Comprehensive Curriculum for Data Privacy Training PPT
What is it
- EduDecks are professionally-created comprehensive decks that provide complete coverage of the subject under discussion
- These are also innovatively-designed for a powerful learning experience and maximum retention
Who is it for?
- EduDecks are for Trainers who want to add punch and flair to program and leave a lasting impact on their trainees
- They are also for Teachers who want to win over their students with content as well design
Why EduDecks?
- EduDecks provide an A-Z coverage of courses on any topic and covers it in both great depth and wide scope
- These slides are also professionally-designed to deliver a punch to your programs
Why Corporate Trainers love us?
- Content created by Industry experts, active in their fields
- Relevant concepts supplemented with industry case studies
- Visually appealing slides with 100% accurate & relevant data
Why Teachers love us?
- Comprehensive curriculum covering all aspects of the topic
- Relevant examples provided with the topics
- Just download and amaze your audience without making any content changes
What you will get
- 17 Structured Sessions
- 40+ Thought Provoking Questions
- Detailed Instructor Notes
- 350+ Professionally Desgined Slides
People who downloaded this PowerPoint presentation also viewed the following :
Create an Immersive Training Experience
Created by Subject Matter Experts
Professionally Designed Slides
Structured Sessions
Comprehensive Curriculum
Detailed Teaching Notes
Real-Life Case Studies
Assessment Questions
Client Proposal
Complete Curriculum
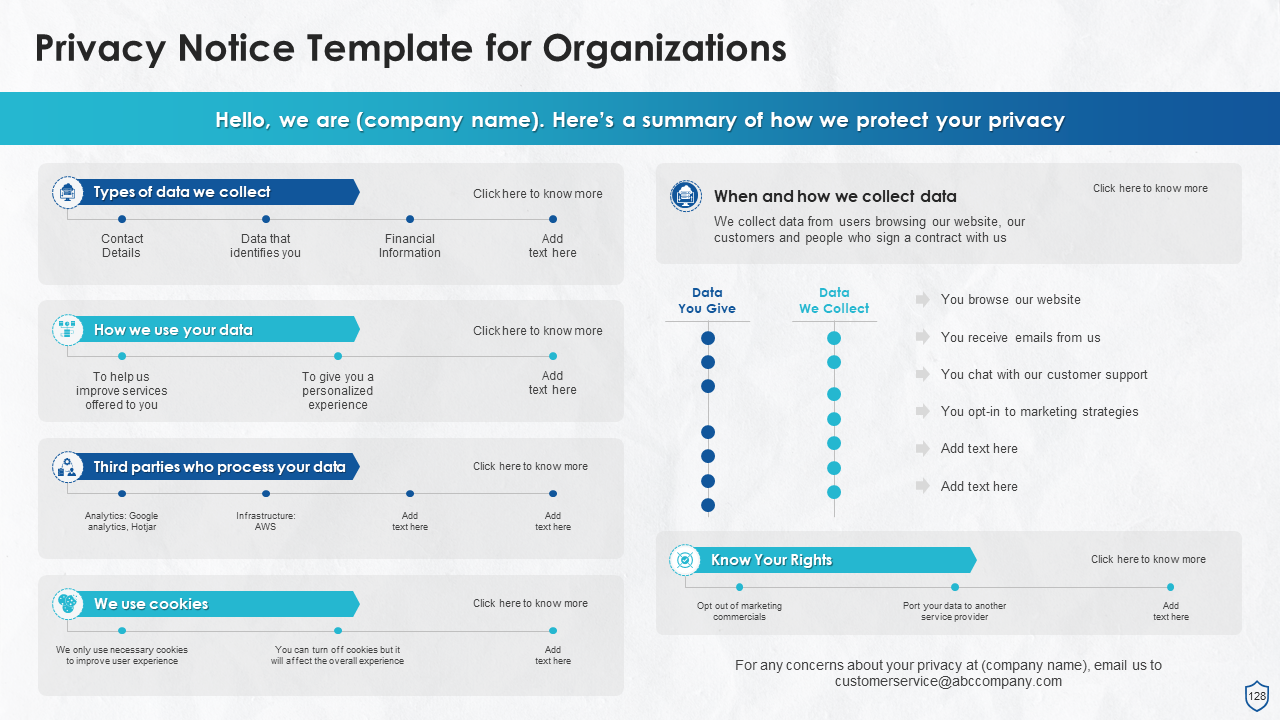
- What is Data Privacy?
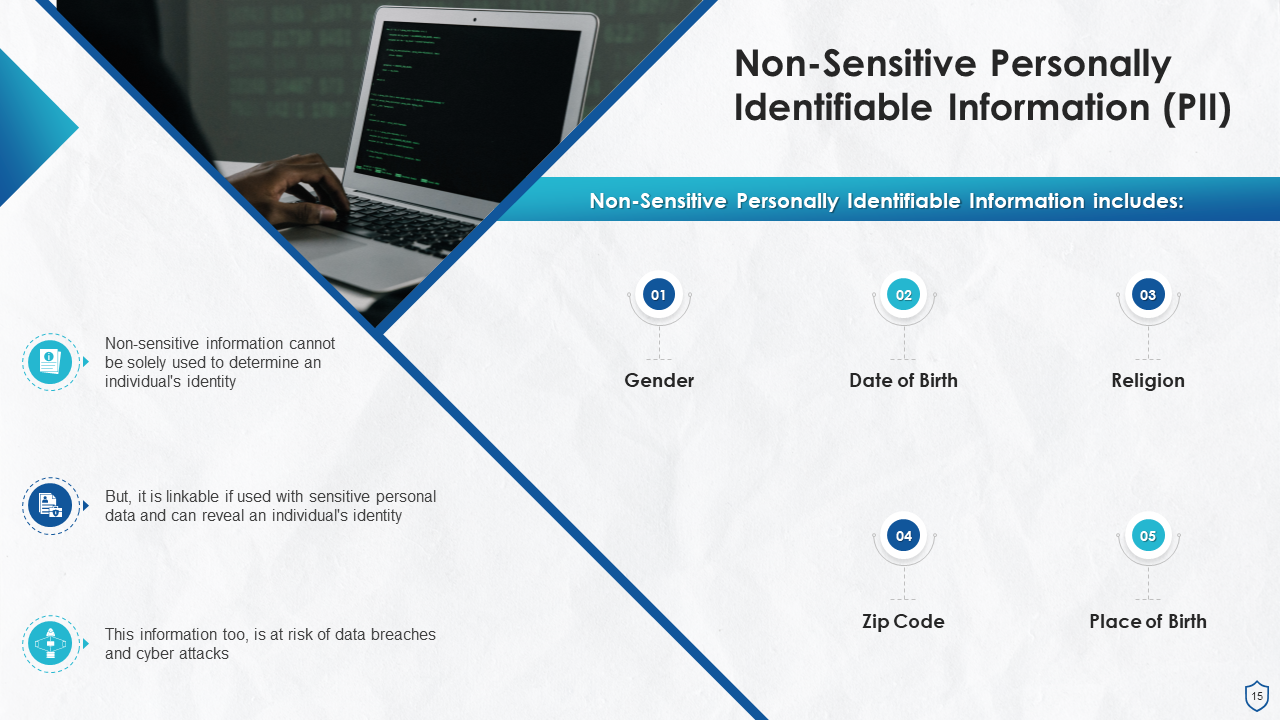
- What is Personally Identifiable Information (PII)?
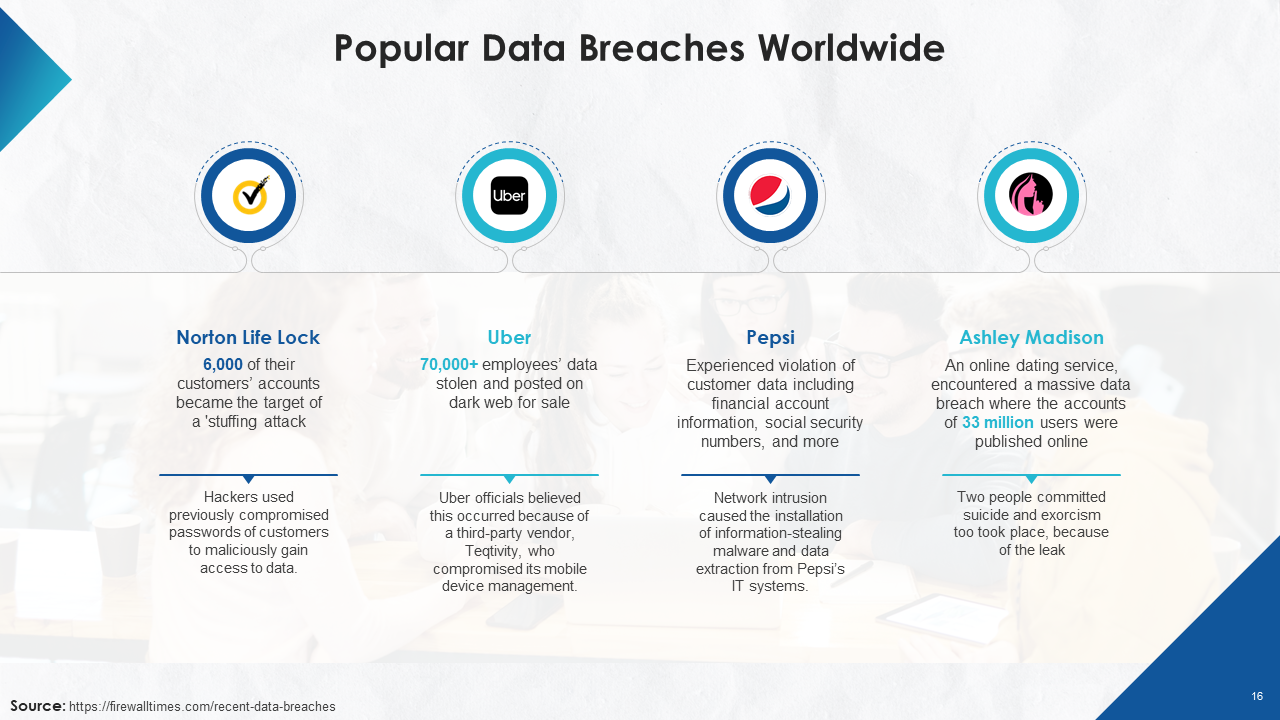
- Popular Data Breaches
- Impact of Data Breaches on Business
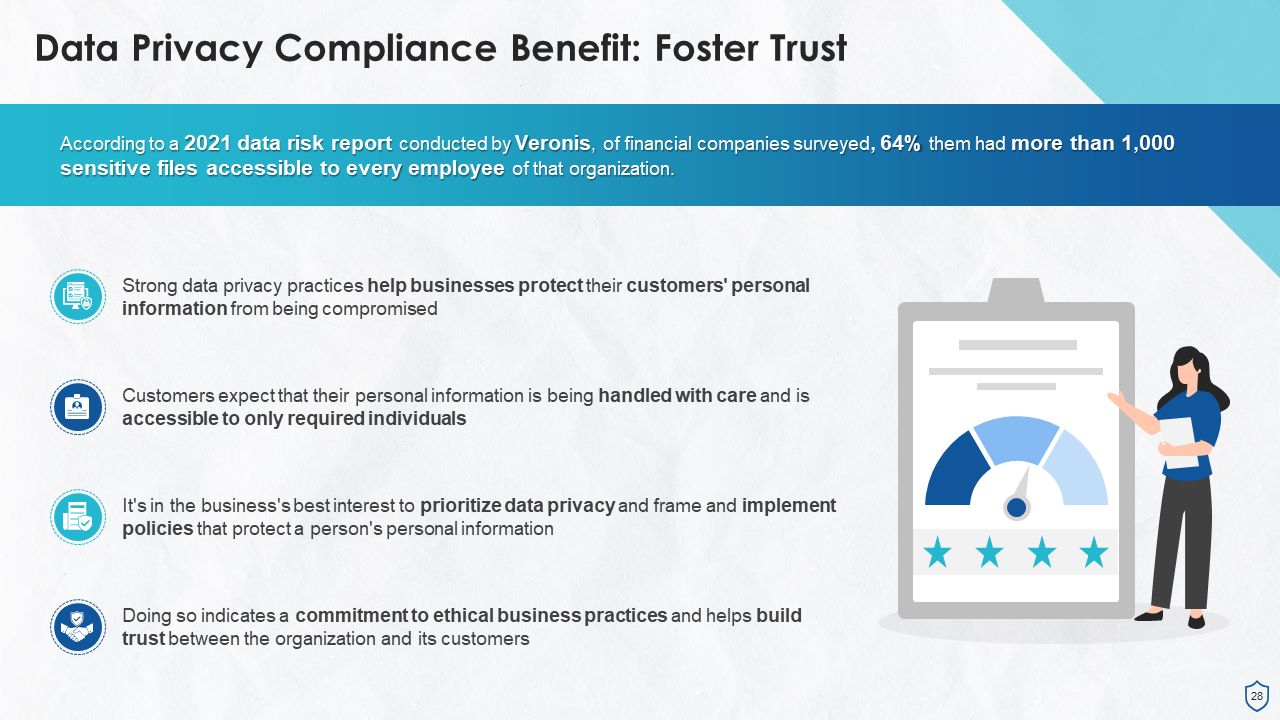
- Benefits of Data Privacy Compliances for Organizations
- Facts and Figures on Data Privacy Compliances
- Poster for Data Privacy Day
- Key Takeaways
- Let’s Discuss
- GDPR in a Nutshell
- Timeline of GDPR Formation
- Applicability of GDPR
- Objectives of GDPR
- GDPR Lines of Defence
- Life Cycle of GDPR Data
- Key Takeaways
- Let’s Discuss
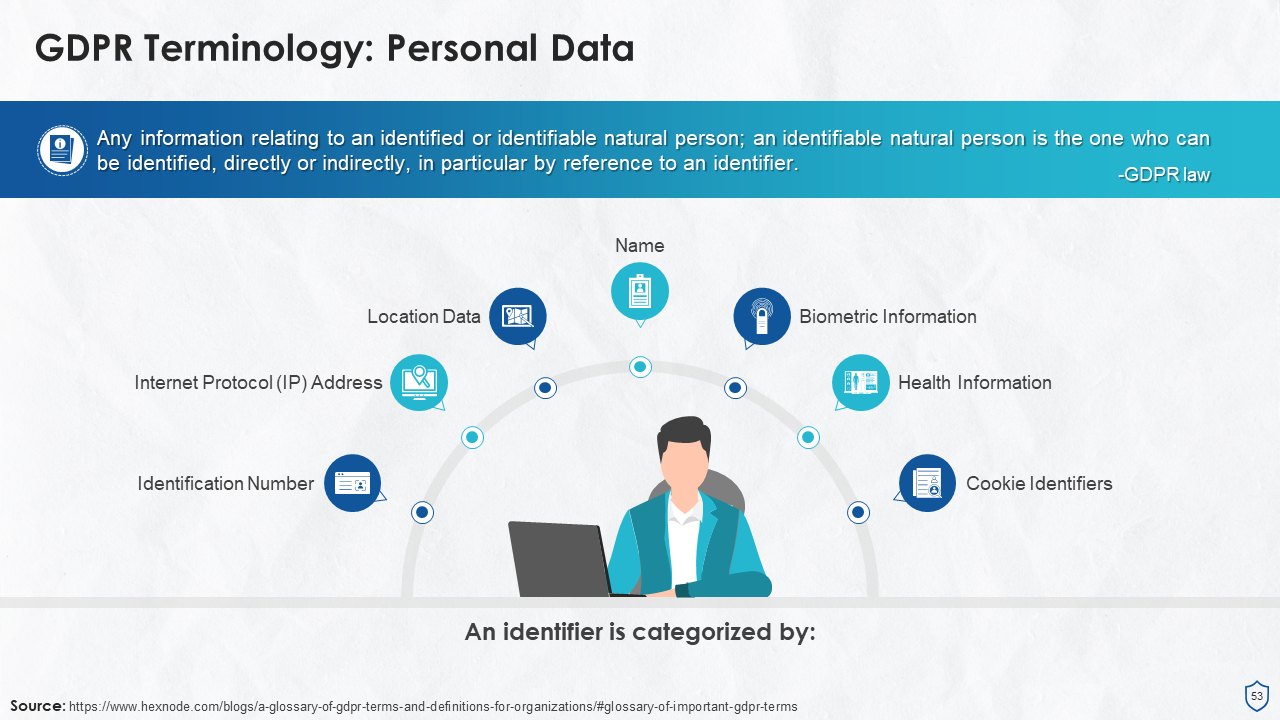
- Personal Data
