Powerpoint Templates and Google slides for Threat Processing
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Threat Process Powerpoint PPT Template Bundles
Threat Process Powerpoint PPT Template BundlesDeliver a credible and compelling presentation by deploying this Threat Process Powerpoint PPT Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The thirteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Threat Process Powerpoint PPT Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Segmented Circle Training Development Process Opportunity Threat Weakness Strength
Segmented Circle Training Development Process Opportunity Threat Weakness StrengthThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Segmented Circle Training Development Process Opportunity Threat Weakness Strength and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Secops V2 Security Operations Threat Management Process
Secops V2 Security Operations Threat Management ProcessThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Deliver an outstanding presentation on the topic using this Secops V2 Security Operations Threat Management Process. Dispense information and present a thorough explanation of Extended Investigation, Preliminary Investigation, Security Operations Threat
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V
Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Cyber Threats In Blockchain Overview And Workflow Process Of Eclipse Attack BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Target Node, Attacker Nodes, Participating Nodes using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V
Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Working Process Of Ddos Attack BCT SS V This template helps you present information on Three stages. You can also present information on Internet Traffic, Perform Operations, Website Hostage using this PPT design. This layout is completely editable so personaize it now
-
 Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process
Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management ProcessThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Deliver an outstanding presentation on the topic using this Analyse And Rank Impact Of Cyber Threat Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Threat, Threat Source, Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process
Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management ProcessThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Present the topic in a bit more detail with this Identify Threat And Vulnerabilities Within Information Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process To Formulate Advanced Threat Protection Measures
Process To Formulate Advanced Threat Protection MeasuresThe purpose of the mentioned slide is to showcase various steps involved in creating advanced threat protection solutions. Presenting our set of slides with Process To Formulate Advanced Threat Protection Measures. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prepare, Report, Design.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Automated Threat Hunting Process
Benefits Of Automated Threat Hunting ProcessThis slide outlines the advantages of an automated threat-hunting process, such as minimizing labour-intensive tasks, improving skill advancement, etc. Introducing Benefits Of Automated Threat Hunting Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Improve Skill Advancement, Increase Productivity Measures, Show Return On Investment, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Perform Threat Hunting Process
Roadmap To Perform Threat Hunting ProcessThis slide outlines the roadmap for performing cyber threat hunting steps, such as defining objectives and scope, data collection and analysis, etc. Introducing Roadmap To Perform Threat Hunting Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Collection And Analysis, Hypothesis Generation And Testing, Investigation And Response, using this template. Grab it now to reap its full benefits.
-
 Steps Of Cyber Threat Hunting Process
Steps Of Cyber Threat Hunting ProcessThis slide outlines the main steps of the cyber threat hunting process, covering hypothesis, data collection, trigger, investigation, and response. Present the topic in a bit more detail with this Steps Of Cyber Threat Hunting Process. Use it as a tool for discussion and navigation on Hypothesis, Cyber Threat Hunting Process, Formulate Initial Ideas, Probe Potential Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Typical Cyber Threat Hunting Process
Typical Cyber Threat Hunting ProcessThis slide showcases the typical cyber threat hunting process, such as creating a hypothesis, conducting a search, validating, adjusting, and broadening the scope. Present the topic in a bit more detail with this Typical Cyber Threat Hunting Process. Use it as a tool for discussion and navigation on Respond To Incidents, Generate New Detection Content, Adjust And Broaden Scope, Create A Hypothesis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Process Of Cyber Threat Hunting
Working Process Of Cyber Threat HuntingThis slide outlines the working process model of cyber threat hunting, including layers such as IoC hunting, intelligence-based hunting, post-incident, etc. Present the topic in a bit more detail with this Working Process Of Cyber Threat Hunting. Use it as a tool for discussion and navigation on Indicators Of Compromise Hunting, Incident Hunting, Anomaly Detections, Infection Readiness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process of threat risk modeling presentation pictures
Process of threat risk modeling presentation picturesPresenting process of threat risk modeling presentation pictures. This is a process of threat risk modeling presentation pictures. This is a six stage process. The stages in this process are identify vulnerabilities, decompose application, risk, application overview, possibility, impact, farming.
