Social Engineering Methods And Mitigation Strategies Powerpoint Presentation Slides
Check out our Social Engineering Methods and Mitigation Strategies PPT, which discusses the social engineering process of manipulating victims to provide access to their confidential information. Additionally, our Behavioral Exploitation Threats Awareness and Protection Module discusses several social engineering techniques, such as impersonation, tailgating, baiting, pretexting, scareware, quid pro quo, reverse social engineering, phishing, smishing, and dumpster diving. Furthermore, this Social Manipulation Techniques and Countermeasures Presentation demonstrates the different types of impersonation attacks, such as email spoofing, cousin domain, forged header, and account takeover. Moreover, this Social Engineering Risk Mitigation Strategies for Businesses Guide outlines the techniques used to conduct baiting attacks, such as online downloads, malware-infected devices, and tempting offers. It also represents the preventive strategies to protect employees from social engineering scams and phishing attacks. Lastly, this Safeguarding Your Organization from Social Engineering Deck comprises a checklist, a roadmap, a 30-60-90 plan, and a timeline for implementing different security measures in organizations to stay safe from social engineering attacks. Download our 100 percent editable and customizable template, also compatible with Google Slides.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Social Engineering Methods And Mitigation Strategies Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty four slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Social Engineering Methods and Mitigation Strategies. State Your Company Name and begin.
Slide 2: This slide is an Agenda slide. State your agendas here.
Slide 3: This slide shows a Table of Contents for the presentation.
Slide 4: This slide is an introductory slide.
Slide 5: This slide discusses about social engineering process of manipulating victims to provide access to their confidential information.
Slide 6: This slide is an introductory slide.
Slide 7: This slide represents the different types of social engineering attacks based on technology and human interaction.
Slide 8: This slide is an introductory slide.
Slide 9: This slide discusses social engineering attacks using impersonation method.
Slide 10: This slide represents the effective strategies to stay safe from impersonation attacks.
Slide 11: This slide is an introductory slide.
Slide 12: This slide demonstrates the procedure of tailgating attack with the help of an illustrative example.
Slide 13: This slide highlights the best practices to avoid tailgating social engineering attacks.
Slide 14: This slide is an introductory slide.
Slide 15: This slide discusses baiting technique of social engineering attacks.
Slide 16: This slide outlines the methods to prevent baiting attacks.
Slide 17: This slide compares the two major techniques of social engineering attacks, known as baiting and phishing.
Slide 18: This slide is an introductory slide.
Slide 19: This slide discusses the pretexting technique of social engineering and its examples.
Slide 20: This slide puts the preventive measures to stay safe from pretexting attacks.
Slide 21: This slide is an introductory slide.
Slide 22: This slide discusses the quid pro quo social engineering scams.
Slide 23: This slide outlines the different methods used by attackers to implement quid pro quo scams.
Slide 24: This slide represents the methods to avoid quid pro quo social engineering scams.
Slide 25: This slide is an introductory slide.
Slide 26: This slide discusses reverse social engineering scams.
Slide 27: This slide contains the strategies to avoid reverse social engineering scams.
Slide 28: This slide is an introductory slide.
Slide 29: This slide discusses dumpster diving technique used to carry out social engineering attacks.
Slide 30: This slide is an introductory slide.
Slide 31: This slide represents the scareware technique used by scammers to attempt social engineering attacks.
