Data Management PowerPoint Templates, Big Data PPT Slides, and Presentation Graphics
- Sub Categories
-
- 30 60 90 Day Plan
- About Us Company Details
- Action Plan
- Agenda
- Annual Report
- Audit Reports
- Balance Scorecard
- Brand Equity
- Business Case Study
- Business Communication Skills
- Business Plan Development
- Business Problem Solving
- Business Review
- Capital Budgeting
- Career Planning
- Change Management
- Color Palettes
- Communication Process
- Company Location
- Company Vision
- Compare
- Competitive Analysis
- Corporate Governance
- Cost Reduction Strategies
- Custom Business Slides
- Customer Service
- Dashboard
- Data Management
- Decision Making
- Digital Marketing Strategy
- Digital Transformation
- Disaster Management
- Diversity
- Equity Investment
- Financial Analysis
- Financial Services
- Financials
- Growth Hacking Strategy
- Human Resource Management
- Innovation Management
- Interview Process
- Knowledge Management
- Leadership
- Lean Manufacturing
- Legal Law Order
- Management
- Market Segmentation
- Marketing
- Media and Communication
- Meeting Planner
- Mergers and Acquisitions
- Metaverse
- Newspapers
- Operations and Logistics
- Organizational Structure
- Our Goals
- Performance Management
- Pitch Decks
- Pricing Strategies
- Process Management
- Product Development
- Product Launch Ideas
- Product Portfolio
- Project Management
- Purchasing Process
- Quality Assurance
- Quotes and Testimonials
- Real Estate
- Risk Management
- Sales Performance Plan
- Sales Review
- SEO
- Service Offering
- Six Sigma
- Social Media and Network
- Software Development
- Solution Architecture
- Stock Portfolio
- Strategic Management
- Strategic Planning
- Supply Chain Management
- Swimlanes
- System Architecture
- Team Introduction
- Testing and Validation
- Thanks-FAQ
- Time Management
- Timelines Roadmaps
- Value Chain Analysis
- Value Stream Mapping
- Workplace Ethic
-
 Ping Flood Attack As A Type Of Dos Attack Training Ppt
Ping Flood Attack As A Type Of Dos Attack Training PptPresenting Ping Flood Attack as a Type of DoS Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Ping Of Death Attack As A Type Of Dos Attack Training Ppt
Ping Of Death Attack As A Type Of Dos Attack Training PptPresenting Ping of Death Attack as a Type of DoS Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Identifying A Denial Of Service Attack Training Ppt
Identifying A Denial Of Service Attack Training PptPresenting Identifying a Denial of Service Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Distributed Denial Of Service Attack In Cyber Security Training Ppt
Distributed Denial Of Service Attack In Cyber Security Training PptPresenting Distributed Denial of Service Attack in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Working Of Distributed Denial Of Service Or DDoS Attacks Training Ppt
Working Of Distributed Denial Of Service Or DDoS Attacks Training PptPresenting Working of Distributed Denial of Service or DDoS Attacks . This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Difference Between Dos And DDoS Attacks Training Ppt
Difference Between Dos And DDoS Attacks Training PptPresenting Difference Between DoS and DDoS Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Ways To Identify DDoS Attacks Training Ppt
Ways To Identify DDoS Attacks Training PptPresenting Ways to Identify DDoS Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Components Of Network Targeted By DDoS Attacks OSI Model Training Ppt
Components Of Network Targeted By DDoS Attacks OSI Model Training PptPresenting Components of Network Targeted by DDoS Attacks OSI Model. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Categories Of DDoS Attacks Training Ppt
Categories Of DDoS Attacks Training PptPresenting Categories of DDoS Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Application Layer Attack As A Category Of DDoS Attack Training Ppt
Application Layer Attack As A Category Of DDoS Attack Training PptPresenting Application Layer Attack as a Category of DDoS Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 HTTP Flood As An Example Of Application Layer Attack Training Ppt
HTTP Flood As An Example Of Application Layer Attack Training PptPresenting HTTP Flood as an Example of Application Layer Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Protocol Attack As A Category Of DDoS Attack Training Ppt
Protocol Attack As A Category Of DDoS Attack Training PptPresenting Protocol Attack as a Category of DDoS Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 SYN Flood As An Example Of Protocol Attack Training Ppt
SYN Flood As An Example Of Protocol Attack Training PptPresenting SYN Flood as an Example of Protocol Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Volumetric Attack As A Category Of DDoS Attack Training Ppt
Volumetric Attack As A Category Of DDoS Attack Training PptPresenting Volumetric Attack as a Category of DDoS Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 DNS Amplification As An Example Of Volumetric Attack Training Ppt
DNS Amplification As An Example Of Volumetric Attack Training PptPresenting DNS Amplification as an Example of Volumetric Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Ways To Mitigate A DDoS Attack Training Ppt
