Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides
Check out our professionally designed Phishing Attacks and Strategies to Mitigate them PowerPoint Presentation. It systematically illustrates the operational processes involved in cyber phishing attacks, shedding light on various targeted industries susceptible to cyber crimes and elucidating why organizations become victims. Additionally, the presentation delineates diverse types of phishing attacks and offers practical strategies to thwart them. These encompass email phishing, spear phishing, whale phishing, vishing, smishing, angler phishing, pharming, pop-up phishing, clone phishing, Man-in-the-Middle attacks, evil twin scams, watering hole attacks, and search engine phishing. It also provides insights into adopting a multi-layered approach to bolster phishing defenses and guidelines to safeguard against phishing scams. Furthermore, the spear phishing deck incorporates sections on phishing attack awareness training, presenting a comprehensive plan for implementing phishing awareness campaigns within organizations. It outlines the resources companies can provide to employees to protect themselves from cybercrime. Lastly, the man-in-the-middle phishing deck encompasses a roadmap, a 30-60-90 days plan, a timeline, a checklist for securing organizations against phishing attacks, and a dashboard for tracking cyber-attacks. Download our 100 percent editable and customizable PowerPoint, compatible with Google Slides, to streamline your presentation process.
You must be logged in to download this presentation.
 Impress your
Impress your audience
Editable
of Time
PowerPoint presentation slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of ninety five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Phishing Attacks and Strategies to Mitigate them. State your company name and begin.
Slide 2: This is an Agenda slide. State your agendas here.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide shows title for topics that are to be covered next in the template.
Slide 5: This slide demonstrates the overview of cyber phishing attacks and talk about the effectiveness of phishing scams.
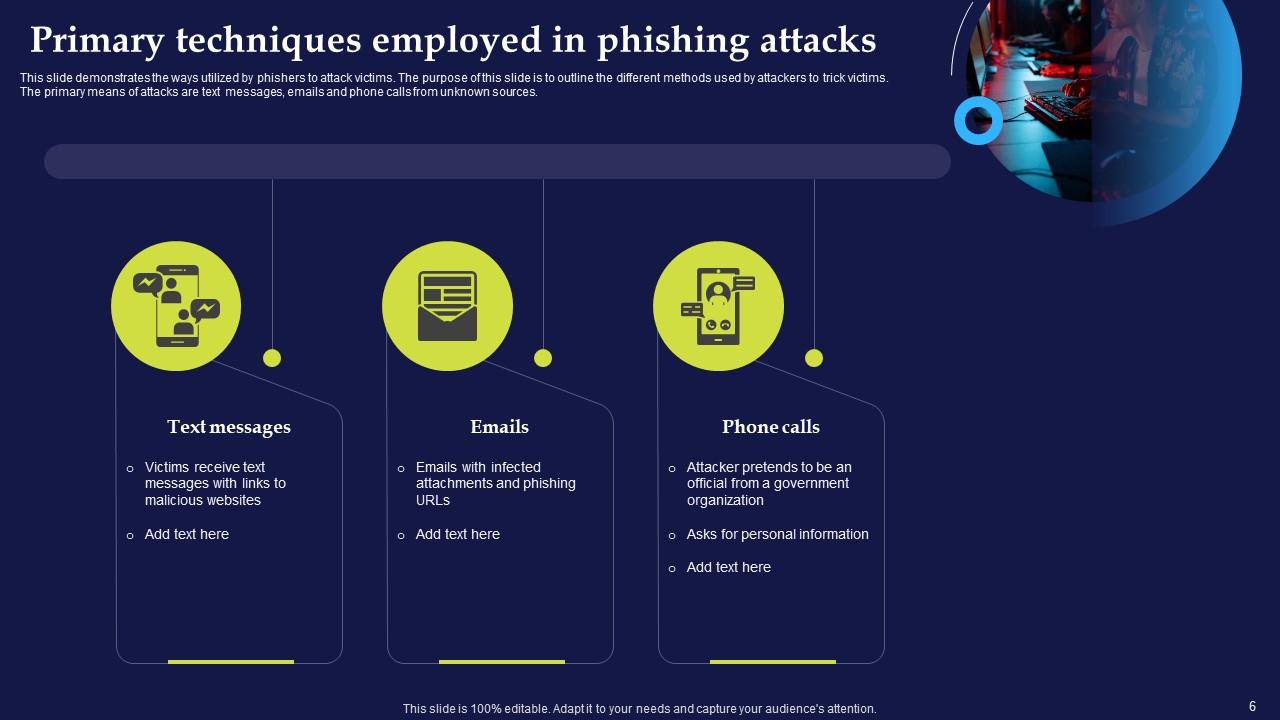
Slide 6: This slide presents the ways utilized by phishers to attack victims and outline the different methods used by attackers to trick victims.
Slide 7: This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted.
Slide 8: This slide demonstrates the working flow of a phishing attack and outline the various phases of phishing scams such as campaign crafted, payloads etc.
Slide 9: This slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks.
Slide 10: This slide shows title for topics that are to be covered next in the template.
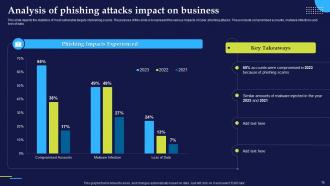
Slide 11: This slide discusses the impact of phishing attacks on businesses and outline the amount of money lost by well-reputed companies due to phishing scams.
