Powerpoint Templates and Google slides for Strong Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data security it prepare and deploy strong it policies ppt slides deck
Data security it prepare and deploy strong it policies ppt slides deckThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Data Security IT Prepare And Deploy Strong IT Policies Ppt Slides Deck. Use it as a tool for discussion and navigation on Build Strong, IT Policies, Required Security Software, Content Sharing, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
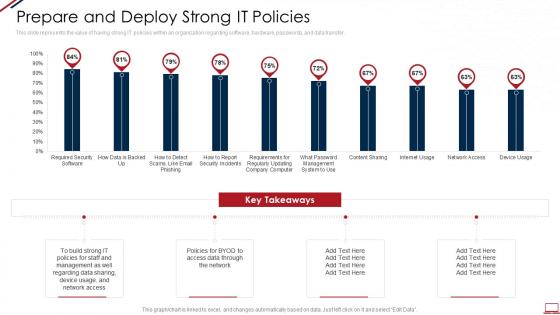 Computer system security prepare and deploy strong it policies
Computer system security prepare and deploy strong it policiesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Computer System Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it implementation of strong password policy
Data security it implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Data Security IT Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Computer system security implementation of strong password policy
Computer system security implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Computer System Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Building Strong Network Security Foundation In Business Strategy
Building Strong Network Security Foundation In Business StrategyThis slide showcases different methods of network security. The main purpose of this slide is to keep clients data safely from getting hacked or getting in the hands of rivals. This includes strategies such as holistic approach, data monitoring, risk assessment, etc. Presenting our set of slides with Building Strong Network Security Foundation In Business Strategy. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Holistic Approach, Risk Assessments.
-
 Best Practices To Create Strong Passwords Hands On Blockchain Security Risk BCT SS V
Best Practices To Create Strong Passwords Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. Increase audience engagement and knowledge by dispensing information using Best Practices To Create Strong Passwords Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Complex Passwords, Personal Information, Never Reuse Passwords using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In It
Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In ItThis slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Characteristics Of Strong Devsecops Program In It. This template helps you present information on six stages. You can also present information on Automated Operations, Security Awareness And Ownership, Developer Acceptance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Leverage Strong And Complex Password Management Creating Cyber Security Awareness
Leverage Strong And Complex Password Management Creating Cyber Security AwarenessThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Increase audience engagement and knowledge by dispensing information using Leverage Strong And Complex Password Management Creating Cyber Security Awareness This template helps you present information on Four stages. You can also present information on Issue Status Summary, It Costs And Revenue, Security Budget Spent using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS
Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SSThis slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Increase audience engagement and knowledge by dispensing information using Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Digital Certificates, Certificates Contains, Protect Cryptographic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats
Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Password Test, Password Encryption, Multi Factor Authentication using this template. Grab it now to reap its full benefits.
-
 Information Security Prepare And Deploy Strong It Policies
Information Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Information Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Prepare And Deploy Strong It Policies
Network Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Network Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong It Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security implementation strong password policy
Electronic information security implementation strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Electronic Information Security Implementation Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
 Information Security Implementation Of Strong Password Policy
Information Security Implementation Of Strong Password PolicyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Present the topic in a bit more detail with this Information Security Implementation Of Strong Password Policy. Use it as a tool for discussion and navigation on Implementation Of Strong Password Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Implementation Of Strong Password Policy
Network Security Implementation Of Strong Password PolicyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Network Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Implementation Of Strong Password Policy Information Technology Security
Implementation Of Strong Password Policy Information Technology SecurityThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Implementation Of Strong Password Policy Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Americans, Implementation, Passwords, using this template. Grab it now to reap its full benefits.
-
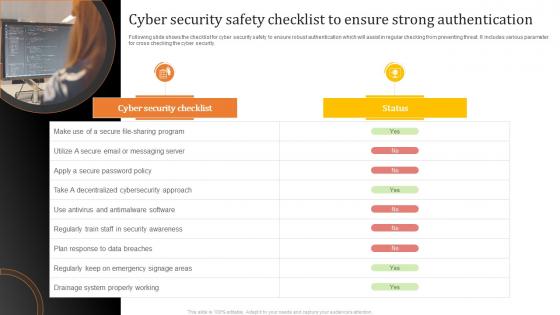 Cyber Security Safety Checklist To Ensure Strong Authentication
Cyber Security Safety Checklist To Ensure Strong AuthenticationFollowing slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Introducing our premium set of slides with Cyber Security Safety Checklist To Ensure Strong Authentication. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Checklist, Status, Messaging Server. So download instantly and tailor it with your information.
-
 Leverage Strong And Generating Security Awareness Among Employees To Reduce
Leverage Strong And Generating Security Awareness Among Employees To ReduceThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Generating Security Awareness Among Employees To Reduce to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Select Strong Password, Conduct Password Test using this template. Grab it now to reap its full benefits.
-
 Strong Security Password Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Strong Security Password Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is an ideal visual aid for presentations on the importance of strong passwords. It features a padlock with a keyhole, a key and a shield, all in bright, vibrant colours to grab the attention of the audience.
-
 Strong Security Password Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Strong Security Password Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is a great way to visually represent the importance of strong passwords. It is a simple and straightforward design that can be used to help educate users on the need for secure passwords.
-
 Steps to create strong cyber security assessment
Steps to create strong cyber security assessmentPresenting this set of slides with name Steps To Create Strong Cyber Security Assessment. This is a six stage process. The stages in this process are Steps Create, Strong Cyber, Security Assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Cyber security it implementation of strong password policy ppt powerpoint ideas example
Cyber security it implementation of strong password policy ppt powerpoint ideas exampleThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Increase audience engagement and knowledge by dispensing information using Cyber Security IT Implementation Of Strong Password Policy Ppt Powerpoint Ideas Example. This template helps you present information on four stages. You can also present information on Implementation Of Strong Password Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security it prepare and deploy strong it policies ppt powerpoint show topics
Cyber security it prepare and deploy strong it policies ppt powerpoint show topicsThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Cyber Security IT Prepare And Deploy Strong IT Policies Ppt Powerpoint Show Topics. Dispense information and present a thorough explanation of It Policies, Management, Access, Policies, Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