-
 Process of threat risk modeling diagram powerpoint images
Process of threat risk modeling diagram powerpoint imagesPresenting process of threat risk modeling diagram powerpoint images. This is a process of threat risk modeling diagram powerpoint images. This is a five stage process. The stages in this process are risk, impact, degree of mitigating, exploitability, damage potential, possibility, identify vulnerabilities, application overview, identify threats, decompose application.
-
 Costs incurred to process faulty minimize cybersecurity threats in healthcare company
Costs incurred to process faulty minimize cybersecurity threats in healthcare companyThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Faulty Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.v
-
 Threat and dashboard effective information security risk management process
Threat and dashboard effective information security risk management processFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Threat And Dashboard Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Security Recommendation, Security Controls, Active Remediation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining security threats effective information security risk management process
Defining security threats effective information security risk management processThis slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.Introducing Defining Security Threats Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Natural Disaster, Environmental Control Failures, Deliberate Software Attacks, using this template. Grab it now to reap its full benefits.
-
 Mitigation plan for threat effective information security risk management process
Mitigation plan for threat effective information security risk management processMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver an outstanding presentation on the topic using this Mitigation Plan For Threat Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Resources Required, Expected Resolution Time, Communication Mode using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat assessment effective information security risk management process
Threat assessment effective information security risk management processFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Threat Assessment Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Affected Asset, Potential Vulnerability, Vulnerability Ranking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat hunting program with process and tools
Cyber threat hunting program with process and toolsThe following slide highlights the cyber threat hunting program including people, process and with four different levels to minimize risks and threats. Introducing our Cyber Threat Hunting Program With Process And Tools set of slides. The topics discussed in these slides are Cyber Threat Hunting, Cyber Security Tool, Cyber Threat Training. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Automating threat identification management logging process
Automating threat identification management logging processThis slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Introducing Automating Threat Identification Management Logging Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Management, Process, using this template. Grab it now to reap its full benefits.
-
 Threat Intelligence Technical Assessment Process
Threat Intelligence Technical Assessment ProcessThis slide represents the process of technical assessment based on threat intelligence. It steps include planning, data collection, processing, analysis, dissemination and feedback. Introducing our premium set of slides with Threat Intelligence Technical Assessment Process. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Processing, Dissemination, Data Collection, Analysis, Feedback. So download instantly and tailor it with your information.
-
 Major Threats in Business Relocation Process
Major Threats in Business Relocation ProcessThe following slide highlights the key risks in relocating business to assess the threat and formulate mitigation strategies accordingly. It includes elements such as customer loss, startup cost, workforce issues, business disturbances etc. Introducing our premium set of slides with Major Threats in Business Relocation Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Business Disturbances, Workforce Issue, Startup Cost. So download instantly and tailor it with your information.
-
 Insider Threat Protection Process With Defensive Controls
Insider Threat Protection Process With Defensive ControlsThis slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Introducing our premium set of slides with Insider Threat Protection Process With Defensive Controls. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recruitment, Scouting, Collection, Elimination. So download instantly and tailor it with your information.
-
 Process Flow For Detecting Insider Threat
Process Flow For Detecting Insider ThreatThis slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Introducing our Process Flow For Detecting Insider Threat set of slides. The topics discussed in these slides are Process Flow, Detecting Insider Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Product Planning Process Risk Management Plan To Mitigate Threats
Product Planning Process Risk Management Plan To Mitigate ThreatsThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Present the topic in a bit more detail with this Product Planning Process Risk Management Plan To Mitigate Threats. Use it as a tool for discussion and navigation on Risk Description, Mitigation Actions, Medium, Low, High. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managed Security Service Threat Detection Process
Managed Security Service Threat Detection ProcessThe following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Introducing our premium set of slides with Managed Security Service Threat Detection Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Event Resolution, Operational Readiness Review, Email Notification, Security Analysis. So download instantly and tailor it with your information.
-
 Best Practices For Threat Modeling Process
Best Practices For Threat Modeling ProcessThis slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method. Presenting our set of slides with name Best Practices For Threat Modeling Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Documentation, Threat Modeling, Suitable Method.
-
 Business Application Threat Modeling Process
Business Application Threat Modeling ProcessThis slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Introducing our premium set of slides with name Business Application Threat Modeling Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine, Security Profiles, Recommendations, Data Flow. So download instantly and tailor it with your information.
