Powerpoint Templates and Google slides for Technology Abuse
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Threats Sybil Attack Poses To Blockchain Technology Training Ppt
Threats Sybil Attack Poses To Blockchain Technology Training PptPresenting Threats Sybil Attack Poses to Blockchain Technology. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Threat Technology Security Displaying Cybersecurity Companies
Threat Technology Security Displaying Cybersecurity CompaniesIntroduce your topic and host expert discussion sessions with this Threat Technology Security Displaying Cybersecurity Companies. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook
Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview Utilizing Technology Responsible By Product Developer Playbook. Use it as a tool for discussion and navigation on Stakeholders, Overview, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Playbook To Mitigate Negative Of Technology. Use it as a tool for discussion and navigation on Collaborate, Prioritization, Initiate Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology
Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of TechnologyThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Key Principles Associated With Agile Threat Modelling Playbook To Mitigate Negative Of Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values , using this template. Grab it now to reap its full benefits.
-
 In And Threat Vectors For Confidential Computing Confidential Computing System Technology
In And Threat Vectors For Confidential Computing Confidential Computing System TechnologyThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using In And Threat Vectors For Confidential Computing Confidential Computing System Technology. This template helps you present information on seven stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secops V2 Software Tools Based On Threats Ppt Icon Graphics Download
Secops V2 Software Tools Based On Threats Ppt Icon Graphics DownloadThis slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. Increase audience engagement and knowledge by dispensing information using Secops V2 Software Tools Based On Threats Ppt Icon Graphics Download. This template helps you present information on five stages. You can also present information on Network Detectin And Response, Anti Phishing, Data Discovery, Packet Level Visibility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
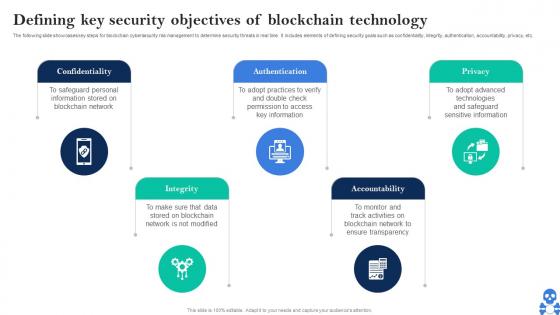 Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V
Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain How Hackers Attack Blockchain Technology BCT SS V
Cyber Threats In Blockchain How Hackers Attack Blockchain Technology BCT SS VThe following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. Introducing Cyber Threats In Blockchain How Hackers Attack Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain To Modify Data, Keys Or Passwords, Obtain System Accessibility using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Importance Of Cybersecurity In Blockchain Technology BCT SS V This template helps you present information on Four stages. You can also present information on Decentralized Architecture, Public Key Cryptography, Smart Contracts using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Major Cybersecurity Challenges In Blockchain Technology BCT SS V Use it as a tool for discussion and navigation on Challenges, Details, Impact This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V
Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Overview And Workflow Of Blockchain Cybersecurity Technology BCT SS V This template helps you present information on One stages. You can also present information on Node Validates Transaction, Existing Blockchain, Transaction Completed using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V
Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Cyber Threats In Blockchain Overview Of Phishing Attack In Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Opportunities, Fake Website, Data Breach using this template. Grab it now to reap its full benefits.
-
 Real Time Cyber Security Threat Monitoring Tools
Real Time Cyber Security Threat Monitoring ToolsThis slide showcases cyber security threat monitoring tool that helps in real-time spectating and identifies malicious behavior on network. It includes elements such as HoneyMap, Norse Map, Digital Attack Map, FireEye, Trend Micro and Akamai. Presenting our well structured Real Time Cyber Security Threat Monitoring Tools. The topics discussed in this slide are Visualization Tools, Real Time, Additional Features. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices To Overcome Smartphone Technology Security Threats
Best Practices To Overcome Smartphone Technology Security ThreatsThis slide represents best practices to overcome smartphone technology security threats which enhances smartphone security and prevents from malware and spyware attacks. It includes security threats such as downloadable applications threats, physical threats, etc. Presenting our set of slides with name Best Practices To Overcome Smartphone Technology Security Threats. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Downloadable Applications Threats, Network And Wi-Fi Security Threats, General Cyber Security Threats, Physical Threats.