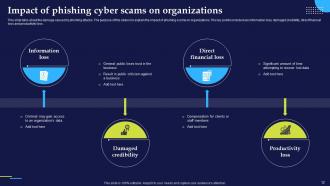
Slide 12: This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations.
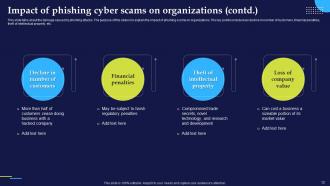
Slide 13: This slide describes about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations.
Slide 14: This slide represents the statistics of most targeted industries of phishing scams.
Slide 15: This slide depicts the statistics of most vulnerable targets of phishing scams and represent the various impacts of cyber phishing attacks.
Slide 16: This slide shows title for topics that are to be covered next in the template.
Slide 17: This slide outlines the various types of cyber phishing attacks. The types include email phishing, HTTPS phishing, whaling etc.
Slide 18: This slide shows title for topics that are to be covered next in the template.
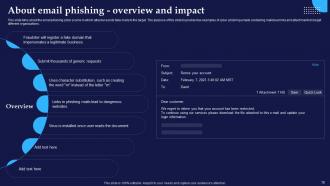
Slide 19: This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target.
Slide 20: This slide demonstrates the procedure of email-based phishing attacks and explain how fake websites are used by attackers to get the sensitive data of the users.
Slide 21: This slide talks about the warning signs that can help the user to recognize phishing email.
Slide 22: This slide shows title for topics that are to be covered next in the template.
Slide 23: This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons.
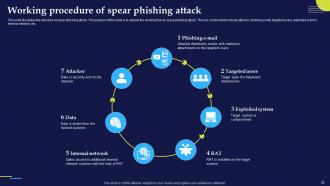
Slide 24: This slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack.
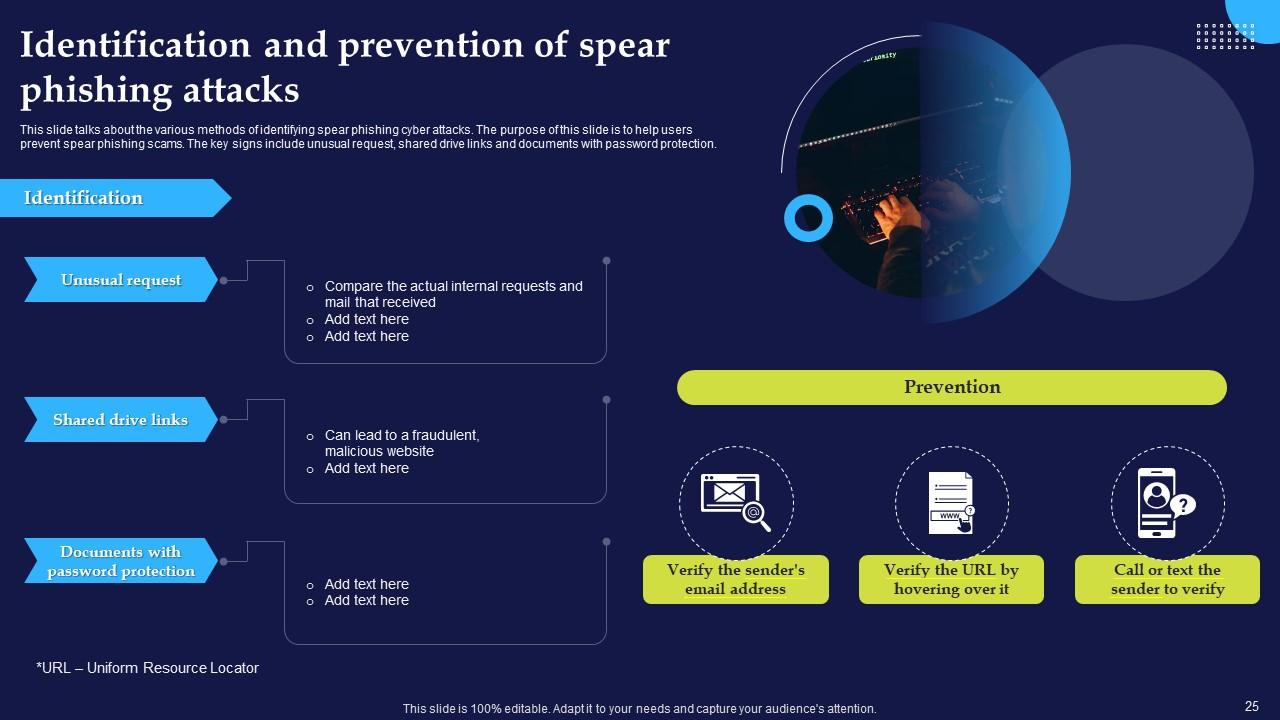
Slide 25: This slide talks about the various methods of identifying spear phishing cyber attacks.
Slide 26: This slide illustrates the steps to be taken immediately after falling for a spear phishing scam.
Slide 27: This slide shows title for topics that are to be covered next in the template.
Slide 28: This slide talks about the whaling phishing attack which is also known as CEO fraud.
Slide 29: This slide talks about the various methods of identifying whale phishing cyber attacks.
Slide 30: This slide shows title for topics that are to be covered next in the template.
Slide 31: This slide talks about the vishing cyber attacks and explain the vishing technique used by phishers to scam victims.
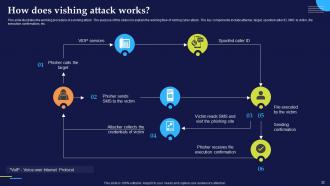
Slide 32: This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack.
