Powerpoint Templates and Google slides for Access Protocol
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 IAM Processes For Effective Access Management Powerpoint Presentation Slides
IAM Processes For Effective Access Management Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this IAM Processes For Effective Access Management Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with seventy one slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Effective data preparation to make data accessible and ready for processing complete deck
Effective data preparation to make data accessible and ready for processing complete deckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Effective Data Preparation To Make Data Accessible And Ready For Processing Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Efficient Data Preparation To Make Information Accessible And Ready For Processing Complete Deck
Efficient Data Preparation To Make Information Accessible And Ready For Processing Complete DeckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Efficient Data Preparation To Make Information Accessible And Ready For Processing Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fourty seven slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Drug discovery and development processes to access potential product toxicity complete deck
Drug discovery and development processes to access potential product toxicity complete deckDeliver an informational PPT on various topics by using this Drug Discovery And Development Processes To Access Potential Product Toxicity Complete Deck. This deck focuses and implements best industry practices, thus providing a birds eye view of the topic. Encompassed with fourty slides, designed using high quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 IAM Process For Effective Access Cost Of Identity And Access Management Over Time
IAM Process For Effective Access Cost Of Identity And Access Management Over TimeThis slide showcases the cost required for Identity and Access Management over time. The purpose of this slide is to depict the cost of IAM through a graph showing the relationship between deploying identity management and maintaining existing management tools. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Cost Of Identity And Access Management Over Time. Dispense information and present a thorough explanation of Cost Of Identity And Access, Management Over Time, Existing Management Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Insights Reporting Dashboard IAM Process For Effective Access
Identity And Access Management Insights Reporting Dashboard IAM Process For Effective AccessThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard IAM Process For Effective Access. Dispense information and present a thorough explanation of Identity And Access Management, Insights Reporting Dashboard, System Checks, Failed Task Results using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective Access
Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective AccessThis slide represents the Identity and Access Management technology adoption lifecycle. The purpose of this slide is to discuss the mapping of Identity and Access Management technologies to the technology adoption lifecycle. Present the topic in a bit more detail with this Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective Access. Use it as a tool for discussion and navigation on Identity And Access Management, Technology Adoption Lifecycle, Password Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Businesses Can Integrate Procedure To Access Chatgpt 4 And Chatgpt Chatgpt SS V
How Businesses Can Integrate Procedure To Access Chatgpt 4 And Chatgpt Chatgpt SS VThis slide showcases process to get access key for OpenAIs ChatGPT 3 and ChatGPT 4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Introducing How Businesses Can Integrate Procedure To Access Chatgpt 4 And Chatgpt Chatgpt SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Use Natural Language, Openai Allows, using this template. Grab it now to reap its full benefits.
-
 Remote Access Protocol Examples In Powerpoint And Google Slides Cpb
Remote Access Protocol Examples In Powerpoint And Google Slides CpbPresenting Remote Access Protocol Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Remote Access Protocol Examples. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V
Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS VThis slide showcases process to get access key for OpenAIs ChatGPT 3 and ChatGPT 4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Increase audience engagement and knowledge by dispensing information using Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V. This template helps you present information on four stages. You can also present information on Client Library, Installation, Switching, Requirements, Natural Language using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V
Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS VThis slide showcases process to get access key for OpenAIs ChatGPT-3 and ChatGPT-4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Introducing Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Client Library, Installation, Switching, Natural Language Processing, using this template. Grab it now to reap its full benefits.
