Powerpoint Templates and Google slides for Abuse
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Infra Security Icon For Eliminating Cyber Threats
Infra Security Icon For Eliminating Cyber ThreatsIncrease audience engagement and knowledge by dispensing information using Infra Security Icon For Eliminating Cyber Threats. This template helps you present information on four stages. You can also present information on Infra Security, Icon Eliminating, Cyber Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threats Affecting Infra Security In Market
Threats Affecting Infra Security In MarketThe following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Increase audience engagement and knowledge by dispensing information using Threats Affecting Infra Security In Market. This template helps you present information on four stages. You can also present information on Phishing, Ransomware, Botnets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Threats Associated Brand Strategy Of Apple To Emerge Branding SS V
Addressing Threats Associated Brand Strategy Of Apple To Emerge Branding SS VThis slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Introducing Addressing Threats Associated Brand Strategy Of Apple To Emerge Branding SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Pandemic, Lawsuits, Rigorous Competition, using this template. Grab it now to reap its full benefits.
-
 New Project Risk Severity And Threats Analysis Software
New Project Risk Severity And Threats Analysis SoftwareThis slide covers the different factors that hinders in project implementation and development. It includes the risk slid meter to check its vulnerability and probability of its occurrences.Presenting our well structured New Project Risk Severity And Threats Analysis Software. The topics discussed in this slide are Project Objectives, Resource Conflict, System Failure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V
IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V
IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V. Use it as a tool for discussion and navigation on Risk Management Plan, Manage Cyber Threats, Natural Disaster, Website Resources Unavailability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss
Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Harassment Workplace Statistics In Powerpoint And Google Slides Cpb
Harassment Workplace Statistics In Powerpoint And Google Slides CpbPresenting Harassment Workplace Statistics In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Harassment Workplace Statistics. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Competitive Business Threats Analysis Matrix Steps For Business Growth Strategy SS
Competitive Business Threats Analysis Matrix Steps For Business Growth Strategy SSThis slide showcases strengths analysis comparison matrix of own business and competitors to identify risks. It assess businesses based on competition, economic downtowns, change in regulations, technology evolution, supply chain disruptions. Deliver an outstanding presentation on the topic using this Competitive Business Threats Analysis Matrix Steps For Business Growth Strategy SS. Dispense information and present a thorough explanation of Consumer Preferences,Supply Chain Disruptions,Changes Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Threats Associated With Apple That Negatively Apple Branding Brand Story Branding SS V
Addressing Threats Associated With Apple That Negatively Apple Branding Brand Story Branding SS VThis slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Introducing Addressing Threats Associated With Apple That Negatively Apple Branding Brand Story Branding SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Rigorous Competition, Lawsuits, Pandemic using this template. Grab it now to reap its full benefits.
-
 Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security
Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorization, Confidentiality, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security
Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an outstanding presentation on the topic using this Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Manufacturing, Government, Healthcare using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security
Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Present the topic in a bit more detail with this Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Unauthorized, Business, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security
Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Deliver an outstanding presentation on the topic using this Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Categorizing, Confidentiality, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security
Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Present the topic in a bit more detail with this Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Management, Initiatives, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security
Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Comparative, Assessment, Parameters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security
Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Contingency Solutions, Contingency Considerations, Information . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security
Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Parameters, Capability, Determine . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security
Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security
Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Present the topic in a bit more detail with this Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Malicious Insider, Negligent Or Careless Insider, Third Party Insider . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security
Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Finance, Corporate Security, Business Division, using this template. Grab it now to reap its full benefits.
-
 Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security
Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security. This template helps you present information on three stages. You can also present information on Plan And Collect, Review And Analyze, Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Cyber Threats Management To Enable Digital Assets Security
Table Of Contents Cyber Threats Management To Enable Digital Assets SecurityPresent the topic in a bit more detail with this Table Of Contents Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorizing, Associated, Determine Sequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Network Security Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting Network Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Threats Vulnerabilities
-
 Potential Future Threats Corporations Microsoft Strategy For Continuous Business Growth Strategy Ss
Potential Future Threats Corporations Microsoft Strategy For Continuous Business Growth Strategy SsThis slide shows four major threats to microsoft in coming years which can effect Microsoft adversely in terms of revenues as well as brand image. It includes competition, changing customer needs, open sources projects and potential lawsuits. Introducing Potential Future Threats Corporations Microsoft Strategy For Continuous Business Growth Strategy Ss to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Changing Customer Needs, Open Source Project , using this template. Grab it now to reap its full benefits.