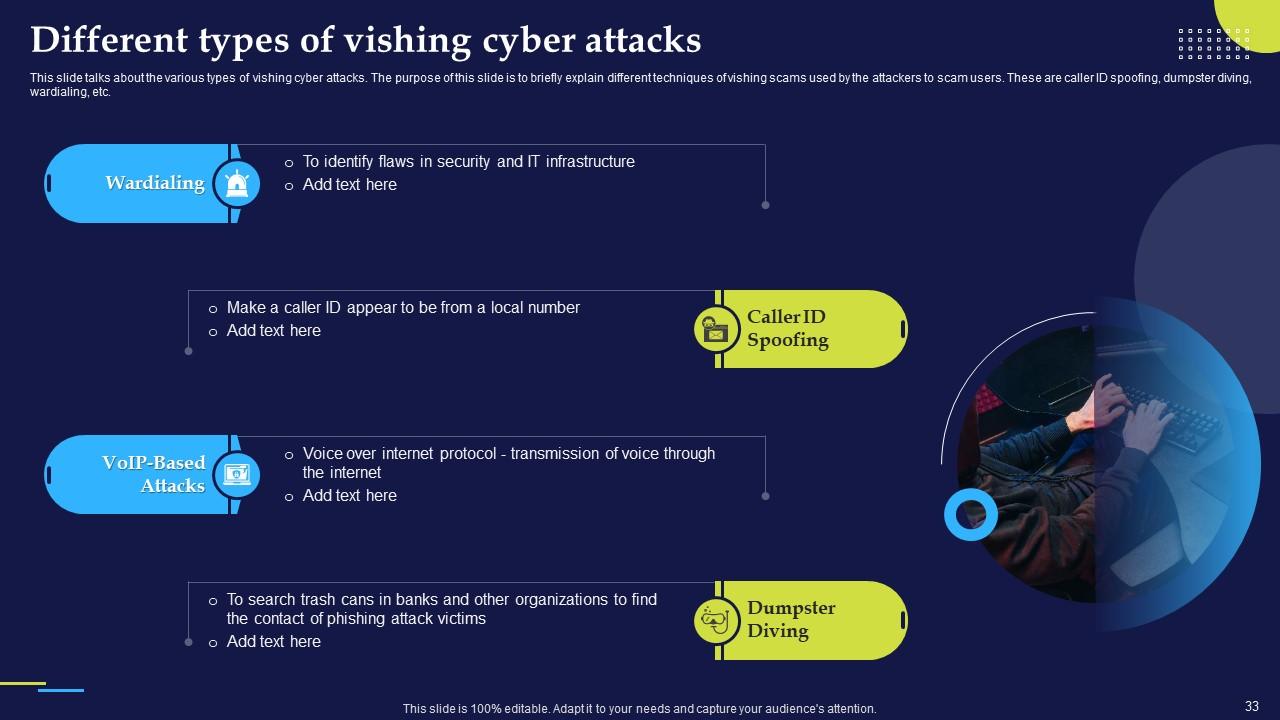
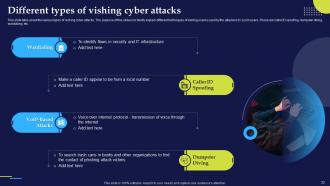
Slide 33: This slide talks about the various types of vishing cyber attacks and briefly explain different techniques of vishing scams used by the attackers to scam users.
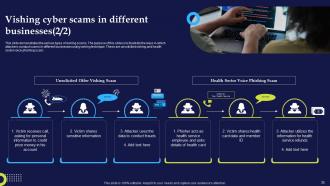
Slide 34: This slide demonstrates the various types of vishing scams and illustrate the ways in which attackers conduct scams in different businesses using vishing technique.
Slide 35: This slide also demonstrates the various types of vishing scams and illustrate the ways in which attackers conduct scams in different businesses using vishing technique.
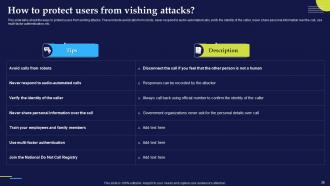
Slide 36: This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls etc.
Slide 37: This slide presents about the techniques which can help in protecting organizations from phishing and vishing attacks.
Slide 38: This slide shows title for topics that are to be covered next in the template.
Slide 39: This slide talks about the smishing cyber attacks conducted by sending text messages to the targets.
Slide 40: This slide displays various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams.
Slide 41: This slide talks about the various types of smishing cyber attacks and explain different techniques of smishing scams used by the attackers to scam users.
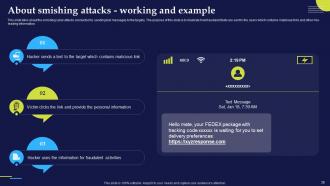
Slide 42: This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations.
Slide 43: This slide shows title for topics that are to be covered next in the template.