-
 Access Protocol In Powerpoint And Google Slides Cpb
Access Protocol In Powerpoint And Google Slides CpbPresenting our Access Protocol In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Protocol This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Cloud Access Security Broker Working Process
Sase Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, an remediation. Deliver an outstanding presentation on the topic using this Sase Security Cloud Access Security Broker Working Process. Dispense information and present a thorough explanation of Remediation, Classification, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Secure Access Service Edge Sase
Cloud Access Security Broker Working Process Secure Access Service Edge SaseThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Information, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process
Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management ProcessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Users Access Request, Approval Rules, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Network Access Implementation Challenges Ppt File Rules
Zero Trust Network Access Implementation Challenges Ppt File RulesThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Present the topic in a bit more detail with this Zero Trust Network Access Implementation Challenges Ppt File Rules. Use it as a tool for discussion and navigation on Hardware, Security Vulnerabilities, Software Modifications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process CASB Cloud Security
Cloud Access Security Broker Working Process CASB Cloud SecurityThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process CASB Cloud Security. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For IAM Process For Effective Access Management
Agenda For IAM Process For Effective Access ManagementIntroducing Agenda For IAM Process For Effective Access Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Effective Access Management, Risks And Issue Associated, Examine The IAM Services, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access 30 60 90 Days Plan For IAM Implementation
IAM Process For Effective Access 30 60 90 Days Plan For IAM ImplementationThis slide represents the 30-60-90-day plan for identity and access management implementation. The purpose of this slide is to showcase the approaches that need to be followed as short-term, medium, and long-term goals to implement the IAM process. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access 30 60 90 Days Plan For IAM Implementation. This template helps you present information on three stages. You can also present information on Access Management Implementation, Long Term Goals, Track System Performance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access About Directory Services And Aggregation Of IAM
IAM Process For Effective Access About Directory Services And Aggregation Of IAMThis slide discusses the directory services and aggregation of identity management. The purpose of this slide is to explain the identity stores stored in organizational stores and aggregation that involves discovering, selecting, and determining authority sources. Present the topic in a bit more detail with this IAM Process For Effective Access About Directory Services And Aggregation Of IAM. Use it as a tool for discussion and navigation on Integration And Synchronization Techniques, Determining Authoritative Sources, Aggregation And Synchronization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access About IBM Identity And Access Management
IAM Process For Effective Access About IBM Identity And Access ManagementThis slide discusses the Identity and Access Management leader IBM IAM. The purpose of this slide is to examine the IBM IAM, which offers expertise in large-scale computing projects and addresses various complex enterprise challenges. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access About IBM Identity And Access Management. Dispense information and present a thorough explanation of Identity And Access Management, Complex Enterprise Challenges, Large Scale Computing Projects using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access About Identity And Access Management Controls
IAM Process For Effective Access About Identity And Access Management ControlsThis slide discusses the various controls of Identity and Access Management. The purpose of this slide is to explain the controls of IAM, which include unique IDs, devices, services, application accounts, access approval, and account management. Present the topic in a bit more detail with this IAM Process For Effective Access About Identity And Access Management Controls. Use it as a tool for discussion and navigation on Service And Application Accounts, Account Management, Applicable Data Protection Categorization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access About Microsoft Azure Active Directory IAM Leader
IAM Process For Effective Access About Microsoft Azure Active Directory IAM LeaderThis slide represents the Identity and Access Management leader Microsoft Azure directory. The purpose of this slide is to discuss the Microsoft Azure active directory that helps provide unique naming, structure, and pricing systems compared to others. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access About Microsoft Azure Active Directory IAM Leader. Dispense information and present a thorough explanation of Identity And Access Management, Microsoft Azure Directory, Structure And Pricing Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Authorization Service Of Identity And Access Management
IAM Process For Effective Access Authorization Service Of Identity And Access ManagementThis slide showcases the Identity and Access Management authorization service. The purpose of this slide is to explain the authorization services that grant user privileges, such as permission, access rights, and IAM challenges targeted by authorization. Introducing IAM Process For Effective Access Authorization Service Of Identity And Access Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Discretionary Access Control, Mandatory Access Control, Role Based Access Control, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management Implementation
IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management ImplementationThis slide showcases the comparative analysis of the before versus after IAM implementation. The purpose of this slide is to discuss the different performance aspects and how IAM has proved beneficial for these aspects. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management Implementation. Dispense information and present a thorough explanation of Credential Management, Identity Provisioning, Policy Enforcement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Budget Allocation For IAM Implementation In Organization
IAM Process For Effective Access Budget Allocation For IAM Implementation In OrganizationThis slide represents the estimated and actual cost of implementing an IAM plan in an organization. The cost categories are IAM software licensing, hardware and infrastructure, implementing service, training and education, testing, and quality assurance. Present the topic in a bit more detail with this IAM Process For Effective Access Budget Allocation For IAM Implementation In Organization. Use it as a tool for discussion and navigation on Hardware And Infrastructure, Training And Education, Implementation Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
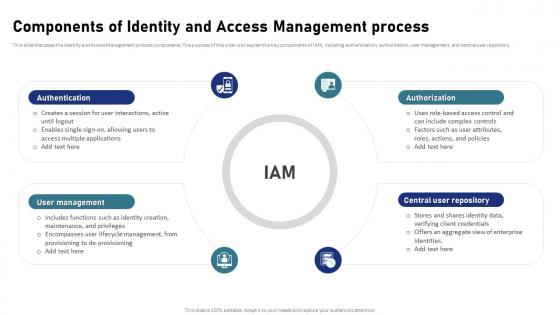 IAM Process For Effective Access Components Of Identity And Access Management Process
IAM Process For Effective Access Components Of Identity And Access Management ProcessThis slide discusses the Identity and Access Management process components. The purpose of this slide is to explain the key components of IAM, including authentication, authorization, user management, and central user repository. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Components Of Identity And Access Management Process. This template helps you present information on four stages. You can also present information on Authentication, User Management, Central User Repository, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Covid 19 Impact On Identity And Access Management
IAM Process For Effective Access Covid 19 Impact On Identity And Access ManagementThis slide highlights the various impacts of the COVID-19 pandemic on Identity and Access Management. The purpose of this slide is to discuss the effects of the pandemic that disrupted global cyber security, causing a surge in cyber attacks. Introducing IAM Process For Effective Access Covid 19 Impact On Identity And Access Management to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Global Cyber Security, Flexibility And Cost Effectiveness, Organizations Susceptible, Cloud Environments, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Essential Principles Of Identity And Access Management
IAM Process For Effective Access Essential Principles Of Identity And Access ManagementThis slide discusses the principles of a successful Identity and Access Management program. The purpose of this slide is to explain the various principles of IAM these include IAM impacts everyone and everything, simplifies the user experiences, enables research and collaboration, and so on. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Essential Principles Of Identity And Access Management. Dispense information and present a thorough explanation of Simplifies The User Experience, Facilitates Technology Innovation, Protects University Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Framework Of Identity And Access Management Process
IAM Process For Effective Access Framework Of Identity And Access Management ProcessThis slide discusses the Identity and Access Management process framework. The purpose of this slide is to explain the IAM framework that gives an overview of identity classification, identity management, and access management. Present the topic in a bit more detail with this IAM Process For Effective Access Framework Of Identity And Access Management Process. Use it as a tool for discussion and navigation on Audit And Reporting, Trust And Federation, Access Management Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Google Cloud Identity And Access Management
IAM Process For Effective Access Google Cloud Identity And Access ManagementThis slide represents the Identity and Access Management leader Google Cloud IAM. The purpose of this slide is to discuss the Google Cloud, which is based on user groups and Google accounts and is particularly useful for implementing changes. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Google Cloud Identity And Access Management. This template helps you present information on six stages. You can also present information on Google Cloud Identity, Access Management, Google Accounts Widely Prevalent using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access IAM Multi Factor Authentication Tool And System
IAM Process For Effective Access IAM Multi Factor Authentication Tool And SystemThis slide discusses the multi-factor authentication tool and system for the Identity and Access Management process. The purpose of this slide is to explain the multi-factor authentication that uses multiple authentication factors for user access. Introducing IAM Process For Effective Access IAM Multi Factor Authentication Tool And System to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Factor Authentication Tool, Access Management Process, Risk Of Credential Based Attacks, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access IAM Role Based Access Control Tool And System
IAM Process For Effective Access IAM Role Based Access Control Tool And SystemThis slide discusses the role based access control tool and system for the Identity and Access Management process. The purpose of this slide is to explain the role based access control tool that assigns predefined access privileges to specific roles. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access IAM Role Based Access Control Tool And System. Dispense information and present a thorough explanation of Network Security, Numerous Employees And Roles, Assigns Predefined Access Privileges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access IAM Single Sign On Tool And System
