Powerpoint Templates and Google slides for Accessed
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Integration For Improved Business Understanding Uniform Data Access Integration Technique
Data Integration For Improved Business Understanding Uniform Data Access Integration TechniqueThis slide explains the uniform data access integration method used for data integration. The purpose of this slide is to give a brief of the techniques process and explain various benefits and limitations associated with it. Introducing Data Integration For Improved Business Understanding Uniform Data Access Integration Technique to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Data Access Integration Technique, Standardizes Presentation, Data Storage Location, using this template. Grab it now to reap its full benefits.
-
 Medical Market Access In Powerpoint And Google Slides Cpb
Medical Market Access In Powerpoint And Google Slides CpbPresenting Medical Market Access In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Medical Market Access This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Playstation Early Access In Powerpoint And Google Slides Cpb
Playstation Early Access In Powerpoint And Google Slides CpbPresenting Playstation Early Access In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Playstation Early Access. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Bring Your Own Device Policy Access Authorization Modification And Identity Access Management
Bring Your Own Device Policy Access Authorization Modification And Identity Access ManagementThis slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Introducing Bring Your Own Device Policy Access Authorization Modification And Identity Access Management to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Modification, Identity Access Management, Access Authorization, Hire And Termination, using this template. Grab it now to reap its full benefits.
-
 Bring Your Own Device Policy Overview Of Remote Access Policy For Employees
Bring Your Own Device Policy Overview Of Remote Access Policy For EmployeesThis slide represents the remote access policy to connect to the company network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. Increase audience engagement and knowledge by dispensing information using Bring Your Own Device Policy Overview Of Remote Access Policy For Employees. This template helps you present information on six stages. You can also present information on Accessing Intranet Resources, Illegal Access To Resources, Risk Of Losses Resulting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Bring Your Own Device Policy Privacy And Company Access To Personal Devices
Bring Your Own Device Policy Privacy And Company Access To Personal DevicesThis slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Increase audience engagement and knowledge by dispensing information using Bring Your Own Device Policy Privacy And Company Access To Personal Devices. This template helps you present information on five stages. You can also present information on Analyze Or Preserve Personal, Data To Government Authorities, Voice Mail, Telephone Logs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Transforming From Traditional Access Over Ownership Business Model Framework DT SS
Transforming From Traditional Access Over Ownership Business Model Framework DT SSThis slide presents the framework highlighting the working of access over ownership model. It also mentions the three key components such as seeker, platform and owner. Increase audience engagement and knowledge by dispensing information using Transforming From Traditional Access Over Ownership Business Model Framework DT SS This template helps you present information on Five stages. You can also present information on Service Provider, Accessing Products Services, Reservation And Payment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Transforming From Traditional Overview Sharing Access Over Ownership Business Model DT SS
Transforming From Traditional Overview Sharing Access Over Ownership Business Model DT SSThis slide presents an overview of sharing model access over ownership model detailing its benefits. It also mentions the framework of sharing economy model including three main components seeker, platform and owner. Increase audience engagement and knowledge by dispensing information using Transforming From Traditional Overview Sharing Access Over Ownership Business Model DT SS This template helps you present information on Eight stages. You can also present information on Scalability, Network Effects, Diversified Revenue Streams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Transforming From Traditional Sharing Access Over Ownership Model Business Case DT SS
Transforming From Traditional Sharing Access Over Ownership Model Business Case DT SSThis slide presents the various use cases of sharing access over ownership business model to optimize businesses. It includes car sharing, co-working spaces, accommodation sharing, and music and video streaming. Deliver an outstanding presentation on the topic using this Transforming From Traditional Sharing Access Over Ownership Model Business Case DT SS Dispense information and present a thorough explanation of Scalability And Growth, Revenue Generation, Adaptability To Change using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Market Available Ways To Access GPT 4 How To Use GPT4 For Content Writing ChatGPT SS V
Market Available Ways To Access GPT 4 How To Use GPT4 For Content Writing ChatGPT SS VThis slide showcases available ways which can help users access GPT-4 technology in this generative AI market. It provides details about GPT-4 API waitlist, ChatGPT Plus, ChatSonic and Microsoft Bing AI. Introducing Market Available Ways To Access GPT 4 How To Use GPT4 For Content Writing ChatGPT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Waitlist, Chatsonic, Bing, using this template. Grab it now to reap its full benefits.
