Powerpoint Templates and Google slides for Access Manager
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Securing Systems With Identity And Access Management Powerpoint Presentation Slides
Securing Systems With Identity And Access Management Powerpoint Presentation SlidesWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Securing Systems With Identity And Access Management Powerpoint Presentation Slides deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 IAM Processes For Effective Access Management Powerpoint Presentation Slides
IAM Processes For Effective Access Management Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this IAM Processes For Effective Access Management Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with seventy one slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Identity And Access Management Proposal Powerpoint Presentation Slides
Identity And Access Management Proposal Powerpoint Presentation SlidesDitch the Dull templates and opt for our engaging Identity And Access Management Proposal Powerpoint Presentation Slides deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 ITIL Access Management Powerpoint Ppt Template Bundles
ITIL Access Management Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this ITIL Access Management Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The eighteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This ITIL Access Management Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Overview Of Identity Access Management Policy Training Ppt
Overview Of Identity Access Management Policy Training PptPresenting Overview of Identity Access Management Policy. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Implementing Identity And Access Management For Operational Security OPSEC Training Ppt
Implementing Identity And Access Management For Operational Security OPSEC Training PptPresenting Implementing Identity and Access Management for Operational Security OPSEC. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 User Access Management Powerpoint PPT Template Bundles
User Access Management Powerpoint PPT Template BundlesIntroduce your topic and host expert discussion sessions with this User Access Management Powerpoint PPT Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the thirteen slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Identity And Access Management Powerpoint PPT Template Bundles
Identity And Access Management Powerpoint PPT Template BundlesIntroduce your topic and host expert discussion sessions with this Identity And Access Management Powerpoint PPT Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Information technology infrastructure library itil access management powerpoint presentation slides
Information technology infrastructure library itil access management powerpoint presentation slidesIt covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Information Technology Infrastructure Library ITIL Access Management Powerpoint Presentation Slides with well suited graphics and subject driven content. This deck consists of total of sixteen slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below.
-
 7 parts circle diagram data analysts product management web access
7 parts circle diagram data analysts product management web accessDeliver a lucid presentation by utilizing this 7 Parts Circle Diagram Data Analysts Product Management Web Access. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as 7 Parts Circle Diagram, Data Analysts, Product Management, Web Access. All the thirteen slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Access Management Ppt Summary Background Designs Logging And Tracking Access
Access Management Ppt Summary Background Designs Logging And Tracking AccessWe bring to you to the point topic specific slides with apt research and understanding. Putting forth our PPT deck comprises of twelve slides. Our tailor made Access Management Ppt Summary Background Designs Logging And Tracking Access editable presentation deck assists planners to segment and expound the topic with brevity. The advantageous slides on Access Management Ppt Summary Background Designs Logging And Tracking Access is braced with multiple charts and graphs, overviews, analysis templates agenda slides etc. to help boost important aspects of your presentation. Highlight all sorts of related usable templates for important considerations. Our deck finds applicability amongst all kinds of professionals, managers, individuals, temporary permanent teams involved in any company organization from any field.
-
 Operational Flow Incident Management Organization Technical Access Architecture Business Intelligence
Operational Flow Incident Management Organization Technical Access Architecture Business IntelligenceIt has PPT slides covering wide range of topics showcasing all the core areas of your business needs. This complete deck focuses on Operational Flow Incident Management Organization Technical Access Architecture Business Intelligence and consists of professionally designed templates with suitable graphics and appropriate content. This deck has total of twelve slides. Our designers have created customizable templates for your convenience. You can make the required changes in the templates like colour, text and font size. Other than this, content can be added or deleted from the slide as per the requirement. Get access to this professionally designed complete deck PPT presentation by clicking the download button below.
