Powerpoint Templates and Google slides for Access time
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 IAM Process For Effective Access Cost Of Identity And Access Management Over Time
IAM Process For Effective Access Cost Of Identity And Access Management Over TimeThis slide showcases the cost required for Identity and Access Management over time. The purpose of this slide is to depict the cost of IAM through a graph showing the relationship between deploying identity management and maintaining existing management tools. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Cost Of Identity And Access Management Over Time. Dispense information and present a thorough explanation of Cost Of Identity And Access, Management Over Time, Existing Management Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
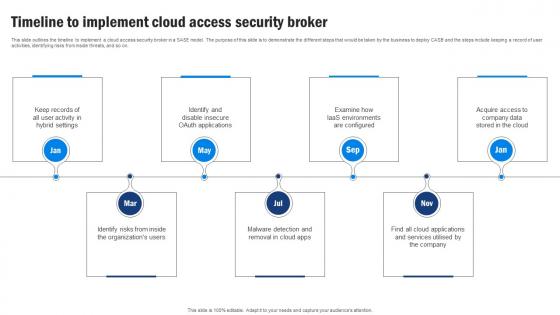
 Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a Cloud Access Security Broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Cloud Applications, Malware Detection And Removal, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.
-
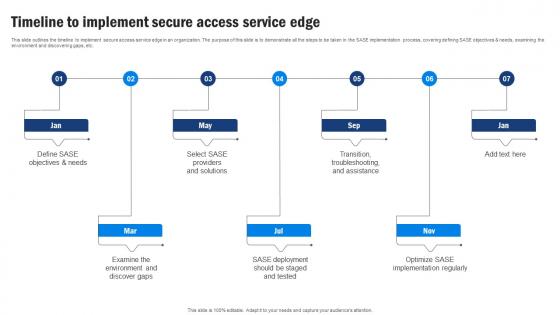
 Timeline To Implement Secure Access Service Edge Cloud Security Model
Timeline To Implement Secure Access Service Edge Cloud Security ModelThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Solutions, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Timeline To Implement Cloud Access Security Broker
Sase Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Security Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Timeline, Applications, Environments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Timeline To Implement Secure Access Service Edge
Sase Security Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Security Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Troubleshooting, using this template. Grab it now to reap its full benefits.
-
 Timeline To Cloud Access Security Broker Secure Access Service Edge Sase
Timeline To Cloud Access Security Broker Secure Access Service Edge SaseThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Cloud Access Security Broker Secure Access Service Edge Sase. This template helps you present information on seven stages. You can also present information on Timeline, Implement, Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase
Timeline To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Environment, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge SASE Network Security
Timeline To Implement Secure Access Service Edge SASE Network SecurityThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge SASE Network Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Solutions, Regularly, using this template. Grab it now to reap its full benefits.
-
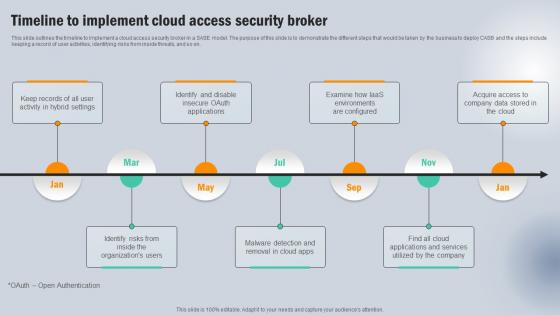 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Secure Access Service Edge
Sase Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Jan, Mar, May, Jul, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Zero Trust Network Access Model Identity Defined Networking
Timeline To Implement Zero Trust Network Access Model Identity Defined NetworkingThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Identity Defined Networking to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assess The Environment, Data Network, Timeline using this template. Grab it now to reap its full benefits.