-
 Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency Management
Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency ManagementThis slide represents the introduction and commonly used web wallets. This slide outlines the ordinary web wallets in the market, such as bit2me, Binance, coin base, myether wallet, metamask, atomic wallet, etc. Deliver an outstanding presentation on the topic using this Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency Management. Dispense information and present a thorough explanation of Web Wallets, Cryptocurrency Management, Typically More Convenient, Store Cryptocurrency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multiple Trendy Fashion Accessories Offered Building Comprehensive Apparel Business Strategy SS V
Multiple Trendy Fashion Accessories Offered Building Comprehensive Apparel Business Strategy SS VIntroducing Multiple Trendy Fashion Accessories Offered Building Comprehensive Apparel Business Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Gym Shoes, Firefighter Hat, Pair Of Gloves, using this template. Grab it now to reap its full benefits.
-
 Offering Exclusive Pre Launch Access Building Comprehensive Apparel Business Strategy SS V
Offering Exclusive Pre Launch Access Building Comprehensive Apparel Business Strategy SS VThis slide provides glimpse about exclusive pre-launch campaign through email marketing for boosting customer engagement. It includes overview, implementation guidelines, impact, etc. Increase audience engagement and knowledge by dispensing information using Offering Exclusive Pre Launch Access Building Comprehensive Apparel Business Strategy SS V. This template helps you present information on two stages. You can also present information on Overview, Implementation Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process
Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management ProcessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Users Access Request, Approval Rules, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identification And Access Governance Under SAP Cybersecurity
Identification And Access Governance Under SAP CybersecurityThis slide depicts the recognition and access governance under systems, application and product cybersecurity. The purpose of this template is to help understand the role of SAP cybersecurity in identity and access governance. It includes elements such as SAP cloud platform identity, SAP cloud solutions, etc. Introducing our Identification And Access Governance Under SAP Cybersecurity set of slides. The topics discussed in these slides are SAP Fieldglass, Identity Lifecycle Management, SAP Success Variables. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Maturity Model To Access Corporate Capability Development
Maturity Model To Access Corporate Capability DevelopmentThis slide represents maturity model that helps corporates to track and monitor capability development process effectively for operational enhancement. It includes various stages such as initial, repeatable, defined, managed, and optimizing stage. Introducing our Maturity Model To Access Corporate Capability Development set of slides. The topics discussed in these slides are Optimizing, Managed, Repeatable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Accessing SEO Metrics For Measuring B2B Marketing Performance
Accessing SEO Metrics For Measuring B2B Marketing PerformanceThis slide represents the SEO metrics that help B2B businesses access their marketing campaigns effectively and make required improvements. It includes metrics such as indexing, page performance, page view, etc. Presenting our set of slides with Accessing SEO Metrics For Measuring B2B Marketing Performance. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Measuring, Marketing, Performance.
-
 Accessing Untapped Market For Boosting Profitability
Accessing Untapped Market For Boosting ProfitabilityThis slide represents untapped market for profitability and includes parameters, methods, projected profit percentage and impact. Presenting our set of slides with Accessing Untapped Market For Boosting Profitability. This exhibits information onone stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Untapped, Accessing, Market.
-
 Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB
Benefits Of Cloud Access Security Broker 2 0 Next Generation CASBThis slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Introducing Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Coverage, Cost Effective, Improved Visibility using this template. Grab it now to reap its full benefits.