IAM Process For Effective Access IAM Single Sign On Tool And SystemThis slide discusses the single sign-on tool and system for the Identity and Access Management process. The purpose of this slide is to explain the single sign-on tool that allows users to use one set of credentials for accessing multiple applications. Present the topic in a bit more detail with this IAM Process For Effective Access IAM Single Sign On Tool And System. Use it as a tool for discussion and navigation on Access Management Process, Accessing Multiple Applications, User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access IAM Solutions To Streamline Tasks And Workflow
IAM Process For Effective Access IAM Solutions To Streamline Tasks And WorkflowThis slide discusses the Identity and Access Management solutions to streamline tasks and workflow. The purpose of this slide is to explain the various solutions to simplify workflow these include centralized directories, automated workflow, access control, and so on. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access IAM Solutions To Streamline Tasks And Workflow. This template helps you present information on six stages. You can also present information on Centralized Directories, Automated Workflows, Authentication Options using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Identity And Access Management Training Schedule For Staff
IAM Process For Effective Access Identity And Access Management Training Schedule For StaffThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Identity And Access Management Training Schedule For Staff. Dispense information and present a thorough explanation of Identity And Access Management, Time Slots For Training, Enforcing Compliance Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Impact Of Identity And Access Management On Business
IAM Process For Effective Access Impact Of Identity And Access Management On BusinessThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Present the topic in a bit more detail with this IAM Process For Effective Access Impact Of Identity And Access Management On Business. Use it as a tool for discussion and navigation on Regulatory Compliance, Improved Productivity, Enhanced Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Management For Table Of Contents
IAM Process For Effective Access Management For Table Of ContentsIntroducing IAM Process For Effective Access Management For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Credentials Management, Auditing Service, Authorization Service, Federation Service, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Overview Of Identity Life Cycle Management
IAM Process For Effective Access Overview Of Identity Life Cycle ManagementThis slide highlights the identity life cycle management of IAM. The purpose of this slide is to showcase the life cycle that includes identity provisioning, credential and password management, self-registration, self-service, etc. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Overview Of Identity Life Cycle Management. This template helps you present information on nine stages. You can also present information on Delegated Administration, Enforcement Of Policies, User And Group Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Primary Identity And Access Management Software
IAM Process For Effective Access Primary Identity And Access Management SoftwareThis slide discusses the primary software used in the Identity and Access Management process. The purpose of this slide is to explain the software of IAM, which are Okta, JumpCloud, Rippling, Auth0, and OneLogin. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Primary Identity And Access Management Software. Dispense information and present a thorough explanation of Customizable Regional Settings, Access Management Software, Flawless Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Roadmap For Identity And Access Management Implementation
IAM Process For Effective Access Roadmap For Identity And Access Management ImplementationThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Introducing IAM Process For Effective Access Roadmap For Identity And Access Management Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Testing And Security Assurance, Monitoring And Continuous Improvement, Access Management Implementation, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Single Sign On Service Of Identity And Access Management
IAM Process For Effective Access Single Sign On Service Of Identity And Access ManagementThis slide showcases the Identity and Access Management single sign-on service. The purpose of this slide is to explain the SOS services that enable users to access various systems with a single set of credentials and IAM challenges targeted by SOS. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Single Sign On Service Of Identity And Access Management. This template helps you present information on four stages. You can also present information on Testing And Security Assurance, Monitoring And Continuous Improvement, Access Management Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Standards And Protocols For Identity And Access Management
IAM Process For Effective Access Standards And Protocols For Identity And Access ManagementThis slide discusses the standards and protocols followed in the IAM process. The purpose of this slide is to highlight the various standards these are oAuth 2.0, next-generation access control, security assertion markup language etc. Present the topic in a bit more detail with this IAM Process For Effective Access Standards And Protocols For Identity And Access Management. Use it as a tool for discussion and navigation on Next Generation Access Control, Security Assertion Markup Language, Access Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Timeline To Implement Identity And Access Management Plan
