Powerpoint Templates and Google slides for Abuse
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Security Threats Compliance Violations Cloud Data Protection
Cloud Security Threats Compliance Violations Cloud Data ProtectionThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. Introducing Cloud Security Threats Compliance Violations Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Authentication Procedures, Business, Organizations, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Data Protection
Cloud Security Threats Contract Breaches With Clients Cloud Data ProtectionThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Data Protection. This template helps you present information on four stages. You can also present information on Business Partners, Organization, Cloud using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats End User Control Cloud Data Protection
Cloud Security Threats End User Control Cloud Data ProtectionThis slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. Introducing Cloud Security Threats End User Control Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Business Data, Customers, Centralized Data, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Data Protection
Cloud Security Threats Loss Of Data Cloud Data ProtectionThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Data Protection. This template helps you present information on four stages. You can also present information on Storage Locations, Organization, Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Malware Attacks Cloud Data Protection
Cloud Security Threats Malware Attacks Cloud Data ProtectionThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Introducing Cloud Security Threats Malware Attacks Cloud Data Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Frameworks, Targets, Technology, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Revenue Losses Cloud Data Protection
Cloud Security Threats Revenue Losses Cloud Data ProtectionThis slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Revenue Losses Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organizations Could, Revenue, Customers using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Threats Shared Vulnerabilities Cloud Data Protection
Cloud Security Threats Shared Vulnerabilities Cloud Data ProtectionThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Introducing Cloud Security Threats Shared Vulnerabilities Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Secure Cloud Data, Organizations, Data Security, using this template. Grab it now to reap its full benefits.
-
 Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G Deployment
Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G DeploymentThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Present the topic in a bit more detail with this Key Security Considerations For 5G For Threat Handling Proactive Approach For 5G Deployment. Use it as a tool for discussion and navigation on Virtualization Threats, Information Interception, Unauthorized Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strength Weakness Opportunity Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Strength Weakness Opportunity Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Strength weakness opportunity threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Strength Weakness Opportunity Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Strength Weakness Opportunity Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Strength weakness opportunity threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Risk Management Plan To Mitigate Threats Retail Merchandising Plan
Risk Management Plan To Mitigate Threats Retail Merchandising PlanThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Risk Management Plan To Mitigate Threats Retail Merchandising Plan. Dispense information and present a thorough explanation of Residual Risk, Cost, Revised Probability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators
Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines OperatorsThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators. Dispense information and present a thorough explanation of Unauthorized Activities, Virtualization Threats, Information Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Four Information Technology Security Threats
Four Information Technology Security ThreatsIntroducing our premium set of slides with Four Information Technology Security Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing Attacks, Cloud Jacking, Insider Threats. So download instantly and tailor it with your information.
-
 5G Technology Enabling Key Security Considerations For 5G For Threat Handling
5G Technology Enabling Key Security Considerations For 5G For Threat HandlingThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this 5G Technology Enabling Key Security Considerations For 5G For Threat Handling. Dispense information and present a thorough explanation of Threat Handling Initiatives, Concerns To Catered, Assets Managed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 List Opportunities Threats In Powerpoint And Google Slides Cpb
List Opportunities Threats In Powerpoint And Google Slides CpbPresenting List Opportunities Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like List Opportunities Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Evolving Cyber Threats In Powerpoint And Google Slides Cpb
Evolving Cyber Threats In Powerpoint And Google Slides CpbPresenting Evolving Cyber Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Evolving Cyber Threats. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Threat Assessment Checklist With Solution
Cyber Security Threat Assessment Checklist With SolutionThe following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Introducing our Cyber Security Threat Assessment Checklist With Solution set of slides. The topics discussed in these slides are System Threat, Data Threat, Cloud Security Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Threat Intelligence Cycle
Cyber Security Threat Intelligence CycleThe following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Introducing our premium set of slides with name Cyber Security Threat Intelligence Cycle. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Direction, Collection, Processing, Analysis, Reporting. So download instantly and tailor it with your information.