-
 Business Threat Modeling Process Icon
Business Threat Modeling Process IconPresenting our set of slides with name Business Threat Modeling Process Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Threat, Modeling, Process Icon.
-
 Cyber Threat Prevention And Security Process
Cyber Threat Prevention And Security ProcessThis slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Introducing our premium set of slides with name Cyber Threat Prevention And Security Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Perimeter, Smart Network Segmentation, Determine And Control. So download instantly and tailor it with your information.
-
 Five Step Process Of Cyber Threat Hunting
Five Step Process Of Cyber Threat HuntingThis slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Presenting our set of slides with name Five Step Process Of Cyber Threat Hunting. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hypothesis, Trigger, Resolution, Investigation.
-
 Insider Threat Mitigation And Protection Process
Insider Threat Mitigation And Protection ProcessThis slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage. Introducing our premium set of slides with name Insider Threat Mitigation And Protection Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Detect, Manage, Assess, Define. So download instantly and tailor it with your information.
-
 Key Steps Of Threat Modelling Process
Key Steps Of Threat Modelling ProcessThis slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate. Presenting our set of slides with name Key Steps Of Threat Modelling Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualize, Validate, Analyse Risks, Mitigate.
-
 Process To Conduct Business Threat Assessment
Process To Conduct Business Threat AssessmentThis slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response. Introducing our premium set of slides with name Process To Conduct Business Threat Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Examine Threats, Determine Threats, Develop Controls. So download instantly and tailor it with your information.
-
 Steps For Cyber Threat Intelligence Process
Steps For Cyber Threat Intelligence ProcessThis slide shows cyber threat intelligence process that helps business to prevent from threats. It include steps such as direction, collection, processing, analysis, dissemination, feedback. Presenting our set of slides with name Steps For Cyber Threat Intelligence Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Dissemination, Analysis, Processing, Collection.
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Threat Modelling Process Of Cyber Security Program
Threat Modelling Process Of Cyber Security ProgramThis slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case. Presenting our set of slides with name Threat Modelling Process Of Cyber Security Program. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Modelling, Cyber Security, Assess Residual Risk .
-
 Threats And Vulnerability Management Program Process
Threats And Vulnerability Management Program ProcessThis slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting our set of slides with Threats And Vulnerability Management Program Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identifying Vulnerabilities, Treating Vulnerabilities, Evaluating Vulnerabilities.
-
 Industrial Blockchain Threat Detection Process Flow
Industrial Blockchain Threat Detection Process FlowThis slide showcases industrial blockchain risk identification process flow. It provides information about designer, blockchain, bad actor, manufacturer, software, fingerprint, etc. Presenting our well structured Industrial Blockchain Threat Detection Process Flow. The topics discussed in this slide are Designer, Blockchain, Manufacturer. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
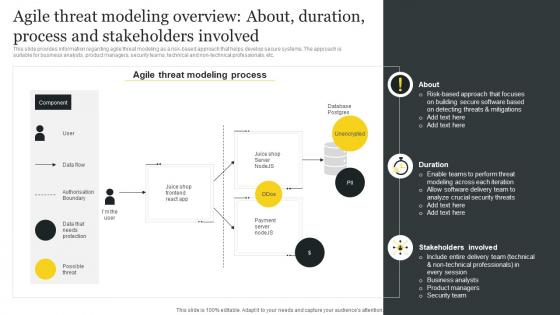 Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process
Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process. Use it as a tool for discussion and navigation on Stakeholders Involved, Duration, Agile Threat, Modeling Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook
Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook. Use it as a tool for discussion and navigation on Overview, Process, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Responsible Organization Agile Threat Modeling Overview About Duration Process
Building Responsible Organization Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Building Responsible Organization Agile Threat Modeling Overview About Duration Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agile Threat Modeling Overview, Stakeholders Involved, Security Teams, Technical And Non Technical Professionals , using this template. Grab it now to reap its full benefits.