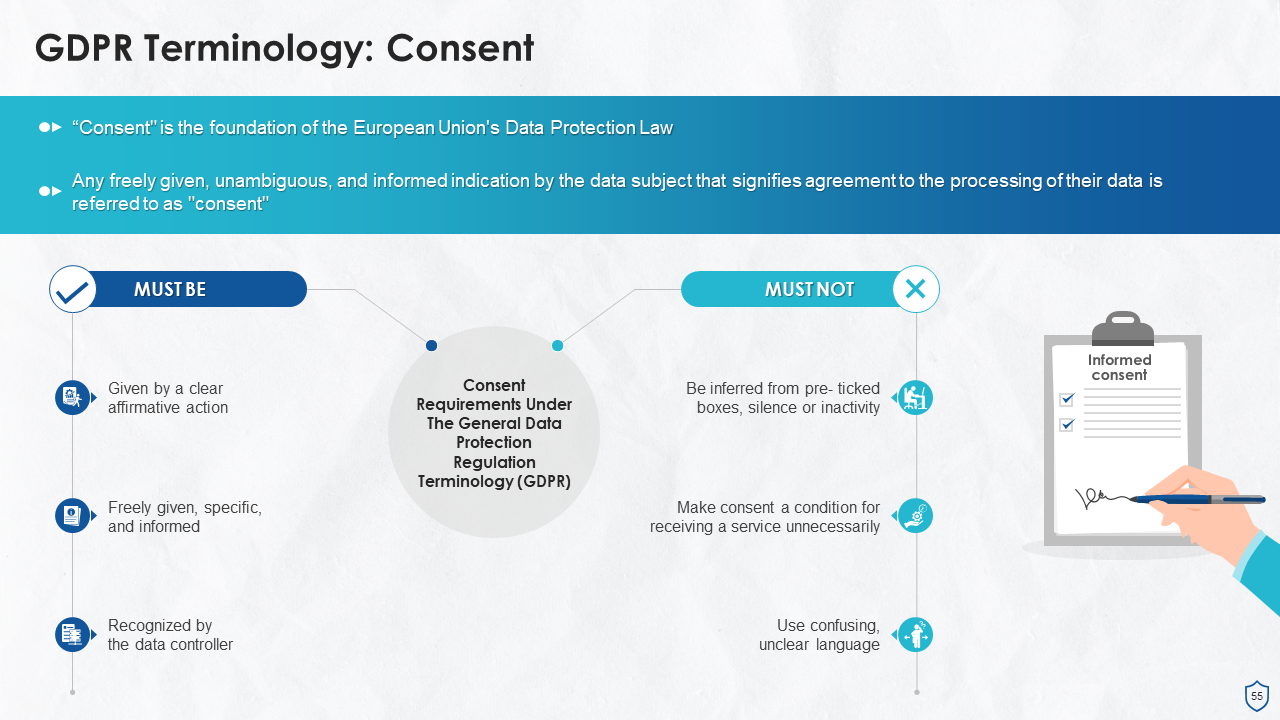
- Consent
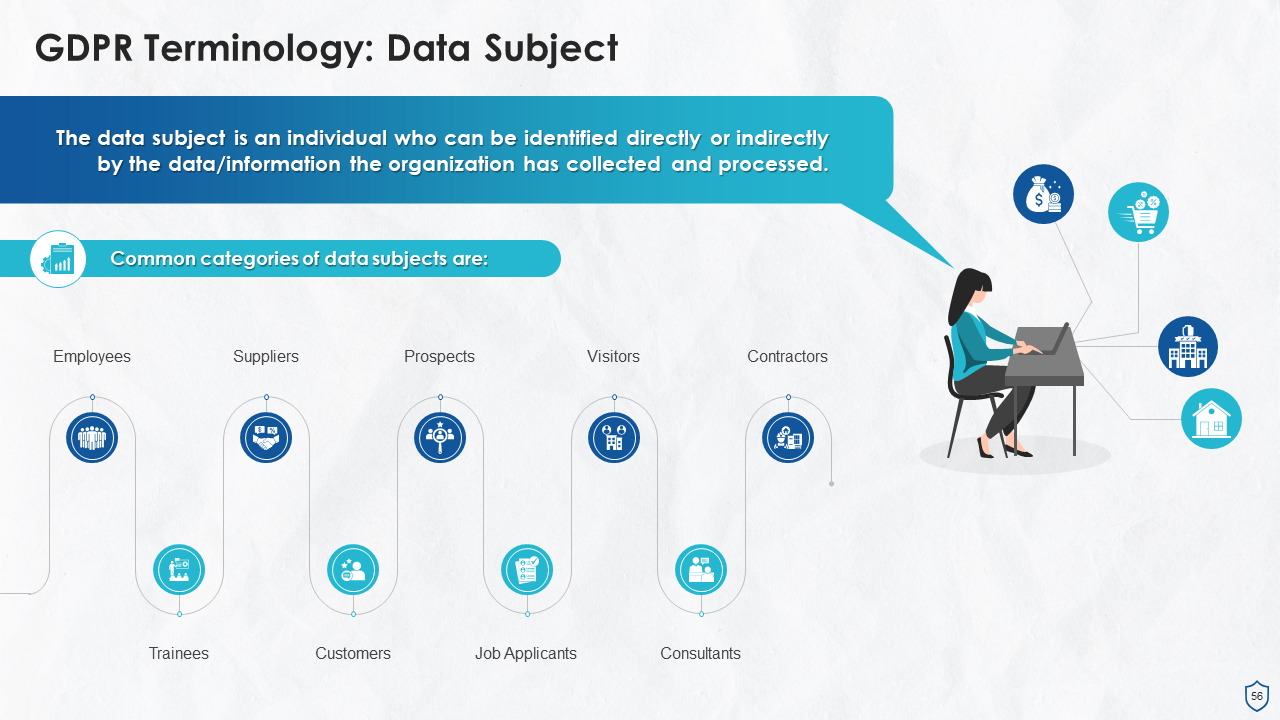
- Data Subject as per Geographical Territory
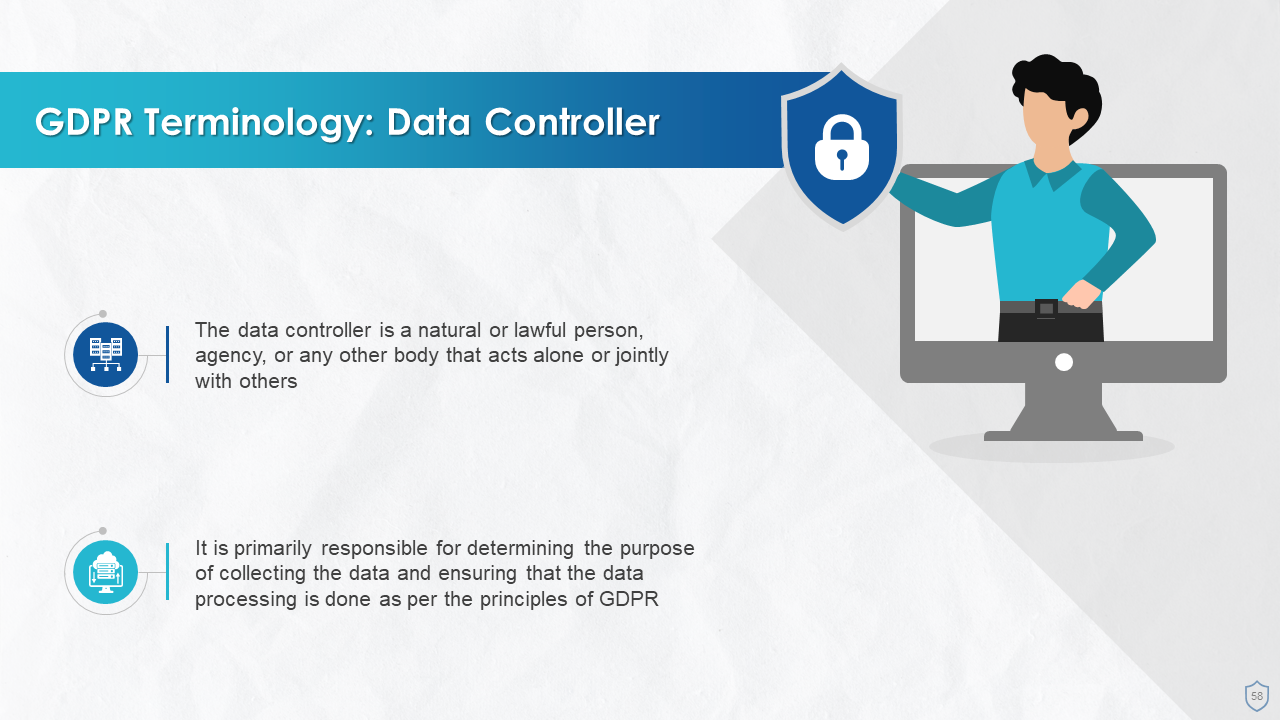
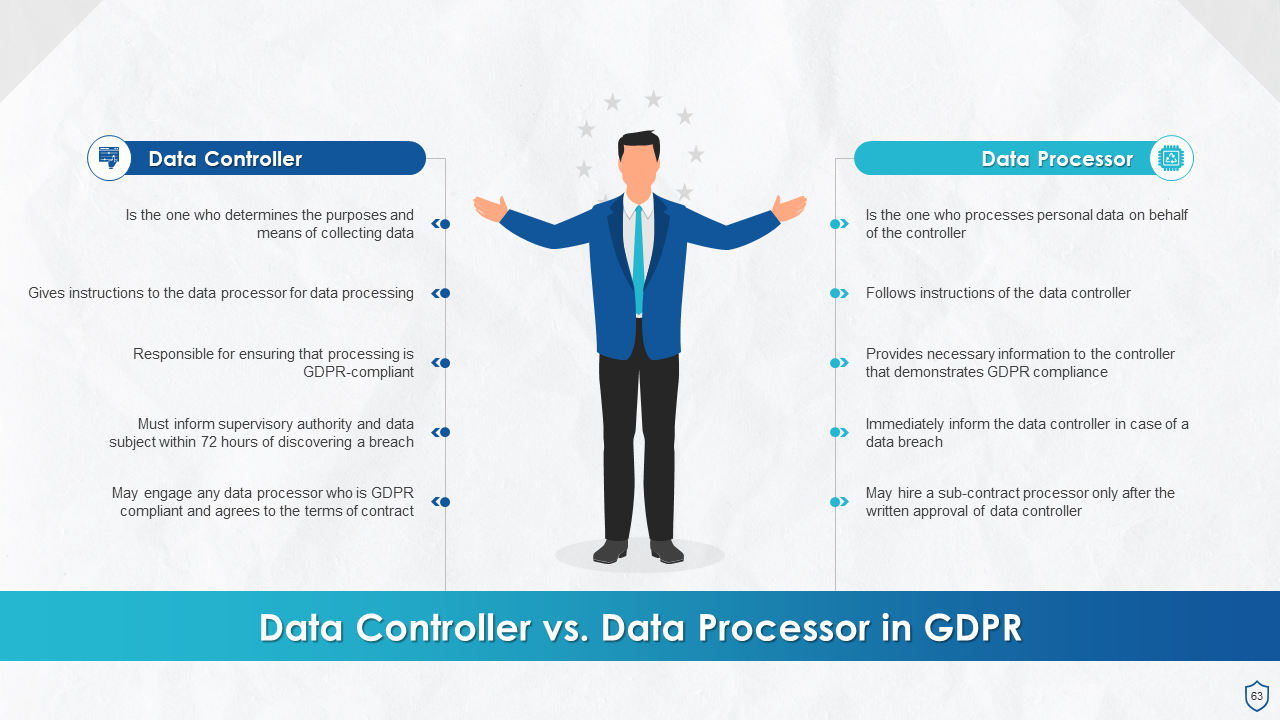
- Data Controller
- Data Processor
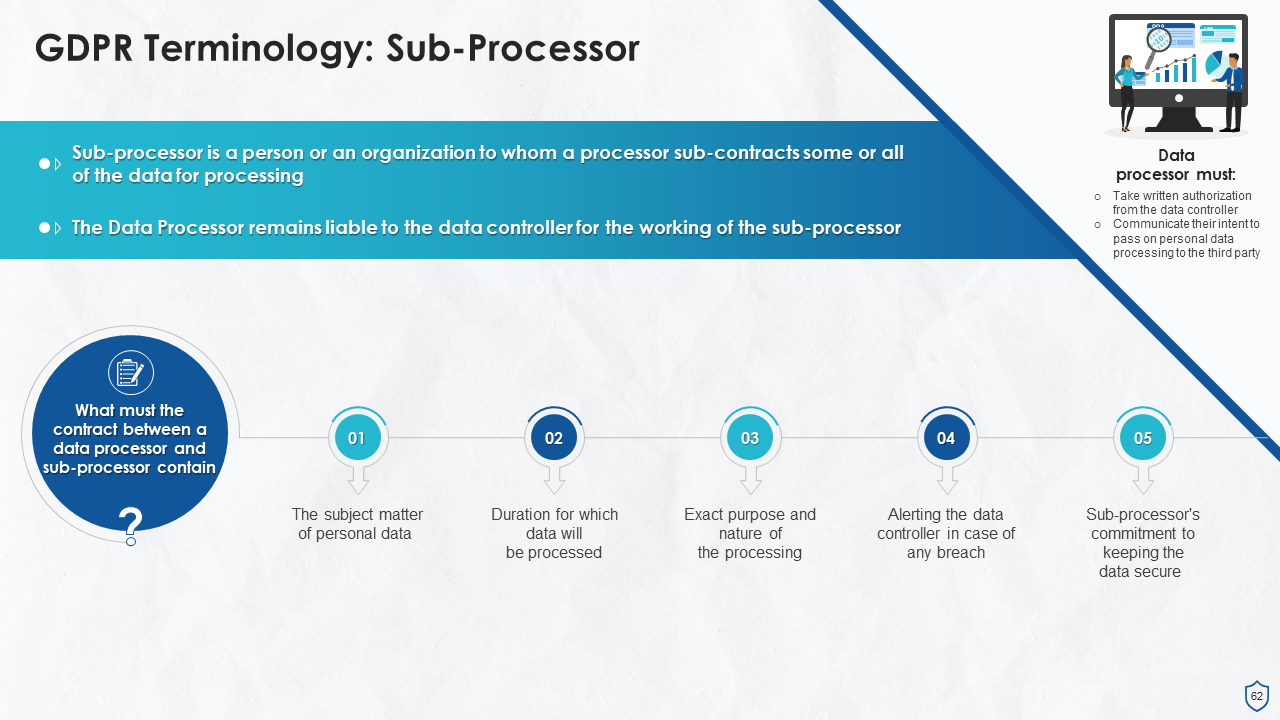
- Sub-Processor
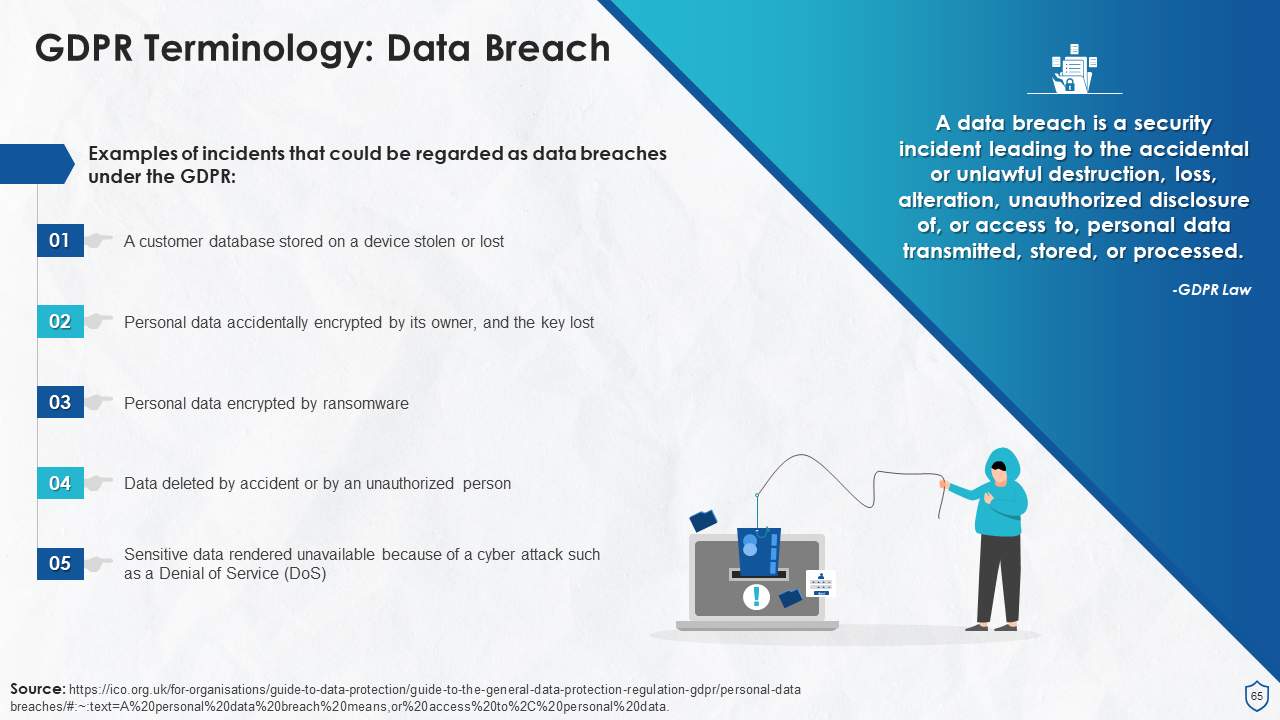
- Data Breach
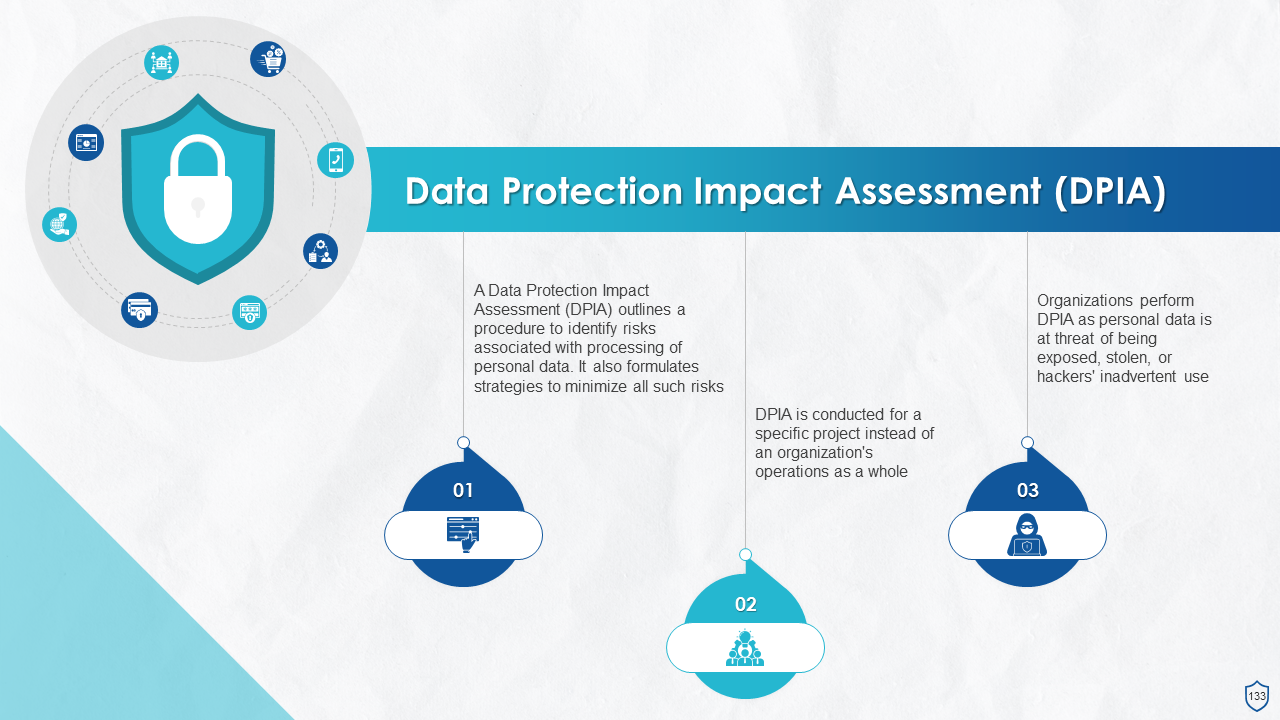
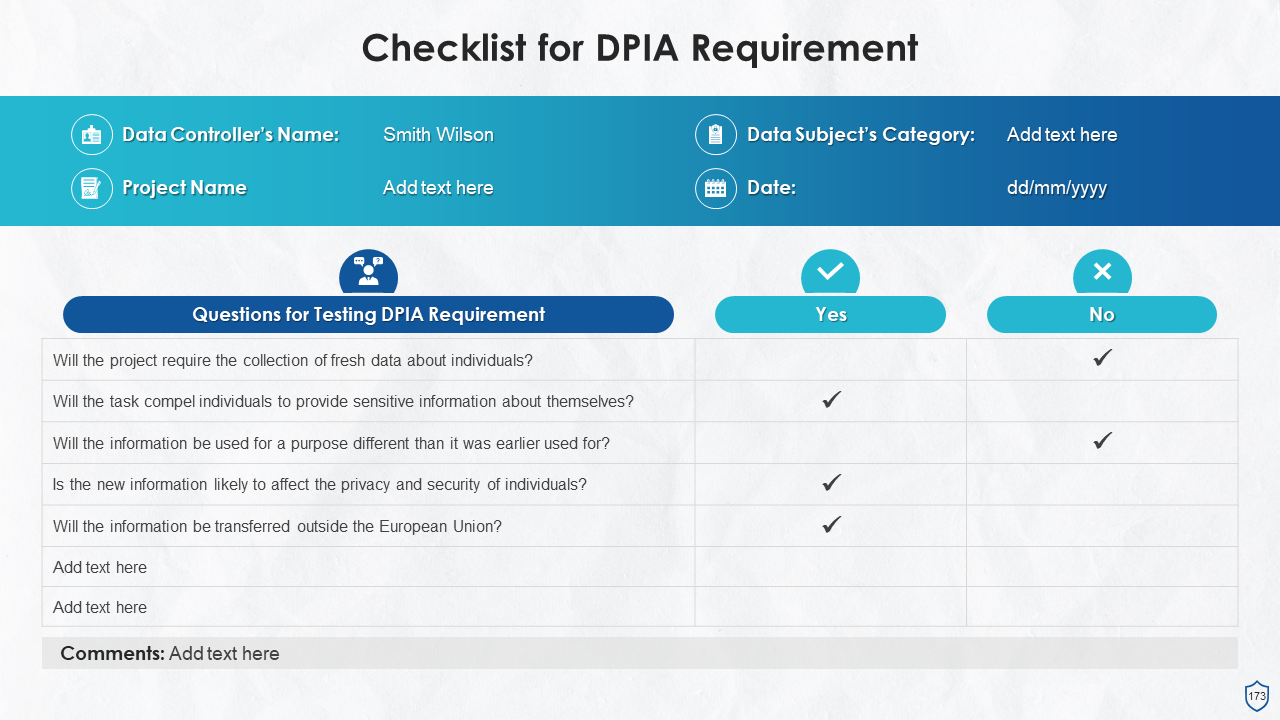
- Data Protection Impact Assessment (DPIA)
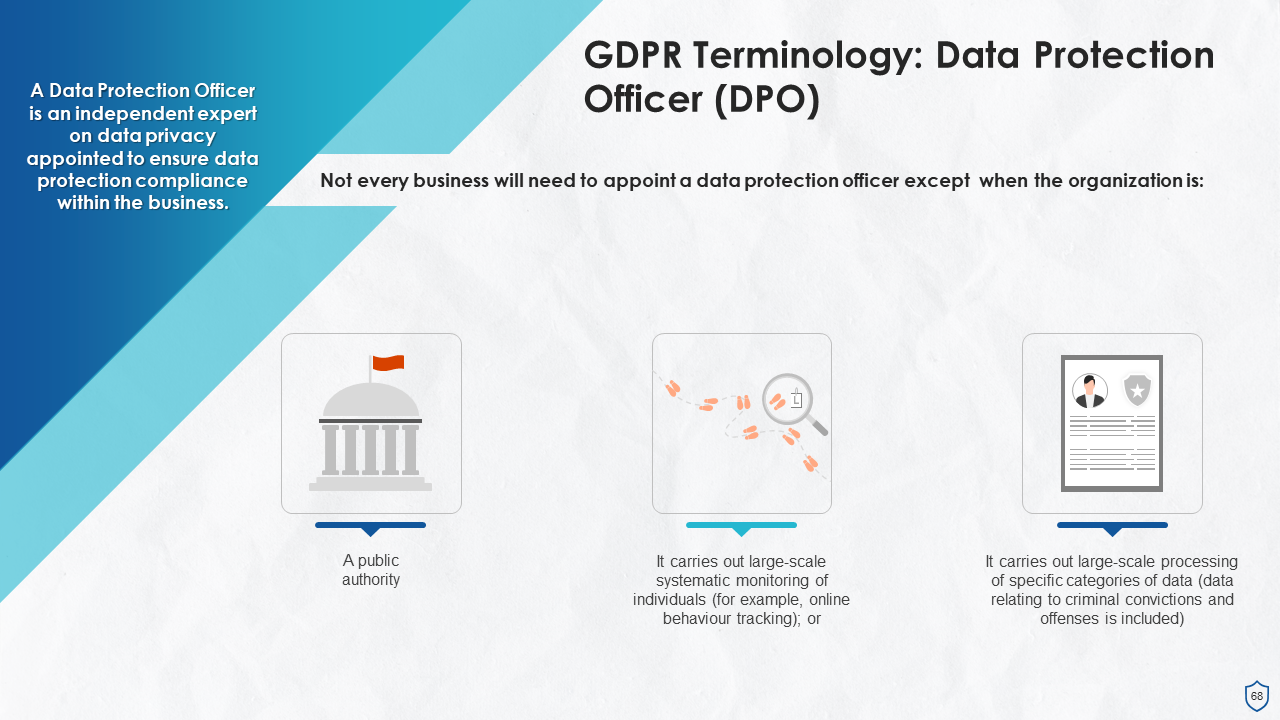
- Data Protection Officer (DPO)
- Binding Corporate Rules (BCRs)
- Pseudonymisation
- Key Takeaways
- Let’s Discuss
- Lawfulness, Fairness and Transparency
- Purpose Limitation
- Data Minimisation
- Accuracy
- Storage Limitation
- Integrity and Confidentiality
- Accountability
- Key Takeaways
- Let’s Discuss
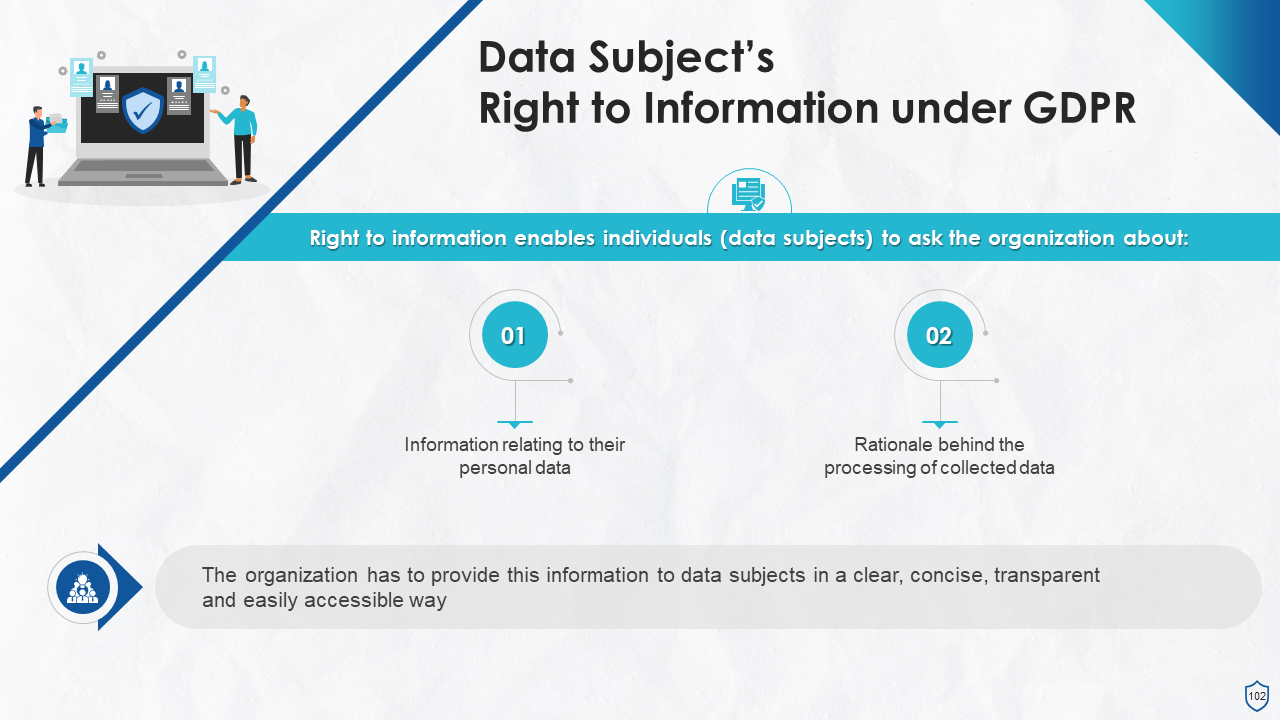
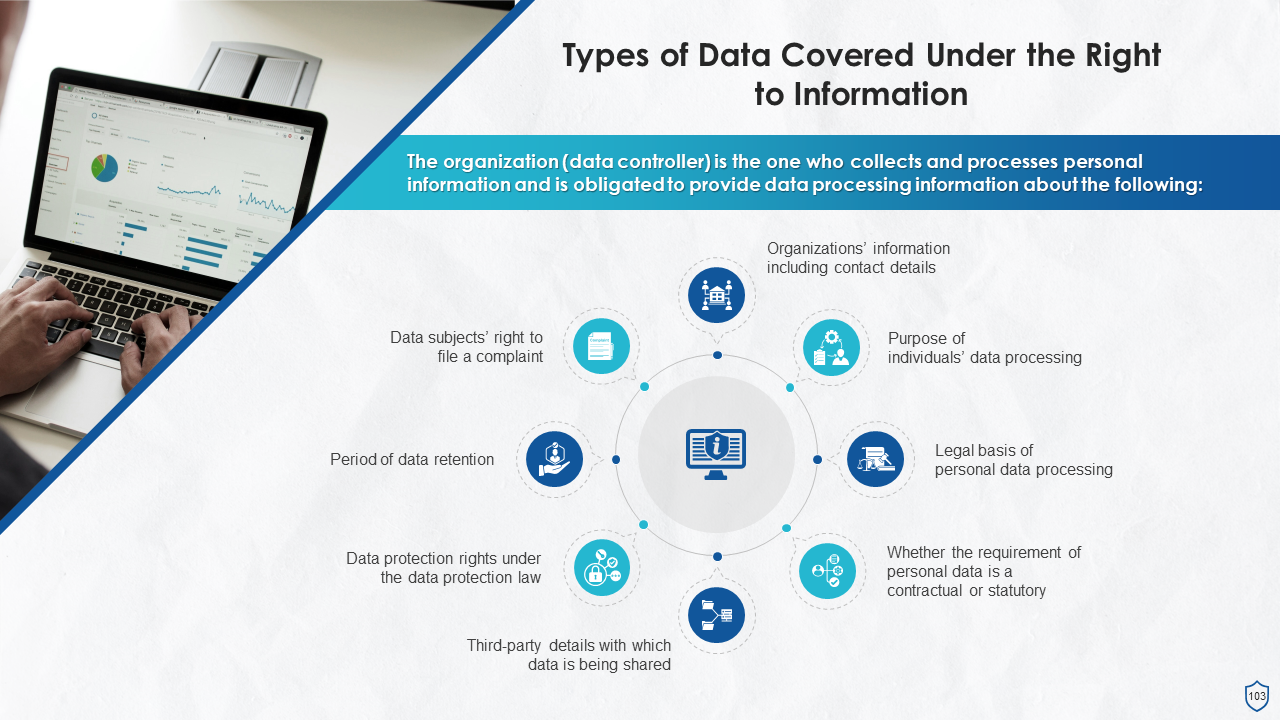
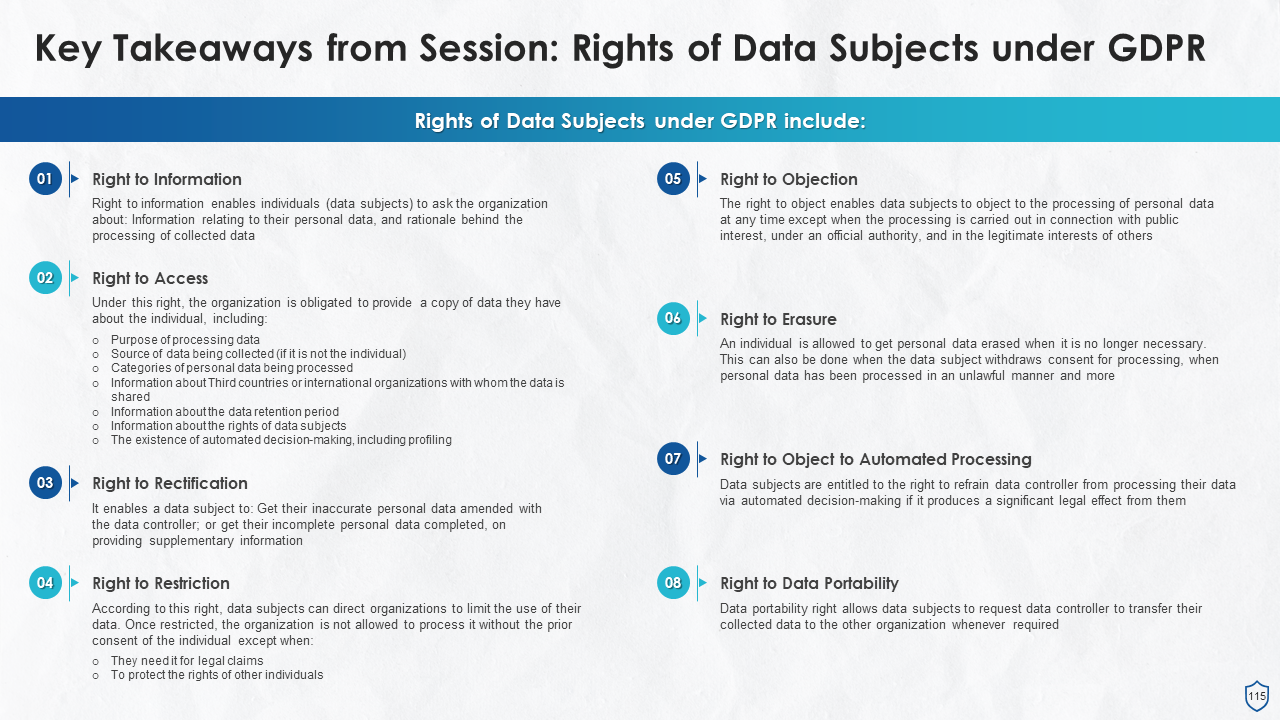
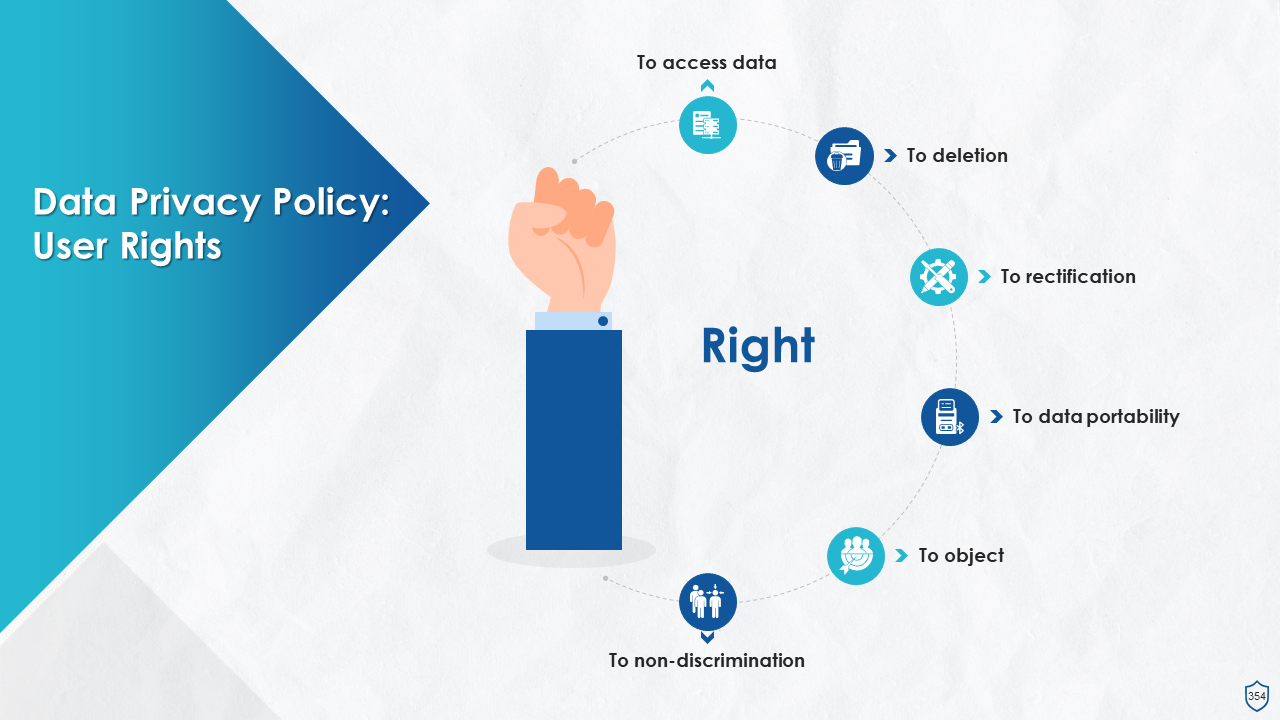
- Right to Information
- Right to Access
- Right to Rectification
- Right to Restriction
- Right to Objection
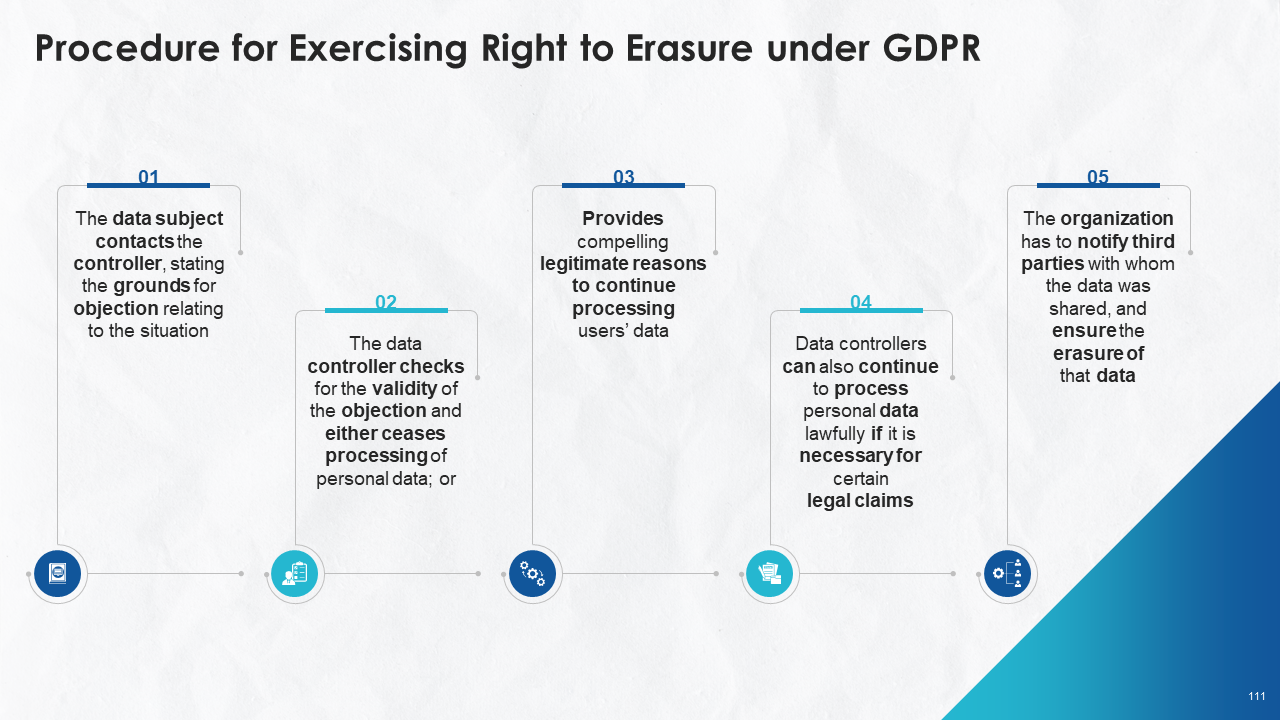
- Right to Erasure