-
 Threat Of Substitute Products Or Microsoft Strategy For Continuous Business Growth Strategy Ss
Threat Of Substitute Products Or Microsoft Strategy For Continuous Business Growth Strategy SsThis slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Deliver an outstanding presentation on the topic using this Threat Of Substitute Products Or Microsoft Strategy For Continuous Business Growth Strategy Ss. Dispense information and present a thorough explanation of Products, Services, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threats Of New Entrants Against Microsoft Strategy For Continuous Business Growth Strategy Ss
Threats Of New Entrants Against Microsoft Strategy For Continuous Business Growth Strategy SsThis slide shows two key factors related to threat of new entry in the existing market where microsoft is major player. These factors are high cost of brand development and moderate cost of doing business. Present the topic in a bit more detail with this Threats Of New Entrants Against Microsoft Strategy For Continuous Business Growth Strategy Ss. Use it as a tool for discussion and navigation on Business, Brand Development, Microsoft. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 24 7 Customer Service For Communication Threat Avoidance Icon
24 7 Customer Service For Communication Threat Avoidance IconPresenting our set of slides with 24 7 Customer Service For Communication Threat Avoidance Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on 24 7 Customer Service, Communication Threat, Avoidance Icon.
-
 Business Employee Threat Communication Icon
Business Employee Threat Communication IconIntroducing our premium set of slides with Business Employee Threat Communication Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Business Employee, Threat Communication Icon. So download instantly and tailor it with your information.
-
 Communication Plan For Effective Threat Management
Communication Plan For Effective Threat ManagementThe slide exhibits risk communication plan to provide meaningful and relevant information to reduce the impact of threats that arise in business. It includes communication channel, content, duration etc to convey risk status. Introducing our Communication Plan For Effective Threat Management set of slides. The topics discussed in these slides are Management, Communication, Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Communication Plan To Mitigate Multiple Threat In It Sector
Communication Plan To Mitigate Multiple Threat In It SectorFollowing slide illustrates communication plan to control various risk to achieve business objectives without any disruption and chaos. The plan includes types of risk, owner, channel, mitigation measures and risk level to combat business related risks. Presenting our well structured Communication Plan To Mitigate Multiple Threat In It Sector. The topics discussed in this slide are Risk Level, Channel, Owner. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Steps To Create HR Crisis Threat Communication Plan
Effective Steps To Create HR Crisis Threat Communication PlanThe slide demonstrates risk communication plan to improve companys reputation and create best impression on all stakeholders. The steps are named as update employee contact information, perform risk assessment, develop policies, give relevant information, engage everyone. Introducing our premium set of slides with Effective Steps To Create HR Crisis Threat Communication Plan. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contact Information, Develop Policies, Engage Everyone. So download instantly and tailor it with your information.
-
 Several Threat Communication Barriers That Hinder Effective Management
Several Threat Communication Barriers That Hinder Effective ManagementThe following slide highlights various challenges in communicating so that management can eliminate these barriers and improve stakeholder opinion to promote accountability. The challenges are stakeholder diversification, Improper communication plan, Use of non standard language and Unsynchronized risk data. Presenting our set of slides with Several Threat Communication Barriers That Hinder Effective Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stakeholder Diversification, Unsynchronized Risk Data, Improper Communication Plan.
-
 Threat Communication Structure To Improve Organization Efficiency
Threat Communication Structure To Improve Organization EfficiencyThis slide covers process of risk communication which helps in taking effective decisions to prevent damage. It involves the following stages such as risk assessment, risk management and risk communication. Introducing our premium set of slides with Threat Communication Structure To Improve Organization Efficiency. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Risk Management, Risk Communication. So download instantly and tailor it with your information.
