Powerpoint Templates and Google slides for Access
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working. Use it as a tool for discussion and navigation on Deployment Overview And Working, Web Servers They Visit, Forward Proxy Method Is A Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0
Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0This slide outlines the overview of Cloud Access Security Broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Future Of Cloud Access Security Broker CASB 2 0. This template helps you present information on seven stages. You can also present information on Data Loss Prevention, Advanced Malware Protection, Managed Security Service, Endpoint Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the Cloud Access Security Broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model. Dispense information and present a thorough explanation of Cloud Security Posture Management, Data Privacy And Protection, Zero Trust Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
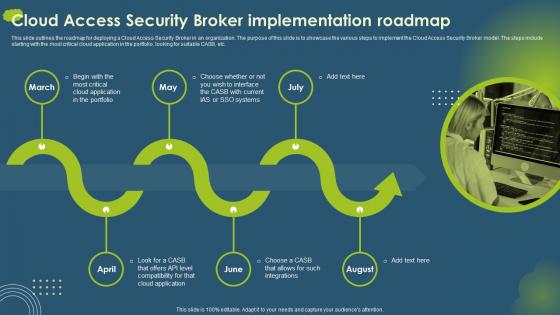 Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait
Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery PortraitThis slide outlines the roadmap for deploying a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to implement the Cloud Access Security Broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker CASB V2 Implementation Roadmap Ppt Gallery Portrait to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Critical Cloud Application, Compatibility, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template Deck
Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template DeckThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the overview, benefits, and pillars of CASB, such as compliance, visibility, threat protection, and data security. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Introduction Ppt Infographic Template Deck. Use it as a tool for discussion and navigation on Risk Visibility, Threat Prevention, Granular Cloud Usage Control, Data Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker Platforms
Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker PlatformsThis slide outlines the Leading Cloud Access Security Broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Leading Cloud Access Security Broker Platforms. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Platforms, Amazon Web Services, Cloud Platforms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout Ideas
Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout IdeasIntroducing Cloud Access Security Broker CASB V2 Life Cycle Protection Ppt Gallery Layout Ideas to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Continuous Visibility And Assessment Systems, System Activity Payload Network, Contain Or Mitigate Risk, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models
Cloud Access Security Broker CASB V2 Overview Of CASB Deployment ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Unmanaged Gadgets, Inline Deployment, Scalable And Strong Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture
Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker ArchitectureThis slide gives an overview of Cloud Access Security Broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Overview Of Cloud Access Security Broker Architecture. Dispense information and present a thorough explanation of Visibility, Compliance, Threat Protection, Enterprise Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background Images
Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background ImagesThis slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Introducing Cloud Access Security Broker CASB V2 Pillar Compliance Ppt Icon Background Images to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compliance Pillar, Cloud Access Security Broker, Financial Services, Compliance Risk Domains, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds
Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon BackgroundsThis slide talks about the data security pillar of the Cloud Access Security Broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds. This template helps you present information on four stages. You can also present information on Document Fingerprinting, Data Security Pillar, Cloud Access Security Broker Pillar using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background Designs
Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background DesignsThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Cloud Access Security Broker CASB V2 Pillar Overview Ppt Icon Background Designs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Threat Protection, Data Security, Compliance, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction
Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon IntroductionThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Threat Protection Ppt Icon Introduction. This template helps you present information on four stages. You can also present information on Threat Protection Pillar, Cloud Access Security Broker, Machine Learning Algorithms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background Image
Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background ImageThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Pillar Visibility Ppt Icon Background Image. Dispense information and present a thorough explanation of Cloud Access Security Broker Pillar, Visibility, Cloud Discovery Analysis, Device And Location Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors
Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker VendorsThis slide outlines the popular Cloud Access Security Broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Popular Cloud Access Security Broker Vendors. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Mid To Large Enterprises, Robust Integration, Cisco Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment
Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server DeploymentThis slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Introducing Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Regular Reverse Proxies, Load Balancers, Proxy Server Deployment, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment
Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB DeploymentThis slide outlines the advantages and disadvantages of the API scanning Cloud Access Security Broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment. This template helps you present information on one stages. You can also present information on Cloud Access Security, Broker Deployment Model, Scanning Deployment Model, Security Policy Modifications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Proxy Based Implementation, Proxy Deployment, Proxy And Reverse Proxy, Operation Of Several using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB
Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASBThis slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB. Use it as a tool for discussion and navigation on Performance And Security, Proxy Based Deployment, Standalone Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model
Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security ModelThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Threat Detection, Continuous Compliance, Data Encryption, Strong Authentication, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model. This template helps you present information on five stages. You can also present information on Reverse Proxy, Cloud Access Security Model Broker, Web Server Anonymity, Websites With High Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward Proxy
Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward ProxyThis slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Reverse Proxy Vs Forward Proxy. Dispense information and present a thorough explanation of Reverse Proxy, Forward Proxy, Performance And Implementation, Load Balancing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview
Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle OverviewThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Network Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security BrokerThis slide outlines the steps to implement a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security Broker. This template helps you present information on one stages. You can also present information on Speedier Installation, Comprehensive Coverage, Cloud Access Security Broker using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a Cloud Access Security Broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Cloud Access Security Broker CASB V2 Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Identifying Risks, Cloud Applications, Malware Detection And Removal, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security BrokerThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security Broker. Use it as a tool for discussion and navigation on Training Program For Cloud, Access Security Broker, System Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment
Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server DeploymentThis slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment. Dispense information and present a thorough explanation of Proxy Server Deployment, Central Proxy Server, Proxy Server Implementation, Data Center Proxies Work using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security BrokerPresent the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security Broker. Use it as a tool for discussion and navigation on Threats And Exploited Accounts, Unmanaged Devices, Label And Protect Sensitive, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Why CASB Is Important For Businesses
Cloud Access Security Broker CASB V2 Why CASB Is Important For BusinessesThis slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the Cloud Access Security Broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. Introducing Cloud Access Security Broker CASB V2 Why CASB Is Important For Businesses to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Cloud Adoption, Better Security, Compliance, Centralized Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example Introduction
Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example IntroductionIntroducing our well researched set of slides titled Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example Introduction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V
Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS VThis slide showcases process to get access key for OpenAIs ChatGPT 3 and ChatGPT 4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Increase audience engagement and knowledge by dispensing information using Integrating Openai API Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V. This template helps you present information on four stages. You can also present information on Client Library, Installation, Switching, Requirements, Natural Language using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Metaverse Can Be Accessed By Users Metaverse Everything AI SS V
How Metaverse Can Be Accessed By Users Metaverse Everything AI SS VThis slide provides information regarding different ways through metaverse can be executed by connecting with VR interface such as headset, game console, to gain immersive metaverse experience. Present the topic in a bit more detail with this How Metaverse Can Be Accessed By Users Metaverse Everything AI SS V Use it as a tool for discussion and navigation on Several Metaverse Experiences, Metaverse Development, Unintegrated Devices This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Metaverse Through Technologies 3d Modeling Metaverse Everything AI SS V
Accessing Metaverse Through Technologies 3d Modeling Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as 3D modeling. It is process of creating 3D representation of object or surface in virtual space. Deliver an outstanding presentation on the topic using this Accessing Metaverse Through Technologies 3d Modeling Metaverse Everything AI SS V. Dispense information and present a thorough explanation of Modeling In Metaverse, Technology, Process Of Generating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Accessing Metaverse Through Technologies AR MR And VR Metaverse Everything AI SS V
Accessing Metaverse Through Technologies AR MR And VR Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as AR, MR and VR. It depicts the metaverse competencies, pros, cons, market, use case, and devices utilized by AR, VR and MR technologies in metaverse. Present the topic in a bit more detail with this Accessing Metaverse Through Technologies AR MR And VR Metaverse Everything AI SS V. Use it as a tool for discussion and navigation on Assisted Reality, Virtual Reality, Augmented Mixed Reality This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Metaverse Through Technologies Artificial Intelligence Ai Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Artificial Intelligence Ai Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Deliver an outstanding presentation on the topic using this Accessing Metaverse Through Technologies Artificial Intelligence Ai Metaverse Everything AI SS V. Dispense information and present a thorough explanation of Content Creation, Security, Customization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Accessing Metaverse Through Technologies Augmented Reality AR Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Augmented Reality AR Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as augmented reality. It helps in offering real world experience to users while interacting with digital elements. Introducing Accessing Metaverse Through Technologies Augmented Reality AR Metaverse Everything AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Deploy Virtual Objects, Physical Engagement, Digital Content using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies Blockchain Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Blockchain Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as blockchain. It enables cryptocurrencies bitcoin, NFTs to buy or sell digital assets in metaverse space. Present the topic in a bit more detail with this Accessing Metaverse Through Technologies Blockchain Metaverse Everything AI SS V. Use it as a tool for discussion and navigation on Blockchain In Metaverse, Cryptocurrency Transactions, Blockchain This template is free to edit as deemed fit for your organization. Therefore download it now.