-
 Server Security Maintenance Timeline For Preventing Unauthorized Access
Server Security Maintenance Timeline For Preventing Unauthorized AccessFollowing slide highlights timeline for server security maintenance by preventing unauthorized access, also including tasks such as installation of new package, updates of other applications, review server accessibility, etc. Presenting our well structured Server Security Maintenance Timeline For Preventing Unauthorized Access. The topics discussed in this slide are Review Server Accessibility, Firewall Rules, User Password Change. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Timeline To Implement Zero Trust Network Access Model Ppt File Designs
Timeline To Implement Zero Trust Network Access Model Ppt File DesignsThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Ppt File Designs to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Zero Trust Team, Network, Applications, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker CASB Cloud Security
Timeline To Implement Cloud Access Security Broker CASB Cloud SecurityThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker CASB Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Malware Detection, Identify Risks, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Timeline To Implement Identity And Access Management Plan
IAM Process For Effective Access Timeline To Implement Identity And Access Management PlanThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing IAM Process For Effective Access Timeline To Implement Identity And Access Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Timeline To Implement Identity, Access Management Plan, Regular System Maintenance, using this template. Grab it now to reap its full benefits.
-
 Time Framework For Implementing IAM Proposal Identity And Access Management
Time Framework For Implementing IAM Proposal Identity And Access ManagementThis slide shows the timeline for implementing the Identity and Access Management plan in an organization the key steps include defining the project objective, etc. Increase audience engagement and knowledge by dispensing information using Time Framework For Implementing IAM Proposal Identity And Access Management This template helps you present information on five stages. You can also present information on Determining Compliance Requirements, Developing And Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Identity And Access Management Plan IAM Implementation Plan
Timeline To Implement Identity And Access Management Plan IAM Implementation PlanThis slide shows the timeline for implementing the Identity and Access Management plan in an organization the key steps include defining the project objective, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Identity And Access Management Plan IAM Implementation Plan. This template helps you present information on five stages. You can also present information on Define Project Objectives, Determine Compliance Requirements, Establish Regular Maintenance Schedule using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Time For Various Memory Levels Memory Hierarchy
Access Time For Various Memory Levels Memory HierarchyThis slide showcases the approximate access time of various memory levels such as registers, cache memory, main memory, flash drives, etc. Present the topic in a bit more detail with this Access Time For Various Memory Levels Memory Hierarchy Use it as a tool for discussion and navigation on Cache Memory, Main Memory, Flash Drives This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost Per Bit And Access Time Ratio In Memory Hierarchy
Cost Per Bit And Access Time Ratio In Memory HierarchyThis slide highlights the hierarchy of different storage units based on increasing order of access time ratio and cost per bit. Increase audience engagement and knowledge by dispensing information using Cost Per Bit And Access Time Ratio In Memory Hierarchy This template helps you present information on two stages. You can also present information on Main Memory, Cache Memory, Register Memory using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Evolution Timeline Of Wireless Access Points WAP
Evolution Timeline Of Wireless Access Points WAPThis slide showcases the evolution of Wireless Access Points over time. The purpose of this slide is to outline the evolution timeline of Wireless Access Points, including the technology introduced at different year intervals from 1997 to 2023. Increase audience engagement and knowledge by dispensing information using Evolution Timeline Of Wireless Access Points WAP. This template helps you present information on Seven stages. You can also present information on Introduced Iot Device Management Features, Enhancing Network Reliability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wireless Access Points Installation Timeline
Wireless Access Points Installation TimelineThis slide represents the timeframe for configuring the Wireless Access Points in an organization. The purpose of this slide is to outline the timeline for organizations that includes the various steps to configure Wireless Access Points. Increase audience engagement and knowledge by dispensing information using Wireless Access Points Installation Timeline. This template helps you present information on Nine stages. You can also present information on Physical Installation Of Waps, Guest Network Setup, Quality Of Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access to real time reporting powerpoint slides background
Access to real time reporting powerpoint slides backgroundPresenting access to real time reporting powerpoint slides background. This is a access to real time reporting powerpoint slides background. This is a three stage process. The stages in this process are increase employee satisfaction, access to real time reporting, secure company assists.
