Powerpoint Templates and Google slides for Types Of Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Types Of Cryptojacking In Cybersecurity Training Ppt
Types Of Cryptojacking In Cybersecurity Training PptPresenting Types of Cryptojacking in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Types Of Adware In Cybersecurity Training Ppt
Types Of Adware In Cybersecurity Training PptPresenting Types of Adware in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Types Of Application Security In Cybersecurity Training Ppt
Types Of Application Security In Cybersecurity Training PptPresenting Types of Application Security in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS
Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT botnet attacks. Bruce force attack, Phishing, Device Bricking, and Cryptocurrency Mining are the most common types which are outlined in slide. Present the topic in a bit more detail with this Most Common Types Of IoT Botnet Attacks Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Bricking, Mining. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various types of ransomware attack which can cause financial loss to company. It covers information about Scareware, Screen Lockers, DDoS Distributed Denial of Service Extortion, Encrypting Ransomware, etc. Deliver an outstanding presentation on the topic using this Most Common Types Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Scareware, Lockers, Mobile using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline multiple types of Denial of Service Dos attack. It covers information about application layer, buffer overflow, DNS Domain Name Server amplification, and ping of death. Deliver an outstanding presentation on the topic using this Various Types Of Dos Attack Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Application, Layer, Death using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate multiple types of Internet of Things IoT password attack. Phishing, Dictionary Attack, Credential Stuffing, and Keyloggers are the major attacks which are mentioned in slide. Present the topic in a bit more detail with this Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Dictionary, Credential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V
Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS V
Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Introducing Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS V to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Client Honeyspot, Malware Honeypots using this template. Grab it now to reap its full benefits.
-
 Types Of Cybersecurity Attacks In Education
Types Of Cybersecurity Attacks In EducationThis slide depicts the types of cybersecurity attacks in education. This slide aims to help education businesses adopt suitable measures to prevent cyberattacks. It includes a graphical analysis and key insights Introducing our Types Of Cybersecurity Attacks In Education set of slides. The topics discussed in these slides are Cyberattacks In Education, Education Is Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS
Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SSThis slide major types of encryption technology, focused on improving data privacy and security of todays business. It provides details about symmetric, asymmetric, RSA, data encryption standard, etc. Introducing Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Encryption, Asymmetric Encryption, RSA Encryption, using this template. Grab it now to reap its full benefits.
-
 Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Introducing Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Software, Financial, Results, using this template. Grab it now to reap its full benefits.
-
 Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase different types of Internet of Things IoT security software. Identity and access management, antivirus software, firewall software, intrusion detection system, and data loss prevention are some of the major tools which are outlined in slide. Introducing Various Types Of IoT Security Tools Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Software, System, using this template. Grab it now to reap its full benefits.
-
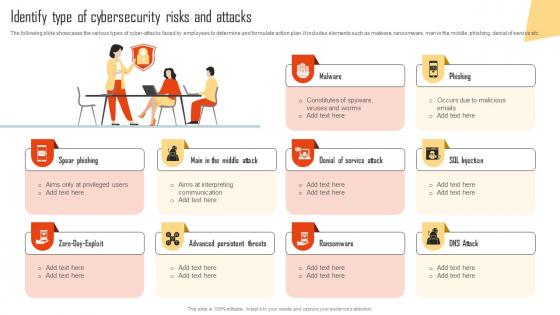 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Comparative Analysis Of Various Types Of Blockchain Network BCT SS V
Blockchain And Cybersecurity Comparative Analysis Of Various Types Of Blockchain Network BCT SS VThe following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Introducing Blockchain And Cybersecurity Comparative Analysis Of Various Types Of Blockchain Network BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Public Blockchain, Private Blockchain, Consortium Blockchain using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V
Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS VThe following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Various Types Of Ddos Attacks Impacting Internet Traffic BCT SS V This template helps you present information on Four stages. You can also present information on Volumetric Attacks, Protocol Attacks, Application Attacks, Fragmentation Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Type Of Attack Cryptography In Cybersecurity
Type Of Attack Cryptography In CybersecurityThis slide covers various attacks on cybersecurity and provides details about to identity threads on organizations. It includes elements such as chosen plaintext, key, and algorithm, etc. Presenting our set of slides with Type Of Attack Cryptography In Cybersecurity. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Brute Force Attack, Key And Algorithm Attack, Known Plaintext Attack.