-
 Comparing Advanced Threat Protection Tools
Comparing Advanced Threat Protection ToolsThe mentioned slide showcases a comparison of various advanced threat protection tools to protect systems crucial data. Presenting our well structured Comparing Advanced Threat Protection Tools. The topics discussed in this slide are Techniques, Security, Platforms. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparison Of Cybersecurity Apps For Threat Detection
Comparison Of Cybersecurity Apps For Threat DetectionThis slide represents comparison table for cybersecurity applications for online risk mitigation including Wireshark, Metasploit, and Entersoft apps. Introducing our premium set of slides with Comparison Of Cybersecurity Apps For Threat Detection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Protocol Analysis, Security Assessment, Infrastructure Security Analysis. So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Tools Comparative Analysis
Cyber Threat Intelligence Tools Comparative AnalysisThis slide showcases cyber threat intelligence tools which help in effective shield against data and allow proactively detect cyber threats. It includes elements such as Cisco umbrella, DeCYFIR, Echosec and GreyNoise. Presenting our well structured Cyber Threat Intelligence Tools Comparative Analysis. The topics discussed in this slide are Key Features, USP, Pricing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Structural Design Of Blockchain Technology On Security Threats
Structural Design Of Blockchain Technology On Security ThreatsIntroducing our Structural Design Of Blockchain Technology On Security Threats set of slides. The topics discussed in these slides are Application Layer, Contract Layer, Incentive Layer. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Features Of Cyber Threat Intelligence Tools
Features Of Cyber Threat Intelligence ToolsThis slide showcases the various characteristics of cyber threat intelligence tools such as data-driven, flexibility, comprehensiveness, etc. Introducing Features Of Cyber Threat Intelligence Tools to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on External Focused, Cyber Threat Intelligence Tools, Comprehensive, using this template. Grab it now to reap its full benefits.
-
 Primary Tools For Cyber Threat Intelligence
Primary Tools For Cyber Threat IntelligenceThis slide represents the various tools used for cyber threat intelligence along with their features and cost. Present the topic in a bit more detail with this Primary Tools For Cyber Threat Intelligence. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Isolated Browser, Data Collection Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Cyber Threat Hunting Tools
Effective Cyber Threat Hunting ToolsThis slide enlists effective cyber threat hunting tools, including managed detection and response, security information and event management, security analysis, etc. Deliver an outstanding presentation on the topic using this Effective Cyber Threat Hunting Tools. Dispense information and present a thorough explanation of Managed Detection And Response, Security Information, Event Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Deepfake Threat Detector Tools
Comparative Assessment Of Deepfake Threat Detector ToolsThe purpose of this slide is to help organizations deploy best deepfake detector tools to boost existing security. It compares tools on the basis of features, pricing and ratings. Presenting our well structured Comparative Assessment Of Deepfake Threat Detector Tools. The topics discussed in this slide are Sentinel, Features, Tools, Pricing, Ratings. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Deepfake Technology Threat Intrusion Framework
Deepfake Technology Threat Intrusion FrameworkThe purpose of this slide is to help businesses identify key considerations for mitigating deepfake threats. It covers various action steps such as intent, target research, training deepfake model, creating media and disseminating deepfake. Introducing our premium set of slides with name Deepfake Technology Threat Intrusion Framework. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Target Research, Intent, Create Media. So download instantly and tailor it with your information.
-
 Deepfake Technology Threat Prevention Checklist
Deepfake Technology Threat Prevention ChecklistThe purpose of this slide is to ensure proactive protection against deepfake technology threats. It showcases status of various tasks such as using VPN, making private social networking profile, limiting sharing pictures, etc. Presenting our set of slides with name Deepfake Technology Threat Prevention Checklist. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Blocking Software, Managing Business Operations, Social Networking.
-
 Deepfake Threat Scanner Technology Icon
Deepfake Threat Scanner Technology IconPresenting our set of slides with name Deepfake Threat Scanner Technology Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deepfake Threat, Scanner, Technology.