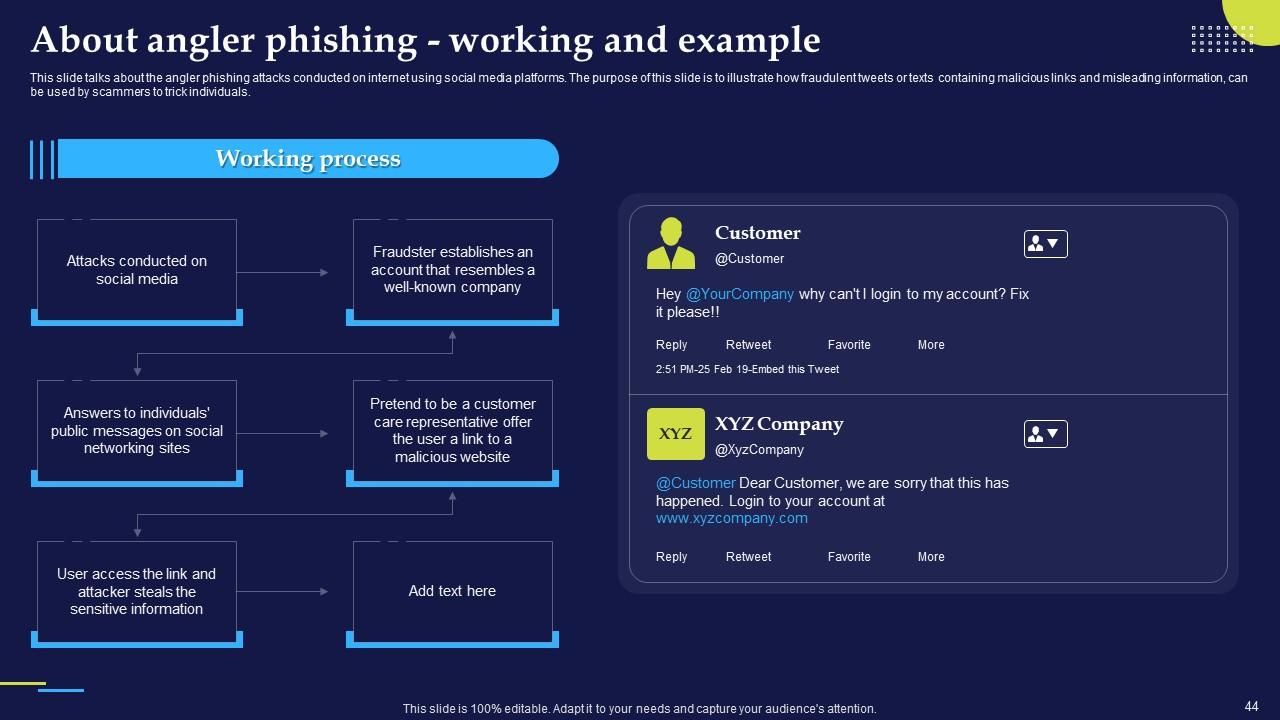
Slide 44: This slide talks about the angler phishing attacks conducted on internet using social media platforms.
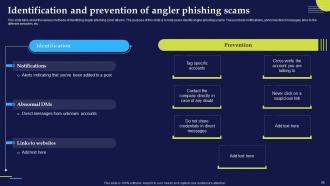
Slide 45: This slide displays various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams.
Slide 46: This slide shows title for topics that are to be covered next in the template.
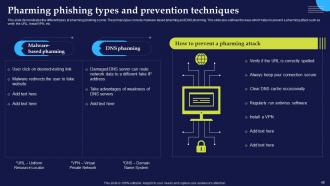
Slide 47: This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams.
Slide 48: This slide demonstrates the different types pf pharming phishing scams. The primary types include malware-based pharming and DNS pharming.
Slide 49: This slide shows title for topics that are to be covered next in the template.
Slide 50: This slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets.
Slide 51: This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks.
Slide 52: This slide shows title for topics that are to be covered next in the template.
Slide 53: This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations.
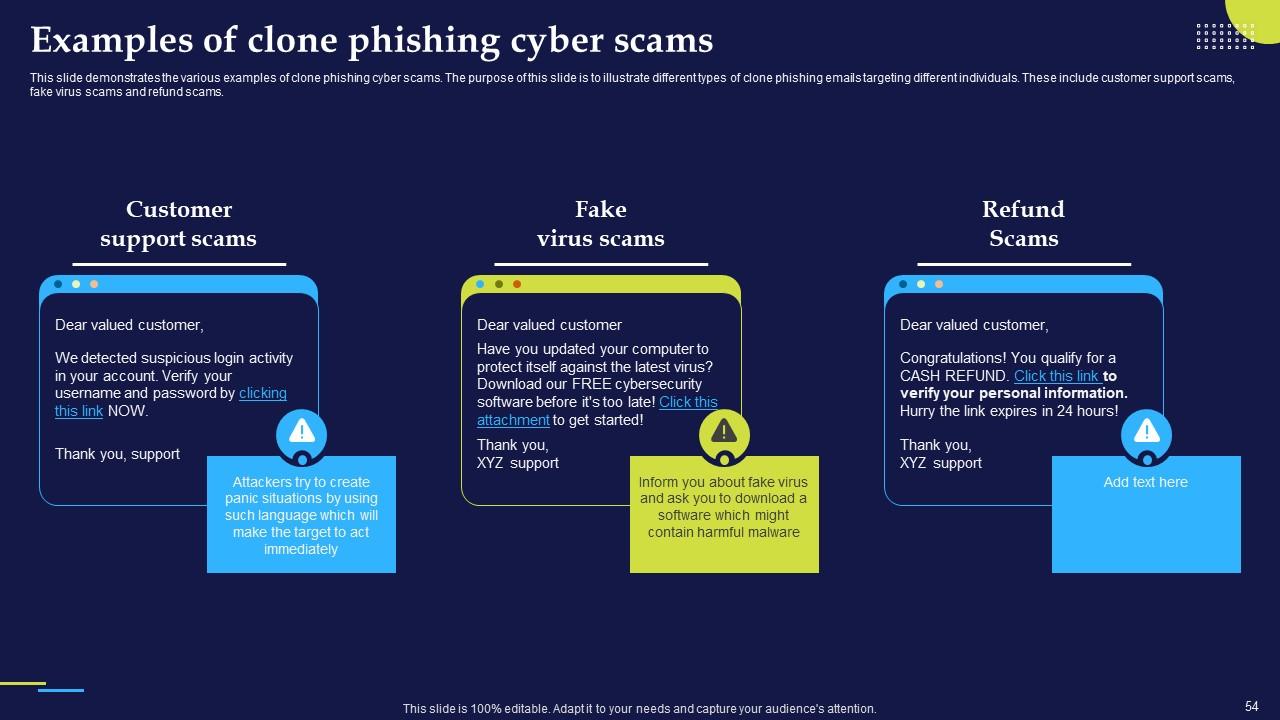
Slide 54: This slide demonstrates the various examples of clone phishing cyber scams.