-
 Benefits Of Cloud Access Security Broker Next Generation CASB
Benefits Of Cloud Access Security Broker Next Generation CASBThis slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Present the topic in a bit more detail with this Benefits Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Risk Visibility, Threat Prevention, Assessment And Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Next Generation CASB
Best Practices To Implement Cloud Access Security Broker Next Generation CASBThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB, Best Practices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Adopt A Cloud Access Security Broker Next Generation CASB
Checklist To Adopt A Cloud Access Security Broker Next Generation CASBThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Deliver an outstanding presentation on the topic using this Checklist To Adopt A Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Vendor Landscape, Conduct A Trial, Functionalities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And Encryption Next Generation CASB
Cloud Access Security Broker And Encryption Next Generation CASBThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Present the topic in a bit more detail with this Cloud Access Security Broker And Encryption Next Generation CASB Use it as a tool for discussion and navigation on Security That Tracks Data, Terminated Moment, Content Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker And Secure Web Gateway Next Generation CASB
Cloud Access Security Broker And Secure Web Gateway Next Generation CASBThis slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker And Secure Web Gateway Next Generation CASB Dispense information and present a thorough explanation of Cloud App Data, Get Dynamic Control, Simplify Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And User Authentication Next Generation CASB
Cloud Access Security Broker And User Authentication Next Generation CASBThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication Next Generation CASB Use it as a tool for discussion and navigation on Cloud Apps, Transaction Detail, User Threat Data This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Introduction Next Generation CASB
Cloud Access Security Broker CASB Introduction Next Generation CASBThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Present the topic in a bit more detail with this Cloud Access Security Broker CASB Introduction Next Generation CASB Use it as a tool for discussion and navigation on Deployment Models, Out Of Band Deployment, Inline Deployment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Implementation Roadmap Next Generation CASB
Cloud Access Security Broker Implementation Roadmap Next Generation CASBThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Implementation Roadmap Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Portfolio, Cloud Application, Systems using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Life Cycle Protection Next Generation CASB
Cloud Access Security Broker Life Cycle Protection Next Generation CASBIncrease audience engagement and knowledge by dispensing information using Cloud Access Security Broker Life Cycle Protection Next Generation CASB This template helps you present information on four stages. You can also present information on Identify Needs, Control Usage, Adaptive Access, Verify Usage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Compliance Next Generation CASB
Cloud Access Security Broker Pillar Compliance Next Generation CASBThis slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Introducing Cloud Access Security Broker Pillar Compliance Next Generation CASB to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Risk Domains, Costly Breaches using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Data Security Next Generation CASB
Cloud Access Security Broker Pillar Data Security Next Generation CASBThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Data Security Next Generation CASB This template helps you present information on five stages. You can also present information on Complex Cloud, Sensitive Material, Risk Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Overview Next Generation CASB
Cloud Access Security Broker Pillar Overview Next Generation CASBThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Cloud Access Security Broker Pillar Overview Next Generation CASB to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Data Security, Threat Protection, Visibility using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Threat Protection Next Generation CASB
Cloud Access Security Broker Pillar Threat Protection Next Generation CASBThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Next Generation CASB This template helps you present information on five stages. You can also present information on Services, Cloud Storage, Compromised Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Visibility Next Generation CASB
Cloud Access Security Broker Pillar Visibility Next Generation CASBThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Present the topic in a bit more detail with this Cloud Access Security Broker Pillar Visibility Next Generation CASB Use it as a tool for discussion and navigation on Visibility Topography, Working Process, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB
Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASBThis slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Introducing Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Encryption, Benefits using this template. Grab it now to reap its full benefits.
-
 Leading Cloud Access Security Broker Platforms Next Generation CASB
Leading Cloud Access Security Broker Platforms Next Generation CASBThis slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Introducing Leading Cloud Access Security Broker Platforms Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Amazon Web Services, Cloud Access, Broker Platforms using this template. Grab it now to reap its full benefits.
-
 Overview Of Cloud Access Security Broker Architecture Next Generation CASB
Overview Of Cloud Access Security Broker Architecture Next Generation CASBThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Present the topic in a bit more detail with this Overview Of Cloud Access Security Broker Architecture Next Generation CASB Use it as a tool for discussion and navigation on Organization, Direct To Cloud, Broker Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Popular Cloud Access Security Broker Vendors Next Generation CASB
Popular Cloud Access Security Broker Vendors Next Generation CASBThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Deliver an outstanding presentation on the topic using this Popular Cloud Access Security Broker Vendors Next Generation CASB Dispense information and present a thorough explanation of Forcepoint, Cisco Systems, Microsoft, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Deploy Cloud Access Security Broker Next Generation CASB
Steps To Deploy Cloud Access Security Broker Next Generation CASBThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Introducing Steps To Deploy Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Location, Deployment Model, Release Model using this template. Grab it now to reap its full benefits.