-
 IAM Process For Effective Access Cost Of Identity And Access Management Over Time
IAM Process For Effective Access Cost Of Identity And Access Management Over TimeThis slide showcases the cost required for Identity and Access Management over time. The purpose of this slide is to depict the cost of IAM through a graph showing the relationship between deploying identity management and maintaining existing management tools. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Cost Of Identity And Access Management Over Time. Dispense information and present a thorough explanation of Cost Of Identity And Access, Management Over Time, Existing Management Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Insights Reporting Dashboard IAM Process For Effective Access
Identity And Access Management Insights Reporting Dashboard IAM Process For Effective AccessThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard IAM Process For Effective Access. Dispense information and present a thorough explanation of Identity And Access Management, Insights Reporting Dashboard, System Checks, Failed Task Results using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective Access
Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective AccessThis slide represents the Identity and Access Management technology adoption lifecycle. The purpose of this slide is to discuss the mapping of Identity and Access Management technologies to the technology adoption lifecycle. Present the topic in a bit more detail with this Identity And Access Management Technology Adoption Lifecycle IAM Process For Effective Access. Use it as a tool for discussion and navigation on Identity And Access Management, Technology Adoption Lifecycle, Password Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Accessing Corporate Crisis Management Dashboard
Accessing Corporate Crisis Management DashboardThis slide illustrates KPI dashboard of corporate crisis management performance including business process crises, crisis rating by user and crisis. Introducing our Accessing Corporate Crisis Management Dashboard set of slides. The topics discussed in these slides are Business Process Crises, Not Executed, Partially Executed. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Client Testimonials For IAM Implementation Proposal Identity And Access Management
Client Testimonials For IAM Implementation Proposal Identity And Access ManagementThis slide showcases a collection of customer testimonials received from multiple clients who have graciously shared their feedback with the organization Increase audience engagement and knowledge by dispensing information using Client Testimonials For IAM Implementation Proposal Identity And Access Management This template helps you present information on three stages. You can also present information on Centralized Management, Client Testimonial, Implementation Proposal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Our Team For IAM Implementation Proposal Identity And Access Management
Our Team For IAM Implementation Proposal Identity And Access ManagementThis slide represents an overview of the team structure for the IAM implementation proposal including the names and designations of each member. Introducing Our Team For IAM Implementation Proposal Identity And Access Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Our Team using this template. Grab it now to reap its full benefits.
-
 Global Statistics Highlighting Access To Diversity Management Programs
Global Statistics Highlighting Access To Diversity Management ProgramsThe purpose of this graph is to visually represent the percentage of employees with access to diversity management programs across different countries that enable HR professionals to analyze and compare the effectiveness of diversity initiatives. Introducing our Global Statistics Highlighting Access To Diversity Management Programs set of slides. The topics discussed in these slides are Strong Foundations, Management Programs, Employee Exploitation This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Budget For Identity And Access Management Training Securing Systems With Identity
Budget For Identity And Access Management Training Securing Systems With IdentityThis slide showcases the breakdown cost for the IAM installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training Securing Systems With Identity Use it as a tool for discussion and navigation on Components, Training Cost Distribution This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity
Identity And Access Management Insights Reporting Dashboard Securing Systems With IdentityThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity Dispense information and present a thorough explanation of Failed Task Results, Syslog Errors, Certifications Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Us Identity And Access Management Market Size Securing Systems With Identity
Us Identity And Access Management Market Size Securing Systems With IdentityThis slide depicts the US IAM market size in global market. The purpose of this slide is to highlight the US market size of the IAM process in terms of revenue generation and compound annual growth rate. Deliver an outstanding presentation on the topic using this Us Identity And Access Management Market Size Securing Systems With Identity Dispense information and present a thorough explanation of Provisioning Access, Compromising Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget For Identity And Access Management Training IAM Implementation Plan
Budget For Identity And Access Management Training IAM Implementation PlanThis slide showcases the breakdown cost for the IAM installation and management training for the customers components, including instructor cost, training, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training IAM Implementation Plan. Use it as a tool for discussion and navigation on Instructors Cost, Training Materials Cost, Add Component. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Identity And Access Management Works IAM Implementation Plan
How Identity And Access Management Works IAM Implementation PlanThe purpose of this slide is to highlight working of the IAM these include identifying, authentication, authorizing, auditing, and verifying the accounts. Increase audience engagement and knowledge by dispensing information using How Identity And Access Management Works IAM Implementation Plan. This template helps you present information on two stages. You can also present information on Authorization, Protected Resource, Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 K161 Identity And Access Management Insights Reporting Dashboard IAM Implementation Plan
K161 Identity And Access Management Insights Reporting Dashboard IAM Implementation PlanThis slide represents the reporting dashboard of the Identity and Access Management it showcase the components include syslog errors, system checks, failed task, etc. Deliver an outstanding presentation on the topic using this K161 Identity And Access Management Insights Reporting Dashboard IAM Implementation Plan. Dispense information and present a thorough explanation of Syslog Errors, Certification Trends, System Checks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Wireless Cloud Access Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Cloud Access Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts wireless cloud access, allowing users to share and access data remotely with ease. Ideal for presentations, this icon is perfect for illustrating the concept of cloud computing.