-
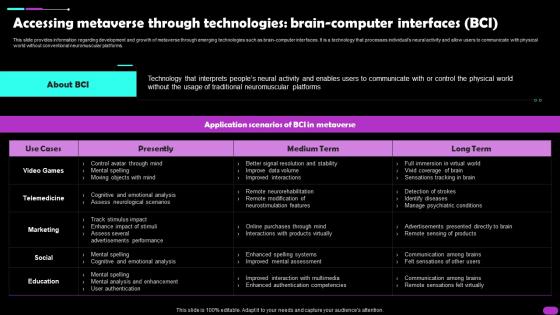 Accessing Metaverse Through Technologies Brain Computer Interfaces BCI Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Brain Computer Interfaces BCI Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as brain computer interfaces. It is a technology that processes individuals neural activity and allow users to communicate with physical world without conventional neuromuscular platforms. Deliver an outstanding presentation on the topic using this Accessing Metaverse Through Technologies Brain Computer Interfaces BCI Metaverse Everything AI SS V. Dispense information and present a thorough explanation of Presently, Technology, Traditional Neuromuscular Platforms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Accessing Metaverse Through Technologies Edge Computing Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Edge Computing Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as edge computing. It enables processing of data on-site for faster information processing to reduce network latency. Present the topic in a bit more detail with this Accessing Metaverse Through Technologies Edge Computing Metaverse Everything AI SS V. Use it as a tool for discussion and navigation on Computing In Metaverse, About Edge Computing, Information Processing This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Metaverse Through Technologies Extended Reality XR Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Extended Reality XR Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as extended reality. It is combination of AR, VR and MR for users to interact with each other in metaverse space. Introducing Accessing Metaverse Through Technologies Extended Reality XR Metaverse Everything AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Development, Manufacturing And Procedure using this template. Grab it now to reap its full benefits.
-
 Accessing Metaverse Through Technologies Internet Of Things IOT Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Internet Of Things IOT Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as internet of things IoT. It is a robust network of interconnected physical devices to leverage link among real world and virtual space. Present the topic in a bit more detail with this Accessing Metaverse Through Technologies Internet Of Things IOT Metaverse Everything AI SS V. Use it as a tool for discussion and navigation on Digital Network, Technological Space, Smart Devices This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Metaverse Through Technologies Spatial Computing Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Spatial Computing Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as spatial computing. It is a technology that enable computers to unlock interaction with physical world immensely with augmented and virtual reality. Deliver an outstanding presentation on the topic using this Accessing Metaverse Through Technologies Spatial Computing Metaverse Everything AI SS V. Dispense information and present a thorough explanation of Spatial Computing In Metaverse, Technology, Spatial Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Accessing Metaverse Through Technologies Virtual Reality AR Metaverse Everything AI SS V
Accessing Metaverse Through Technologies Virtual Reality AR Metaverse Everything AI SS VThis slide provides information regarding development and growth of metaverse through emerging technologies such as virtual reality. It is simulated 3D environment that enable users interaction with virtual space. Introducing Accessing Metaverse Through Technologies Virtual Reality AR Metaverse Everything AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Virtual Environment, Representations Of Themselves, Social Events using this template. Grab it now to reap its full benefits.
-
 Various Services Accessible Via Mobile Banking E Wallets As Emerging Payment Method Fin SS V
Various Services Accessible Via Mobile Banking E Wallets As Emerging Payment Method Fin SS VThis slide shows various services which can be availed by customers through mobile banking. It includes services such as account management, funds transfer, bills payment, mobile check deposits, ATM and branch locators, cards management, etc. Introducing Various Services Accessible Via Mobile Banking E Wallets As Emerging Payment Method Fin SS V to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Investment Services, Loan Services, Cards Management, using this template. Grab it now to reap its full benefits.