-
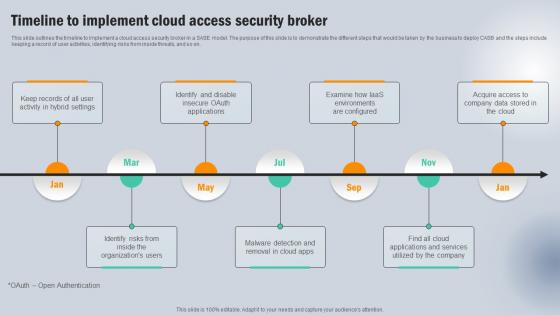 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
 Training Program For Cloud Access Security Broker Next Generation CASB
Training Program For Cloud Access Security Broker Next Generation CASBThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Training Program For Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Agenda, System Requirements, Deployment Options This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Cases Of Cloud Access Security Broker Next Generation CASB
Use Cases Of Cloud Access Security Broker Next Generation CASBPresent the topic in a bit more detail with this Use Cases Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Unsanctioned Apps, Sanctioned Apps, Cloud Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Provide Access To Resources That Streamline Partner Onboarding Nurturing Relationships
Provide Access To Resources That Streamline Partner Onboarding Nurturing RelationshipsThis slide details the access to resources to be provided during partner onboarding stage. It includes tools such as, marketing kit, partner portal, referral program and product or service demos. Deliver an outstanding presentation on the topic using this Provide Access To Resources That Streamline Partner Onboarding Nurturing Relationships Dispense information and present a thorough explanation of Marketing Kit, Partner Portal, Referral Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security
Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client SecurityThis slide outlines the many ways to control access and guarantee web client security policy. The purpose of this slide is to highlight the firewall techniques to limit user access and confirm web user security, such as service control, direction control, user control and behavior control. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security This template helps you present information on Four stages. You can also present information on Market By Deployment, Market By Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Continuous Software Access Monitoring In Devops Continuous Delivery And Integration With Devops
Continuous Software Access Monitoring In Devops Continuous Delivery And Integration With DevopsPresent the topic in a bit more detail with this Continuous Software Access Monitoring In Devops Continuous Delivery And Integration With Devops. Use it as a tool for discussion and navigation on Name, Access Level, License Source, Date Added. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 3D Verse Fusion Of Physical Reality Accessing Metaverse Through Technologies Virtual AI SS V
3D Verse Fusion Of Physical Reality Accessing Metaverse Through Technologies Virtual AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as virtual reality. It is simulated 3D environment that enable users interaction with virtual space. Introducing 3D Verse Fusion Of Physical Reality Accessing Metaverse Through Technologies Virtual AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Stunning Landscapes, Virtual Concerts, Seamless Integration, Virtual Environment, using this template. Grab it now to reap its full benefits.
-
 3D Verse Fusion Of Physical Reality How Metaverse Can Be Accessed By Users AI SS V
3D Verse Fusion Of Physical Reality How Metaverse Can Be Accessed By Users AI SS VThis slide provides information regarding different ways through metaverse can be executed by connecting with VR interface such as headset, game console, to gain immersive metaverse experience. Increase audience engagement and knowledge by dispensing information using 3D Verse Fusion Of Physical Reality How Metaverse Can Be Accessed By Users AI SS V. This template helps you present information on seven stages. You can also present information on Several Metaverse Experiences, Platforms, Myriad Unintegrated Devices, Metaverse Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Accessing Metaverse Through Technologies 3D Modeling 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies 3D Modeling 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as 3D modeling. It is process of creating 3D representation of object or surface in virtual space. Introducing Accessing Metaverse Through Technologies 3D Modeling 3D Verse Fusion Of Physical Reality AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Metaverse Experience, Physical Environment, Risk Of Accidents Or Collisions, Physical Experience, using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as blockchain. It enables cryptocurrencies bitcoin, NFTs to buy or sell digital assets in metaverse space. Increase audience engagement and knowledge by dispensing information using Accessing Metaverse Through Technologies 3D Verse Fusion Of Physical Reality AI SS V. This template helps you present information on two stages. You can also present information on Blockchain Is Decentralized Ledger, Cryptocurrency Transactions, Block Comprises Of Transaction Information, Timestamp And Cryptographic Hash using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Accessing Metaverse Through Technologies Ar Mr 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Ar Mr 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as AR, MR and VR. It depicts the metaverse competencies, pros, cons, market, use case, and devices utilized by AR, VR and MR technologies in metaverse. Present the topic in a bit more detail with this Accessing Metaverse Through Technologies Ar Mr 3D Verse Fusion Of Physical Reality AI SS V. Use it as a tool for discussion and navigation on Remote Expert Guidance, Digital Workflow, Field