Slide 55: This slide talks about the various steps that can be taken to prevent clone phishing attacks.
Slide 56: This slide shows title for topics that are to be covered next in the template.
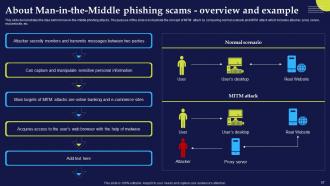
Slide 57: This slide demonstrates the idea behind man-in-the-middle phishing attacks.
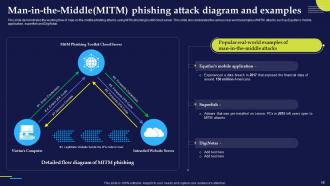
Slide 58: This slide displays the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server.
Slide 59: This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams.
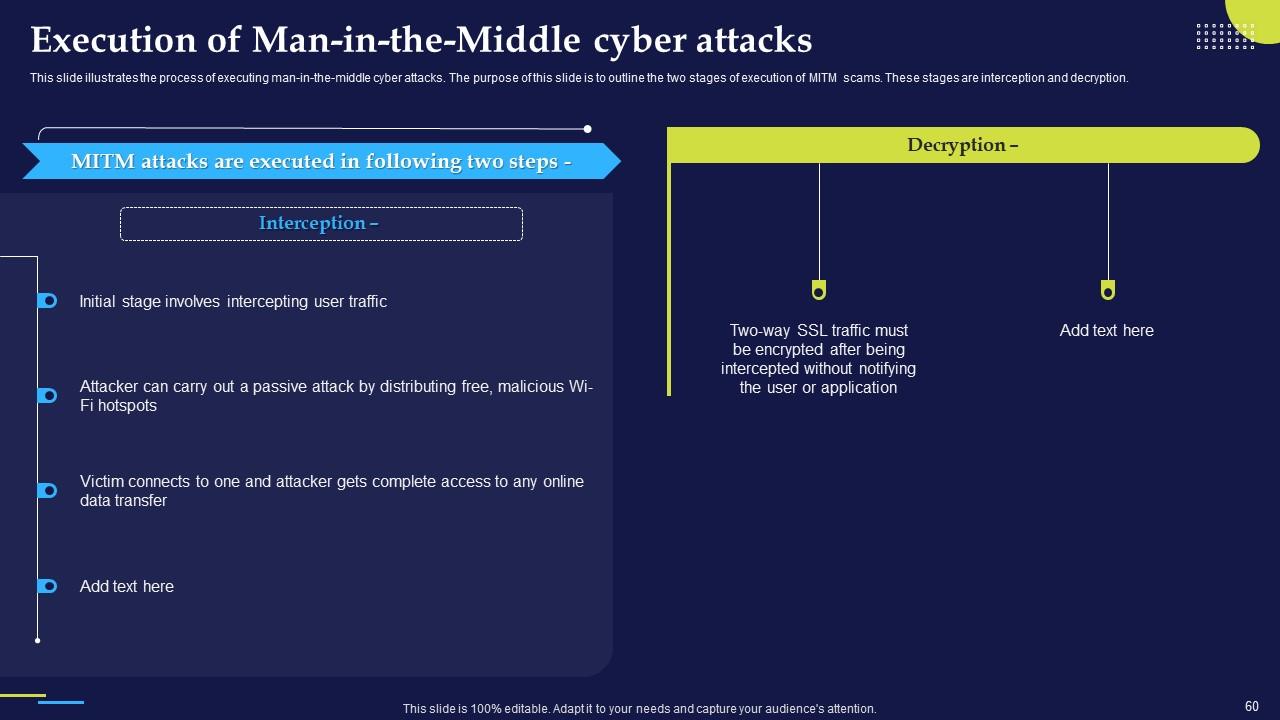
Slide 60: This slide illustrates the process of executing man-in-the-middle cyber attacks.
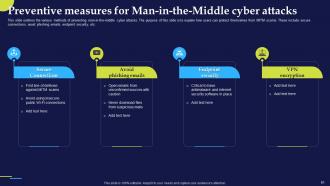
Slide 61: This slide outlines the various methods of preventing man-in-the-middle cyber attacks.
Slide 62: This slide shows title for topics that are to be covered next in the template.