Ways To Mitigate A DDoS Attack Training PptPresenting Ways to Mitigate a DDoS Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Blackhole Routing To Prevent Password Attacks Training Ppt
Blackhole Routing To Prevent Password Attacks Training PptPresenting Blackhole Routing to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Rate Limiting To Prevent DDoS Attacks Training Ppt
Rate Limiting To Prevent DDoS Attacks Training PptPresenting Rate Limiting to Prevent DDoS Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Anycast Network Diffusion To Prevent DDoS Attacks Training Ppt
Anycast Network Diffusion To Prevent DDoS Attacks Training PptPresenting Anycast Network Diffusion to Prevent DDoS Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Web Application Firewalls Wafs To Prevent Password Attacks Training Ppt
Web Application Firewalls Wafs To Prevent Password Attacks Training PptPresenting Web Application Firewalls WAFs to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Man In The Middle Attacks In Cybersecurity Training Ppt
Man In The Middle Attacks In Cybersecurity Training PptPresenting Man in the Middle Attacks in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Working Of Man In The Middle Attacks Training Ppt
Working Of Man In The Middle Attacks Training PptPresenting Working of Man in the Middle Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Execution Of Man In The Middle Attacks Training Ppt
Execution Of Man In The Middle Attacks Training PptPresenting Execution of Man in the Middle Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
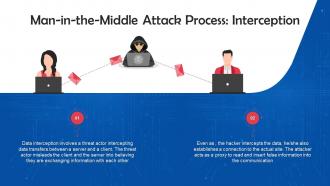 Interception Mode Of Executing Man In The Middle Attacks Training Ppt
Interception Mode Of Executing Man In The Middle Attacks Training PptPresenting Interception Mode of Executing Man in the Middle Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Decryption To Execute Man In The Middle Attacks Training Ppt
Decryption To Execute Man In The Middle Attacks Training PptPresenting Decryption to Execute Man-in-the-Middle Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Types Of Man In The Middle Attacks Training Ppt
Types Of Man In The Middle Attacks Training PptPresenting Working of Types of Man in the Middle Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 IP Spoofing As A Type Of Man In The Middle Attack Training Ppt
IP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting IP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 HTTP Spoofing As A Type Of Man In The Middle Attack Training Ppt
HTTP Spoofing As A Type Of Man In The Middle Attack Training PptPresenting HTTP Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 DNS Spoofing As A Type Of Man In The Middle Attack Training Ppt
DNS Spoofing As A Type Of Man In The Middle Attack Training PptPresenting DNS Spoofing as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Email Spoofing As A Type Of Man In The Middle Attack Training Ppt
Email Spoofing As A Type Of Man In The Middle Attack Training PptPresenting Email Spoofing as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 SSL Hijacking As A Type Of Man In The Middle Attack Training Ppt
SSL Hijacking As A Type Of Man In The Middle Attack Training PptPresenting SSL Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Session Hijacking As A Type Of Man In The Middle Attack Training Ppt
Session Hijacking As A Type Of Man In The Middle Attack Training PptPresenting Session Hijacking as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cache Poisoning As A Type Of Man In The Middle Attack Training Ppt
Cache Poisoning As A Type Of Man In The Middle Attack Training PptPresenting Cache Poisoning as a Type of Man in the Middle Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training Ppt
Wi Fi Eavesdropping As A Type Of Man In The Middle Attack Training PptPresenting Wi-Fi Eavesdropping as a Type of Man in the Middle Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Example Of Man In The Middle Attack Training Ppt
Example Of Man In The Middle Attack Training PptPresenting Example of Man in the Middle Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Prevention Of Man In The Middle Attacks Training Ppt
Prevention Of Man In The Middle Attacks Training PptPresenting Prevention of Man in the Middle Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Man In The Browser Attacks In Cybersecurity Training Ppt
Man In The Browser Attacks In Cybersecurity Training PptPresenting Man in the Browser Attacks in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Working Of Man In The Browser Attacks Training Ppt
Working Of Man In The Browser Attacks Training PptPresenting Working of Man in the Browser Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Examples Of Man In The Browser Attacks Training Ppt
Examples Of Man In The Browser Attacks Training PptPresenting Examples of Man in the Browser Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Zeus As A Man In The Browser Attack Training Ppt
Zeus As A Man In The Browser Attack Training PptPresenting Zeus as a Man in the Browser Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 SpyEye As A Man In The Browser Attack Training Ppt