-
 Corporate Cyber Threat Intelligence Process
Corporate Cyber Threat Intelligence ProcessThis slide depicts cyber threat intelligence process for improving the overall security posture of the organization, by providing actionable intelligence about the threats. It includes phases such as set, gather, analyse and act. Introducing our Corporate Cyber Threat Intelligence Process set of slides. The topics discussed in these slides are Act, Analyze, Gather. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Digital Safety Control Threat Modeling Process Flowchart
Digital Safety Control Threat Modeling Process FlowchartThis slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Introducing our Digital Safety Control Threat Modeling Process Flowchart set of slides. The topics discussed in these slides are Process, Flowchart, Attack Probability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SecOps Security Operations Threat Management Process Ppt Professional
SecOps Security Operations Threat Management Process Ppt ProfessionalThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Present the topic in a bit more detail with this SecOps Security Operations Threat Management Process Ppt Professional. Use it as a tool for discussion and navigation on External Threat Intelligance, Behavioral Analytics . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
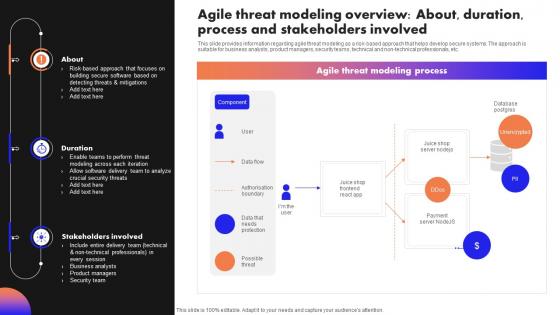 Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process
Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process. Dispense information and present a thorough explanation of Database Postgres, Unencrypted, Stakeholders Involved, Crucial Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools
Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech ToolsThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Playbook For Responsible Tech Tools. Use it as a tool for discussion and navigation on Agile Threat Modeling Process, Stakeholders Involved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook
Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Agile Threat Modeling Overview About Duration Process Manage Technology Interaction With Society Playbook to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on bout, Duration, Stakeholders Involved, using this template. Grab it now to reap its full benefits.
-
 Business process workflow diagram examples avoid threats powerpoint slides 0515
Business process workflow diagram examples avoid threats powerpoint slides 0515Widescreen yield with no blunder of pixilation and obscured vision. Completely editable slide content. Customize the substance with organization name, trademark and logo. Easy to incorporate and prohibit information in slide foundation like PPT symbols, hues, introduction. Easy to download and good with fluctuated groups. Compatible with different on the web and disconnected programming alternatives. Significantly valuable PowerPoint slide by business people, understudies and educators.
-
 Business process workflow diagram examples beaware to face threats powerpoint slides 0515
Business process workflow diagram examples beaware to face threats powerpoint slides 0515We are proud to present our business process workflow diagram examples beaware to face threats powerpoint slides 0515. Be aware to face threats concepts is shown in this Power Point template. This template is can be used for different threat warning presentations .
-
 Process optimization cybersecurity strategy insider threat statistics fundraising cpb
Process optimization cybersecurity strategy insider threat statistics fundraising cpbPresenting this set of slides with name - Process Optimization Cybersecurity Strategy Insider Threat Statistics Fundraising Cpb. This is an editable seven stages graphic that deals with topics like Process Optimization, Cybersecurity Strategy, Insider Threat Statistics, Fundraising to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Human capital management process vulnerability threat management program cpb
Human capital management process vulnerability threat management program cpbPresenting this set of slides with name - Human Capital Management Process Vulnerability Threat Management Program Cpb. This is an editable five stages graphic that deals with topics like Human Capital Management Process, Vulnerability Threat Management Program to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Identification and analysis of disaster risks threats process ppt powerpoint presentation file influencers
Identification and analysis of disaster risks threats process ppt powerpoint presentation file influencersPresenting this set of slides with name Identification And Analysis Of Disaster Risks Threats Process Ppt Powerpoint Presentation File Influencers. This is a eight stage process. The stages in this process are Planning, Management, Marketing, Business, Strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Threat management process ppt powerpoint presentation ideas aids cpb
Threat management process ppt powerpoint presentation ideas aids cpbPresenting this set of slides with name Threat Management Process Ppt Powerpoint Presentation Ideas Aids Cpb. This is an editable Powerpoint two stages graphic that deals with topics like Threat Management Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.