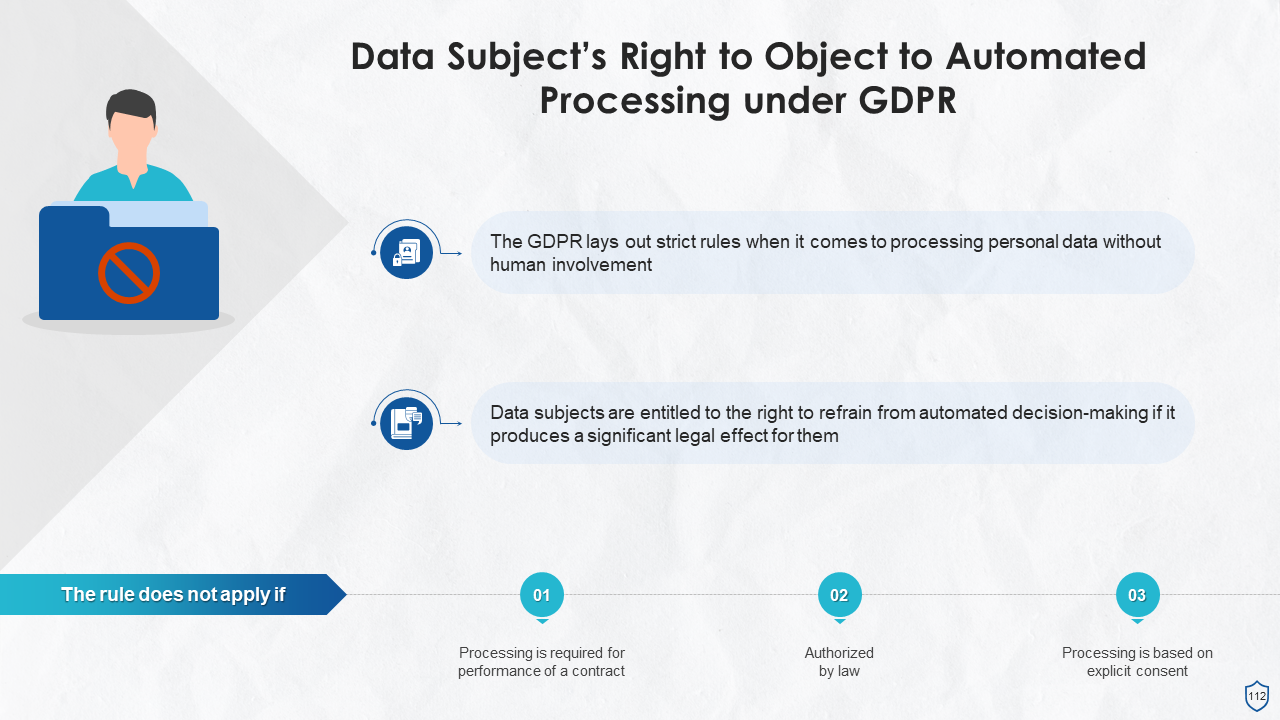
- Right to Object to Automated Processing
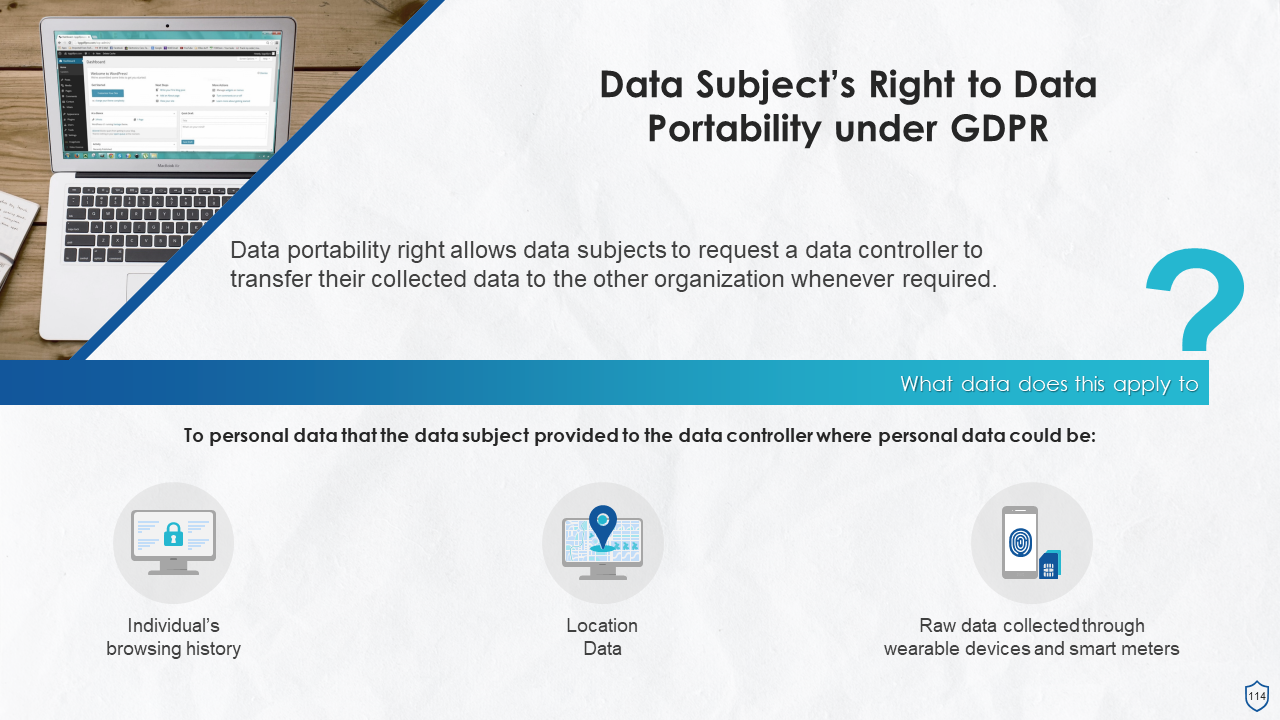
- Right to Data Portability
- Key Takeaways
- Let’s Discuss
- Definition of GDPR Compliance
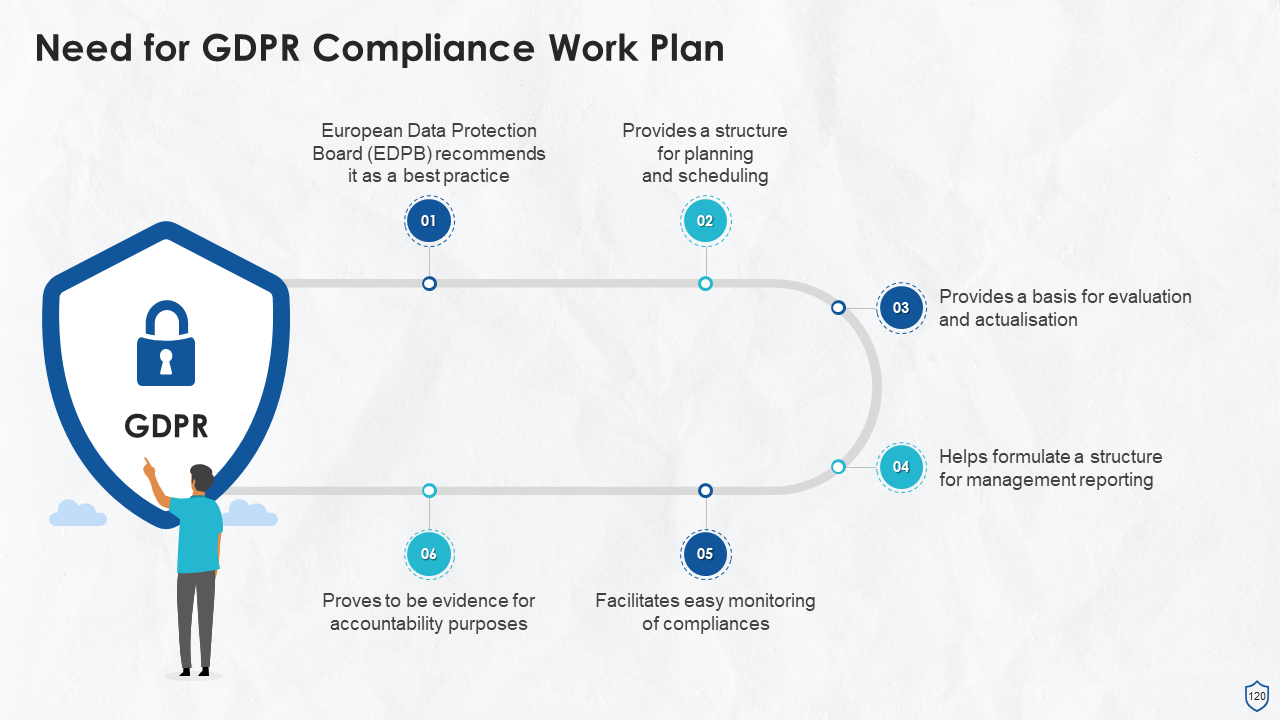
- Need for GDPR Compliance Work Plan
- Basic Outline of a GDPR Compliance Work Plan
- Auditing and Monitoring in GDPR:
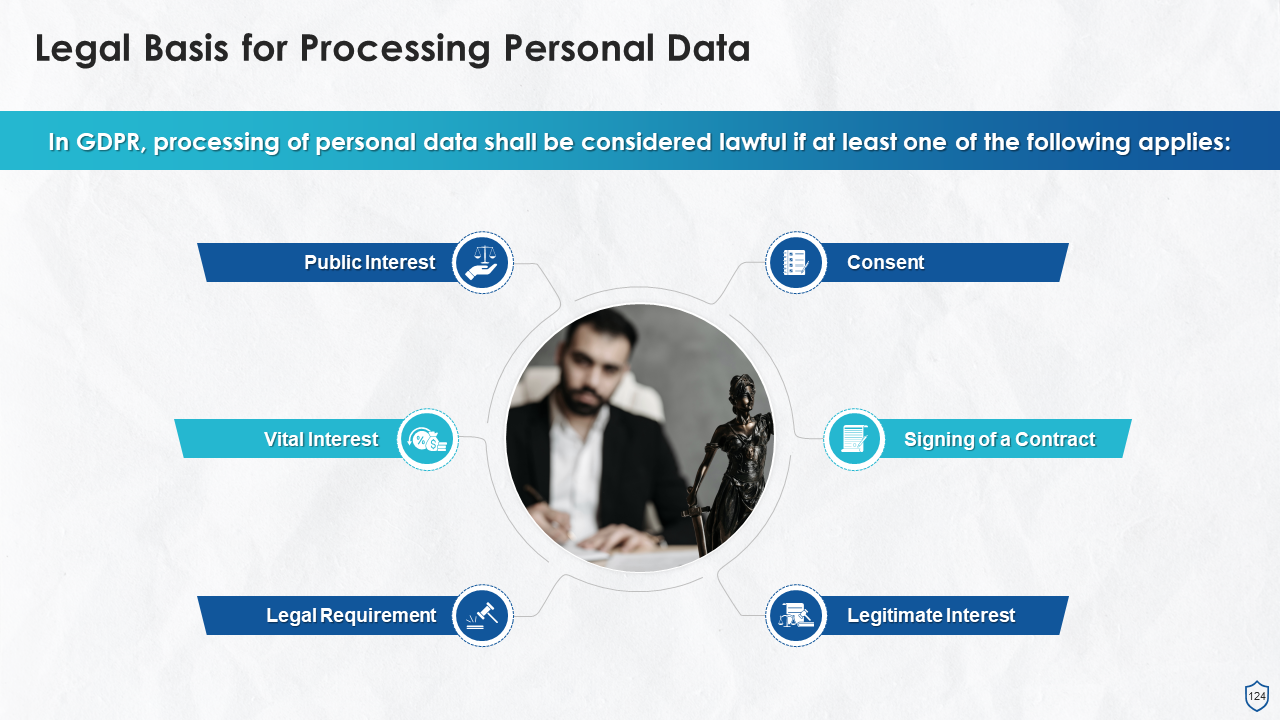
- Legal Basis for Processing Personal Data
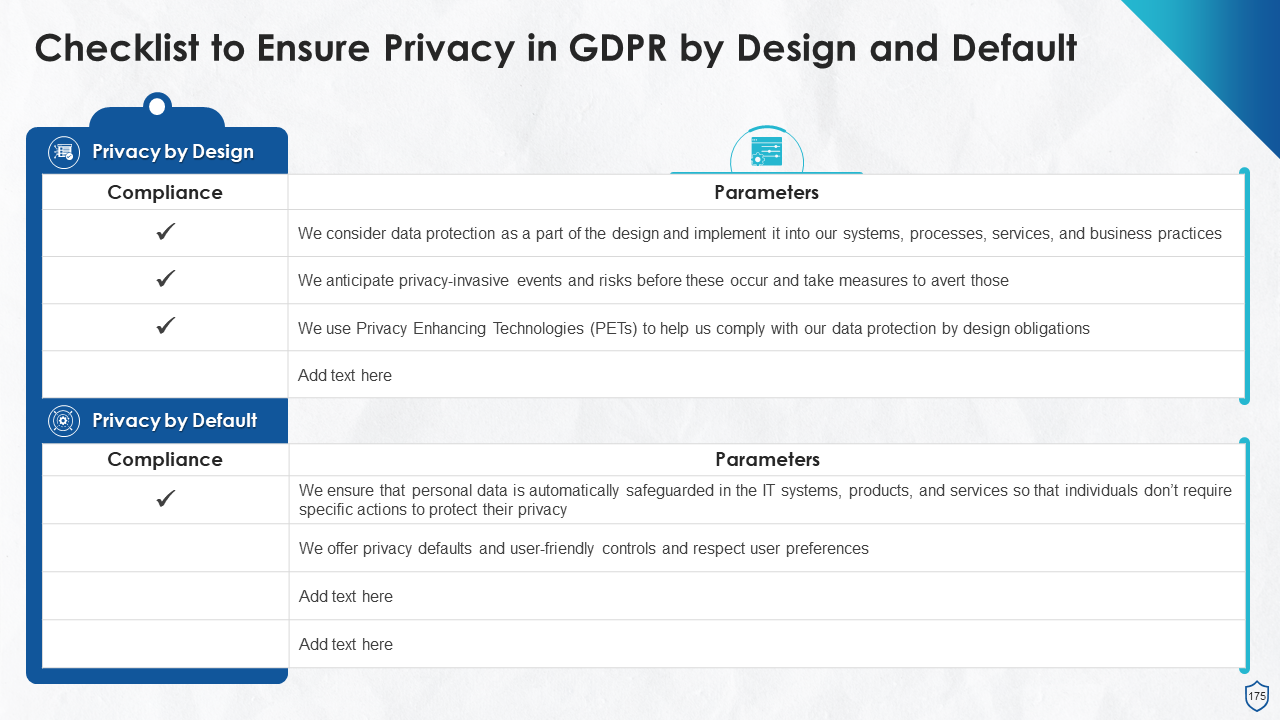
- Data Protection by:
- Design
- Default
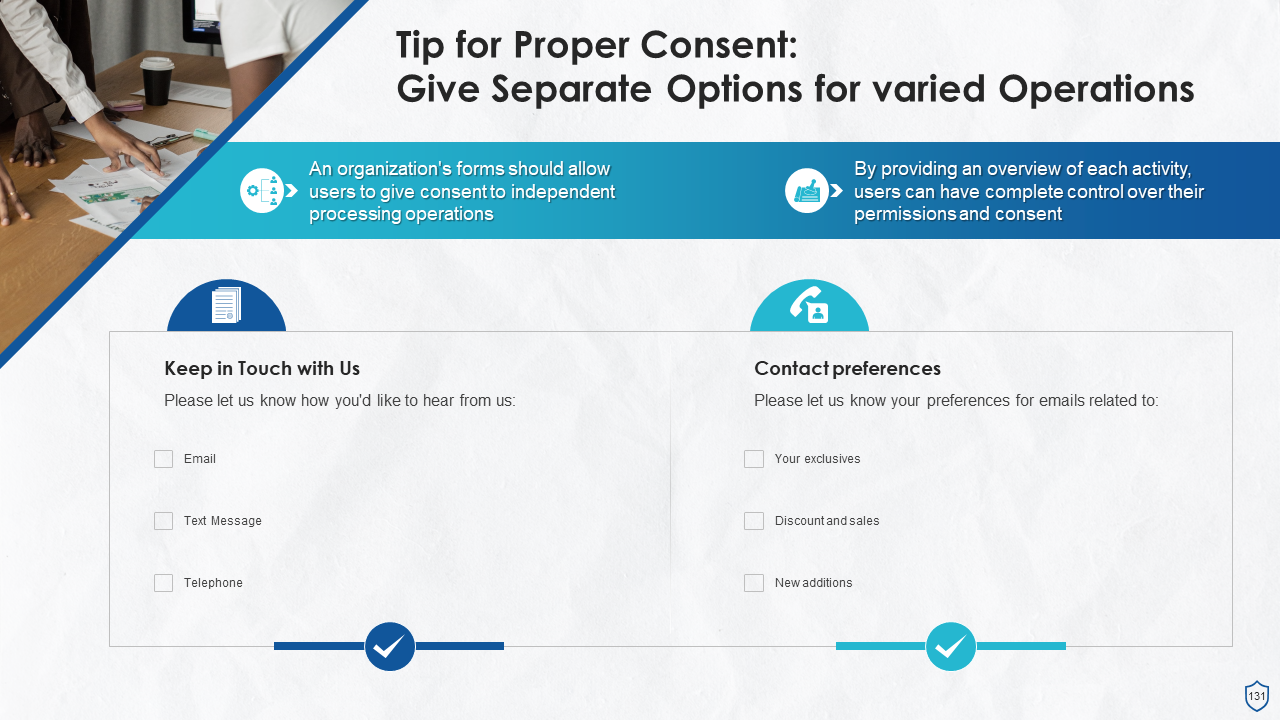
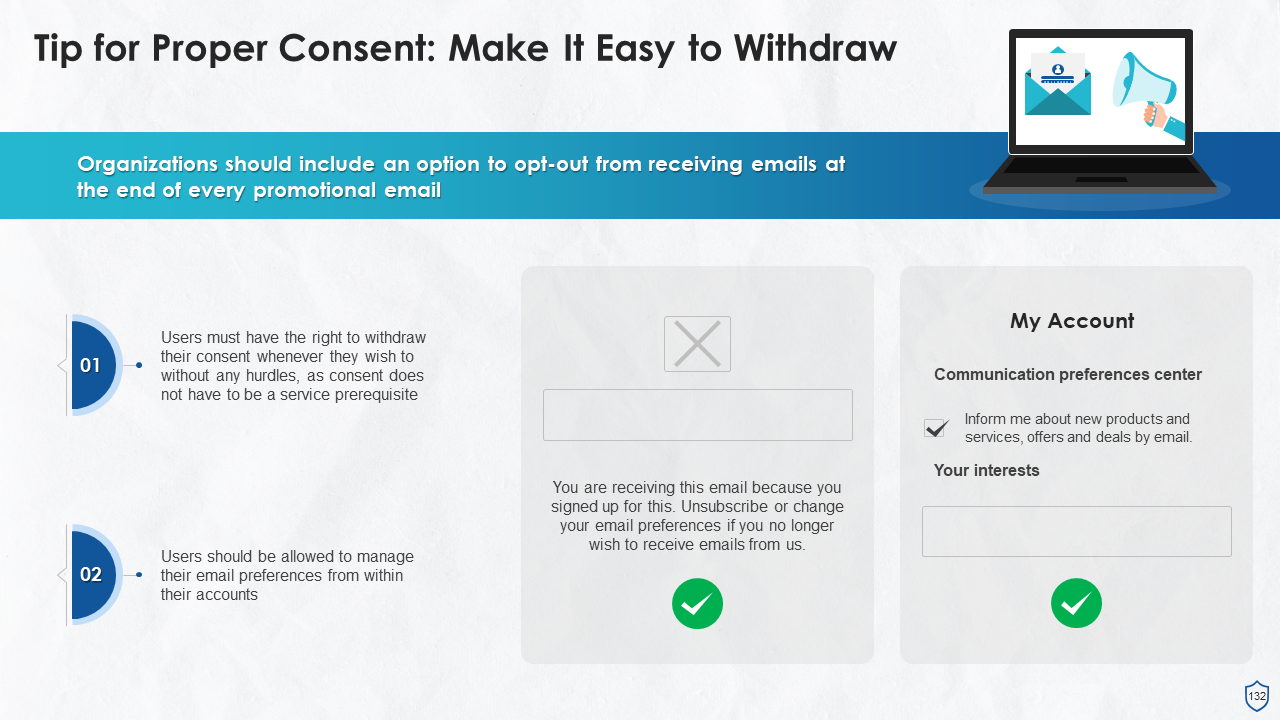
- Privacy Notice and Consent
- Data Protection Impact Assessment (DPIA)
- Benefits of Conducting a DPIA
- Activities Necessitating DPIA under GDPR
- Activities Not Necessitating DPIA under GDPR
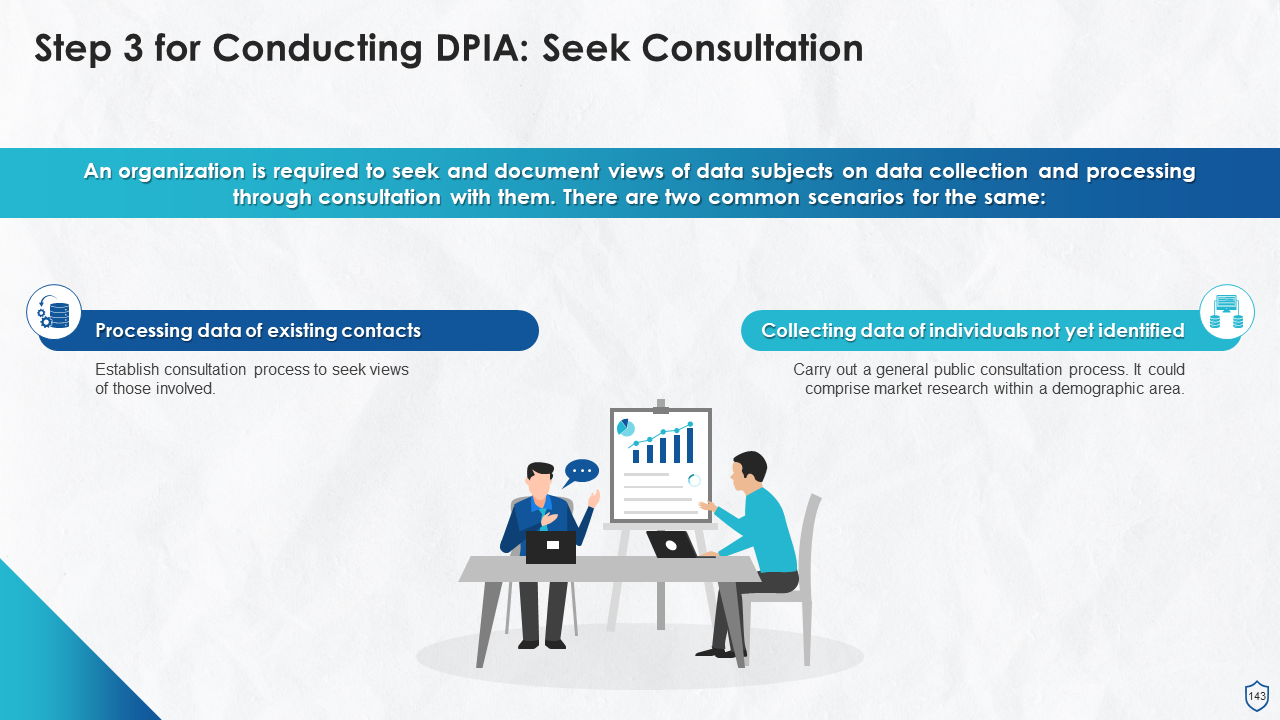
- Who Should be Involved in Conducting DPIA?
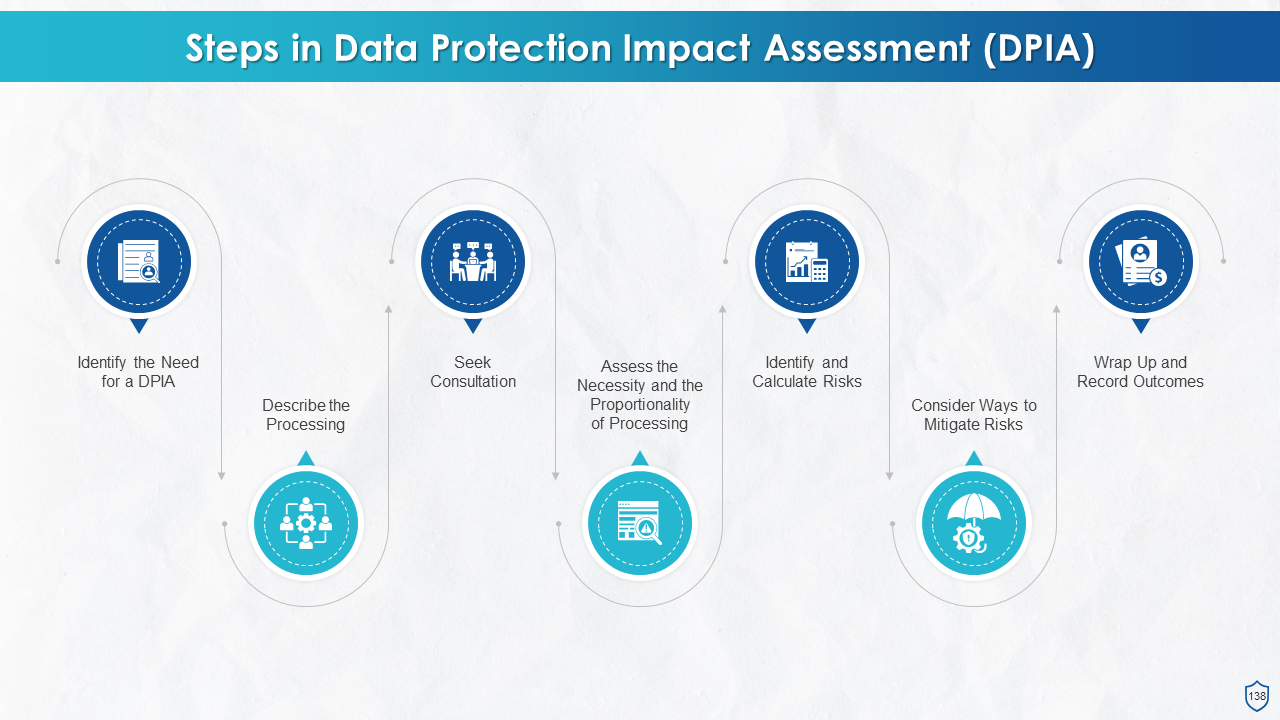
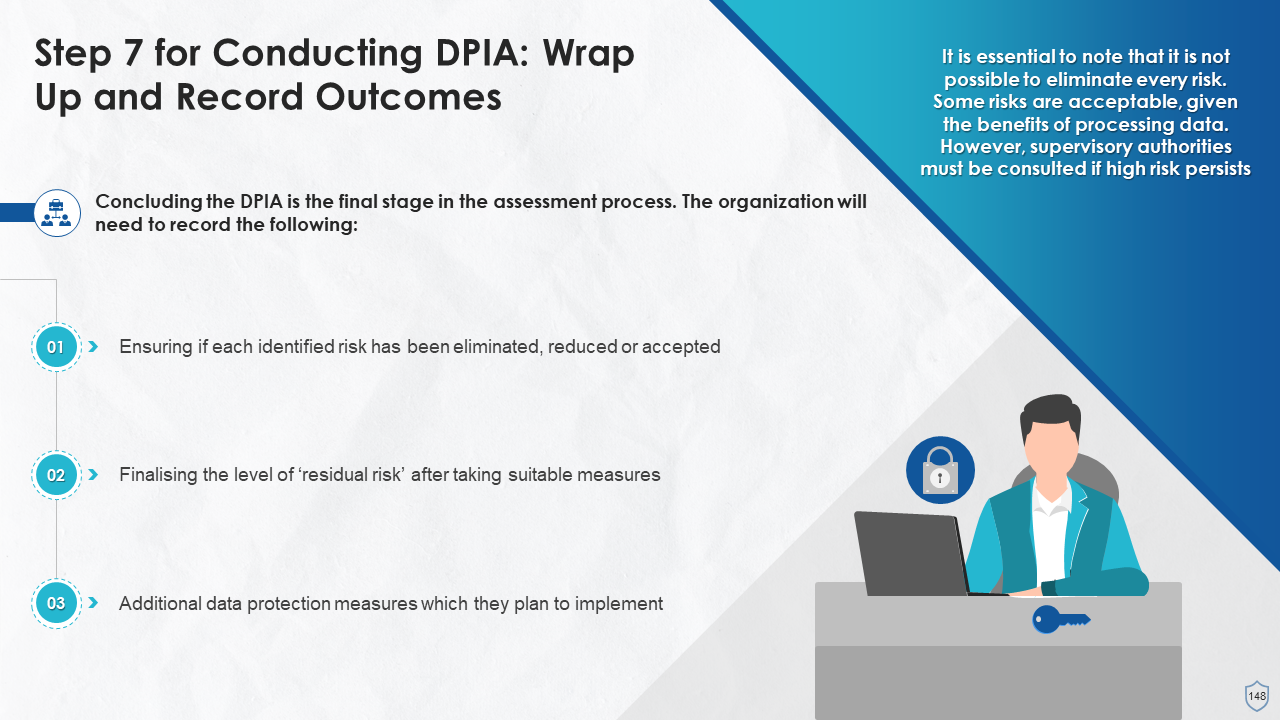
- Steps in DPIA
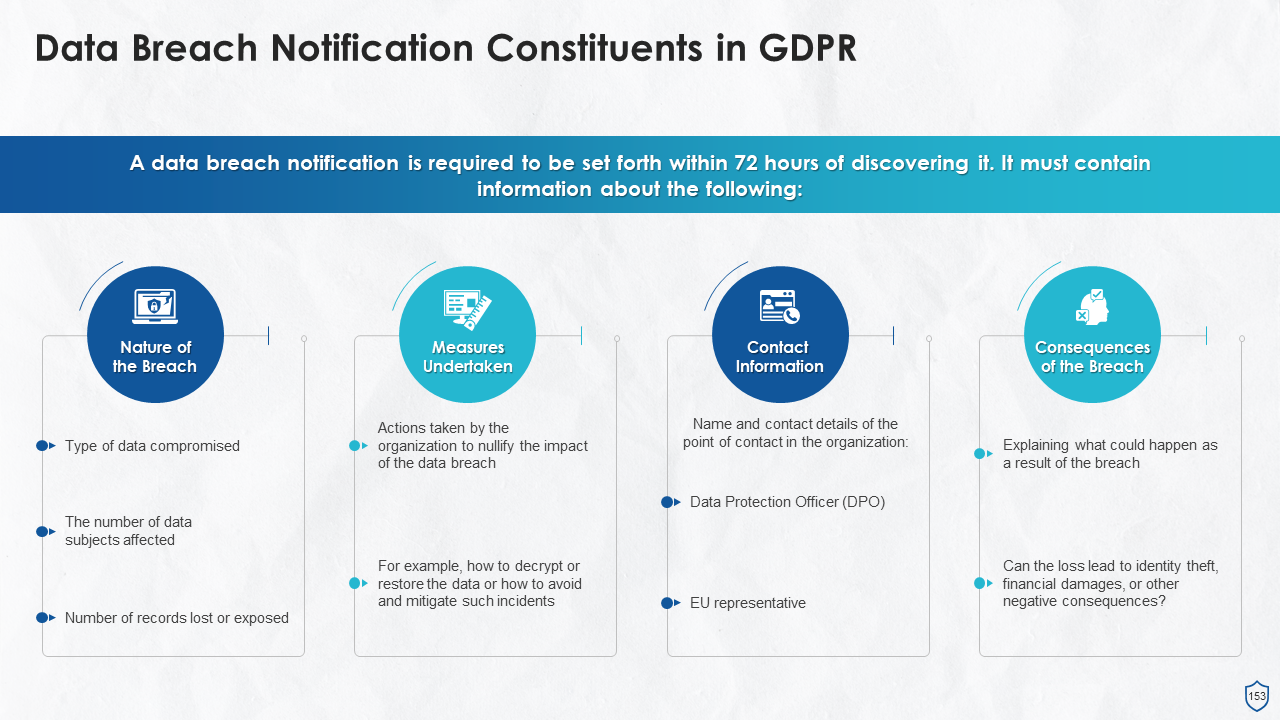
- Data Breach Notification under GDPR
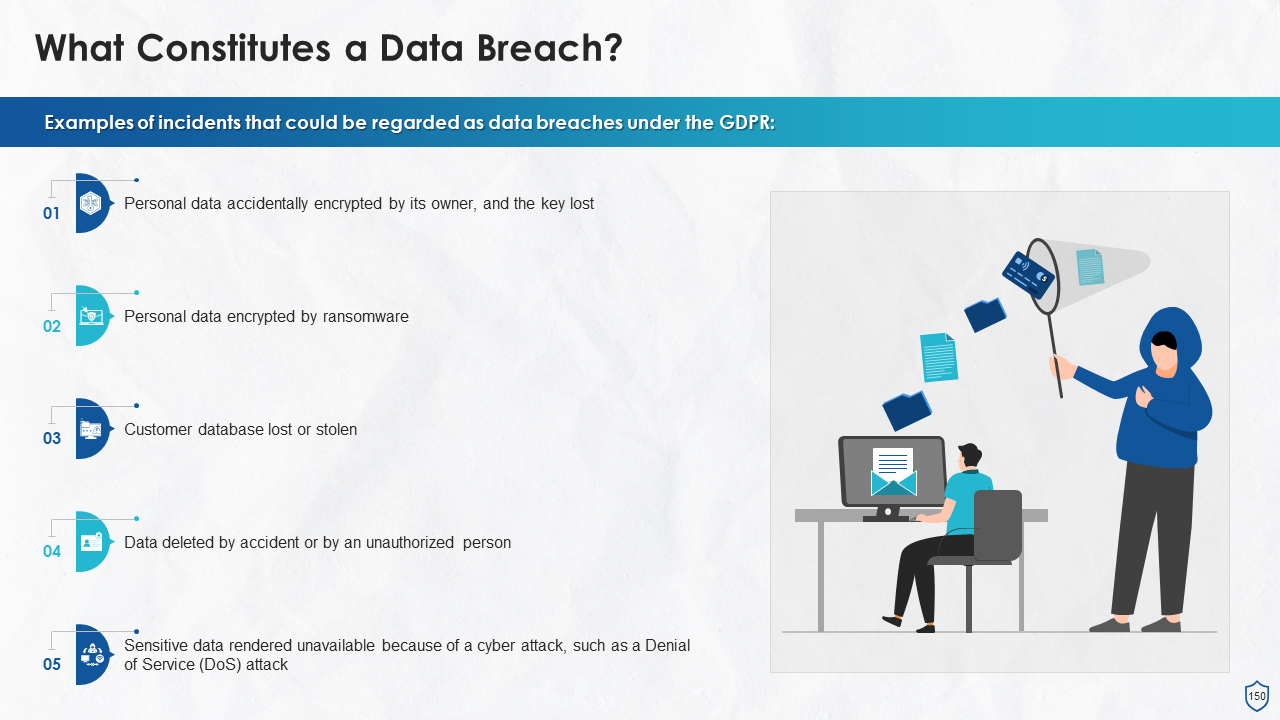
- What Constitutes a Data Breach?