-
 Erp system framework implementation keep business real time data accessibility status in the company
Erp system framework implementation keep business real time data accessibility status in the companyThis slide shows the future estimated Real Time Data Accessibility status of the company in terms of accessible and not accessible after implementation of an integrated ERP system with advanced business intelligence and proactive decision making. Present the topic in a bit more detail with this Erp System Framework Implementation Keep Business Real Time Data Accessibility Status In The Company. Use it as a tool for discussion and navigation on Accessibility, Company, Accessible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Erp system framework implementation to keep business current real time data accessibility status company
Erp system framework implementation to keep business current real time data accessibility status companyThis slide shows the current Real Time Data Accessibility status of the company in terms of accessible and not accessible. Present the topic in a bit more detail with this Erp System Framework Implementation To Keep Business Current Real Time Data Accessibility Status Company. Use it as a tool for discussion and navigation on Current Real Time Data Accessibility Status In The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Erp system framework implementation real time data accessibility status in the company
Erp system framework implementation real time data accessibility status in the companyThis slide shows the current Real Time Data Accessibility status of the company in terms of accessible and not accessible Deliver an outstanding presentation on the topic using this Erp System Framework Implementation Real Time Data Accessibility Status In The Company. Dispense information and present a thorough explanation of Current Real Time Data Accessibility Status In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Future estimated real time data accessibility erp system framework implementation
Future estimated real time data accessibility erp system framework implementationThis slide shows the future estimated Real Time Data Accessibility status of the company in terms of accessible and not accessible after implementation of an integrated ERP system with advanced business intelligence and proactive decision making Deliver an outstanding presentation on the topic using this Future Estimated Real Time Data Accessibility Erp System Framework Implementation. Dispense information and present a thorough explanation of Future Estimated Real Time Data Accessibility Status in the Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Real Time Data Accessibility Overview Cloud ERP System Framework
Current Real Time Data Accessibility Overview Cloud ERP System FrameworkThe slide provides information about the first and second step defining project scope and selecting an ERP system that is involved in the ERP Implementation process that must be followed by the company in order to achieve the objectives of ERP Enterprise Resource Planning and in order to keep business up to date, streamline business processes, establish SOPs etc. Deliver an outstanding presentation on the topic using this Current Real Time Data Accessibility Overview Cloud ERP System Framework. Dispense information and present a thorough explanation of Current Real Time Data Accessibility Status In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Future Estimated Real Time Data Accessibility Overview Cloud ERP System Framework
Future Estimated Real Time Data Accessibility Overview Cloud ERP System FrameworkThis slide shows the future estimated Real Time Data Accessibility status of the company in terms of accessible and not accessible after implementation of an integrated ERP system with advanced business intelligence and proactive decision making Deliver an outstanding presentation on the topic using this Future Estimated Real Time Data Accessibility Overview Cloud ERP System Framework. Dispense information and present a thorough explanation of Future Estimated Real Time Data Accessibility Status In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ERP System Framework Current Real Time Data Accessibility Status In The Company
ERP System Framework Current Real Time Data Accessibility Status In The CompanyThis slide shows the current Real Time Data Accessibility status of the company in terms of accessible and not accessible. Present the topic in a bit more detail with this ERP System Framework Current Real Time Data Accessibility Status In The Company. Use it as a tool for discussion and navigation on Real Time Data Accessible, Real Time Data Not Accessible, Business Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ERP System Framework Future Estimated Real Time Data Accessibility Status In The Company
ERP System Framework Future Estimated Real Time Data Accessibility Status In The CompanyThis slide shows the future estimated real time data accessibility status of the company in terms of accessible and not accessible after implementation of an integrated ERP system with advanced business intelligence and proactive decision making. Deliver an outstanding presentation on the topic using this ERP System Framework Future Estimated Real Time Data Accessibility Status In The Company. Dispense information and present a thorough explanation of Real Time Data Accessible, Real Time Data Not Accessible, Integrated ERP system using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi for unauthorized disclosures qar completion time production access presentation slide
Kpi for unauthorized disclosures qar completion time production access presentation slidePresenting kpi for unauthorized disclosures qar completion time production access presentation slide. This presentation slide shows three Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is percentage of HIPAA Unauthorized Disclosures. The second KPI is QAR Completion Time and the third is Developer Access to Production. These KPI Powerpoint graphics are all data driven,and the shape automatically adjusts according to your data. Just right click on the KPI graphic,enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Kpi for user share direct url access last member login time powerpoint slide
Kpi for user share direct url access last member login time powerpoint slidePresenting kpi for user share direct url access last member login time powerpoint slide. This presentation slide shows three Key Performance Indicators or KPIs in a Dashboard style design. The first KPI that can be shown is Heavy User Share. The second KPI is of Direct URL Access and the third is Average Time Since Last Member Login. These KPI Powerpoint graphics are all data driven, and the shape automatically adjusts according to your data. Just right click on the KPI graphic, enter the right value and the shape will adjust automatically. Make a visual impact with our KPI slides.