SpyEye As A Man In The Browser Attack Training PptPresenting SpyEye as a Man in the Browser Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 OddJob As A Man In The Browser Attack Training Ppt
OddJob As A Man In The Browser Attack Training PptPresenting OddJob as a Man in the Browser Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Key Signs Of Man In The Browser Attacks Training Ppt
Key Signs Of Man In The Browser Attacks Training PptPresenting Key Signs of Man-in-the-Browser Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Preventing Man In The Browser Attacks Training Ppt
Preventing Man In The Browser Attacks Training PptPresenting Preventing Man-in-the-Browser Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Spyware Cyber Attack In Cybersecurity Training Ppt
Spyware Cyber Attack In Cybersecurity Training PptPresenting Spyware Cyber Attack in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Overview Of Working Of Spyware Training Ppt
Overview Of Working Of Spyware Training PptPresenting Overview of Working of Spyware. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Ways Spyware Infections Can Occur Training Ppt
Ways Spyware Infections Can Occur Training PptPresenting Ways Spyware Infections can Occur. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Different Types Of Spyware Infections Training Ppt
Different Types Of Spyware Infections Training PptPresenting Different Types of Spyware Infections. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Common Examples Of Spyware Infections Training Ppt
Common Examples Of Spyware Infections Training PptPresenting Common Examples of Spyware Infections. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Ways To Prevent Spyware Infections Training Ppt
Ways To Prevent Spyware Infections Training PptPresenting Ways to Prevent Spyware Infections. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Ways To Remove Spyware Infections Training Ppt
Ways To Remove Spyware Infections Training PptPresenting Ways to Remove Spyware Infections. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Anti Spyware Tools In Cybersecurity Training Ppt
Anti Spyware Tools In Cybersecurity Training PptPresenting Anti Spyware Tools in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Social Engineering Attacks In Cybersecurity Training Ppt
Social Engineering Attacks In Cybersecurity Training PptPresenting Social Engineering Attacks in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 The Social Engineering Life Cycle Training Ppt
The Social Engineering Life Cycle Training PptPresenting The Social Engineering Life Cycle. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Types Of Social Engineering Techniques Training Ppt
Types Of Social Engineering Techniques Training PptPresenting Types of Social Engineering Techniques. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Baiting As A Social Engineering Technique Training Ppt
Baiting As A Social Engineering Technique Training PptPresenting Baiting as a Social Engineering Technique . This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Pretexting As A Social Engineering Technique Training Ppt
Pretexting As A Social Engineering Technique Training PptPresenting Pretexting as a Social Engineering Technique. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Scareware As A Social Engineering Technique Training Ppt
Scareware As A Social Engineering Technique Training PptPresenting Scareware as a Social Engineering Technique. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Phishing As A Social Engineering Technique Training Ppt
Phishing As A Social Engineering Technique Training PptPresenting Phishing as a Social Engineering Technique. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Watering Hole Attack As A Social Engineering Technique Training Ppt
Watering Hole Attack As A Social Engineering Technique Training PptPresenting Watering Hole Attack as a Social Engineering Technique. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
What a stunning collection of customizable templates! Really a time-saver..
-
SlideTeam just saved my project! Thank you so much. The variety of templates helped me showcase multiple perspectives easily.
-
It’s really cool, and you can find pretty much everything you could need for your work or school.
-
The designs are very attractive and easy to edit. Looking forward to downloading more of your PowerPoint Presentations.
-
Editable, diversified, compatible with MS PPT and Google Slides, and on top of that finest graphics!! I mean in the words of the famous Ross Geller, “What more do you want!”
-
Placing an order on SlideTeam is very simple and convenient, saves you a lot of your time.
-
I discovered this website through a google search, the services matched my needs perfectly and the pricing was very reasonable. I was thrilled with the product and the customer service. I will definitely use their slides again for my presentations and recommend them to other colleagues.
-
The design is clean-cut, modern, and sleek, keeping the users' needs in mind. The multiple uses make this product worth every penny!
-
Excellent design and quick turnaround.
-
Definitely a time saver! Predesigned and easy-to-use templates just helped me put together an amazing presentation.