-
 Various Types Of Cryptography In Cybersecurity
Various Types Of Cryptography In CybersecurityThis slide covers categories of cybersecurity cryptography and details how the company can secure the data. It includes elements such as harsh functions, symmetric keys, etc. Introducing our premium set of slides with Various Types Of Cryptography In Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Symmetric Key Cryptography, Hash Functions, Asymmetric Key Cryptography. So download instantly and tailor it with your information.
-
 Crucial Types Of Firewall In Cybersecurity
Crucial Types Of Firewall In CybersecurityThis slide showcases the major types of firewall in cybersecurity which helps an organization to provide proactive protection and enable users for safely surf over the internet. It include details such as packet filtering, proxy service firewall, stateful inspection firewall, etc. Introducing our premium set of slides with Crucial Types Of Firewall In Cybersecurity. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Packet Filtering, Stateful Inspection Firewall, Proxy Service Firewall . So download instantly and tailor it with your information.
-
 Types Of Maritime Cybersecurity Attacks On Sensitive Data
Types Of Maritime Cybersecurity Attacks On Sensitive DataThis slide showcases various types of cybersecurity attacks on sensitive data. The main purpose of this template is to highlight various types of attacks, such as phishing attacks, supply chain attacks, data theft, and IoT device exploitation. Presenting our set of slides with Types Of Maritime Cybersecurity Attacks On Sensitive Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IOT Device Exploitation, Supply Chain Attacks, Phishing Attacks.
-
 Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SS
Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SSThis slide showcases types of internet of things IoT security along with its brief explanation, referable for companies dealing with related vulnerabilities. It provides details about communication attacks, lifecycle attacks, etc. Increase audience engagement and knowledge by dispensing information using Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on four stages. You can also present information on Communication Attacks, Lifecycle Attacks, Physical Attacks, Internet Of Things Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Types Of Cybersecurity Policy To Protect Data
Major Types Of Cybersecurity Policy To Protect DataThis slide showcases the important types of cybersecurity policy securing sensitive information which helps an organization to regulate compliance and ensure providing better data management. It include details such as account management, anti-virus, email policy, etc. Presenting our set of slides with Major Types Of Cybersecurity Policy To Protect Data This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Systems Acceptable Use Policy, Account Management Policy
-
 Types Of Cybersecurity Ethical Issues Affecting Data Protection
Types Of Cybersecurity Ethical Issues Affecting Data ProtectionThis slide represents various actions to mitigate multiple cybersecurity ethical issues assisting companies to enhance corporate and customer data protection. It includes issues such as harm to privacy, harm to property, transparency, etc. Presenting our well structured Types Of Cybersecurity Ethical Issues Affecting Data Protection. The topics discussed in this slide are Details, Actions By Professional, Priority. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS
Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Mobile Threat Defense, Endpoint Protection Platform, Advanced Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a comprehensive training plan to help employees effectively identify various types of phishing attacks, including deceptive phishing, spear phishing, whaling, vishing and smishing.Deliver an outstanding presentation on the topic using this Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Sessions, Training Hours, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And Vulnerability
Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And VulnerabilityFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Deliver an outstanding presentation on the topic using this Identifying The Origin And Type Of Cyber Incident Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Web, Email, Removable Media using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response Playbook
Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response PlaybookFollowing slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Present the topic in a bit more detail with this Identifying The Origin And Type Of Cyber Incident Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Effectively, Information, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types of information security controls to strengthen cybersecurity
Types of information security controls to strengthen cybersecurityIntroducing our premium set of slides with Types Of Information Security Controls To Strengthen Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preventative Controls, Detective Controls, Corrective Controls. So download instantly and tailor it with your information.