-
 Wireless Cloud Access Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Wireless Cloud Access Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon depicts a wireless cloud providing access to data and resources. It is a great visual tool to represent wireless cloud access in presentations and other documents.
-
 Network Management Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Network Management Cloud Access Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for representing wireless cloud access. It features a vibrant blue cloud with a white antenna, making it eye-catching and easy to identify. Its ideal for use in presentations, websites, and other digital projects.
-
 Network Management Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Network Management Cloud Access Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone PowerPoint Icon on Wireless Cloud Access is a simple, yet powerful vector graphic that is perfect for presentations or webpages. It is a modern, minimalistic design that conveys a strong message of connectivity and access to the cloud. It is a great choice for any project that needs a professional, yet eye-catching design.
-
 Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview
Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle OverviewThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Cloud Access Security Broker CASB V2 Shadow IT Management Lifecycle Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Network Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Smart Home Access Management The Ultimate Guide To Blockchain Integration IoT SS
Smart Home Access Management The Ultimate Guide To Blockchain Integration IoT SSThis slide provides information related to smart home access management system to ensure access data are securely recorded on blockchain network. It includes elements such as IoT smart home ecosystem, smart home blockchain, external users, admin, etc. Deliver an outstanding presentation on the topic using this Smart Home Access Management The Ultimate Guide To Blockchain Integration IoT SS. Dispense information and present a thorough explanation of Access, Management, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN And Secure Access Service Edge Sase Managed Wan Services
SD WAN And Secure Access Service Edge Sase Managed Wan ServicesThis slide represents the relationship between secure access service edge and software defined wide area network. It also includes the benefits of SASE and its security features, such as software defined WAN, firewall as a service, zero trust network access, cloud access security broker, secure web gateway, and unified management.Present the topic in a bit more detail with this SD WAN And Secure Access Service Edge Sase Managed Wan Services. Use it as a tool for discussion and navigation on Combination Technologies, Increased Efficiency, Network Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Access Service Edge Vs SD WAN Managed Wan Services
Secure Access Service Edge Vs SD WAN Managed Wan ServicesThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access.Present the topic in a bit more detail with this Secure Access Service Edge Vs SD WAN Managed Wan Services. Use it as a tool for discussion and navigation on Streamlined Administration, Limited Security Features, Business Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Lead Management Access Template In Powerpoint And Google Slides Cpb
Lead Management Access Template In Powerpoint And Google Slides CpbPresenting Lead Management Access Template In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Lead Management Access Template. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Bring Your Own Device Policy Access Authorization Modification And Identity Access Management
Bring Your Own Device Policy Access Authorization Modification And Identity Access ManagementThis slide represents the access authorization, modification, and identity access management based on PoLP, including the departments involved in creating this policy, such as HR and IT. Introducing Bring Your Own Device Policy Access Authorization Modification And Identity Access Management to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Modification, Identity Access Management, Access Authorization, Hire And Termination, using this template. Grab it now to reap its full benefits.