IAM Process For Effective Access Timeline To Implement Identity And Access Management PlanThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing IAM Process For Effective Access Timeline To Implement Identity And Access Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Timeline To Implement Identity, Access Management Plan, Regular System Maintenance, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For IAM Process For Effective Access Management
Icons Slide For IAM Process For Effective Access ManagementIntroducing our well researched set of slides titled Icons Slide For IAM Process For Effective Access Management. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identity And Access Management Advance Self Service IAM Process For Effective Access
Identity And Access Management Advance Self Service IAM Process For Effective AccessThis slide discusses the advance self-service of Identity and Access Management. The purpose of this slide is to explain the advance self-services that store and manage user identities and resource information and the IAM challenges targeted by the directory. Present the topic in a bit more detail with this Identity And Access Management Advance Self Service IAM Process For Effective Access. Use it as a tool for discussion and navigation on Demand For Personalized Content, Low User Productivity, Many Password Calls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management And Compliance Regulation IAM Process For Effective Access
Identity And Access Management And Compliance Regulation IAM Process For Effective AccessThis slide showcases the Identity and Access Management and compliance regulations. The purpose of this slide is to discuss the compliances adopting the IAM system, enhancing data security and privacy, simplifying compliance, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management And Compliance Regulation IAM Process For Effective Access. Dispense information and present a thorough explanation of Adoption Of IAM Systems, Automation For Reporting Compliance, Regulatory Documentation Requirements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Auditing Service IAM Process For Effective Access
Identity And Access Management Auditing Service IAM Process For Effective AccessThis slide showcases the auditing service of Identity and Access Management. The purpose of this slide is to explain the auditing services that ensure alignment of workflow, identity data, access controls, and IAM challenges targeted by auditing. Present the topic in a bit more detail with this Identity And Access Management Auditing Service IAM Process For Effective Access. Use it as a tool for discussion and navigation on Need For Segregation Of Duties, Increasing Authentication Complexity, Inconsistent Security Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Challenges And Solutions IAM Process For Effective Access
Identity And Access Management Challenges And Solutions IAM Process For Effective AccessThis slide highlights the challenges associated with IAM. The purpose of this slide is to discuss the solutions provided to different challenges related to IAM. These include distributed workforce, distributed application, productive provisioning, BYOD, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Challenges And Solutions IAM Process For Effective Access. Dispense information and present a thorough explanation of Productive Provisioning, Distributed Applications, Password Problems, Access Management Challenges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Credentials Management Service IAM Process For Effective Access
Identity And Access Management Credentials Management Service IAM Process For Effective AccessThis slide discusses the credentials management service of Identity and Access Management. The purpose of this slide is to explain the CM services that oversee the life cycle of various credential types and IAM challenges targeted by CM. Present the topic in a bit more detail with this Identity And Access Management Credentials Management Service IAM Process For Effective Access. Use it as a tool for discussion and navigation on Smart Cards, Certificates, Biometric Data, Proximity Cards. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management De Provisioning Service IAM Process For Effective Access
Identity And Access Management De Provisioning Service IAM Process For Effective AccessThis slide discusses the de-provisioning service of Identity and Access Management. The purpose of this slide is to explain the de-provisioning services that utilizes the same tools and service as provisioning and IAM challenges targeted by de-provisioning. Introducing Identity And Access Management De Provisioning Service IAM Process For Effective Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Redundant Tasks, Privacy Control Issues, Need For Auditing, using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Directory Technologies IAM Process For Effective Access
Identity And Access Management Directory Technologies IAM Process For Effective AccessThis slide discusses the directory technologies service of Identity and Access Management. The purpose of this slide is to explain the directory services that store and manage user identities and resource information and the IAM challenges targeted by the directory. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Directory Technologies IAM Process For Effective Access. This template helps you present information on five stages. You can also present information on Identity And Access Management, Directory Technologies, Resource Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Ease Of Use Issue IAM Process For Effective Access
Identity And Access Management Ease Of Use Issue IAM Process For Effective AccessThis slide discusses the ease of use issue of the Identity and Access Management process. The purpose of this slide is to explain the ease of use challenges of IAM these include the increasing authentication complexity, demand for self-service, and so on. Deliver an outstanding presentation on the topic using this Identity And Access Management Ease Of Use Issue IAM Process For Effective Access. Dispense information and present a thorough explanation of Authentication Complexity, Demand For Self Service, Financial Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