-
 Threat Communication Timeline For Efficient Management
Threat Communication Timeline For Efficient ManagementThe following slide outlines communication timeline for effective risk assessment and helps in controlling crises and providing useful suggestions to eliminate them. It contains gathering risk information, accurate understanding, believing, restrictions, choosing alternative options etc. Presenting our well structured Threat Communication Timeline For Efficient Management. The topics discussed in this slide are Timeline, Communication, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ways To Minimize Communication Threat In Project Management
Ways To Minimize Communication Threat In Project ManagementThis slide showcases methods to communicate risk status to all shareholders foe effective project management. Its key methods are understanding communication tools, audience, stakeholders, setting objectives and staying positive. Introducing our premium set of slides with Ways To Minimize Communication Threat In Project Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understand Stakeholders, Stay Positive, Set Objectives. So download instantly and tailor it with your information.
-
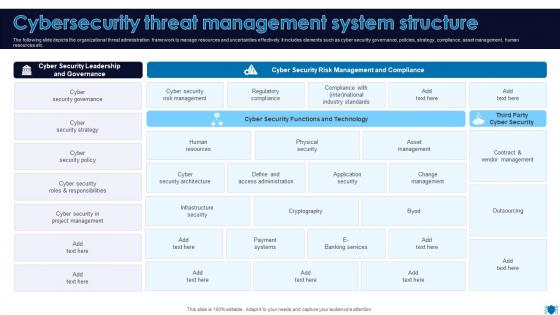 Cybersecurity Threat Management System Structure
Cybersecurity Threat Management System StructureThe following slide depicts the organizational threat administration framework to manage resources and uncertainties effectively. It includes elements such as cyber security governance, policies, strategy, compliance, asset management, human resources etc. Presenting our well structured Cybersecurity Threat Management System Structure. The topics discussed in this slide are Cyber Security Governance, Cyber Security Strategy, Cyber Security Policy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Country Wise Security Strategies For Virtual Terrorism
Country Wise Security Strategies For Virtual TerrorismThis slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc.Presenting our set of slides with Country Wise Security Strategies For Virtual Terrorism. This exhibits information on one stage of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Consumer Commission, Trusted Identities, Cyber Damage.
-
 Future Innovative Techniques For Global Virtual Terrorism
Future Innovative Techniques For Global Virtual TerrorismThis slide show future upcoming techniques for tackling global cyber terrorism attacks and providing overall security to business data. It include techniques like permanent remote work security, regular automation and zero-trust principles etc.Introducing our premium set of slides with Future Innovative Techniques For Global Virtual Terrorism. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Provide Permanent, Remote Work Security, Automate Regularly. So download instantly and tailor it with your information.
-
 Global Strategic Objectives For Tackling Virtual Terrorism
Global Strategic Objectives For Tackling Virtual TerrorismThis slide shows global level objectives to protect and promote digital business activities with transparency. It include objectives such as developing global level cyber crime system, building resilient system etc.Presenting our set of slides with Global Strategic Objectives For Tackling Virtual Terrorism. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Doing Business, Terrorism Providing, System For Tackling Global.
-
 Individual And Organizational Practices For Virtual Terrorism Attacks
Individual And Organizational Practices For Virtual Terrorism AttacksThis slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc.Introducing our premium set of slides with Individual And Organizational Practices For Virtual Terrorism Attacks. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Various Accounts, Keep Social Accounts, Security Programs. So download instantly and tailor it with your information.
-
 Organizational Planning Process For Virtual Terrorism
Organizational Planning Process For Virtual TerrorismPresenting our set of slides with Organizational Planning Process For Virtual Terrorism. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Understand Work Culture, Related Threats, Security Framework.
-
 Program Aligning Phases For Virtual Terrorism
Program Aligning Phases For Virtual TerrorismThis slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc.Introducing our premium set of slides with Program Aligning Phases For Virtual Terrorism. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understand Basics, Planning Phase, Aligning Phase. So download instantly and tailor it with your information.
-
 Program Budget Setting Approaches For Virtual Terrorism
Program Budget Setting Approaches For Virtual TerrorismThis slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc.Presenting our set of slides with Program Budget Setting Approaches For Virtual Terrorism. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Benchmarking Approach, Proactive Approach, Reactive Approach.
-
 Security Techniques For Virtual Terrorism Icon
Security Techniques For Virtual Terrorism IconPresenting our well structured Security Techniques For Virtual Terrorism Icon. The topics discussed in this slide are Security Techniques, Virtual Terrorism. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Signs For Various Virtual Terrorism Attacks
Signs For Various Virtual Terrorism AttacksThis slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc.Presenting our set of slides with Signs For Various Virtual Terrorism Attacks. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Accounts Hacked, Fraudulent Financial, Account Deductions.