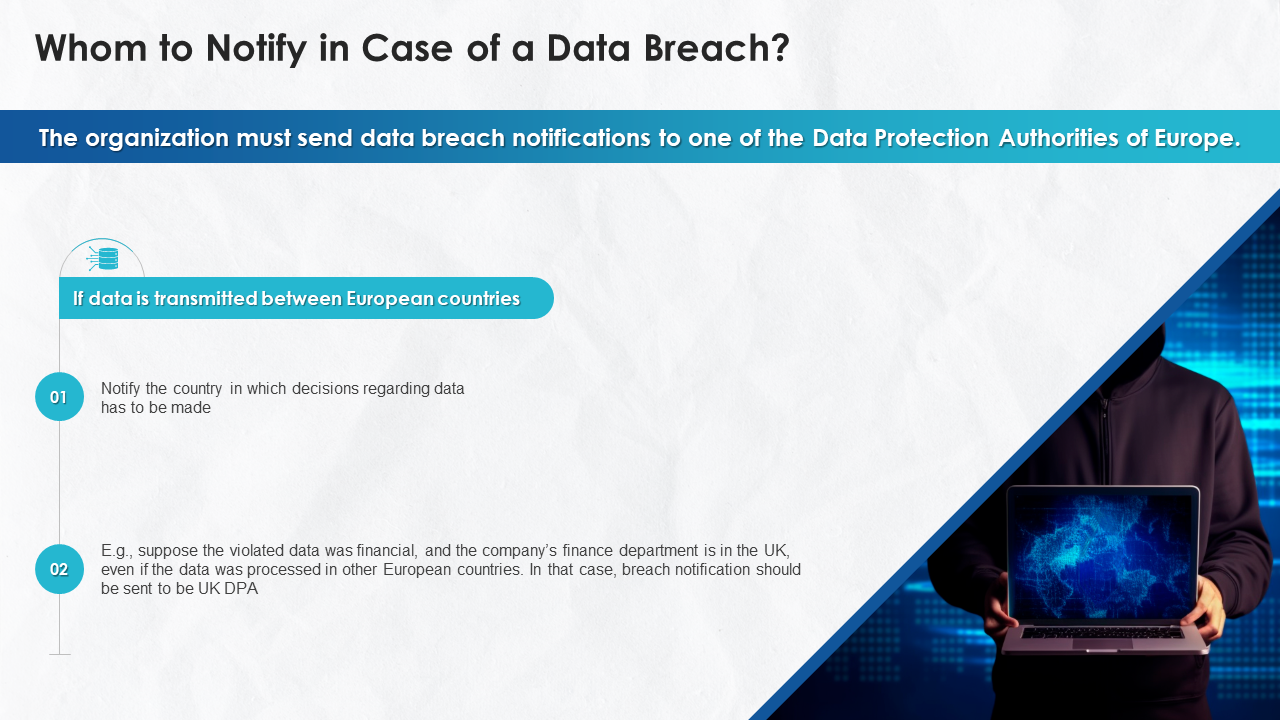
- Whom to Notify in Case of a Data Breach?
- Data Breach Notification Constituents in GDPR
- Data Breach Notification Template
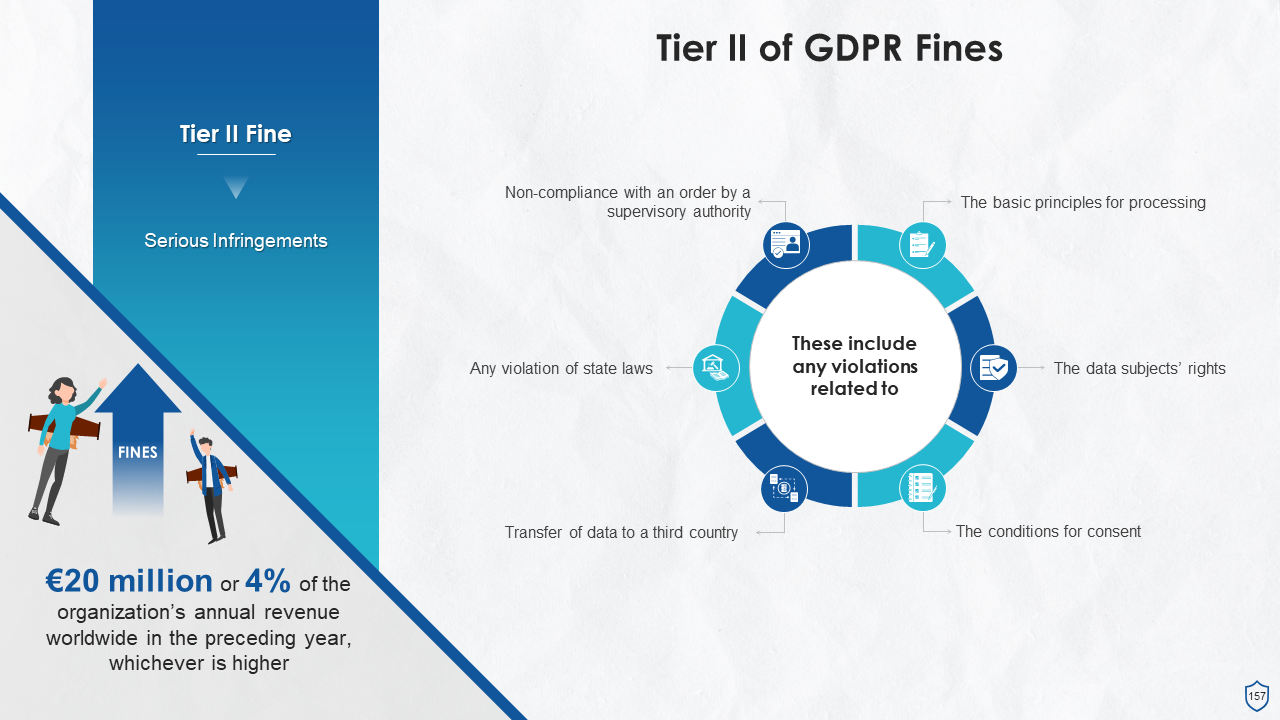
- Fines
- Factors Determining Fines Under GDPR
- Tier I of GDPR Fines
- Tier II of GDPR Fines
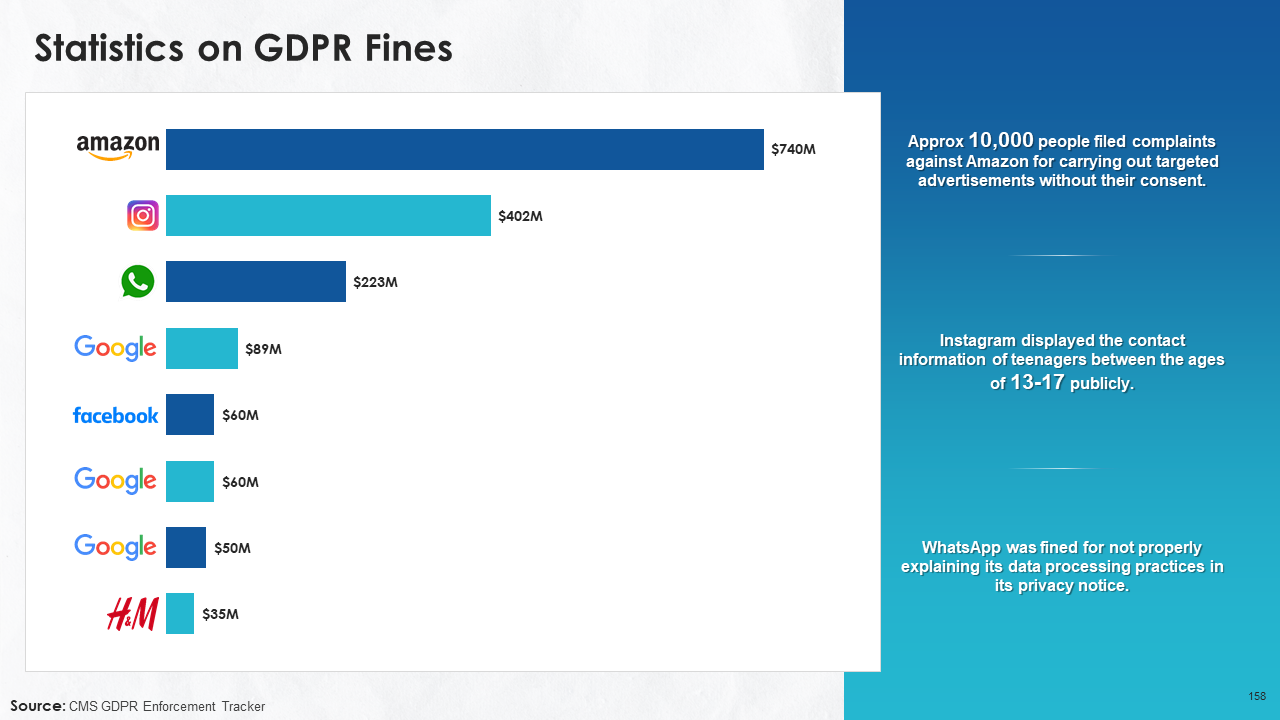
- Statistics on GDPR Fines
- Key Takeaways
- Let’s Discuss
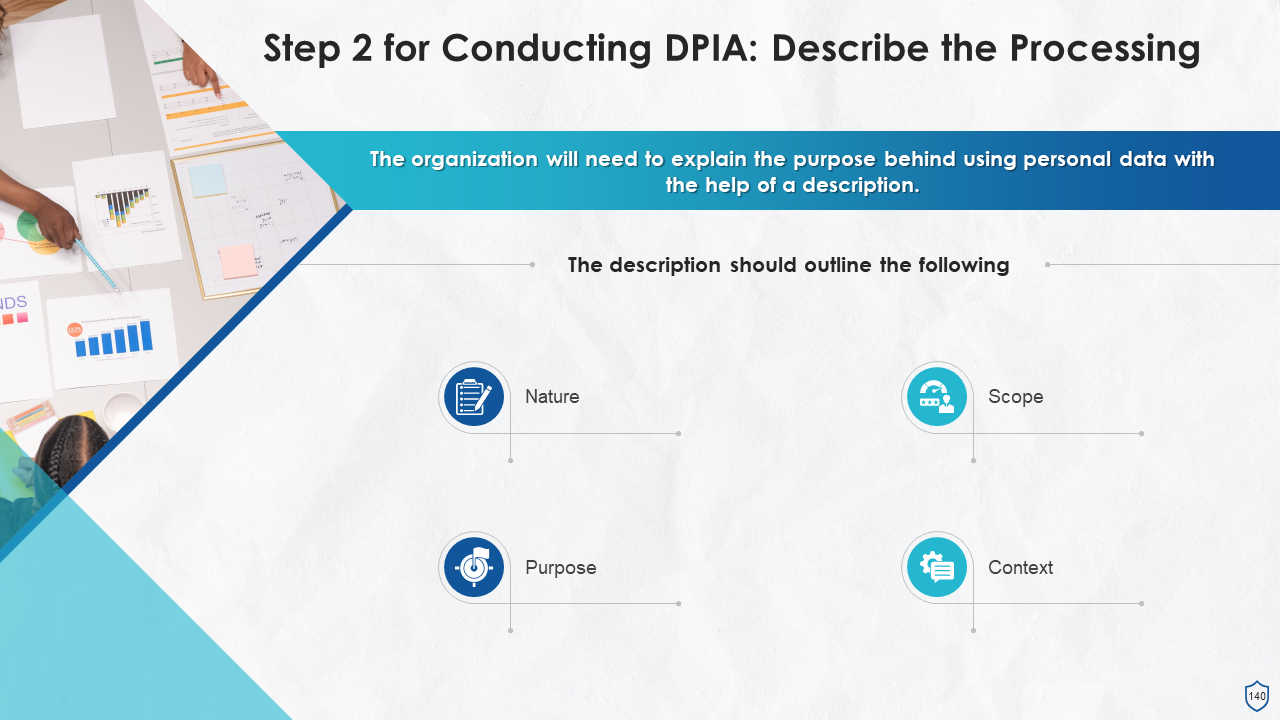
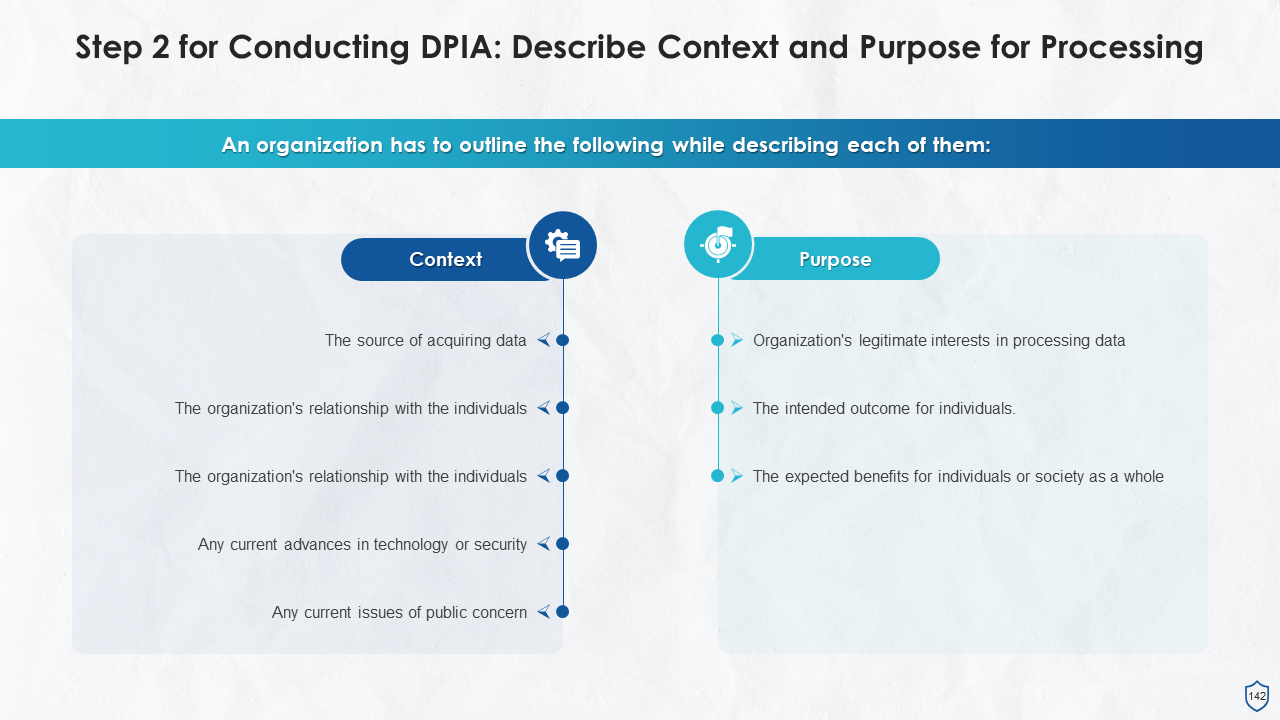
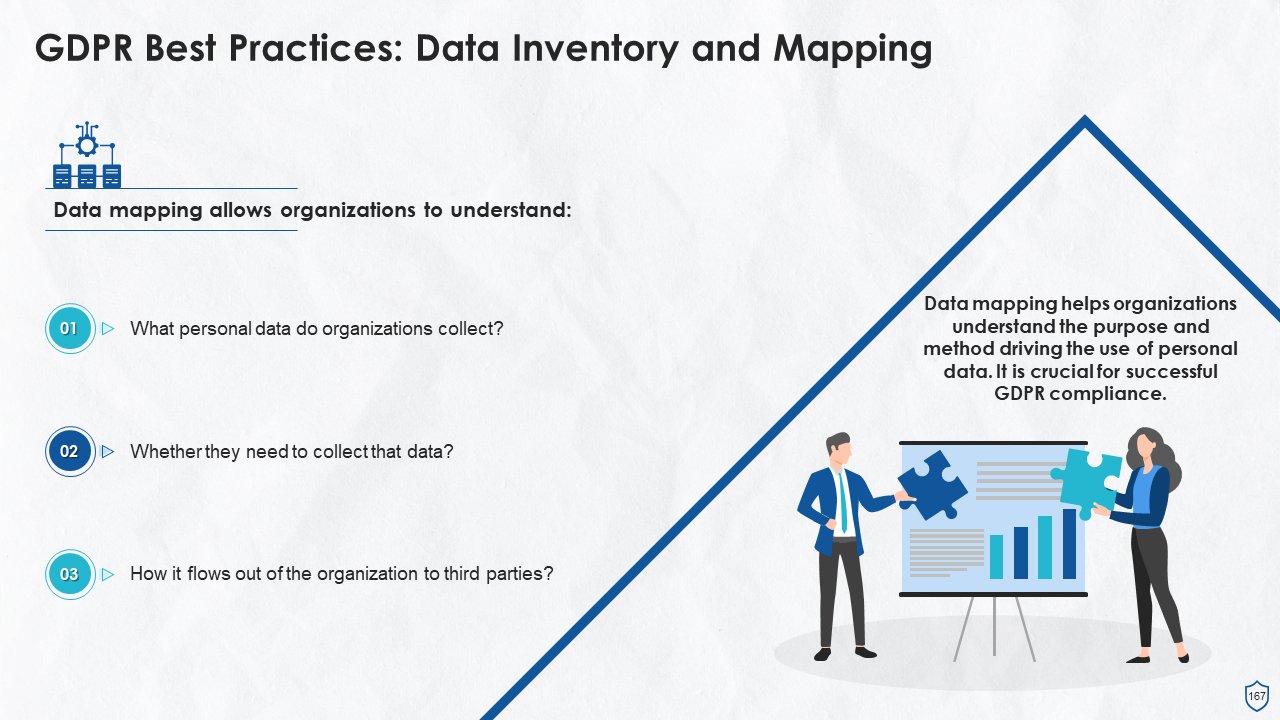
- Data Inventory and Mapping
- Data Protection Impact Assessment
- Checklist
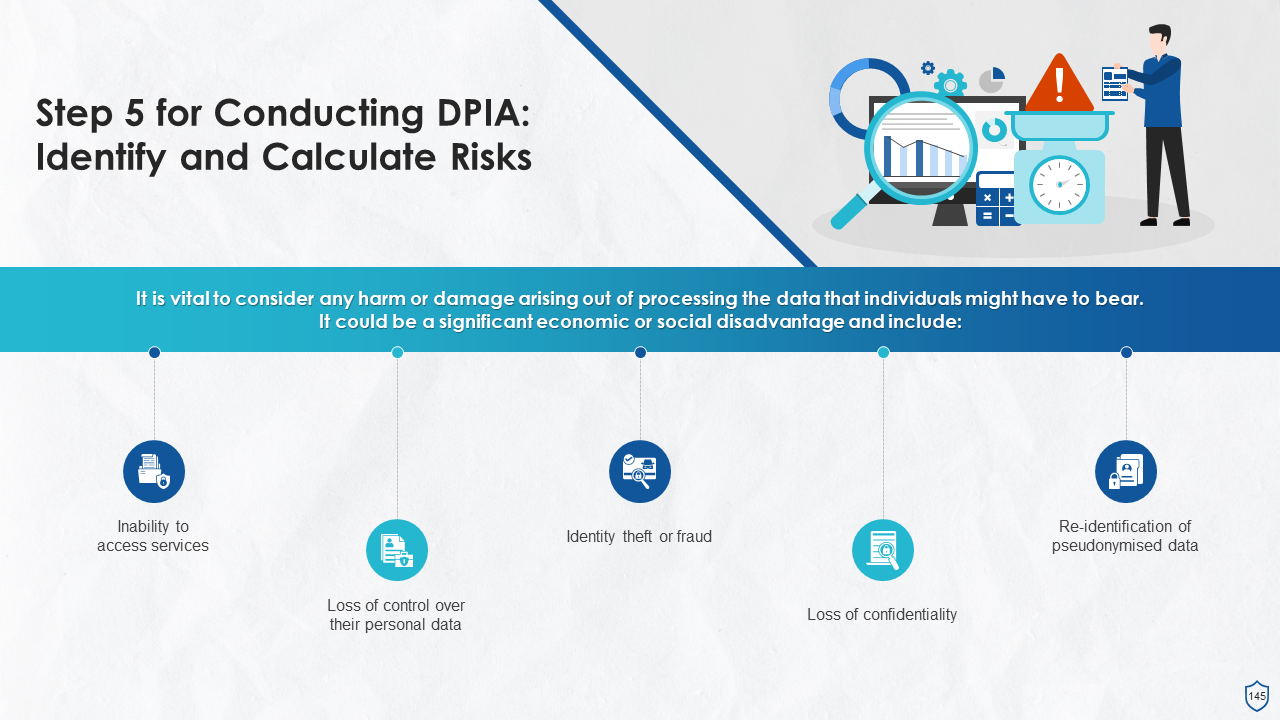
- Risk Assessment under DPIA
- Privacy by Design and Default
- Consent Management
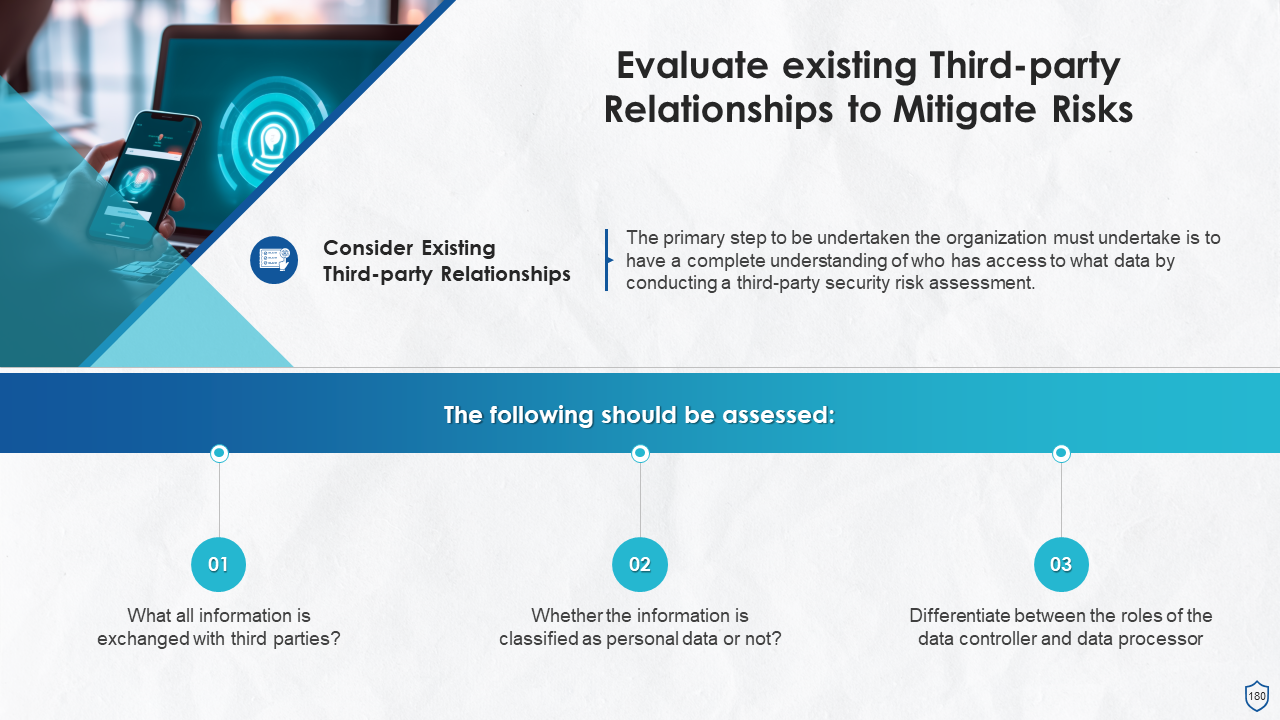
- Third-Party Risk Management
- Types of Third-Party Risks
- Cybersecurity Risk
- Operational Risk
- Reputational Risk
- Financial Risk
- Regulatory and Compliance Risk
- How to Mitigate Third-Party Risks?
