vs After Impact Of Identity And Access Management Securing Systems With IdentityThis slide showcases the comparative analysis of the before versus after IAM implementation. The purpose of this slide is to discuss the different performance aspects and how IAM has proved beneficial for these aspects. Present the topic in a bit more detail with this Before Vs After Impact Of Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Aspect, Self Registration, Policy Enforcement This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Before Vs After Implementing Web Security
Web Security Upgradation Before Vs After Implementing Web SecurityThis slide showcases the different performance metrics and how web security have improved these metrics. Present the topic in a bit more detail with this Web Security Upgradation Before Vs After Implementing Web Security. Use it as a tool for discussion and navigation on Threats, CSRF Vulnerabilities, SQL Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Before Vs After Implementing Email Security Policies
Email Security Best Practices Before Vs After Implementing Email Security PoliciesThis slide shows the before vs. after comparison of implementing email security policies. The different aspects compared in this slide are data security, phishing incidents, productivity, regulatory compliance, and system downtime. Present the topic in a bit more detail with this Email Security Best Practices Before Vs After Implementing Email Security Policies. Use it as a tool for discussion and navigation on Data Security, Phishing Incidents, Productivity, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Immediate Steps To Be Taken After Email Hack
Email Security Best Practices Immediate Steps To Be Taken After Email HackThis slide demonstrates the steps to be taken after falling for an email scam. These strategies are changing your account password, contacting email service provider, notifying all the contacts, scanning device for viruses and checking other accounts. Introducing Email Security Best Practices Immediate Steps To Be Taken After Email Hack to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Contact Email Provider, Notify Your Contacts, Scan Device For Viruses, Check Other Accounts, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Implementing Web Security Solution
Before Vs After Implementing Web Security SolutionThis slide showcases the different performance metrics and how web security have improved these metrics. Present the topic in a bit more detail with this Before Vs After Implementing Web Security Solution. Use it as a tool for discussion and navigation on Csrf Vulnerabilities, Parameterized Queries, Sql Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Impact On Organization After Implementing Information Strategy Training
Information Security Impact On Organization After Implementing Information Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Security Impact On Organization After Implementing Information Strategy Training. Use it as a tool for discussion and navigation on Implementing, Information, Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Impact On Organization After Implementing
Network Security Impact On Organization After ImplementingThis slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver an outstanding presentation on the topic using this Network Security Impact On Organization After Implementing. Dispense information and present a thorough explanation of Impact On Organization After Implementing Network Security Strategy And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Before And After Results Of Cyber Security Process Changes
Before And After Results Of Cyber Security Process ChangesThis slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Introducing our Before And After Results Of Cyber Security Process Changes set of slides. The topics discussed in these slides are Computer Virus, Data Breach, DOS. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Architecture And Security Review Impact On The Organization After Removing Multi Cloud Complexity
Cloud Architecture And Security Review Impact On The Organization After Removing Multi Cloud ComplexityThis slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Impact On The Organization After Removing Multi Cloud Complexity. Dispense information and present a thorough explanation of Impact On The Organization, Removing Multi Cloud, Complexity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
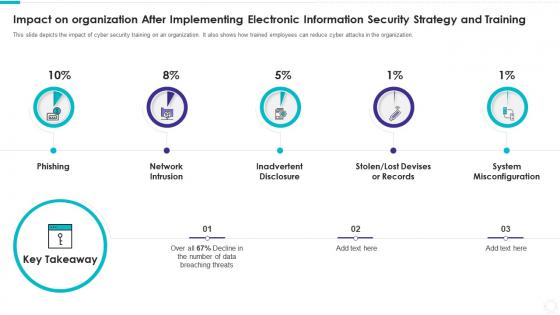 Impact on organization after implementing electronic information security strategy
Impact on organization after implementing electronic information security strategyThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Introducing Impact On Organization After Implementing Electronic Information Security Strategy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen, Lost Devises Or Records, System Misconfiguration, using this template. Grab it now to reap its full benefits.
-
 Incident Management Response Steps After Detecting Security Event
Incident Management Response Steps After Detecting Security EventPresenting our set of slides with Incident Management Response Steps After Detecting Security Event. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assembling Team, Detecting And Ascertaining Source, Containing Damage.