-
 Future Trends In Deepfake Technology Threats
Future Trends In Deepfake Technology ThreatsThe purpose of this slide is to illustrate key trends emerging in deepfake technology sector. It covers three key trends such as biometric implementation, digital doppelgangers and customized deepfakes. Introducing our premium set of slides with name Future Trends In Deepfake Technology Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Biometric Implementation, Digital Doppelgangers, Customized Deepfakes. So download instantly and tailor it with your information.
-
 Major Threats Associated With Deepfake Technology
Major Threats Associated With Deepfake TechnologyThe purpose of this slide is to show how applying deepfake technology can pose organizations to multiple threats. It covers various deepfake threats such as scams, disinformation attacks and identity thefts. Introducing our premium set of slides with name Major Threats Associated With Deepfake Technology. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Disinformation Attacks, Scams, Identity Thefts. So download instantly and tailor it with your information.
-
 Techniques To Spot Deepfake Technology Threats
Techniques To Spot Deepfake Technology ThreatsThe purpose of this slide is to assist identify potential deepfake technology threats by providing list of streamlined detection approaches. It covers four key techniques such as unnatural eye movement, lack of emotions, inconsistent audio and blurring. Presenting our set of slides with name Techniques To Spot Deepfake Technology Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Lack Emotions, Blurring, Inconsistent Audio.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Technology Security Dashboard Snapshot Threat Tracking Information Technology Security
Information Technology Security Dashboard Snapshot Threat Tracking Information Technology SecurityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Information Technology Security Dashboard Threat Tracking Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quarterly Comparison Of Information Technology Security Threats
Quarterly Comparison Of Information Technology Security ThreatsThis slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Introducing our Quarterly Comparison Of Information Technology Security Threats set of slides. The topics discussed in these slides are Quarterly Comparison, Information Technology, Security Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Automation In Information Technology Time To Fix Security Threat With Manual Testing
Security Automation In Information Technology Time To Fix Security Threat With Manual TestingThis slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver an outstanding presentation on the topic using this Security Automation In Information Technology Time To Fix Security Threat With Manual Testing. Dispense information and present a thorough explanation of Security, Threat, Manual Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Cybersecurity Technology Threat Management
IoT Cybersecurity Technology Threat ManagementThe below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Presenting our well structured IoT Cybersecurity Technology Threat Management. The topics discussed in this slide are Cybersecurity, Technology, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Internal technology threat ppt powerpoint presentation ideas cpb
Internal technology threat ppt powerpoint presentation ideas cpbPresenting Internal Technology Threat Ppt Powerpoint Presentation Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internal Technology Threat. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Internal technology threat ppt powerpoint presentation ideas clipart cpb
Internal technology threat ppt powerpoint presentation ideas clipart cpbPresenting our Internal Technology Threat Ppt Powerpoint Presentation Ideas Clipart Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on internal Technology Threat. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Environmental analysis tools techniques step analysis opportunity threat
Environmental analysis tools techniques step analysis opportunity threatThis slide shows STEP analysis to analyze likelihood, importance and influence of political, economic, social and technological factors on organizational activities. Present the topic in a bit more detail with this Environmental Analysis Tools Techniques STEP Analysis Opportunity Threat. Use it as a tool for discussion and navigation on Political, Economic, Social, Technological. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber threat hunting program with process and tools
Cyber threat hunting program with process and toolsThe following slide highlights the cyber threat hunting program including people, process and with four different levels to minimize risks and threats. Introducing our Cyber Threat Hunting Program With Process And Tools set of slides. The topics discussed in these slides are Cyber Threat Hunting, Cyber Security Tool, Cyber Threat Training. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Table of contents for cyber terrorism cyberterrorism it ppt slides tools
Table of contents for cyber terrorism cyberterrorism it ppt slides toolsPresent the topic in a bit more detail with this Table Of Contents For Cyber Terrorism Cyberterrorism IT Ppt Slides Tools. Use it as a tool for discussion and navigation on Current Scenario Company, Elements Cyber Terrorism, Preventive Measures, Against Cyber Terrorism Tools, Steps To Mitigate Cyber Terrorism, Tools Misused Cyber Terrorism, Current Situation Around Globe. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operational Technology Icon For Security Threat Detection
Operational Technology Icon For Security Threat DetectionIntroducing Operational Technology Icon For Security Threat Detection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Operational Technology Icon For Security Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Common Methods Used Threaten Information Security
Information Technology Security Common Methods Used Threaten Information SecurityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Introducing Information Technology Security Common Methods Used Threaten Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Daniel Of Service, Man In The Middle, SQL Injection , using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Latest Threats In Information Technology Security
Information Technology Security Latest Threats In Information Technology SecurityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Deliver an outstanding presentation on the topic using this Information Technology Security Latest Threats In Information Technology Security. Dispense information and present a thorough explanation of Latest Threats In Information Technology Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Threats In Information Technology Security
Information Technology Security Threats In Information Technology SecurityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Introducing Information Technology Security Threats In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Types Of Threats In Information Technology Security, using this template. Grab it now to reap its full benefits.