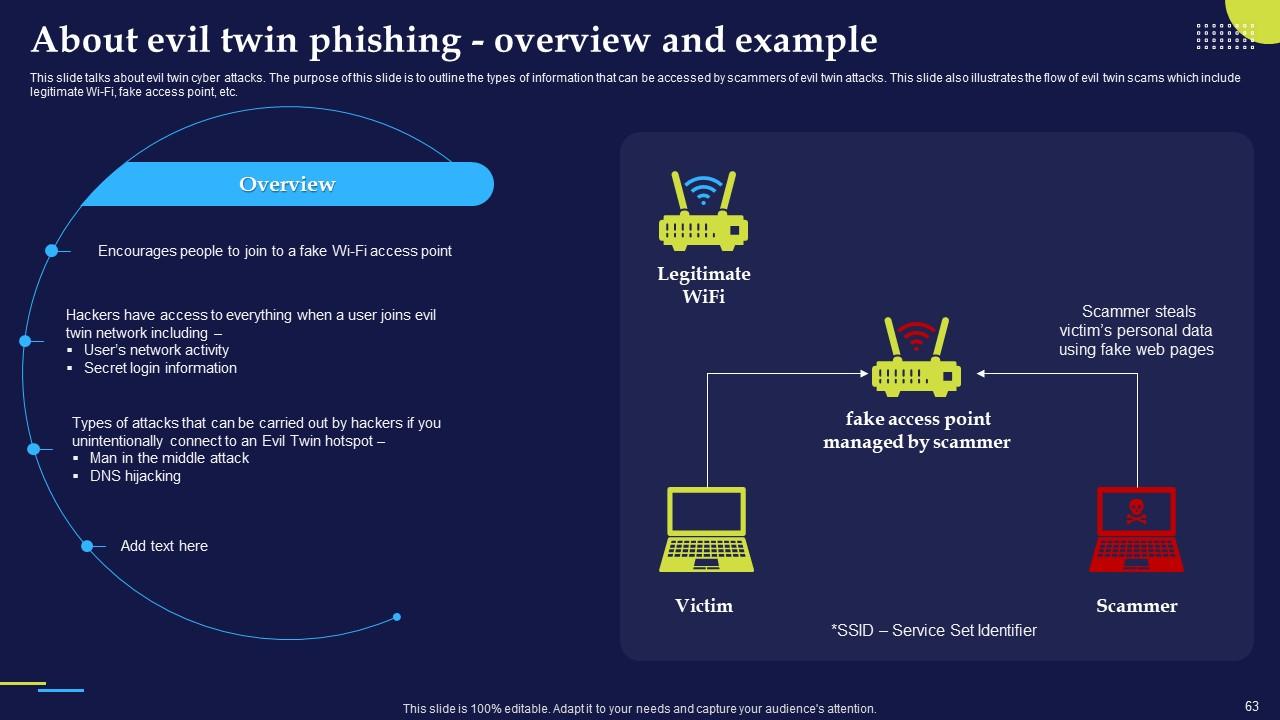
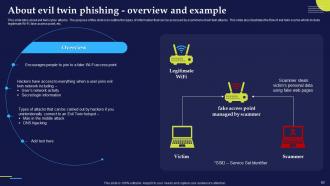
Slide 63: This slide talks about evil twin cyber attacks and outline the types of information that can be accessed by scammers of evil twin attacks.
Slide 64: This slide represents the working of evil twin phishing attacks. The key points include set up evil twin fake access point, set up a fake captive portal etc.
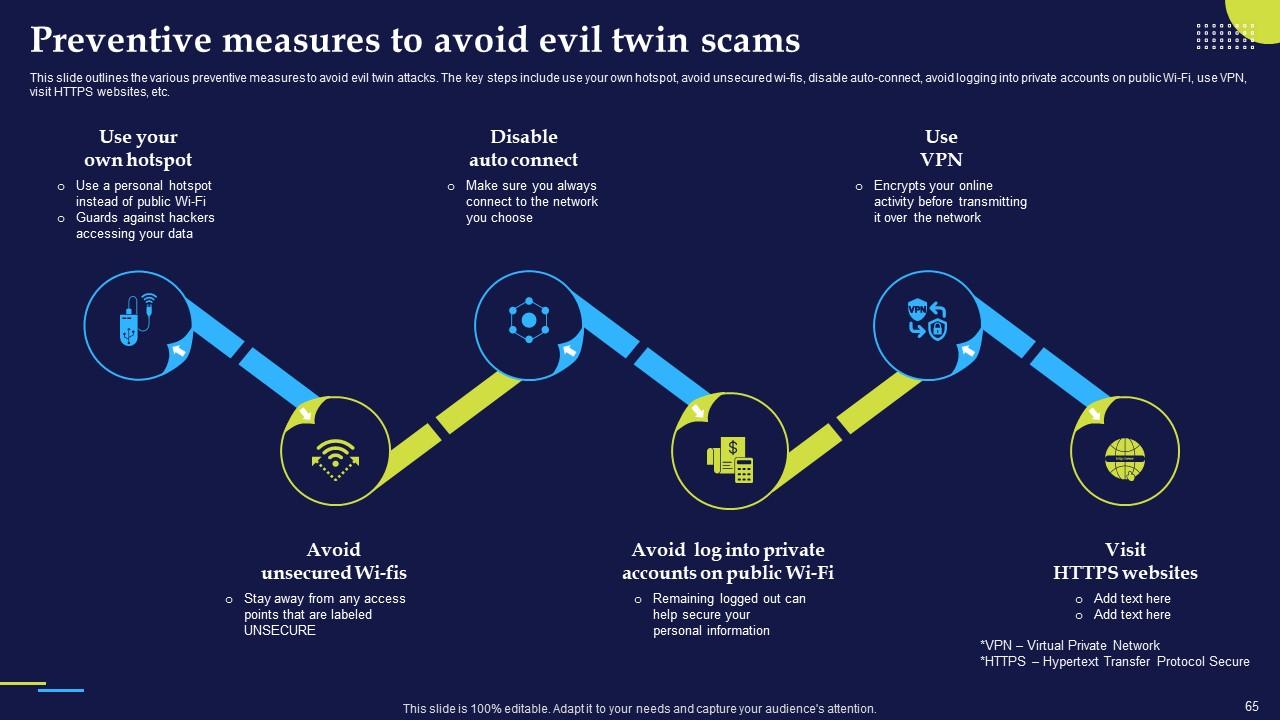
Slide 65: This slide outlines the various preventive measures to avoid evil twin attacks. The key steps include use your own hotspot, avoid unsecured wi-fis etc.