- Third-Party Risk Mitigation Checklist
- Key Takeaways
- Let’s Discuss
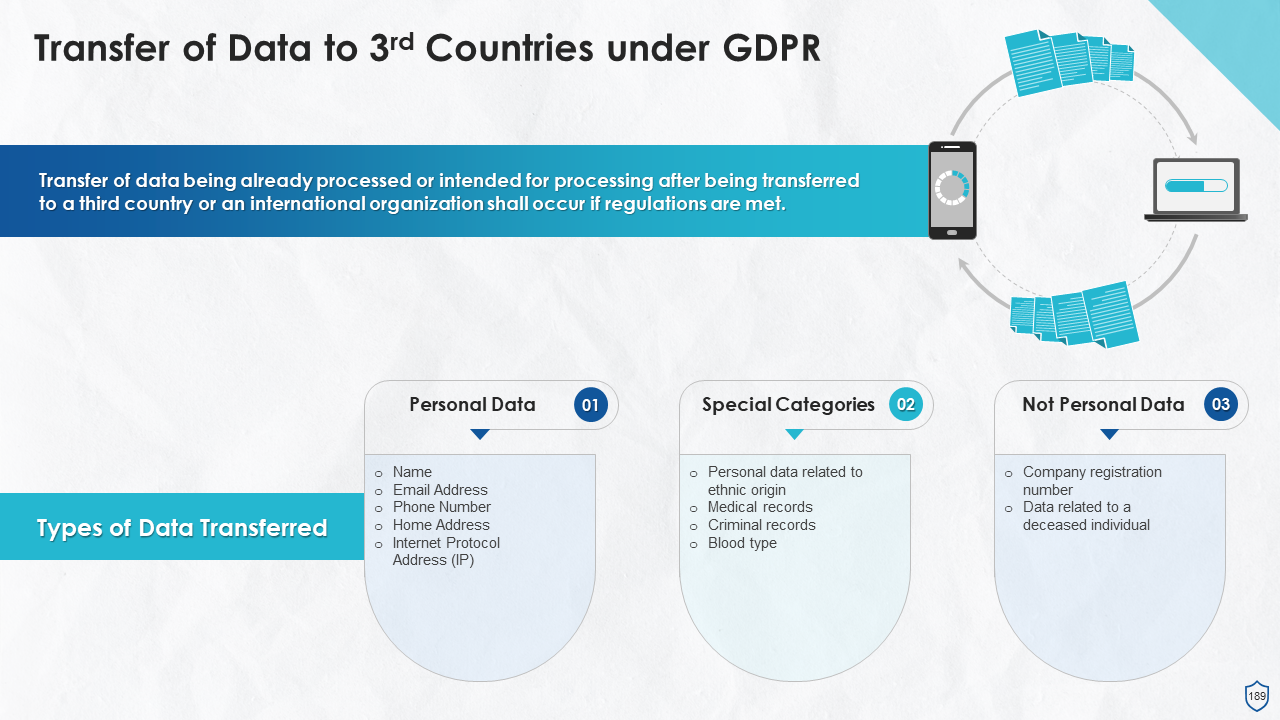
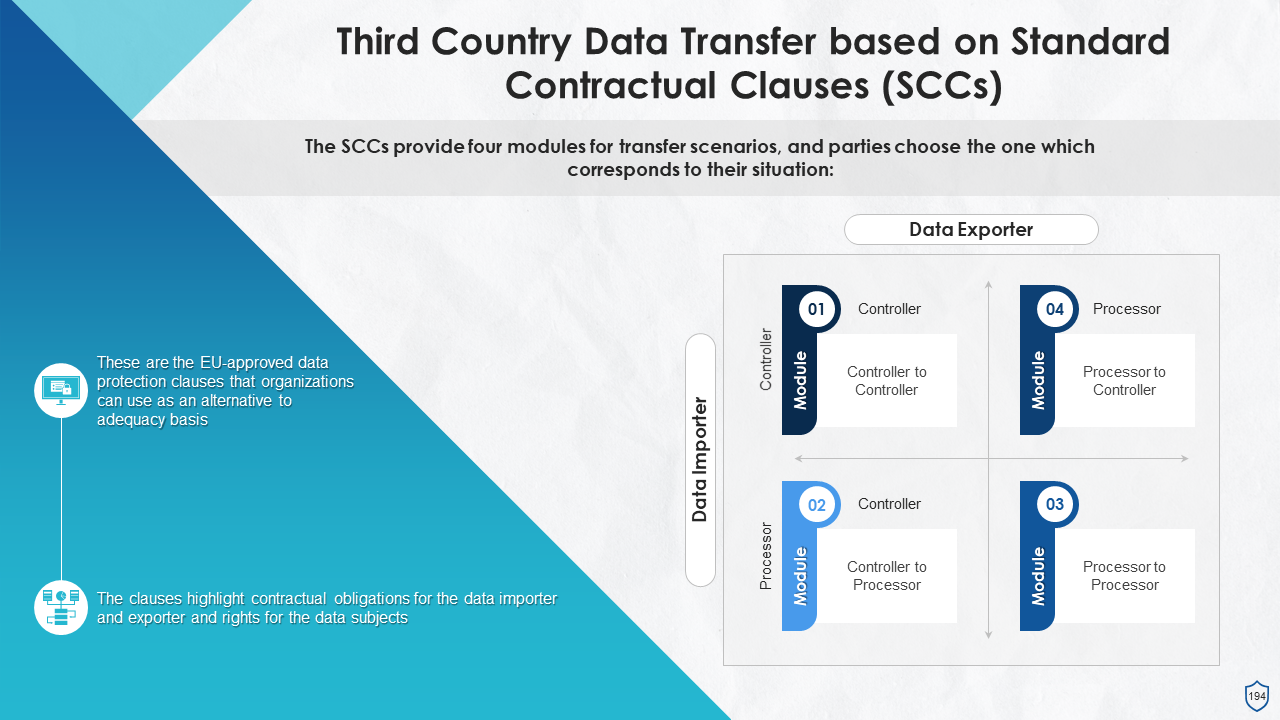
- General Principles for Third Country Data Transfer
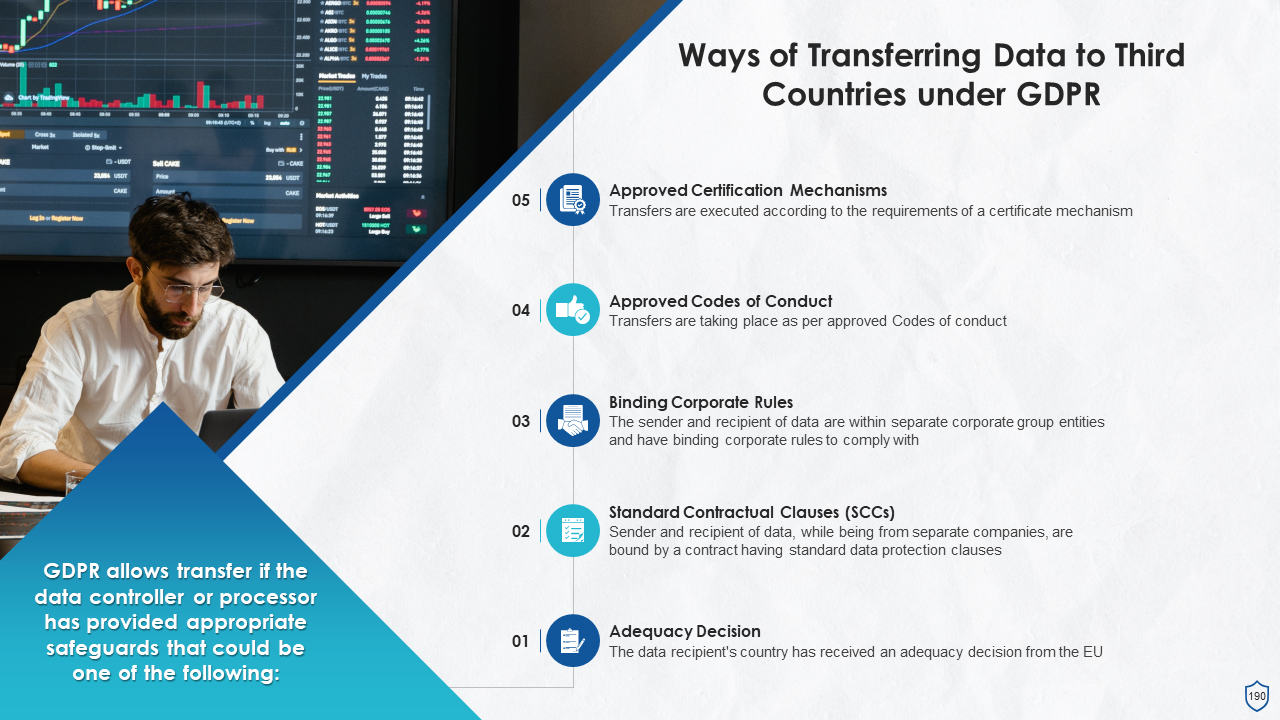
- Ways of Transferring Data to Third Countries under GDPR
- Flowchart Depicting Scenarios for Third Country Data Transfer under GDPR
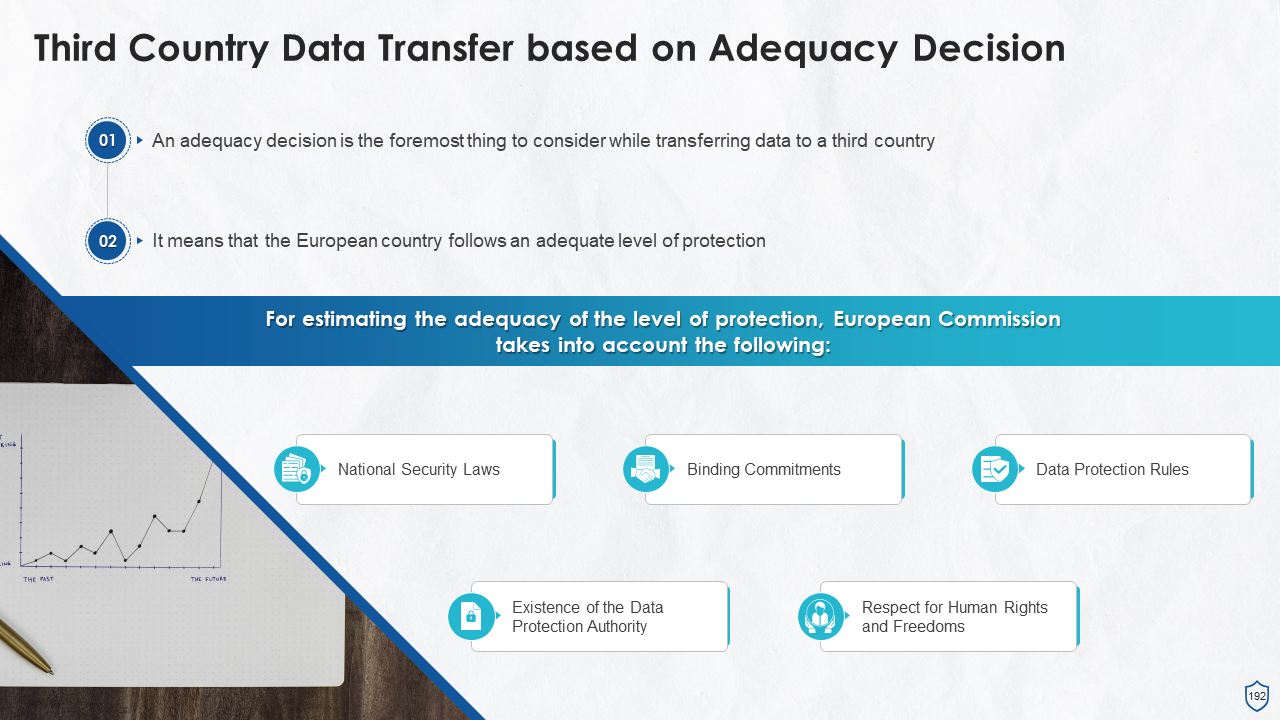
- Third Country Transfer Based on Adequacy Decision
- Data Transfers Subject to Appropriate Safeguards
- Derogations for Specific Situations
- Key Takeaways
- Let’s Discuss
- Emerging Technology Trends in GDPR
- Ensuring GDPR Compliance using AI
- Artificial Intelligence Use Cases in GDPR
- Ensuring GDPR Compliance using Blockchain
- Internet of Things (IoT) Use Cases in GDPR
- Future Changes in GDPR
- A Cookie-less Future!
- Global Acceptance as a Data Privacy Regulation
- Test for Anonymization
- Greater Fines for GDPR Violation
- Key Takeaways
- Let’s Discuss
- What is CCPA (California Consumer Privacy Act)?
- CCPA - Applicability
- CCPA - Scope
- CCPA - Timeline
- Does the CCPA Apply to your Business?
- Categories of Personal Information under CCPA
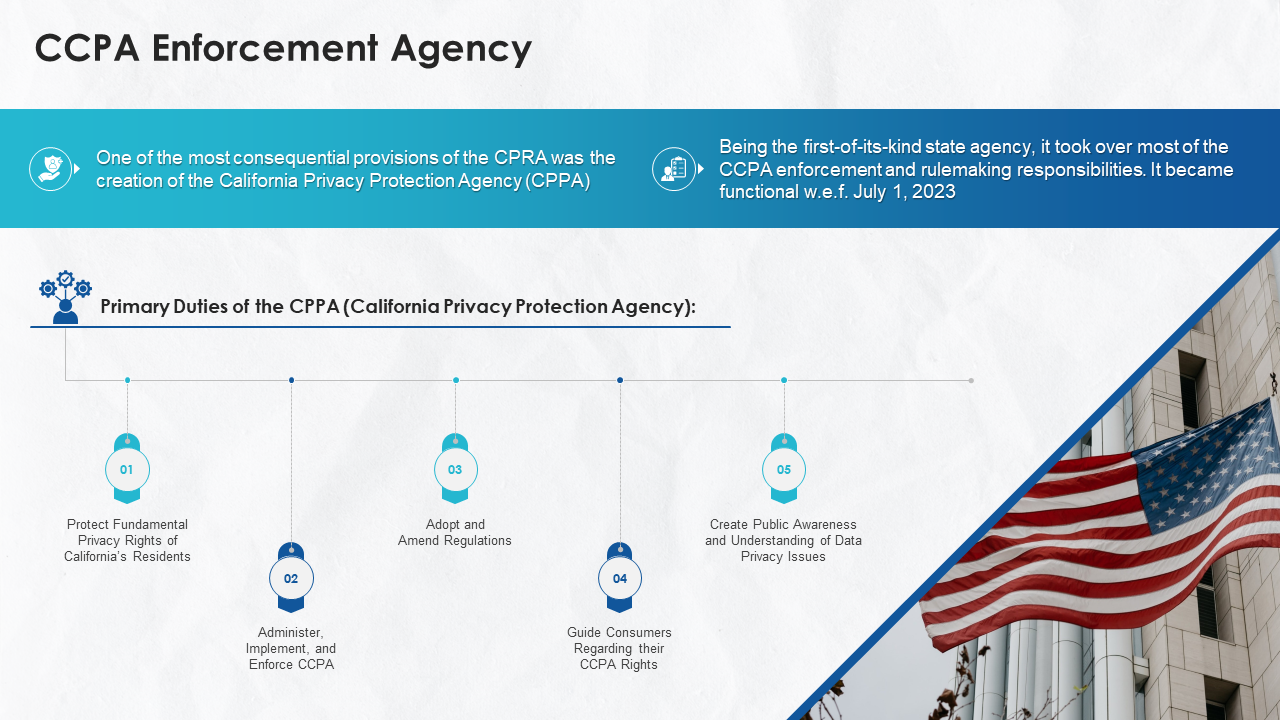
- What is California Privacy Rights Act (CPRA)?
- CPRA or CCPA 2.0
- Key Takeaways
- Let’s Discuss
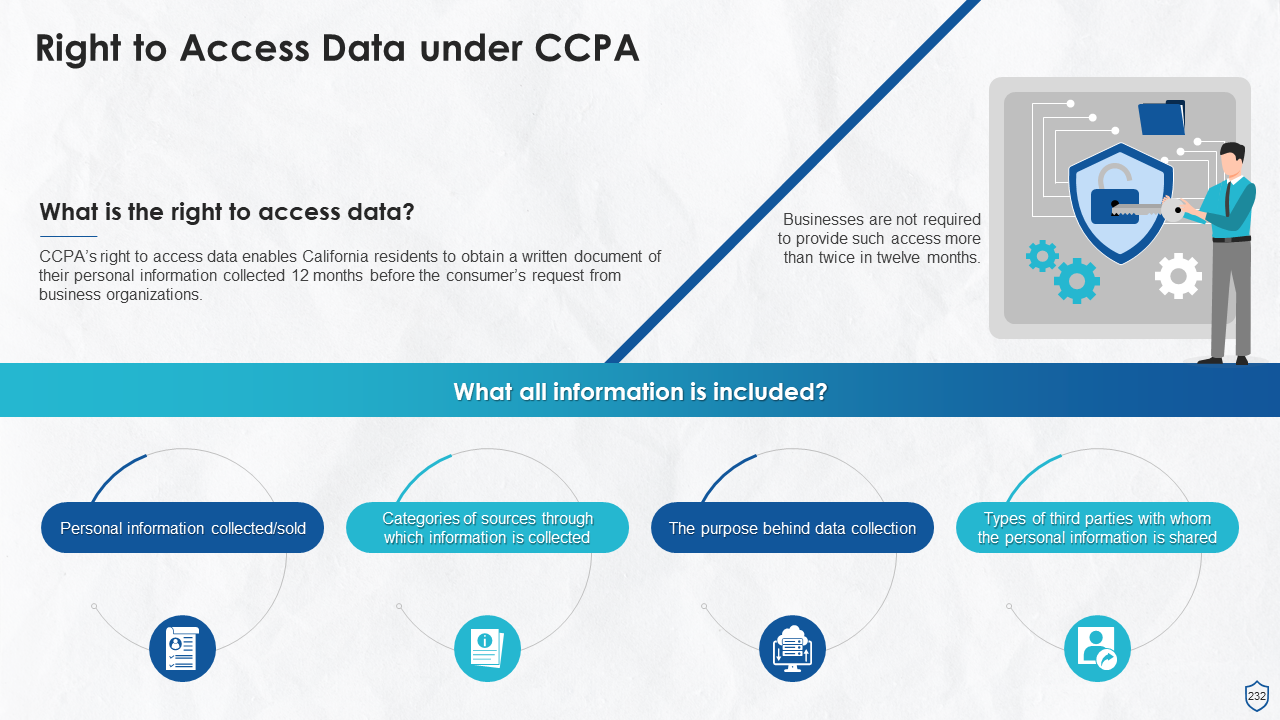
- Right to Access Data
- Right to Deletion
- Right to Opt-out from having Information Sold
- Right to Opt-in to having Information Sold (Minors)
- Right to Receive Services on Equal Terms
- New Rights under California Consumer Privacy Act
- Key Takeaways
- Let’s Discuss
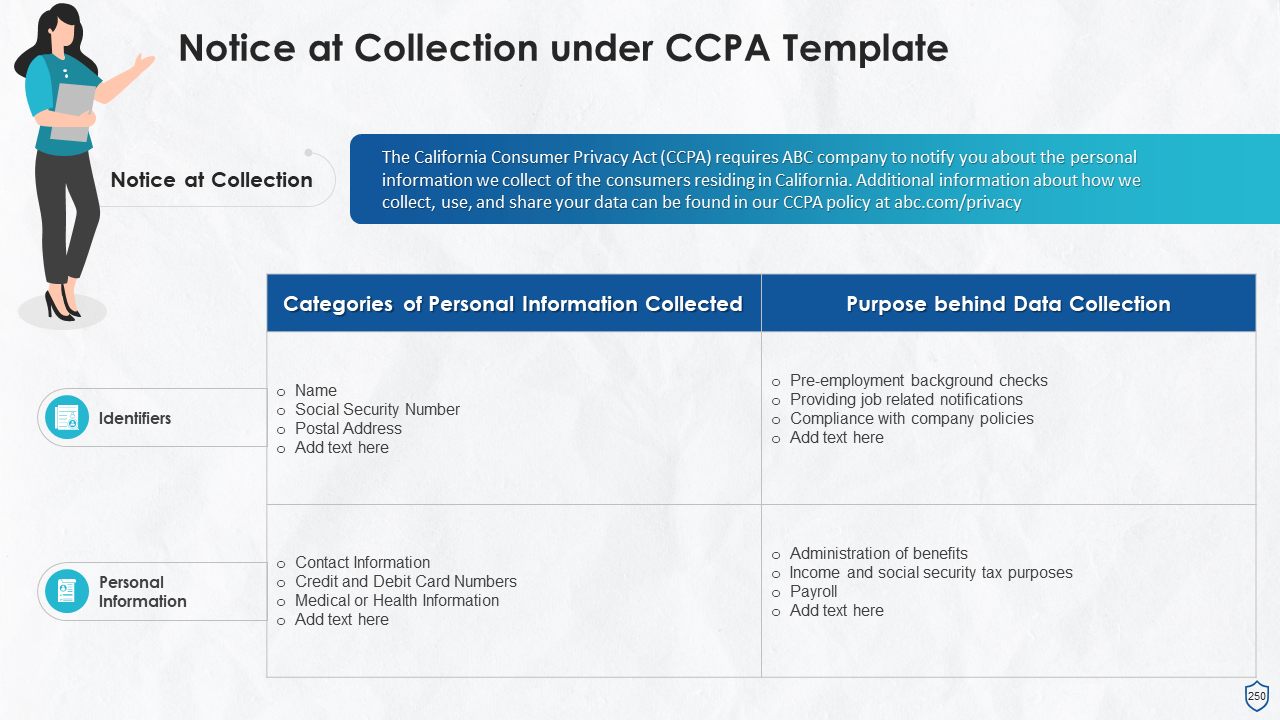
- Notice at the Time of Data Collection under CCPA
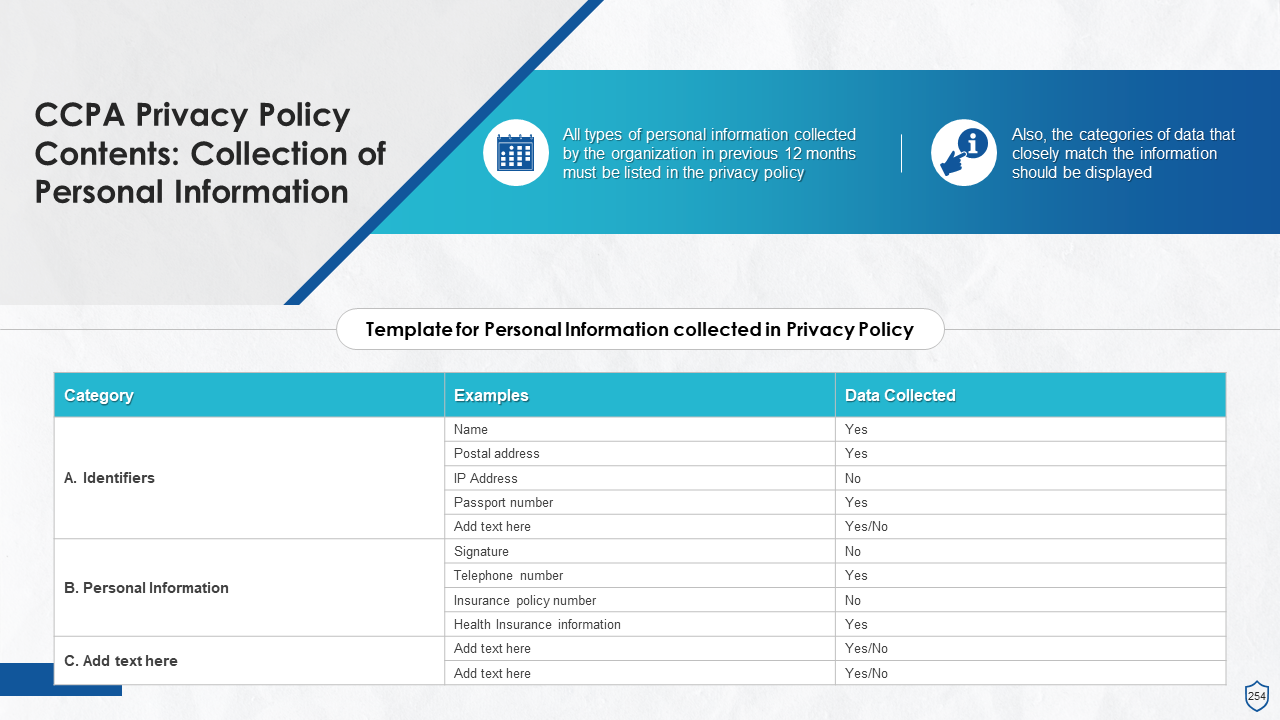
- Privacy Policy under CCPA
- Must Haves for an Appropriate Privacy Policy
- What is Included in a CCPA?