-
 Swot analysis threats high staff turnover rate in technology firm
Swot analysis threats high staff turnover rate in technology firmThe slide explains the attrition rate of the employees on the monthly basis with total numbers of employees in the begging and end of the months. Deliver an outstanding presentation on the topic using this SWOT Analysis Threats High Staff Turnover Rate In Technology Firm. Dispense information and present a thorough explanation of Monthly Employee Attrition Rate Membership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Terrorism Prevention Tools Comparative Analysis
Cyber Terrorism Prevention Tools Comparative AnalysisThis slide represents the comparison between various cyber terrorism prevention tools on the basis of their top features, bottom line and the free trials provided. It includes features such as multiple server support, breach severity insights, anti-exploit module etc. Introducing our Cyber Terrorism Prevention Tools Comparative Analysis set of slides. The topics discussed in these slides are Analysis Of Event Logs, Detection Of SQL Injection Attacks, Highly Automated, Comprehensive. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Most Effective It Security Tools For Protection Against Insider Threat
Most Effective It Security Tools For Protection Against Insider ThreatThis slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM Introducing our premium set of slides with Most Effective It Security Tools For Protection Against Insider Threat. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Loss Prevention, User Entity Behavior, Identity Access Management. So download instantly and tailor it with your information.
-
 Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators
Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines OperatorsThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators. Dispense information and present a thorough explanation of Unauthorized Activities, Virtualization Threats, Information Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Four Information Technology Security Threats
Four Information Technology Security ThreatsIntroducing our premium set of slides with Four Information Technology Security Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing Attacks, Cloud Jacking, Insider Threats. So download instantly and tailor it with your information.
-
 5G Technology Enabling Key Security Considerations For 5G For Threat Handling
5G Technology Enabling Key Security Considerations For 5G For Threat HandlingThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this 5G Technology Enabling Key Security Considerations For 5G For Threat Handling. Dispense information and present a thorough explanation of Threat Handling Initiatives, Concerns To Catered, Assets Managed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Icon To Reduce Threats
Information Technology Security Icon To Reduce ThreatsIntroducing our premium set of slides with Information Technology Security Icon To Reduce Threats. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology Security Icon, Reduce Threats. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Information Technology Risks Form Human Threat Source
IT Risk Management Strategies Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this IT Risk Management Strategies Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
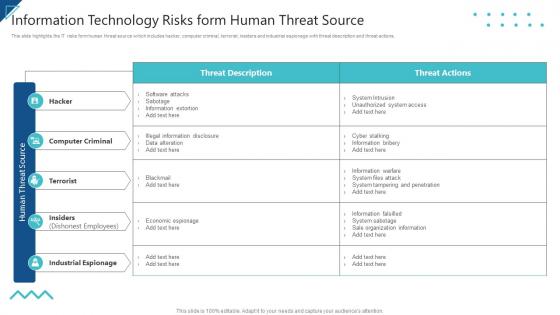 Enterprise Risk Management Information Technology Risks Form Human Threat Source
Enterprise Risk Management Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Enterprise Risk Management Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems
Classification Of IT Risks With Threats Risk Management Guide For Information Technology SystemsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems
IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology SystemsThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems
Information Technology Risks Form Human Threat Source Risk Assessment Of It SystemsThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Information, Technology, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology
Key Security Considerations For 5g For Threat Handling Developing 5g Transformative TechnologyThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology. Dispense information and present a thorough explanation of Considerations, Unauthorized Activities, Unauthorized Activities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