-
 Cyber Security Threat Mitigation Strategies
Cyber Security Threat Mitigation StrategiesThe following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting our set of slides with name Cyber Security Threat Mitigation Strategies. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Assessment, Patch Management, Traffic Monitoring.
-
 E Commerce Business Security Threats And Solutions
E Commerce Business Security Threats And SolutionsThis slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Introducing our E Commerce Business Security Threats And Solutions set of slides. The topics discussed in these slides are Business Security Risks, Threat Type, Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Server Security Threat Report With Action Plan
Server Security Threat Report With Action PlanThis slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident.Introducing our premium set of slides with Server Security Threat Report With Action Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Profile, Diagnostic, Action Plan. So download instantly and tailor it with your information.
-
 Threats Swot Analysis In Powerpoint And Google Slides Cpb
Threats Swot Analysis In Powerpoint And Google Slides CpbPresenting our innovatively designed set of slides titled Threats Swot Analysis In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Threats Swot Analysis that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
-
 Being Abused Work In Powerpoint And Google Slides Cpb
Being Abused Work In Powerpoint And Google Slides CpbPresenting our Being Abused Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Being Abused Work. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis Threats
Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis ThreatsThis slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Increase audience engagement and knowledge by dispensing information using Q235 Emerging Business Model Pharmaceutical Company SWOT Analysis Threats. This template helps you present information on four stages. You can also present information on High Competition, Regulations International Trade, Suppliers, Threat using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Backward Integration In Powerpoint And Google Slides Cpb
Threat Backward Integration In Powerpoint And Google Slides CpbPresenting Threat Backward Integration In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Backward Integration. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate Threats
Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate ThreatsThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate Threats. Dispense information and present a thorough explanation of Cost, Quality, Secondary Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Classification Of IT Risks With Threats
IT Risk Management Strategies Classification Of IT Risks With ThreatsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this IT Risk Management Strategies Classification Of IT Risks With Threats. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Icon To Reduce Threats
Information Technology Security Icon To Reduce ThreatsIntroducing our premium set of slides with Information Technology Security Icon To Reduce Threats. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology Security Icon, Reduce Threats. So download instantly and tailor it with your information.
-
 Risk Management Plan To Mitigate Threats Approaches To Merchandise Planning
Risk Management Plan To Mitigate Threats Approaches To Merchandise PlanningThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Risk Management Plan To Mitigate Threats Approaches To Merchandise Planning. Dispense information and present a thorough explanation of Mitigation Actions, Probability, Residual Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Of Substitute Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat of substitute colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Of Substitute Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat of substitute monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 IT Security Threat Mitigation Strategies
IT Security Threat Mitigation StrategiesThe slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring Introducing our premium set of slides with IT Security Threat Mitigation Strategies. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Assessment, Network Access Controls, Incident Response Plan, Regular Network Traffic Monitoring. So download instantly and tailor it with your information.
-
 Risk Assessment Scorecard For Strategic Threat
Risk Assessment Scorecard For Strategic ThreatThis slide shows scorecard for procurement of risk assessment used by organizations to eliminate potential threats. This slide provides data regarding area, scorecard criteria, risk rating scale, remarks, area wise weight and rating, week to date rating and overall rating. Introducing our Risk Assessment Scorecard For Strategic Threat set of slides. The topics discussed in these slides are Scorecard Criteria, Supply Risk Rating, Strategic Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IT Risk Management Strategies Information Technology Risks Form Human Threat Source
IT Risk Management Strategies Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this IT Risk Management Strategies Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action
IT Risk Management Strategies IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Classification Of IT Risks With Threats
Enterprise Risk Management Classification Of IT Risks With ThreatsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Enterprise Risk Management Classification Of IT Risks With Threats. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
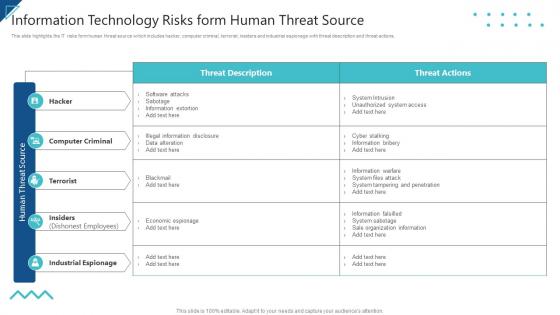 Enterprise Risk Management Information Technology Risks Form Human Threat Source
Enterprise Risk Management Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Enterprise Risk Management Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management IT Vulnerabilities With Threat Source And Action
