Powerpoint Templates and Google slides for Threat Source
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Sources For Cyber Threat Intelligence During Cybersecurity
Sources For Cyber Threat Intelligence During CybersecurityThis slide showcases the sources for cyber threat intelligence during cyber security. The purpose of this slide is to establish rigid security through the use of cyber threat intelligence. It includes open source intelligence, internal intelligence, etc. Presenting our well structured Sources For Cyber Threat Intelligence During Cybersecurity The topics discussed in this slide are CTI Information Source, Description, Examples This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Addressing internal and external sources cyber threat management workplace
Addressing internal and external sources cyber threat management workplaceThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Increase audience engagement and knowledge by dispensing information using Addressing Internal And External Sources Cyber Threat Management Workplace. This template helps you present information on three stages. You can also present information on Internal Sources, External Sources, Targeted Intelligence, Malware Intelligence, Reputation Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Threat management for organization critical addressing internal and external sources of threat data gathering
Threat management for organization critical addressing internal and external sources of threat data gatheringThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Present the topic in a bit more detail with this Threat Management For Organization Critical Addressing Internal And External Sources Of Threat Data Gathering. Use it as a tool for discussion and navigation on Targeted Intelligence, Malware Intelligence, Reputation Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace A Internal And External Sources Threat Data Gathering
Vulnerability Administration At Workplace A Internal And External Sources Threat Data GatheringThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Present the topic in a bit more detail with this Vulnerability Administration At Workplace A Internal And External Sources Threat Data Gathering. Use it as a tool for discussion and navigation on Sources, Intelligence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
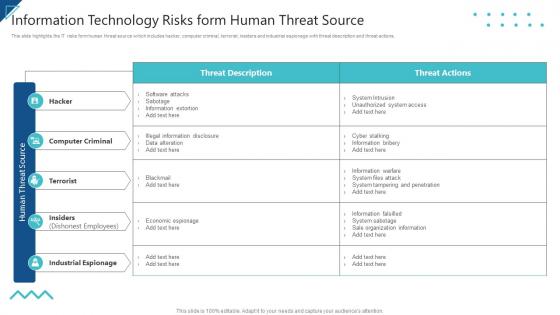
 IT Risk Management Strategies Information Technology Risks Form Human Threat Source
IT Risk Management Strategies Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this IT Risk Management Strategies Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action
IT Risk Management Strategies IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Information Technology Risks Form Human Threat Source
Enterprise Risk Management Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Enterprise Risk Management Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management IT Vulnerabilities With Threat Source And Action
Enterprise Risk Management IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this Enterprise Risk Management IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems
IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology SystemsThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems
Information Technology Risks Form Human Threat Source Risk Assessment Of It SystemsThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Information, Technology, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction
It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides IntroductionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction. Use it as a tool for discussion and navigation on Vulnerabilities, Source, Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Protection Sources Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Protection Sources Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat protection sources colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Protection Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Protection Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat protection sources monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat sources colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat sources monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Virus Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Virus Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Virus threat sources colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Virus Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Virus Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Virus threat sources monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cyber Threat Intelligence Data Sources For Analytics
Cyber Threat Intelligence Data Sources For AnalyticsThis slide provides a brief description of cyber threat intelligence data sources used in analytics to detect key threats and enable businesses to gain protection against cyber threats. It covers aspects such as data sources, description, types of source, best fit and benefits. Presenting our well structured Cyber Threat Intelligence Data Sources For Analytics. The topics discussed in this slide are Internal Intelligence, Counter Intelligence, Human Intelligence. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Open source data icons slide gears threat ppt powerpoint presentation infographics good
Open source data icons slide gears threat ppt powerpoint presentation infographics goodPresenting this set of slides with name Open Source Data Icons Slide Gears Threat Ppt Powerpoint Presentation Infographics Good. The topics discussed in these slides are Business, Planning, Strategy, Marketing, Management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Open source threat intelligence tools ppt powerpoint presentation ideas graphics example cpb
Open source threat intelligence tools ppt powerpoint presentation ideas graphics example cpbPresenting this set of slides with name Open Source Threat Intelligence Tools Ppt Powerpoint Presentation Ideas Graphics Example Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Open Source Threat Intelligence Tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Sources threat intelligenc security teams ppt powerpoint presentation portfolio clipart cpb
Sources threat intelligenc security teams ppt powerpoint presentation portfolio clipart cpbPresenting this set of slides with name Sources Threat Intelligenc Security Teams Ppt Powerpoint Presentation Portfolio Clipart Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Sources Threat Intelligenc Security Teams to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber threat intelligence sources ppt powerpoint presentation icon styles cpb
Cyber threat intelligence sources ppt powerpoint presentation icon styles cpbPresenting this set of slides with name Cyber Threat Intelligence Sources Ppt Powerpoint Presentation Icon Styles Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Threat Intelligence Sources to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber threat intelligence sources ppt powerpoint presentation infographic template graphic images cpb
Cyber threat intelligence sources ppt powerpoint presentation infographic template graphic images cpbPresenting this set of slides with name Cyber Threat Intelligence Sources Ppt Powerpoint Presentation Infographic Template Graphic Images Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Cyber Threat Intelligence Sources to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 External threat intelligence sources ppt powerpoint presentation professional guidelines cpb
External threat intelligence sources ppt powerpoint presentation professional guidelines cpbPresenting this set of slides with name External Threat Intelligence Sources Ppt Powerpoint Presentation Professional Guidelines Cpb. This is an editable Powerpoint four stages graphic that deals with topics like External Threat Intelligence Sources to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Threat intelligence sources ppt powerpoint presentation outline display cpb
Threat intelligence sources ppt powerpoint presentation outline display cpbPresenting our Threat Intelligence Sources Ppt Powerpoint Presentation Outline Display Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Threat Intelligence Sources This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.