- CCPA Privacy Policy Checklist
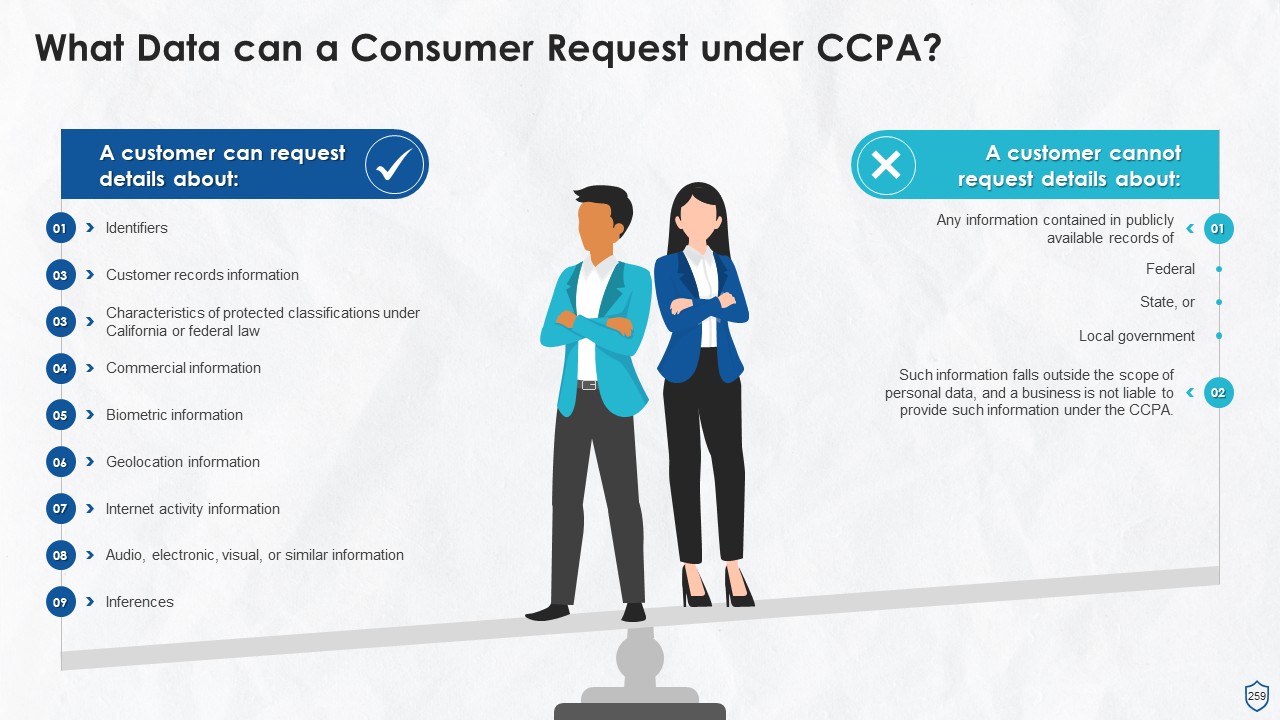
- What Data a Consumer can and cannot Request under CCPA
- Mechanisms by which Consumers can Submit Requests:
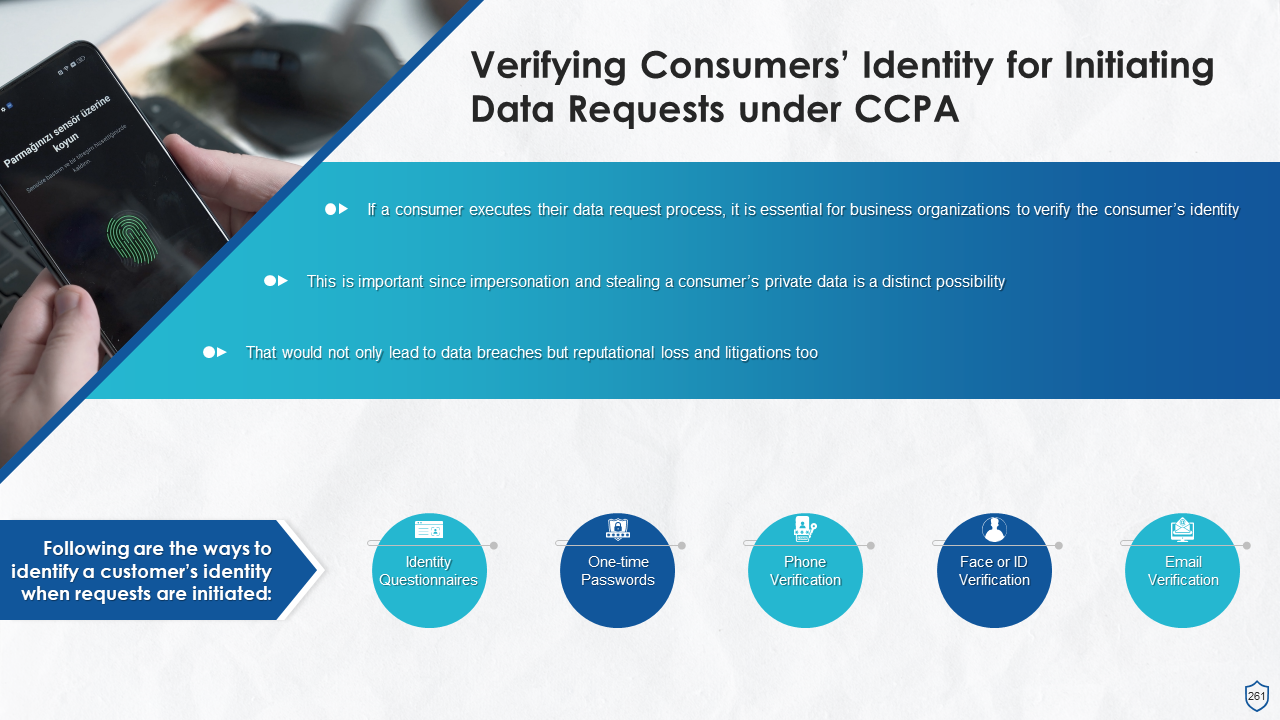
- Verifying Consumers’ Identity for Initiating Data Requests:
- Timelines for Responding to Consumer Requests
- Mechanism for Responding to Consumers’ Opt-Out Requests
- Authorized Agent Requests under CCPA
- Checklist for Validating Data Subject Requests that Authorized Agents
- Key Takeaways
- Let’s Discuss
- Steps Towards CCPA Compliance
- Know Business Obligation towards CCPA
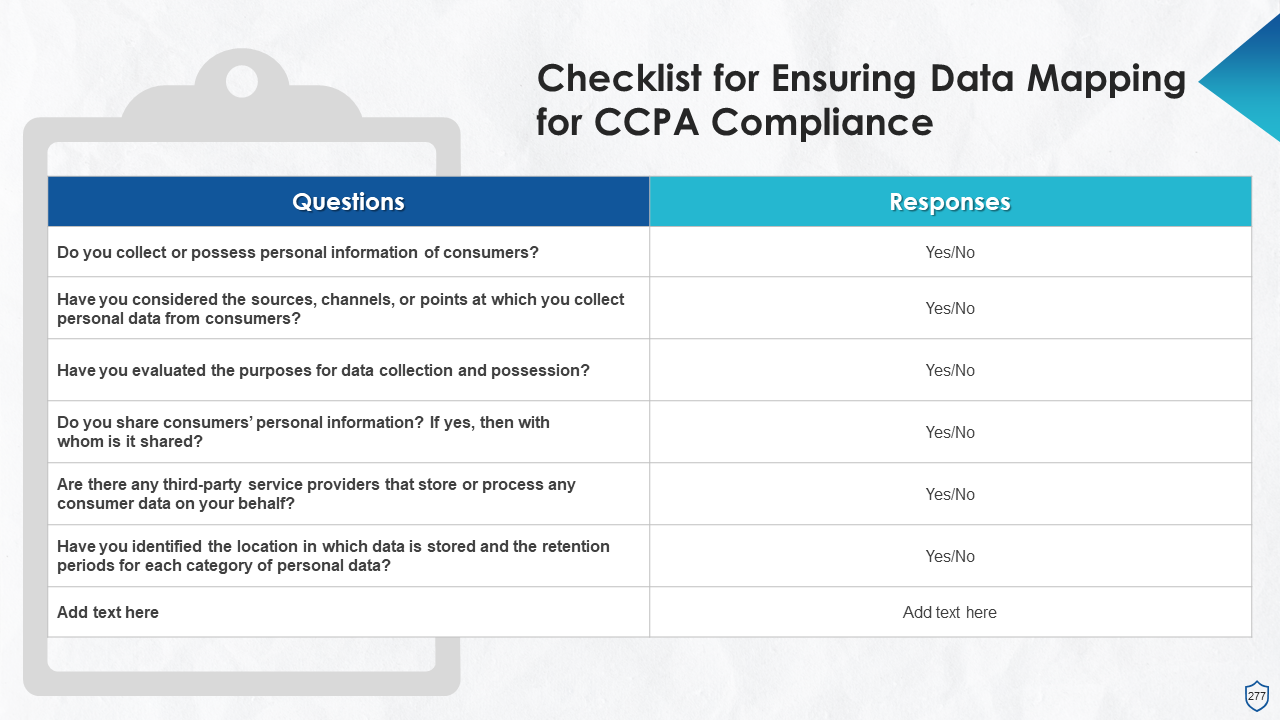
- Map Data Flow
- Update Privacy Disclosures
- Create a Link to Privacy Policy on the Homepage
- Develop a Procedure for Handling Consumer Requests
- Train Employees
- Which Businesses are Exempt from CCPA?
- Non-Profit Organizations
- Government Agencies
- Insurance Companies, Agents, and Support Organizations
- Types of Data Outside the Purview of CCPA
- Key Takeaways
- Let’s Discuss
- Steps Towards CCPA Compliance
- Know Business Obligation towards CCPA
- Map Data Flow
- Update Privacy Disclosures
- Create a Link to Privacy Policy on the Homepage
- Develop a Procedure for Handling Consumer Requests
- Train Employees
- Which Businesses are Exempt from CCPA?
- Non-Profit Organizations
- Government Agencies
- Insurance Companies, Agents, and Support Organizations
- Types of Data Outside the Purview of CCPA
- Key Takeaways
- Let’s Discuss
- What Constitutes a Data Breach?
- Data Breach Situations under CCPA
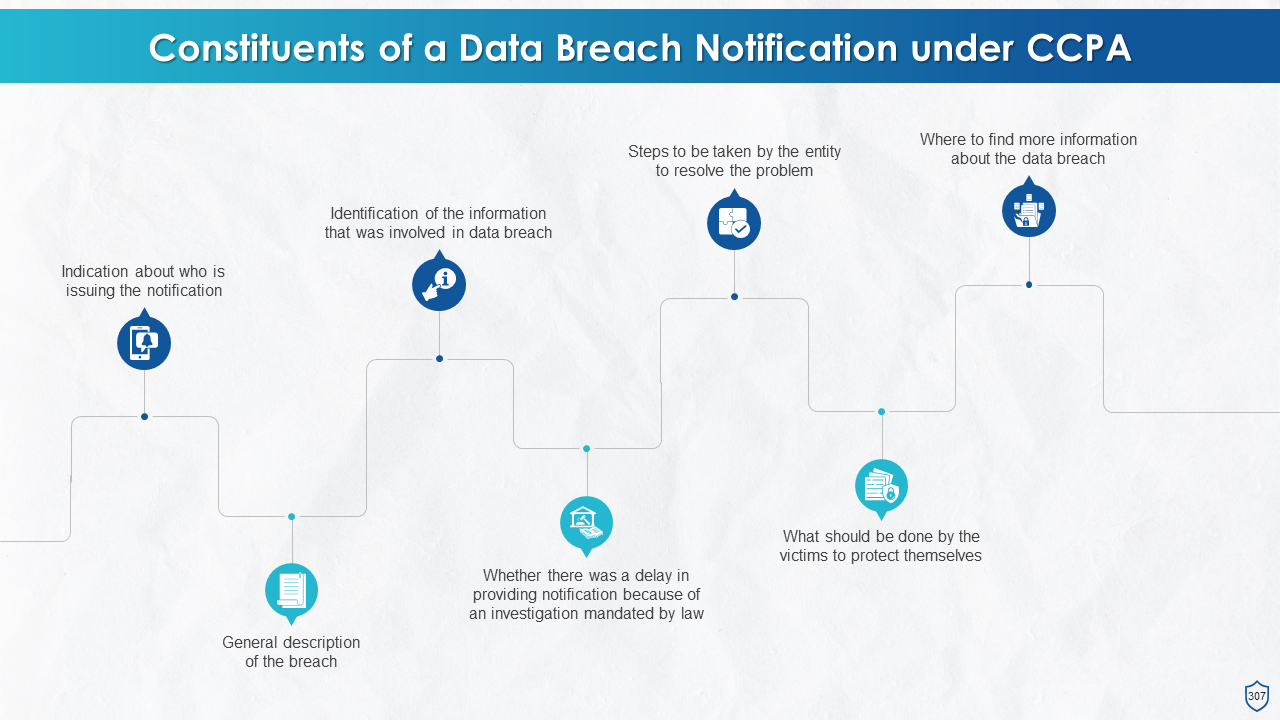
- Constituents of a Data Breach Notification under CCPA
- Data Breach Notification Template
- Data Breach Response Steps under CCPA
- Data Security Measures
- Data Subject Access Requests (DSARs) Flowchart under CCPA
- Steps for Processing DSARs
- Collect & Process DSARs
- Collect the Personal Information (PII) and Identify its Owner
- Review & Approve the Consumer PII Request Submission
- Document, Collaborate and Confirm
- Respond Quickly and Securely
- Consider DSAR Exemptions and Refusals
- DSAR Form under CCPA
- Key Takeaways
- Let’s Discuss
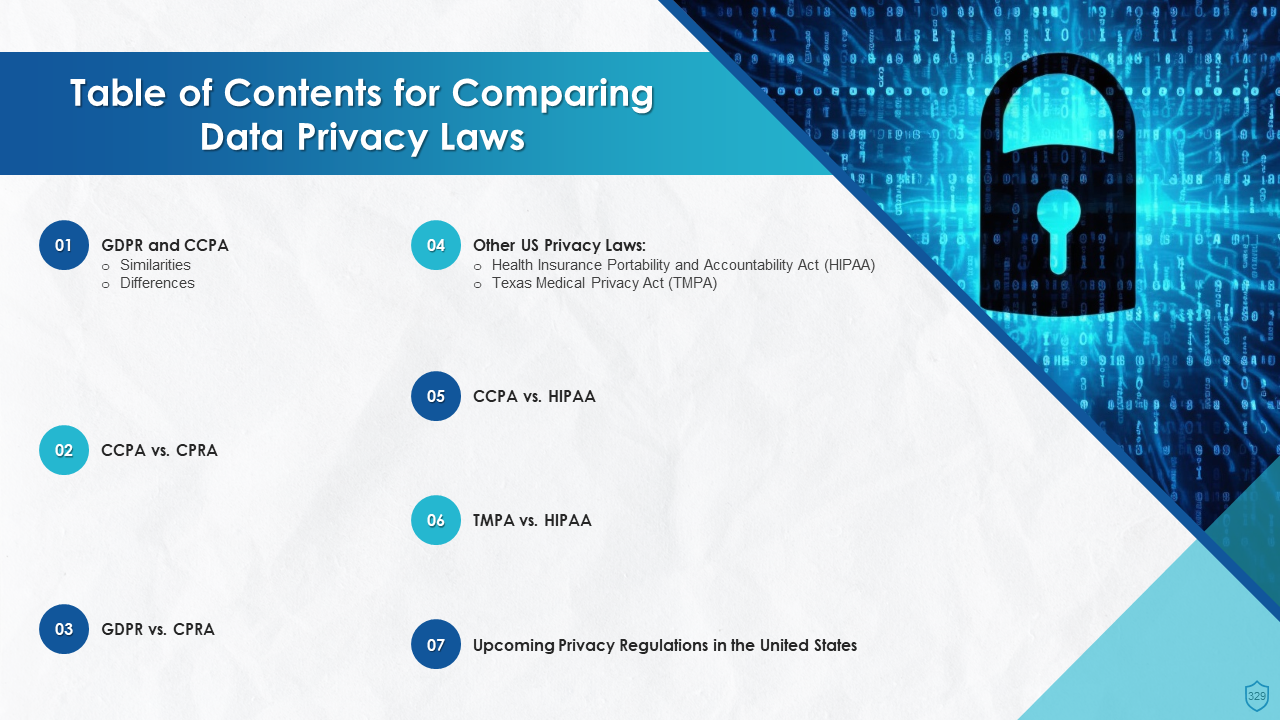
- GDPR vs. CCPA
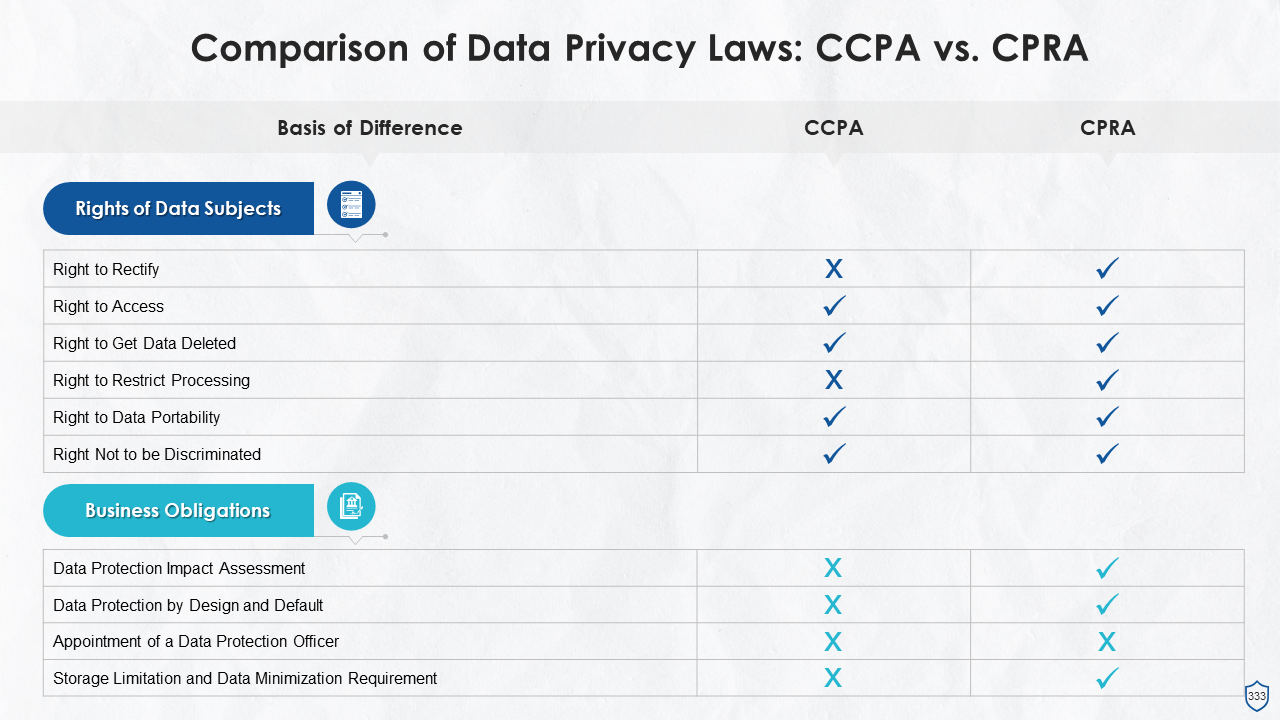
- CCPA vs. CPRA
- GDPR vs. CPRA
- Other US Privacy Laws:
- Health Insurance Portability and Accountability Act (HIPAA)
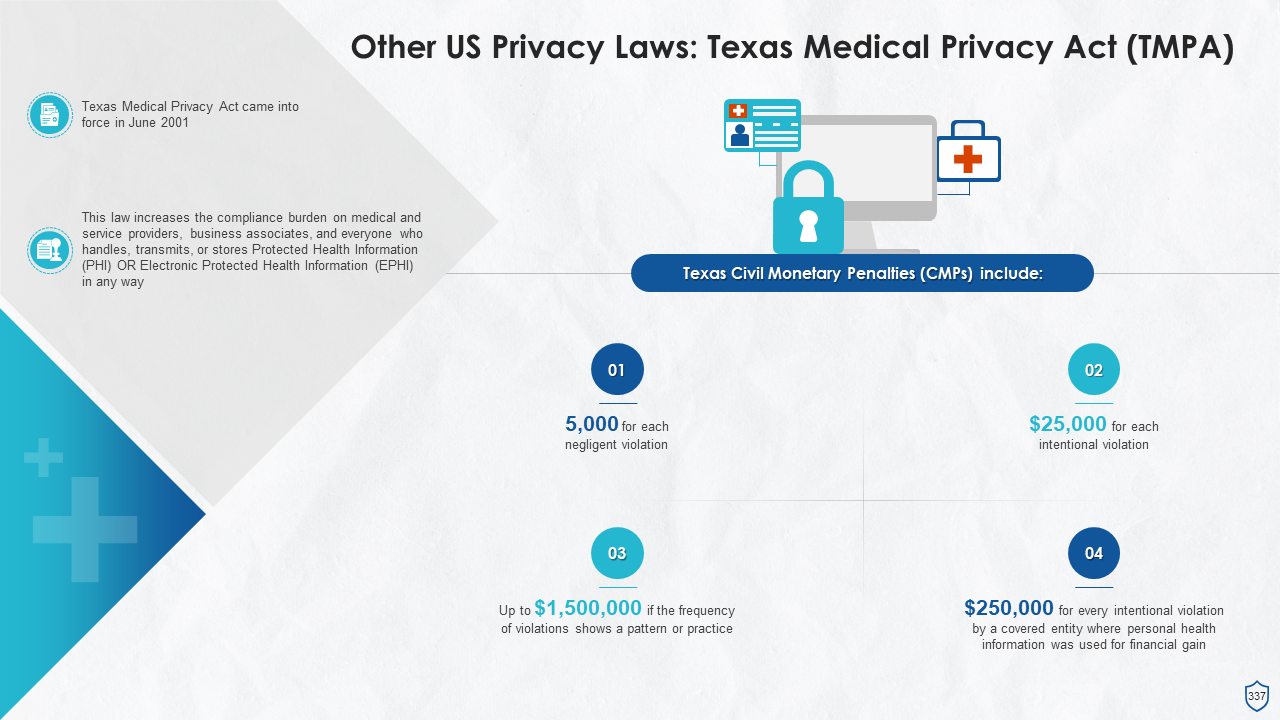
- Texas Medical Privacy Act (TMPA)
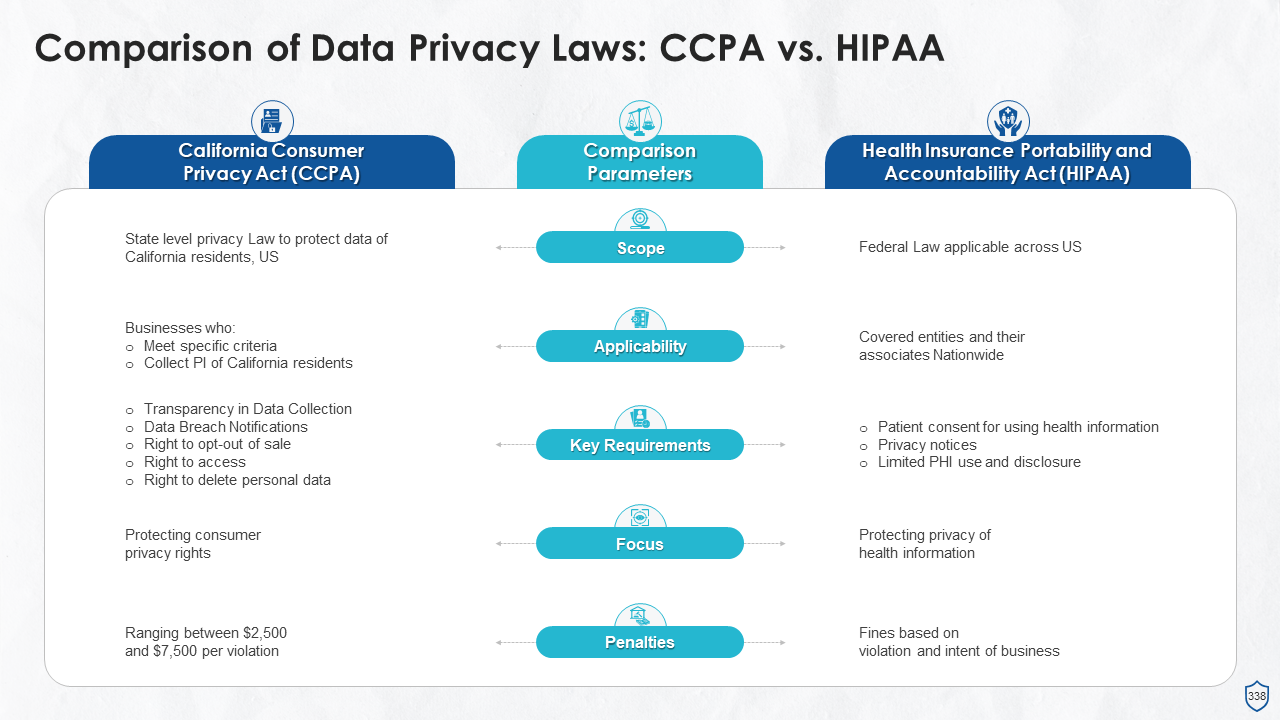
- CCPA vs. HIPAA
- TMPA vs. HIPAA
- Upcoming Privacy Regulations in the United States
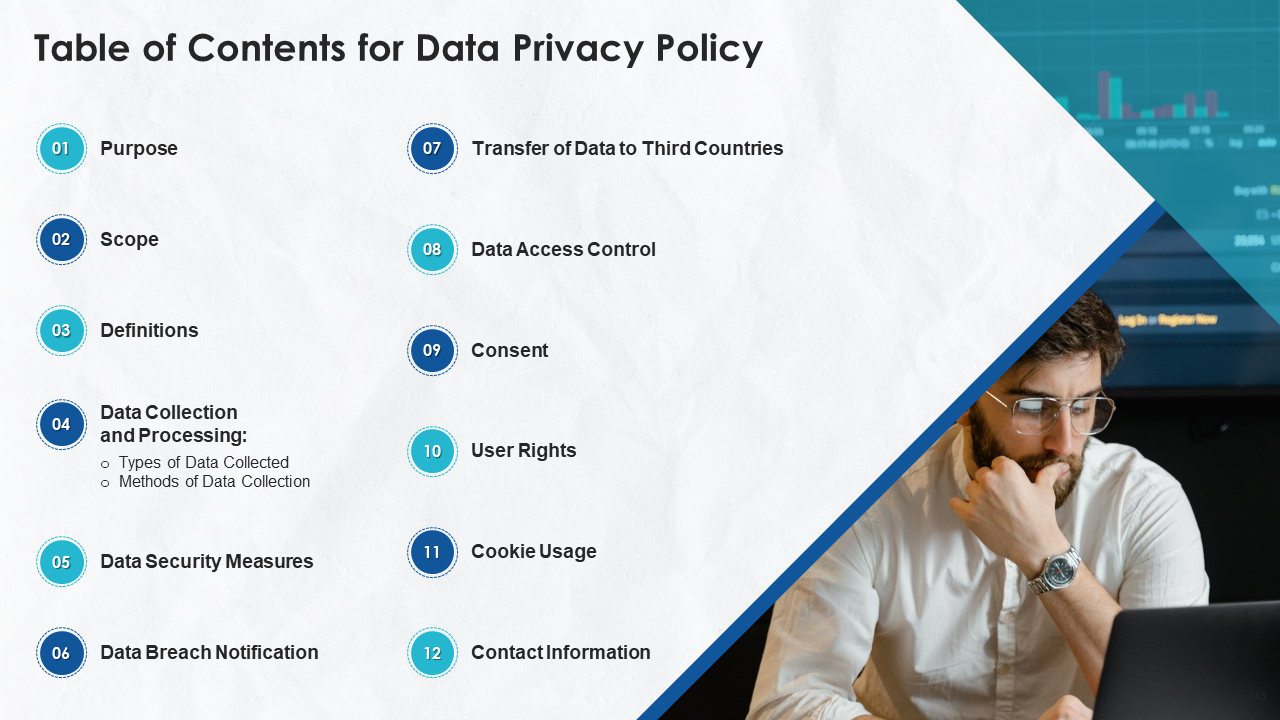
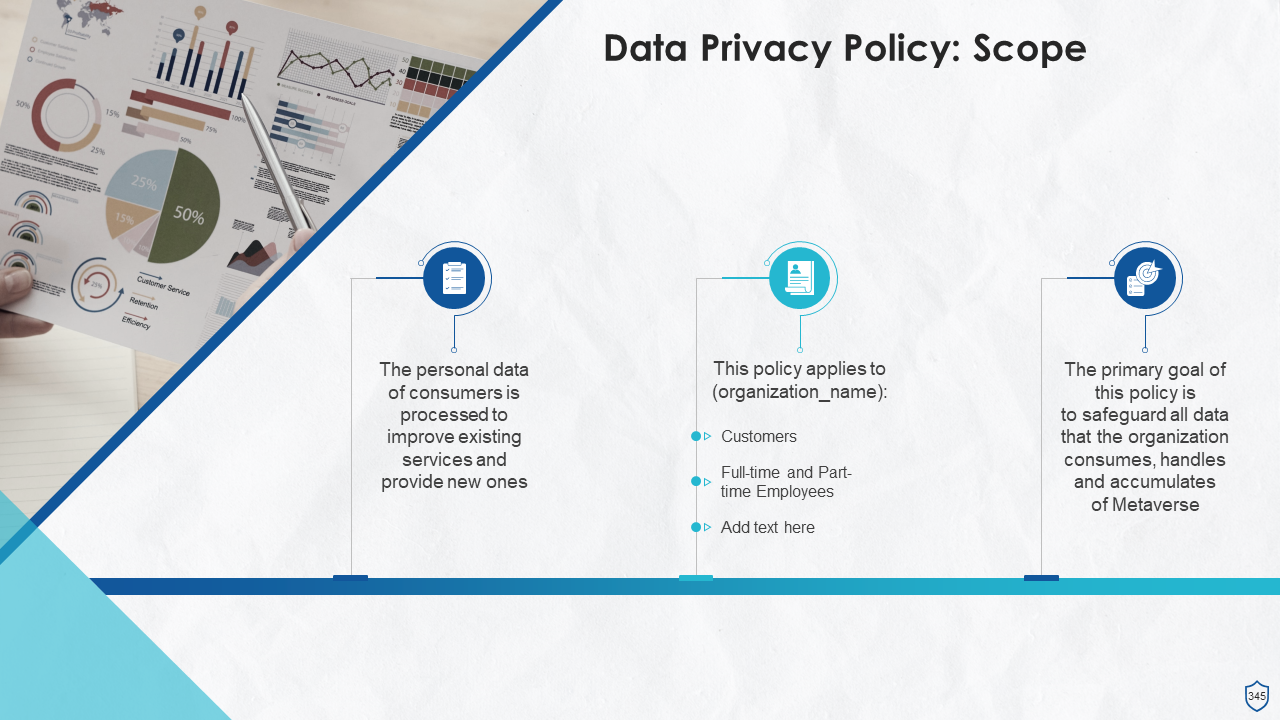
- Purpose
- Scope
- Definitions
- Data Collection and Processing:
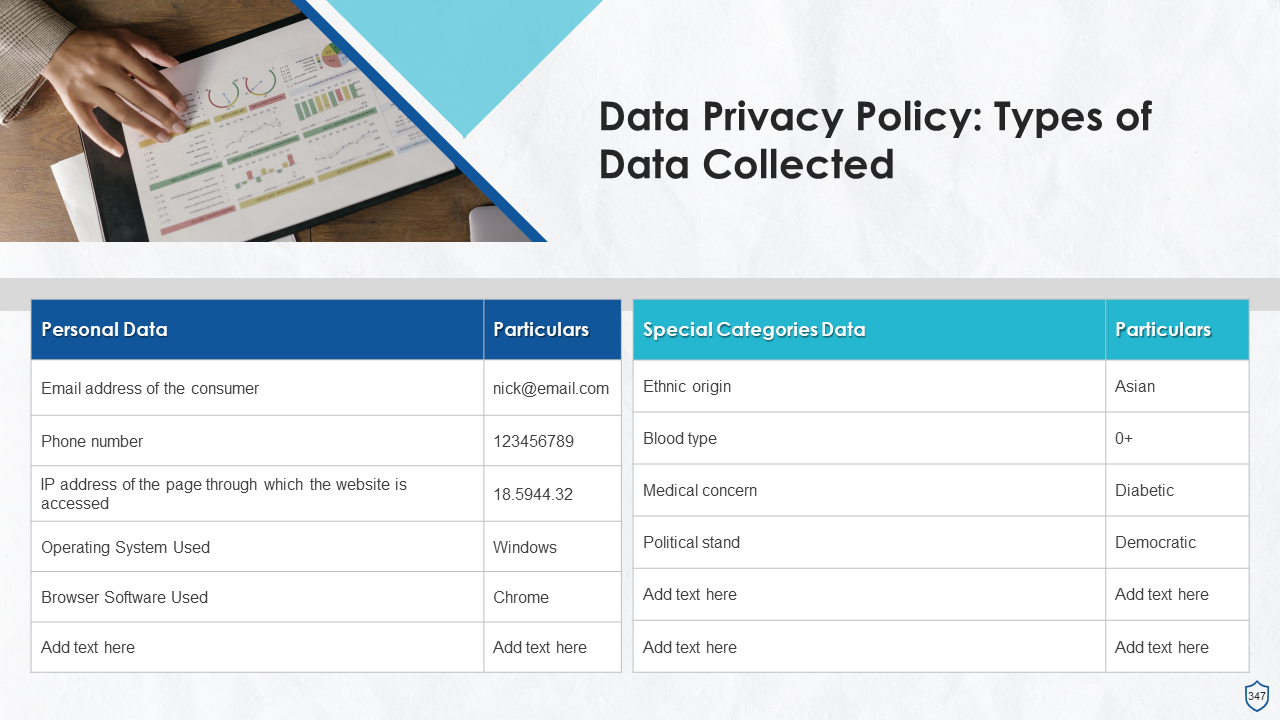
- Types of Data Collected
- Methods of Data Collection
- Data Security Measures
- Data Breach Notification
- Transfer of Data to Third Countries
- Data Access Control
- Consent
- User Rights
- Cookie Usage
- Contact Information
Sample Instructor Notes
What is this slide for: Data Privacy Compliance Reduce Financial Losses
This slide contains: This slide contains information on reducing the risk of fines and financial losses with the practice of data privacy at an organization. It avoids ransoms, non-compliance fines, and guards intellectual property.
Instructor’s Notes:
A robust data privacy policy enables a company to reduce the risk of financial loss as it:
- Avoids Ransoms:An excellent data policy allows a company to reduce the risk of data breaches and associated costs such as blackmailing or ransoms which can lead to financial as well as reputational losses
- Avoids Non-Compliance Fines:Many countries and jurisdictions have stringent laws and rules that make data protection and privacy mandatory. Complying with these regulations help companies avoid legal penalties and fines
- Guards Intellectual Property: Companies involved in creating intellectual property (IP), like patents, trademarks, or trade secrets, are at significant risk of data theft. They can protect their IP and avoid losses arising from infringement or misappropriation
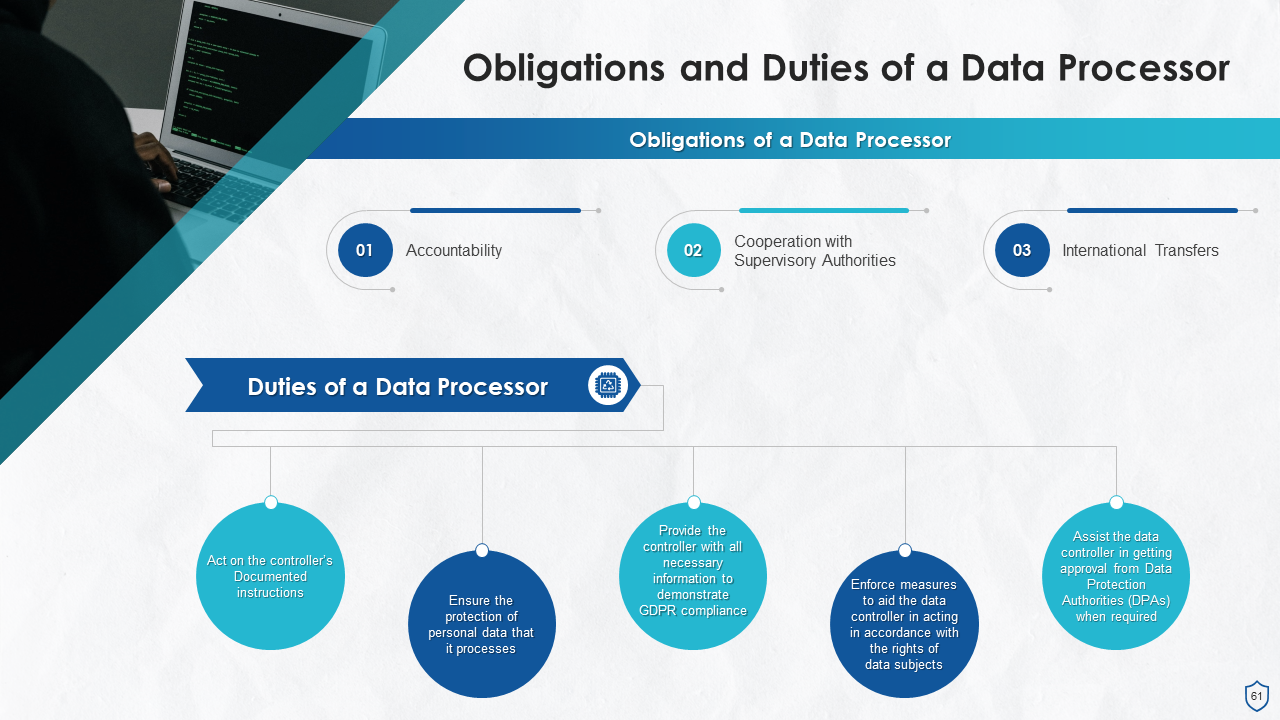
What is this slide for: Data Processor Obligations and Duties in GDPR
This slide contains: This slide states the obligations and responsibilities that a data processor must fulfil under the GDPR (General Data Protection Regulation).
Instructor’s Notes:
Following are the obligations of a data processor:
- Accountability: Even though a data processor does not have the authority to express the purpose behind the processing activities, but will be held accountable if something unlawful happens
- Cooperation with Supervisory Authorities: Data processors must assist the authorities (such as the Information Commissioner's Office) in performing their duties and extend a helping hand to them
- International Transfers: It is the duty of data processors that the controller approves any international transfers of personal data and are following the GDPR transfer provisions
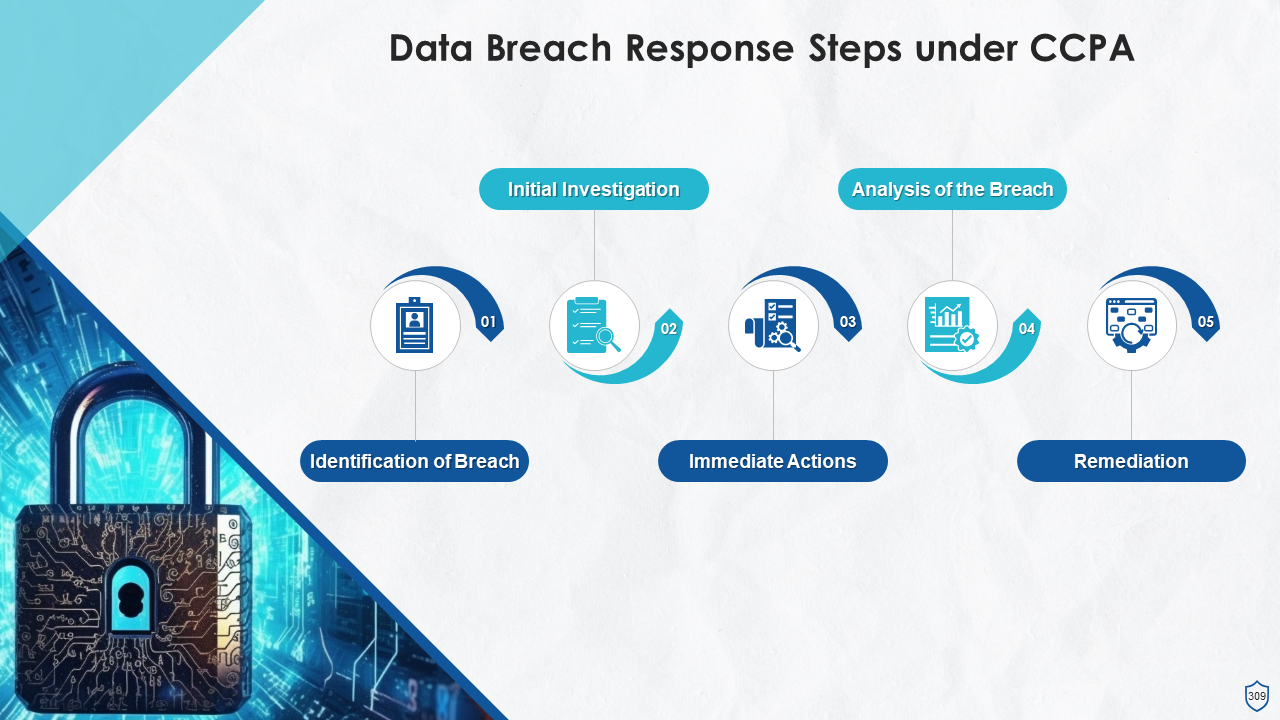
What is this slide for: Data Breach Response Steps under CCPA