Enterprise Risk Management IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this Enterprise Risk Management IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats In Powerpoint And Google Slides Cpb
Cyber Security Threats In Powerpoint And Google Slides CpbPresenting our Cyber Security Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems
Classification Of IT Risks With Threats Risk Management Guide For Information Technology SystemsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems
IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology SystemsThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Risk Assessment In Powerpoint And Google Slides Cpb
Threat Risk Assessment In Powerpoint And Google Slides CpbPresenting our Threat Risk Assessment In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Threat Risk Assessment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk Mitigation Plan Framework To Minimize Threats
Risk Mitigation Plan Framework To Minimize ThreatsThis slide shows the risk mitigation plan framework to minimize threats which includes definition of risks, probability and consequences, business impact analysis, risk management strategies, risk mitigation action planning, plan execution and monitoring, etc. Deliver an outstanding presentation on the topic using this Risk Mitigation Plan Framework To Minimize Threats. Dispense information and present a thorough explanation of Risk Mitigation, Executing And Monitoring, Risk Probability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Substitutes Examples In Powerpoint And Google Slides Cpb
Threat Substitutes Examples In Powerpoint And Google Slides CpbPresenting Threat Substitutes Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Substitutes Examples. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Threats And Key Performance Indicators
Cyber Security Threats And Key Performance IndicatorsThis slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Introducing our Cyber Security Threats And Key Performance Indicators set of slides. The topics discussed in these slides are Security Incidents, Intrusion Attempts, Unidentified Devices. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Components Of Risk Scenario With Threat Type
Key Components Of Risk Scenario With Threat TypeThis slide focuses on the key components of risk scenario which focuses on management, threat type, event, resource and time that further includes staff members, contractors, competitors, natural disasters, modifications, processes, data management, interruptions, etc. Introducing our premium set of slides with Key Components Of Risk Scenario With Threat Type. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management, Threat Type, Time, Event. So download instantly and tailor it with your information.
-
 Analysing The Impact Of Security Threats On Organization Information Security Risk Management
Analysing The Impact Of Security Threats On Organization Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Analysing The Impact Of Security Threats On Organization Information Security Risk Management. Dispense information and present a thorough explanation of Analysing, Security Threats, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Information Security Risk Management
Identifying Information Security Threats And Impact Information Security Risk ManagementThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Increase audience engagement and knowledge by dispensing information using Identifying Information Security Threats And Impact Information Security Risk Management. This template helps you present information on one stage. You can also present information on Errors And Omissions, Employee Sabotage, Physical Infrastructure Loss using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Matrix For Threat Solution And Risk Management Information Security Risk Management
Matrix For Threat Solution And Risk Management Information Security Risk ManagementThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Introducing Matrix For Threat Solution And Risk Management Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Monitor Database Activity, Validate Database Protocols, Capture Detailed Transactions, using this template. Grab it now to reap its full benefits.
-
 Mitigation Plan For Resolving Encountered Threat Information Security Risk Management
Mitigation Plan For Resolving Encountered Threat Information Security Risk ManagementMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Mitigation Plan For Resolving Encountered Threat Information Security Risk Management. Dispense information and present a thorough explanation of Risk Mitigation Plan, Expected Resolution Time, Mitigation Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management
Mitigation Strategies To Tackle Information Security Threats Information Security Risk ManagementThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management. This template helps you present information on five stages. You can also present information on Mitigation Strategies, Tackle Information, Security Threats using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Threat Of Substitute Product Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Product Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat of substitute product colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Of Substitute Product Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Product Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat of substitute product monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Threat Of Substitute Products Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Products Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat of substitute products colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Of Substitute Products Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Products Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat of substitute products monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.