-
 Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency Management
Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency ManagementThis slide represents the introduction and commonly used web wallets. This slide outlines the ordinary web wallets in the market, such as bit2me, Binance, coin base, myether wallet, metamask, atomic wallet, etc. Deliver an outstanding presentation on the topic using this Crypto Wallets Types And Applications Web Wallets For Accessible Cryptocurrency Management. Dispense information and present a thorough explanation of Web Wallets, Cryptocurrency Management, Typically More Convenient, Store Cryptocurrency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process
Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management ProcessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Users Access Request, Approval Rules, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Access Control Password Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Password Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Access Control Password Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Access Control Password Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment
Reduce Attack Surface With Privilege Access Management Cyber Risk AssessmentThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Cyber Risk Assessment Dispense information and present a thorough explanation of Users Access Request, Record Sessions, Session Proxy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness
Reduce Attack Surface With Privilege Access Management Creating Cyber Security AwarenessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Time Consuming Process, Incremental Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For IAM Process For Effective Access Management
Agenda For IAM Process For Effective Access ManagementIntroducing Agenda For IAM Process For Effective Access Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Effective Access Management, Risks And Issue Associated, Examine The IAM Services, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access About IBM Identity And Access Management
IAM Process For Effective Access About IBM Identity And Access ManagementThis slide discusses the Identity and Access Management leader IBM IAM. The purpose of this slide is to examine the IBM IAM, which offers expertise in large-scale computing projects and addresses various complex enterprise challenges. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access About IBM Identity And Access Management. Dispense information and present a thorough explanation of Identity And Access Management, Complex Enterprise Challenges, Large Scale Computing Projects using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access About Identity And Access Management Controls
IAM Process For Effective Access About Identity And Access Management ControlsThis slide discusses the various controls of Identity and Access Management. The purpose of this slide is to explain the controls of IAM, which include unique IDs, devices, services, application accounts, access approval, and account management. Present the topic in a bit more detail with this IAM Process For Effective Access About Identity And Access Management Controls. Use it as a tool for discussion and navigation on Service And Application Accounts, Account Management, Applicable Data Protection Categorization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Authorization Service Of Identity And Access Management
IAM Process For Effective Access Authorization Service Of Identity And Access ManagementThis slide showcases the Identity and Access Management authorization service. The purpose of this slide is to explain the authorization services that grant user privileges, such as permission, access rights, and IAM challenges targeted by authorization. Introducing IAM Process For Effective Access Authorization Service Of Identity And Access Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Discretionary Access Control, Mandatory Access Control, Role Based Access Control, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management Implementation
IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management ImplementationThis slide showcases the comparative analysis of the before versus after IAM implementation. The purpose of this slide is to discuss the different performance aspects and how IAM has proved beneficial for these aspects. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Before Vs After Impact Of Identity And Access Management Implementation. Dispense information and present a thorough explanation of Credential Management, Identity Provisioning, Policy Enforcement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
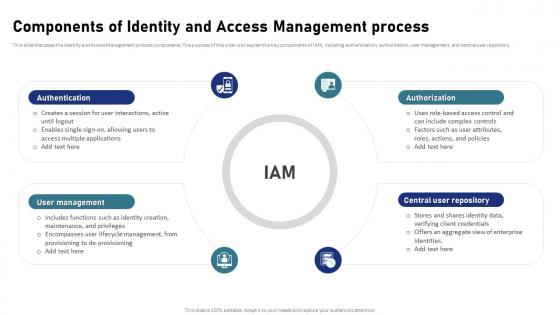 IAM Process For Effective Access Components Of Identity And Access Management Process
IAM Process For Effective Access Components Of Identity And Access Management ProcessThis slide discusses the Identity and Access Management process components. The purpose of this slide is to explain the key components of IAM, including authentication, authorization, user management, and central user repository. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Components Of Identity And Access Management Process. This template helps you present information on four stages. You can also present information on Authentication, User Management, Central User Repository, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Covid 19 Impact On Identity And Access Management
IAM Process For Effective Access Covid 19 Impact On Identity And Access ManagementThis slide highlights the various impacts of the COVID-19 pandemic on Identity and Access Management. The purpose of this slide is to discuss the effects of the pandemic that disrupted global cyber security, causing a surge in cyber attacks. Introducing IAM Process For Effective Access Covid 19 Impact On Identity And Access Management to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Global Cyber Security, Flexibility And Cost Effectiveness, Organizations Susceptible, Cloud Environments, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Essential Principles Of Identity And Access Management