Slide 66: This slide shows title for topics that are to be covered next in the template.
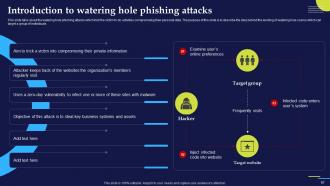
Slide 67: This slide talks about the watering hole phishing attacks which trick the victim to do activities compromising their personal data.
Slide 68: This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams.
Slide 69: This slide demonstrates the techniques used by scammers to conduct watering hole attacks.
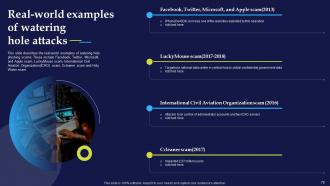
Slide 70: This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam etc.
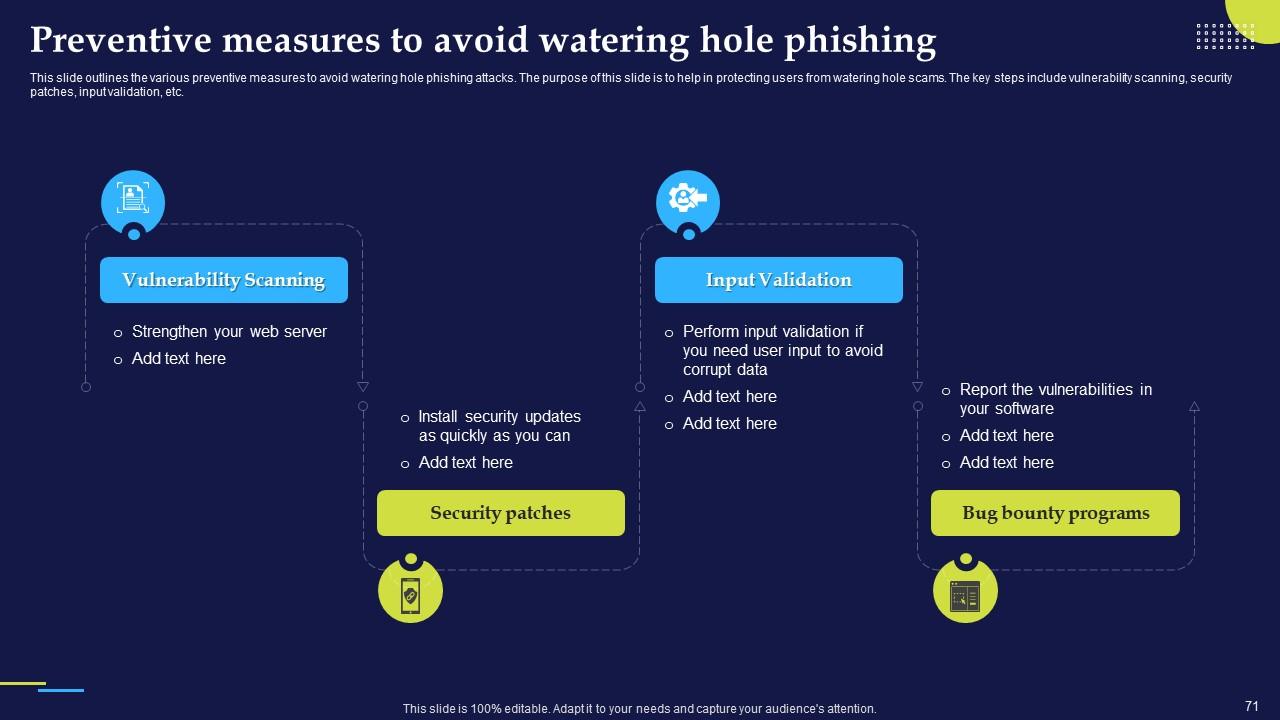
Slide 71: This slide outlines the various preventive measures to avoid watering hole phishing attacks.
Slide 72: This slide shows title for topics that are to be covered next in the template.
Slide 73: This slide talks about search engine phishing scams and explain how phishers use their own-built websites to trick victims.
Slide 74: This slide describes various tricks utilized by fraudulent websites to scam the visitors.
Slide 75: This slide shows title for topics that are to be covered next in the template.
Slide 76: This slide talks about the major crime committed by phishers named as identity theft.
Slide 77: This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams.
Slide 78: This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link etc.
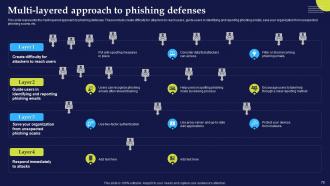
Slide 79: This slide represents the multi-layered approach to phishing defenses.
Slide 80: This slide shows title for topics that are to be covered next in the template.