-
 Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions
Cloud Architecture And Security Multi Cloud It Environments After Implementing SolutionsThis slide covers the running all the workloads on a variety of clouds including public cloud, third party public clouds, hosted private clouds, and colocation servers while managing them. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions. This template helps you present information on seven stages. You can also present information on Colocation, Hosted Private Cloud, Migration Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After An Incident Ppt Guidelines
Cyber Security Incident Management Checklist After An Incident Ppt GuidelinesThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Introducing Cyber Security Incident Management Checklist After An Incident Ppt Guidelines to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Incident Management, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist After An Incident Response Strategies Deployment
Cyber Security Incident Management Checklist After An Incident Response Strategies DeploymentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Response Strategies Deployment. This template helps you present information on ten stages. You can also present information on Management, Security, Review using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Architecture Review Of A Cloud Setting Standards After A Clear Picture
Security Architecture Review Of A Cloud Setting Standards After A Clear PictureThis slide covers the guide to set standards after getting a clear picture of the cloud infrastructure and cloud computing software. Increase audience engagement and knowledge by dispensing information using Security Architecture Review Of A Cloud Setting Standards After A Clear Picture. This template helps you present information on two stages. You can also present information on Stack Of The Technology, Investments In Technology, Innovations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After Development And Implementation Of Security
Cyber Security Incident Management Checklist After Development And Implementation Of SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Introducing Cyber Security Incident Management Checklist After Development And Implementation Of Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Review Performance, Incident Response Team, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Before And After Artificial Intelligence
Cyber Security Before And After Artificial IntelligenceThis slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Introducing our Cyber Security Before And After Artificial Intelligence set of slides. The topics discussed in these slides are Endpoints, Social Engineering, Servicec. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Incident Management Checklist After An Incident Deploying Computer Security
Cyber Security Incident Management Checklist After An Incident Deploying Computer SecurityThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident.Introducing Cyber Security Incident Management Checklist After An Incident Deploying Computer Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Reporting Requirements, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 After effects of cyber security attack on firms and clients
After effects of cyber security attack on firms and clientsPresenting this set of slides with name After Effects Of Cyber Security Attack On Firms And Clients. This is a two stage process. The stages in this process are Loss Of Productivity, Business People, Online Banking, Customers, Violates, Transactions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber security it impact on organization after implementing cyber security strategy and training
Cyber security it impact on organization after implementing cyber security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Cyber Security IT Impact On Organization After Implementing Cyber Security Strategy And Training. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effect after implementing cyber risk security awareness program department ppt ideas
Effect after implementing cyber risk security awareness program department ppt ideasThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Increase audience engagement and knowledge by dispensing information using Effect After Implementing Cyber Risk Security Awareness Program Department Ppt Ideas. This template helps you present information on four stages. You can also present information on Effect After Implementing Cyber Risk Security Awareness Program using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Corporate data security awareness effect after implementing cyber risk security awareness program ppt tips
Corporate data security awareness effect after implementing cyber risk security awareness program ppt tipsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Corporate Data Security Awareness Effect After Implementing Cyber Risk Security Awareness Program Ppt Tips. Use it as a tool for discussion and navigation on Accounts Department, Sales Department, It Department, R And D Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security awareness effect after implementing cyber risk security awareness program ppt styles
Information security awareness effect after implementing cyber risk security awareness program ppt stylesThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Information Security Awareness Effect After Implementing Cyber Risk Security Awareness Program Ppt Styles. Use it as a tool for discussion and navigation on Accounts Department, Sales Department, It Department, R And D Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In Organization
Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In OrganizationThis slide compares the company before and after firewall implementation situation. The purpose of this slide is to showcase the decline in malware attacks on different departments after implementing firewall network security. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Before Vs After Firewall Implementation In Organization. Dispense information and present a thorough explanation of Before Firewall Implementation, After Firewall Implementation, Firewall Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Monitor Performance After IT Implementing Organizational Security Training
Dashboard To Monitor Performance After IT Implementing Organizational Security TrainingThe slide showcases a dashboard to evaluate and monitor performance after information technology security management. It includes risk compliance, control issues etc. Deliver an outstanding presentation on the topic using this Dashboard To Monitor Performance After IT Implementing Organizational Security Training. Dispense information and present a thorough explanation of Risk Compliance Dashboard, Control Review Effectiveness, Control Issues By Risk Category using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Review Advanced Protection After Implementing Organizational Security Training
Dashboard To Review Advanced Protection After Implementing Organizational Security TrainingThe slide showcases dashboard that assist in reviewing advance protection after cloud security training of employees in the organization. Present the topic in a bit more detail with this Dashboard To Review Advanced Protection After Implementing Organizational Security Training. Use it as a tool for discussion and navigation on Adaptive Application Control, File Integrity Monitoring, Adaptive Network Hardening. This template is free to edit as deemed fit for your organization. Therefore download it now.