-
 Steps To Access Online Banking For First Time Users
Steps To Access Online Banking For First Time UsersThis slide mentions the steps to access online banking for first time users. This includes gathering account number, opening online portal, registering for access and account log in. Introducing our premium set of slides with Steps To Access Online Banking For First Time Users. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Steps To Access, Online Banking, First Time Users. So download instantly and tailor it with your information.
-
 SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait
SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint PortraitThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Organizations Users, Cloud Apps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure
SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint BrochureThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on SASE Objectives And Needs, SASE Providers And Solutions,Transition, Troubleshooting, And Assistance, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips
Timeline To Implement Cloud Access Security Broker Ppt Ideas TipsThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips. This template helps you present information on seven stages. You can also present information on Keep Records, Identify And Disable, Examine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ZTNA Timeline To Implement Zero Trust Network Access Model
ZTNA Timeline To Implement Zero Trust Network Access ModelIntroducing ZTNA Timeline To Implement Zero Trust Network Access Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assess The Environment, Implement, Technology, using this template. Grab it now to reap its full benefits.
-
 Access real time reporting secure company assets onboard manage
Access real time reporting secure company assets onboard managePresenting this set of slides with name - Access Real Time Reporting Secure Company Assets Onboard Manage. This is an editable four stages graphic that deals with topics like Access Real Time Reporting, Secure Company Assets, Onboard Manage to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Real time access account across multiple carriers onboard manage
Real time access account across multiple carriers onboard managePresenting this set of slides with name - Real Time Access Account Across Multiple Carriers Onboard Manage. This is an editable four graphic that deals with topics like Real Time Access Account, Across Multiple Carriers, Onboard Manage to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Access control system showing real time compatible solutions
Access control system showing real time compatible solutionsPresenting this set of slides with name - Access Control System Showing Real Time Compatible Solutions. This is a one stage process. The stages in this process are Access Control, Information Security, Identity Management.
-
 Proper coding time activities time resources web access
Proper coding time activities time resources web accessPresenting this set of slides with name - Proper Coding Time Activities Time Resources Web Access. This is an editable five stages graphic that deals with topics like Proper Coding Time, Activities Time Resources, Web Access to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Unaware prospects direct financial benefits last time accessed
Unaware prospects direct financial benefits last time accessedPresenting this set of slides with name - Unaware Prospects Direct Financial Benefits Last Time Accessed. This is an editable five stages graphic that deals with topics like Unaware Prospects, Direct Financial Benefits, Last Time Accessed to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data quality accuracy relevance accessibility clarity timelines completeness
Data quality accuracy relevance accessibility clarity timelines completenessPresenting this set of slides with name - Data Quality Accuracy Relevance Accessibility Clarity Timelines Completeness. This is a six stage process. The stages in this process are Data Quality, Data Governance, Data Management.
-
 End to end returns management automation real time access ppt templates
End to end returns management automation real time access ppt templatesThe purpose of this slide is to display streamlined returns process that improve stakeholder performance and reduce costs. Presenting this set of slides with name End To End Returns Management Automation Real Time Access Ppt Templates. The topics discussed in these slides are End End Returns, Management Automation, Real Time Access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Returns management end to end returns management automation time access ppts rules
Returns management end to end returns management automation time access ppts rulesThe purpose of this slide is to display streamlined returns process that improve stakeholder performance and reduce costs. Present the topic in a bit more detail with this Returns Management End To End Returns Management Automation Time Access Ppts Rules. Use it as a tool for discussion and navigation on End Returns, Management Automation, Time Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity access management timeline ppt powerpoint presentation model summary cpb
Identity access management timeline ppt powerpoint presentation model summary cpbPresenting our Identity Access Management Timeline Ppt Powerpoint Presentation Model Summary Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Identity Access Management Timeline This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Timeline drug discovery and development processes to access potential product toxicity
Timeline drug discovery and development processes to access potential product toxicityIncrease audience engagement and knowledge by dispensing information using Timeline Drug Discovery And Development Processes To Access Potential Product Toxicity. This template helps you present information on six stages. You can also present information on Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.