-
 Virtual Terrorism Risk Identification Icon
Virtual Terrorism Risk Identification IconPresenting our set of slides with Virtual Terrorism Risk Identification Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Virtual Terrorism, Risk Identification.
-
 Virtual Terrorism Threat Attacking Network Icon
Virtual Terrorism Threat Attacking Network IconIntroducing our premium set of slides with Virtual Terrorism Threat Attacking Network Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Virtual Terrorism, Threat Attacking Network. So download instantly and tailor it with your information.
-
 Virtual Terrorism Types And Categories With Examples
Virtual Terrorism Types And Categories With ExamplesThis slide shows various categories of cyber terrorism attacks according to their severity . It include categories such as simple unstructured, advance structured, complex coordinated etc.Presenting our set of slides with Virtual Terrorism Types And Categories With Examples. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Simple Unstructured, Advance Structured, Complex Coordinated.
-
 Problem Related To Drug And Alcohol Abuse At Workplace Best Practices For Workplace Security
Problem Related To Drug And Alcohol Abuse At Workplace Best Practices For Workplace SecurityThe following slide highlights the problems with excessive drug and alcohol at workplace which showcases the alcohol abuse leads to multiple problems and major drinking habits that creates issues for work.Increase audience engagement and knowledge by dispensing information using Problem Related To Drug And Alcohol Abuse At Workplace Best Practices For Workplace Security. This template helps you present information on six stages. You can also present information on Environment Non Mandatory, Reproductive Toxicity, Skin Sensitizer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Safety Guidelines To Detect And Prevent Alcohol Abuse Best Practices For Workplace Security
Safety Guidelines To Detect And Prevent Alcohol Abuse Best Practices For Workplace SecurityThis slide highlights the preventive and detective measures for alcohol abuse which showcase multiple ways to deal the situation with training program, and experts assistance.Increase audience engagement and knowledge by dispensing information using Safety Guidelines To Detect And Prevent Alcohol Abuse Best Practices For Workplace Security. This template helps you present information on four stages. You can also present information on Raise Alarm, Alert Everyone, Exposure Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Macro Analysis Of Threats Checklist Icon
Macro Analysis Of Threats Checklist IconPresenting our set of slides with Macro Analysis Of Threats Checklist Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Macro Analysis, Threats Checklist Icon.
-
 Macro Level Threat Detection And Analysis Icon
Macro Level Threat Detection And Analysis IconIntroducing our premium set of slides with Macro Level Threat Detection And Analysis Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Macro Level Threat Detection, Analysis Icon. So download instantly and tailor it with your information.
-
 Key Potential Threats For Phone Security
Key Potential Threats For Phone SecurityThis slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Presenting our set of slides with Key Potential Threats For Phone Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Sensitive Data Theft, Impersonation Threats.
-
 Phone Security Tools For Preventing Threats
Phone Security Tools For Preventing ThreatsThis slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc Presenting our set of slides with Phone Security Tools For Preventing Threats. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Loss Prevention, Customer Feedback.
-
 Smart Phone Security Threats With Solutions
Smart Phone Security Threats With SolutionsThis slide show various categories of phone security threats with sub-categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Introducing our premium set of slides with Smart Phone Security Threats With Solutions. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Download Application Threats, Cyber Security Threats. So download instantly and tailor it with your information.
-
 Deal Harassment Work Manager In Powerpoint And Google Slides Cpb
Deal Harassment Work Manager In Powerpoint And Google Slides CpbPresenting Deal Harassment Work Manager In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Deal Harassment Work Manager This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Competitive Business Threats Analysis Business Growth And Success Strategic Guide Strategy SS
Competitive Business Threats Analysis Business Growth And Success Strategic Guide Strategy SSThis slide showcases strengths analysis comparison matrix of own business and competitors to identify risks. It assess businesses based on competition, economic downtowns, change in regulations, technology evolution, supply chain disruptions. Deliver an outstanding presentation on the topic using this Competitive Business Threats Analysis Business Growth And Success Strategic Guide Strategy SS. Dispense information and present a thorough explanation of Business, Threats, Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