Service, Audit And Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Metaverse Through Technologies Artificial 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Artificial 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Introducing Accessing Metaverse Through Technologies Artificial 3D Verse Fusion Of Physical Reality AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Developing And Managing, Digital Entities, Real Time Translation, Artificial Intelligence, Customization, using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies Augmented 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Augmented 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as augmented reality. It helps in offering real world experience to users while interacting with digital elements. Increase audience engagement and knowledge by dispensing information using Accessing Metaverse Through Technologies Augmented 3D Verse Fusion Of Physical Reality AI SS V. This template helps you present information on seven stages. You can also present information on Augmented Reality, Real World Scenario, Leveraging Visual, Auditory And Relevant Sensory Interactive using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Accessing Metaverse Through Technologies Brain 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Brain 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as brain-computer interfaces. It is a technology that processes individuals neural activity and allow users to communicate with physical world without conventional neuromuscular platforms. Deliver an outstanding presentation on the topic using this Accessing Metaverse Through Technologies Brain 3D Verse Fusion Of Physical Reality AI SS V. Dispense information and present a thorough explanation of Development And Growth Of Metaverse, Brain Computer Interfaces, Individuals Neural Activity, Conventional Neuromuscular Platforms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Accessing Metaverse Through Technologies Edge 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Edge 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as edge computing. It enables processing of data on-site for faster information processing to reduce network latency. Introducing Accessing Metaverse Through Technologies Edge 3D Verse Fusion Of Physical Reality AI SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Reduce Network Latency, Edge Computing Assists Metaverse, Reducing Network Latency, Seamless Communication, using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies Extended Reality 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Extended Reality 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as extended reality. It is combination of AR, VR and MR for users to interact with each other in metaverse space. Increase audience engagement and knowledge by dispensing information using Accessing Metaverse Through Technologies Extended Reality 3D Verse Fusion Of Physical Reality AI SS V. This template helps you present information on seven stages. You can also present information on Development And Growth Of Metaverse, Emerging Technologies, Technology Focuses On Collaborating using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Accessing Metaverse Through Technologies Internet 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Internet 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as internet of things IoT. It is a robust network of interconnected physical devices to leverage link among real world and virtual space. Introducing Accessing Metaverse Through Technologies Internet 3D Verse Fusion Of Physical Reality AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Development And Growth Of Metaverse, Emerging Technologies, Internet Of Things, Robust Network, Robust Digital Network, using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies Spatial 3D Verse Fusion Of Physical Reality AI SS V
Accessing Metaverse Through Technologies Spatial 3D Verse Fusion Of Physical Reality AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as spatial computing. It is a technology that enable computers to unlock interaction with physical world immensely with augmented and virtual reality. Increase audience engagement and knowledge by dispensing information using Accessing Metaverse Through Technologies Spatial 3D Verse Fusion Of Physical Reality AI SS V. This template helps you present information on six stages. You can also present information on Development And Growth Of Metaverse, Emerging Technologies, Spatial Computing, Gaming And Entertainment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Renewable Energy Access Industry Analysis
Renewable Energy Access Industry AnalysisThe following slide assists organizations in analyzing the renewable energy access industry, focusing on universal access, improved living conditions, economic empowerment, and environmental benefits, guiding informed actions for sustainable development. Introducing our premium set of slides with Renewable Energy Access Industry Analysis. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Universal Energy Access, Renewable Energy Solutions, Economic Empowerment. So download instantly and tailor it with your information.
-
 Multiple Trendy Fashion Accessories Efficient Marketing Campaign Plan Strategy SS V
Multiple Trendy Fashion Accessories Efficient Marketing Campaign Plan Strategy SS VIntroducing Multiple Trendy Fashion Accessories Efficient Marketing Campaign Plan Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Trendy, Accessories, Offered, using this template. Grab it now to reap its full benefits.