IAM Process For Effective Access Essential Principles Of Identity And Access ManagementThis slide discusses the principles of a successful Identity and Access Management program. The purpose of this slide is to explain the various principles of IAM these include IAM impacts everyone and everything, simplifies the user experiences, enables research and collaboration, and so on. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Essential Principles Of Identity And Access Management. Dispense information and present a thorough explanation of Simplifies The User Experience, Facilitates Technology Innovation, Protects University Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Framework Of Identity And Access Management Process
IAM Process For Effective Access Framework Of Identity And Access Management ProcessThis slide discusses the Identity and Access Management process framework. The purpose of this slide is to explain the IAM framework that gives an overview of identity classification, identity management, and access management. Present the topic in a bit more detail with this IAM Process For Effective Access Framework Of Identity And Access Management Process. Use it as a tool for discussion and navigation on Audit And Reporting, Trust And Federation, Access Management Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Google Cloud Identity And Access Management
IAM Process For Effective Access Google Cloud Identity And Access ManagementThis slide represents the Identity and Access Management leader Google Cloud IAM. The purpose of this slide is to discuss the Google Cloud, which is based on user groups and Google accounts and is particularly useful for implementing changes. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Google Cloud Identity And Access Management. This template helps you present information on six stages. You can also present information on Google Cloud Identity, Access Management, Google Accounts Widely Prevalent using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Identity And Access Management Training Schedule For Staff
IAM Process For Effective Access Identity And Access Management Training Schedule For StaffThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Identity And Access Management Training Schedule For Staff. Dispense information and present a thorough explanation of Identity And Access Management, Time Slots For Training, Enforcing Compliance Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Impact Of Identity And Access Management On Business
IAM Process For Effective Access Impact Of Identity And Access Management On BusinessThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Present the topic in a bit more detail with this IAM Process For Effective Access Impact Of Identity And Access Management On Business. Use it as a tool for discussion and navigation on Regulatory Compliance, Improved Productivity, Enhanced Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IAM Process For Effective Access Management For Table Of Contents
IAM Process For Effective Access Management For Table Of ContentsIntroducing IAM Process For Effective Access Management For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Credentials Management, Auditing Service, Authorization Service, Federation Service, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Overview Of Identity Life Cycle Management
IAM Process For Effective Access Overview Of Identity Life Cycle ManagementThis slide highlights the identity life cycle management of IAM. The purpose of this slide is to showcase the life cycle that includes identity provisioning, credential and password management, self-registration, self-service, etc. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Overview Of Identity Life Cycle Management. This template helps you present information on nine stages. You can also present information on Delegated Administration, Enforcement Of Policies, User And Group Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Process For Effective Access Primary Identity And Access Management Software
IAM Process For Effective Access Primary Identity And Access Management SoftwareThis slide discusses the primary software used in the Identity and Access Management process. The purpose of this slide is to explain the software of IAM, which are Okta, JumpCloud, Rippling, Auth0, and OneLogin. Deliver an outstanding presentation on the topic using this IAM Process For Effective Access Primary Identity And Access Management Software. Dispense information and present a thorough explanation of Customizable Regional Settings, Access Management Software, Flawless Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Process For Effective Access Roadmap For Identity And Access Management Implementation
IAM Process For Effective Access Roadmap For Identity And Access Management ImplementationThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Introducing IAM Process For Effective Access Roadmap For Identity And Access Management Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Testing And Security Assurance, Monitoring And Continuous Improvement, Access Management Implementation, using this template. Grab it now to reap its full benefits.
-
 IAM Process For Effective Access Single Sign On Service Of Identity And Access Management
IAM Process For Effective Access Single Sign On Service Of Identity And Access ManagementThis slide showcases the Identity and Access Management single sign-on service. The purpose of this slide is to explain the SOS services that enable users to access various systems with a single set of credentials and IAM challenges targeted by SOS. Increase audience engagement and knowledge by dispensing information using IAM Process For Effective Access Single Sign On Service Of Identity And Access Management. This template helps you present information on four stages. You can also present information on Testing And Security Assurance, Monitoring And Continuous Improvement, Access Management Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