-
 Hybrid Wan Sd Wan And Secure Access Service Edge Sase
Hybrid Wan Sd Wan And Secure Access Service Edge SaseThis slide represents the relationship between secure access service edge and software defined wide area network. It also includes the benefits of SASE and its security features, such as software defined WAN, firewall as a service, zero trust network access, cloud access security broker, secure web gateway, and unified management. Introducing Hybrid Wan Sd Wan And Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Features, Improves Agility, using this template. Grab it now to reap its full benefits.
-
 Hybrid Wan Secure Access Service Edge Vs Sd Wan
Hybrid Wan Secure Access Service Edge Vs Sd WanThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this Hybrid Wan Secure Access Service Edge Vs Sd Wan. Use it as a tool for discussion and navigation on Security, Remote Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V
Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS VThis slide showcases process to get access key for OpenAIs ChatGPT-3 and ChatGPT-4 APIs which companies can use as a guide to get easy login and signup procedure. It provides details about client library, installation, switching, etc. Introducing Openai Api Everything You Need Procedure To Access ChatGPT 4 And ChatGPT 3 APIs ChatGPT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Client Library, Installation, Switching, Natural Language Processing, using this template. Grab it now to reap its full benefits.
-
 Access Capital Entrepreneurs In Powerpoint And Google Slides Cpb
Access Capital Entrepreneurs In Powerpoint And Google Slides CpbPresenting our Access Capital Entrepreneurs In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Access Capital Entrepreneurs This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Multiple Trendy Fashion Accessories Offered Elevating Sales Revenue With New Promotional Strategy SS V
Multiple Trendy Fashion Accessories Offered Elevating Sales Revenue With New Promotional Strategy SS VIntroducing Multiple Trendy Fashion Accessories Offered Elevating Sales Revenue With New Promotional Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Gym Shoes, Pair Of Gloves, Belt Pouch, using this template. Grab it now to reap its full benefits.
-
 Offering Exclusive Pre Launch Access Elevating Sales Revenue With New Promotional Strategy SS V
Offering Exclusive Pre Launch Access Elevating Sales Revenue With New Promotional Strategy SS VThis slide provides glimpse about exclusive pre-launch campaign through email marketing for boosting customer engagement. It includes overview, implementation guidelines, impact, etc. Increase audience engagement and knowledge by dispensing information using Offering Exclusive Pre Launch Access Elevating Sales Revenue With New Promotional Strategy SS V. This template helps you present information on two stages. You can also present information on Overview, Implementation Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 First Access Credit Card Review In Powerpoint And Google Slides Cpb
First Access Credit Card Review In Powerpoint And Google Slides CpbPresenting First Access Credit Card Review In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like First Access Credit Card Review. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Access Protocol In Powerpoint And Google Slides Cpb
Access Protocol In Powerpoint And Google Slides CpbPresenting our Access Protocol In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Protocol This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 First Access Credit Card Legit In Powerpoint And Google Slides Cpb
First Access Credit Card Legit In Powerpoint And Google Slides CpbPresenting First Access Credit Card Legit In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like First Access Credit Card Legit. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Optimize IT Audit Application Tools For Access Controls
Optimize IT Audit Application Tools For Access ControlsThis slide illustrates best IT audit softwares for streamlining the auditing process by observing monitoring progress. It include tools such as solarwinds, galvanize, eramba and EHS Insight. Introducing our Optimize IT Audit Application Tools For Access Controls set of slides. The topics discussed in these slides are Adaptable Audit Management, Solution IT Infrastructure, Presents Industry Specific. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Secure Access Service Edge SASE Cloud Security Model
Benefits Of Secure Access Service Edge SASE Cloud Security ModelThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Present the topic in a bit more detail with this Benefits Of Secure Access Service Edge SASE Cloud Security Model. Use it as a tool for discussion and navigation on Secure, Benefits, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Zero Trust Network Access ZTNA Cloud Security Model
Benefits Of Zero Trust Network Access ZTNA Cloud Security ModelThis slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Deliver an outstanding presentation on the topic using this Benefits Of Zero Trust Network Access ZTNA Cloud Security Model. Dispense information and present a thorough explanation of Benefits, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget To Implement Secure Access Service Edge Cloud Security Model
Budget To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Budget To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Implement, Network, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.