This slide contains: This slide highlights the process of responding to a data breach as per the California Consumer Privacy Act. The steps are: Identification of breach, initial investigation, immediate actions, analysis of the breach, and remediation.
Instructor's Notes:
Steps involved in responding to data breach under CCPA are:
- Identification of Breach: Timely identification of a breach can reduce the time taken to remove the malicious actor from the system and begin the recovery process. Automated threat detection tools can be used to alert IT teams on the presence of malicious activity or outside intrusion
- Initial Investigation: Upon the identification of an incident, a preliminary investigation should be done. The goal is to determine the extent of damage, including the systems and services being affected. It might not be easy to detect all the damages, but it is better to assume that the breaches are severe rather than omitting details that could prolong the damage
- Immediate Actions: Since the nature of the breach has now been identified, steps should be taken to isolate the affected areas. For example, if an employee’s email account has been compromised, the IT team should opt for a forced lockout. If the organization has suffered a ransomware attack, the IT team should work to protect the unencrypted systems
- Analysis of the Breach: Next comes the task of analyzing the breach. It helps understand the scope of the breach, how it happened, and identify the type of data that was compromised. However, a few things need to be determined, such as whether an insider or an external hacker caused the breach, the level of access, and for how long was the information compromised
- Remediation: Recovery is the most critical aspect while responding to a data breach. The actions to be taken will be decided by assessing what went wrong. The organization must document responsibilities, prioritize tasks, and assign duties by keeping in mind how long each task will take
FAQs
We provide training decks on a wide variety of business and technical topics such as Diversity & Inclusion, Customer Service, Search Engine Optimization, Blockchain Technology, and many more. These are ready-to-present decks that can be downloaded and presented in their current form. These decks are carefully created by industry experts, designed by professionals to deliver a power packed training session.
We want our training decks to evoke curiosity and inspire passion for learning. Each training deck consists of multiple sessions with impeccably designed slides to explain concepts in-depth, key takeaways to summarize sessions, discussions, and multiple-choice questions to assess trainees’ learning. The deck also contains activities and memes to break the monotony and make the training more interactive. Each training deck comes with an assessment form and editable proposal to help pitch your training to clients with success.
It depends on the trainer's content delivery pace, but each deck is created to ensure that training content is for a minimum of 16 hours.
Yes. A significant segment of our customers are professional mentors, coaches and teachers. You can create presentations with our content and distribute these to your trainees. The only caveat is that you cannot share your subscription to our content with others; the license is not transferable. Also, you cannot resell SlideTeam content to others.
Each slide is 100% editable in PowerPoint. Every element of the slide – text, icons, images, vectors, color scheme, etc. can be modified to build an effective PowerPoint presentation. Simply DOWNLOAD, EDIT, and PRESENT!
All PPT slides are compatible with PowerPoint 2007 and above. Some diagrams will not show up correctly with older versions of PowerPoint, like PowerPoint 2003 or lower, because of rendering issues. Yes, they work with PowerPoint for MAC, and decks are compatible with Google Slides too.
Absolutely yes! Our decks are yours to keep and build upon even after your subscription expires. You will not be able to download any additional decks once your subscription expires, but the ones you've downloaded are yours to keep forever.
Our entire website is HTTPS secure, and our payment system is managed by PayPal and Stripe, two of the world's leaders in credit card payment systems and very respected companies in online payments. This makes our systems 100% secure. We do not store or have access to any credit card information ourselves. We direct you to these third-party secure sites with 100% secure SSL connections where you can safely purchase a subscription and then direct you back to our site to download products.
You are allowed to log in and download content from 3 computers. Our website keeps track of login IP addresses, MAC Address Usage, and Browser and Computer Operating System fingerprinting, and you will not be able to log in from more than three computers.

2 Item(s)
-
by Duncan Berry
4.5/580%The templates are the best in class. Very clear and innovative graphics! I am excited to explore and download more presentations.
-
by O'Connor Collins
4.5/5100%It makes easy work of my work presentations. I’ve never had to be nervous about my presentations for meetings.
2 Item(s)