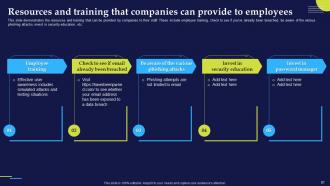
Slide 81: This slide demonstrates the resources and training that can be provided by companies to their staff.
Slide 82: This slide shows title for topics that are to be covered next in the template.
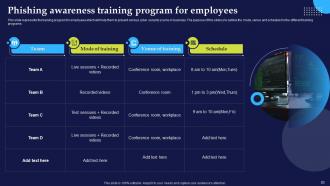
Slide 83: This slide represents the training program for employees which will help them to prevent various cyber security scams in business.
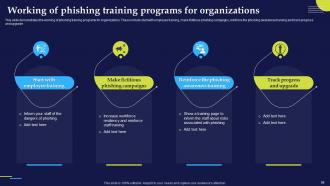
Slide 84: This slide demonstrates the working of phishing training programs for organizations.
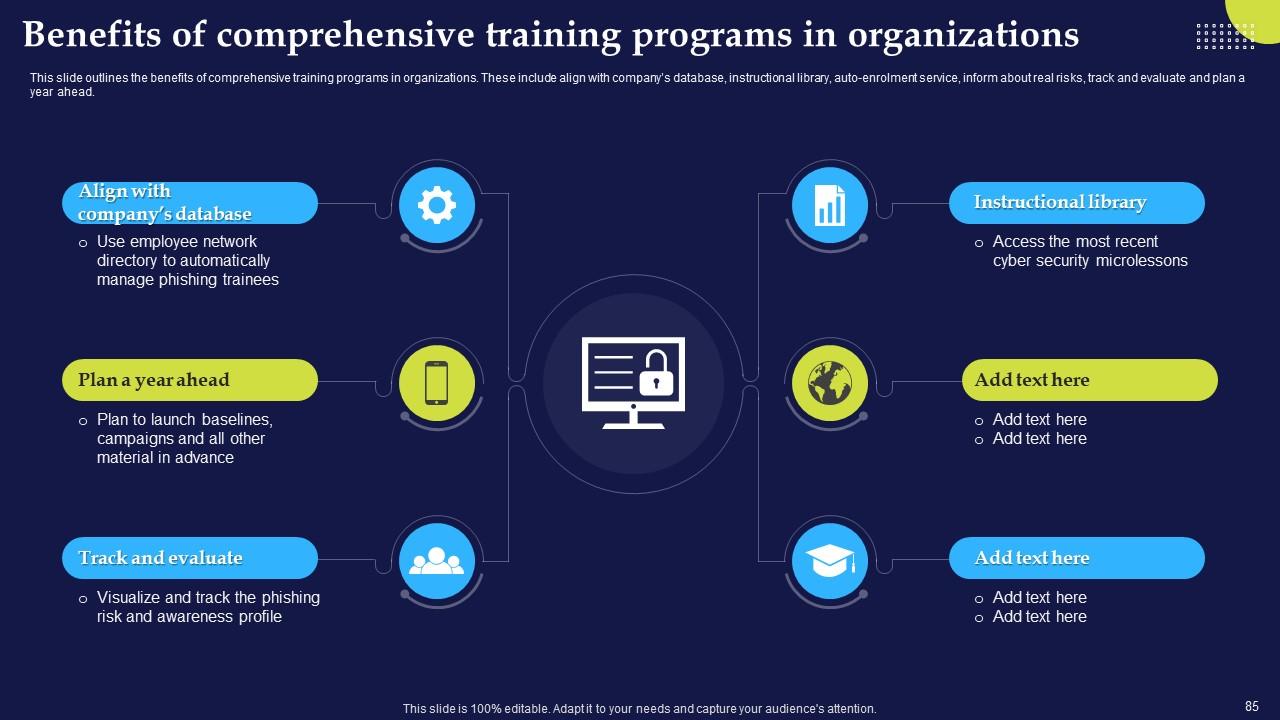
Slide 85: This slide outlines the benefits of comprehensive training programs in organizations.
Slide 86: This slide talks about the measures for successful phishing awareness campaign.
Slide 87: This slide shows title for topics that are to be covered next in the template.
Slide 88: This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks.
Slide 89: This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks.
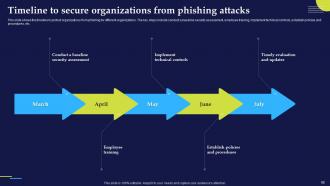
Slide 90: This slide shows the timeline to protect organizations from phishing for different organizations.
Slide 91: This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training etc.
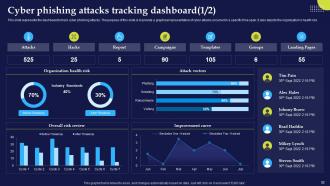
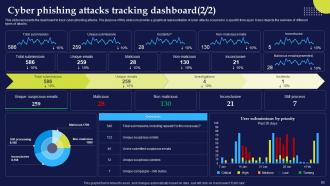
Slide 92: This slide presents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks.
Slide 93: This slide also represents the dashboard to track cyber phishing attacks and provide a graphical representation of cyber attacks occurred in a specific time span.
Slide 94: This slide shows all the icons included in the presentation.
Slide 95: This is a Thank You slide with address, contact numbers and email address.
Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides with all 104 slides:
Use our Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
I was confident and well prepared for my presentation for the first time ever. With SlideTeam’s templates, I could deliver one of my best presentations. Will be coming back for more!
-
SlideTeam provides PPTs on every single topic. Their templates suit my job very well. I am very grateful!