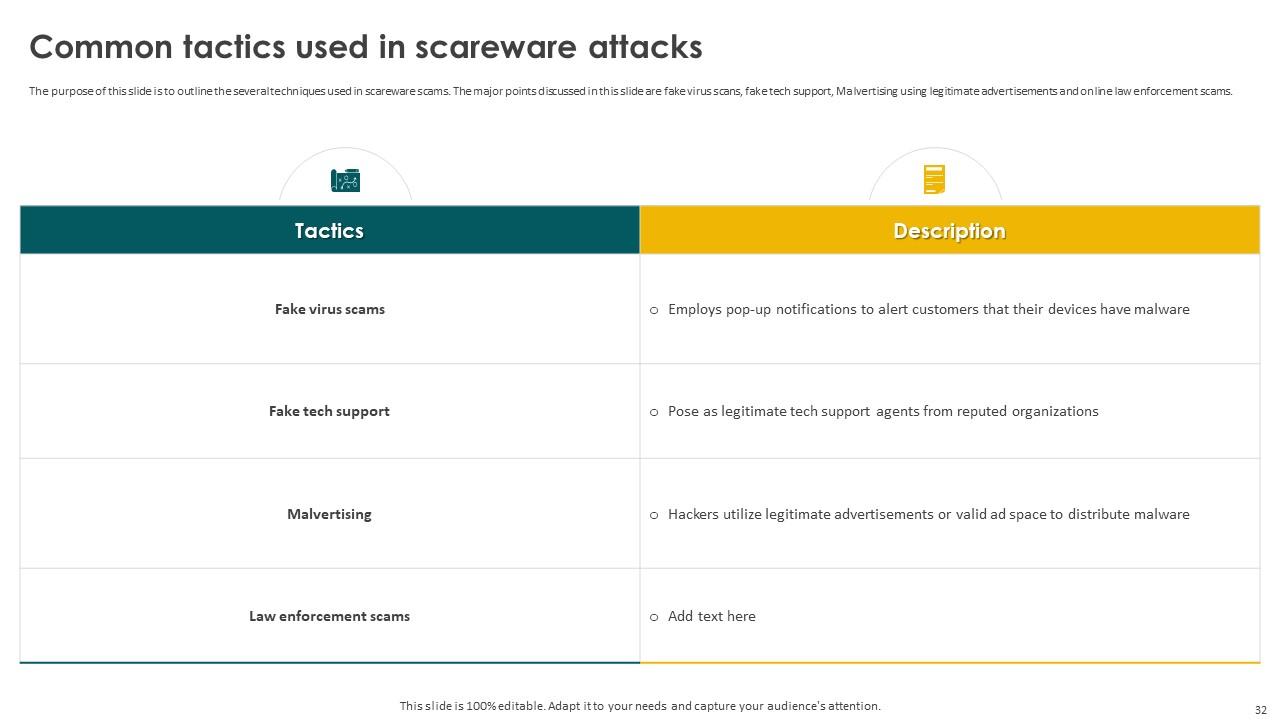
Slide 32: This slide outlines the several techniques used in scareware scams.
Slide 33: This slide represents the various steps involved in fake antivirus scareware campaign process.
Slide 34: This slide entails the tools and best practice to avoid scareware attacks.
Slide 35: This slide is an introductory slide.
Slide 36: This slide demonstrates the overview of cyber phishing attacks.
Slide 37: This slide outlines the various preventive measures to stay safe from phishing attacks.
Slide 38: This slide is an introductory slide.
Slide 39: This slide denotes the procedure of email-based phishing attacks.
Slide 40: This slide talks about several email-based phishing attacks such as spear phishing and whaling.
Slide 41: This slide is an introductory slide.
Slide 42: This slide illustrates the structure of spear phishing attack.
Slide 43: This slide talks about the various methods of identifying spear phishing cyber attacks.
Slide 44: This slide illustrates the steps to be taken immediately after falling for a spear phishing scam.
Slide 45: This slide is an introductory slide.
Slide 46: This slide contains the whaling phishing attack which is also known as CEO fraud.
Slide 47: This slide caters to the various methods of identifying whale phishing cyber attacks.
Slide 48: This slide is an introductory slide.
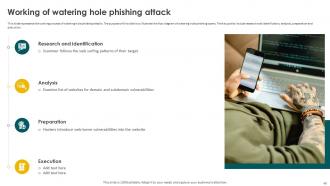
Slide 49: This slide depicts the working process of watering hole phishing attacks.
Slide 50: This slide outlines the various preventive measures to avoid watering hole phishing attacks.
Slide 51: This slide is an introductory slide.
Slide 52: This slide talks about the vishing cyber attacks.
Slide 53: This slide deals with the various types of vishing cyber attacks.
Slide 54: This slide entails the ways to protect users from vishing attacks.
Slide 55: This slide is an introductory slide.
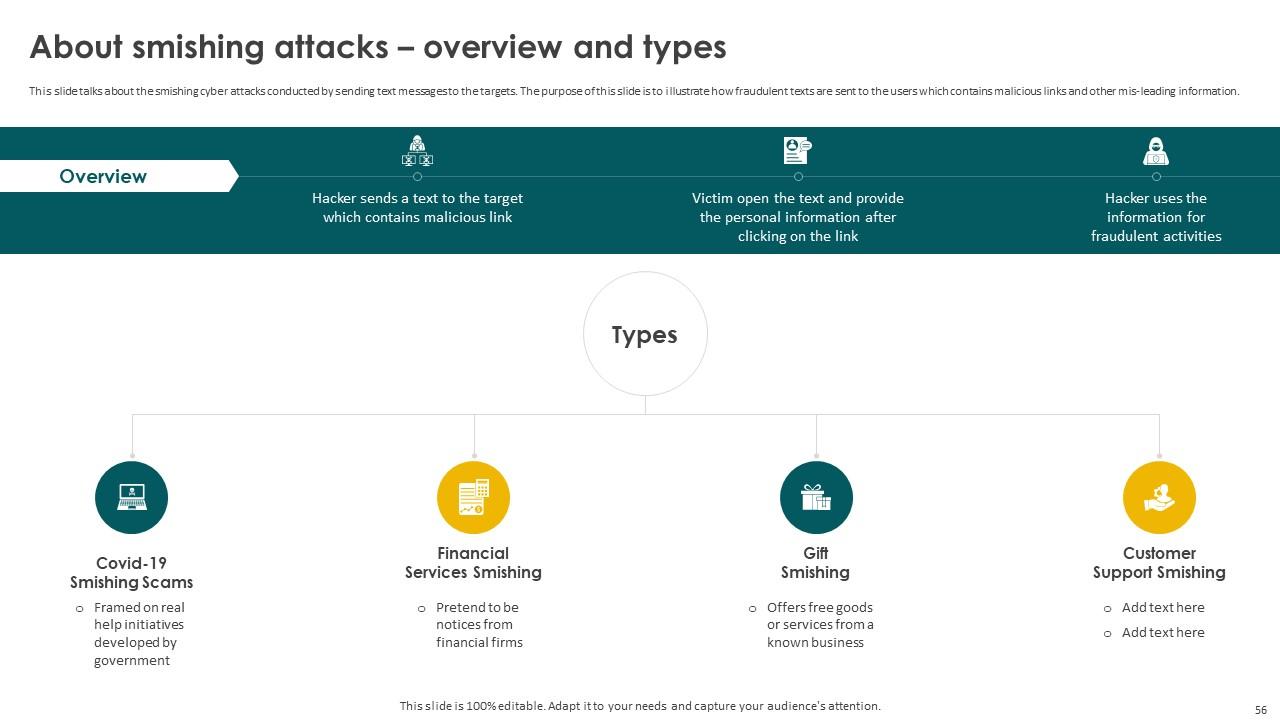
Slide 56: This slide showcases the smishing cyber attacks conducted by sending text messages to the targets.
Slide 57: This slide shows the various methods of identifying smishing cyber attacks.
Slide 58: This slide is an introductory slide.
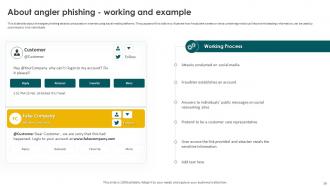
Slide 59: This slide talks about the angler phishing attacks conducted on internet using social media platforms.
Slide 60: This slide illustrates the various methods of identifying angler phishing cyber attacks.
Slide 61: This slide is an introductory slide.
Slide 62: This slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server.
Slide 63: This slide illustrates the process of executing man-in-the-middle cyber attacks.
Slide 64: This slide outlines the various methods of preventing man-in-the-middle cyber attacks.
Slide 65: This slide is an introductory slide.
Slide 66: This slide represents the training program for employees which will help them to prevent various cyber security scams in business.
Slide 67: This slide shows the cost breakup of social engineering awareness training program.
Slide 68: This slide is an introductory slide.
Slide 69: This slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks.
Slide 70: This slide represents 30-60-90 plan to protect companies and their employees from social engineering attacks.
Slide 71: This slide shows the timeline to protect organizations from social engineering attacks.
Slide 72: This slide presents the roadmap to prevent social engineering attacks in organizations.
Slide 73: This slide is an introductory slide.
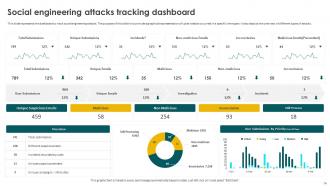
Slide 74: This slide puts the dashboard to track social engineering attacks.
Slide 75: This slide shows all the icons included in the presentation.
Slide 76: This slide is titled Additional Slides for moving forward.
Slide 77: This slide is Our Team slide with names and designations.
Slide 78: This slide is a Timeline slide. Show data related to time intervals here.
Slide 79: This slide is an About Us slide to show company specifications etc.
Slide 80: This slide is Our Target slide. State your targets here.
Slide 81: This slide depicts a Venn diagram with text boxes.
Slide 82: This slide presents a Roadmap with additional text boxes.
Slide 83: This slide showcases the suitable graph/chart.
Slide 84: This slide is a thank-you slide with address, contact numbers, and email address.
Social Engineering Methods And Mitigation Strategies Powerpoint Presentation Slides with all 93 slides:
Use our Social Engineering Methods And Mitigation Strategies Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
SlideTeam is the best in the business. Their templates are engaging and customizable. You can rely on them.
-
Keep doing the good work guys. Surpass the needs and expectations always!!