Powerpoint Templates and Google slides for Strategies Implemented
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Man-in-the-Middle MITM Attacks in cyber terrorism. It includes mitigation startegies such as encryption, PKI, network security, 2FA and secure Wi-Fi.Introducing Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Account Security, Network Security, Encryption, using this template. Grab it now to reap its full benefits.
-
 Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SS
Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SSThis slide showcases the nation-state actors. It includes its characteristics and activities such as government backing, activities, objectives and techniques.Increase audience engagement and knowledge by dispensing information using Nation State Actors With Characteristics And Activities Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Government Backing, Activities, Objectives, Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS
Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SSThis slide showcases the Need for vigilance and adaptation in cyber security. It includes key points such as evolving threat landscape, pervasive cyber attacks, data as a target, adaptive strategies and resilience building.Present the topic in a bit more detail with this Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Pervasive Cyberattacks, Adaptive Strategies, Resilience Building, Evolving Threat Landscape. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SS
Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SSThis slide showcases the main objectives of cyber terrorist to enhance activities. It includes objectives such as political goals, making money, causing fear, revenge and payback and stealing secrets.Deliver an outstanding presentation on the topic using this Objectives Of Cyber Terrorist To Increase Activities Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Political Goals, Making Money, Revenge And Payback, Stealing Secrets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS
Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SSThis slide showcases the Offensive Cyber Operations and Deterrence. It includes elements such as definition, objective and examples.Present the topic in a bit more detail with this Offensive Cyber Operations And Deterrence Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Define, Objective, Examples, Deterrence Cyber Operations, Offensive Cyber Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS
Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SSThis slide showcases the Ongoing Threat of Cyber terrorism in digital age. It includes key aspects such as constant evolution of tactics, wide-ranging targets, legislation and regulation and future perspectives.Deliver an outstanding presentation on the topic using this Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Wide Ranging Targets, Legislation And Regulation, Future Perspectives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as user education, email filtering, MFA and incident reaction strategies.Introducing Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Example, Phishing Attack, Ideological Purposes, using this template. Grab it now to reap its full benefits.
-
 Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the political motivation and goals of cyber terrorism. It includes goals such as nationalism and separatism, conflict and warfare, influence elections and revenge and retaliation.Increase audience engagement and knowledge by dispensing information using Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Conflict And Warfare, Nationalism And Separatism, Influence Elections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS
Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SSThis slide showcases the Psychological Factors of cyber terrorism identify potential risks. It includes goals such as revenge and grudges, mental helath isuues, desire for power and frustration and alienation.Present the topic in a bit more detail with this Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Mental Health Issues, Frustration And Alienation, Revenge And Grudges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Ransomware attack with mitigation strategies and example. It also includes mitigation strategies such as regular backups, email security and antivirus and anti-malware.Increase audience engagement and knowledge by dispensing information using Ransomware Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Encrypts Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS
Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Role of Interpol and Europol in cyber terrorism. It also includes role such as global network, digital forensics, coordination and EC3, investigation support, operational coordination and public awareness.Introducing Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Global Network, Capacity Building, Digital Forensics, Coordination, using this template. Grab it now to reap its full benefits.
-
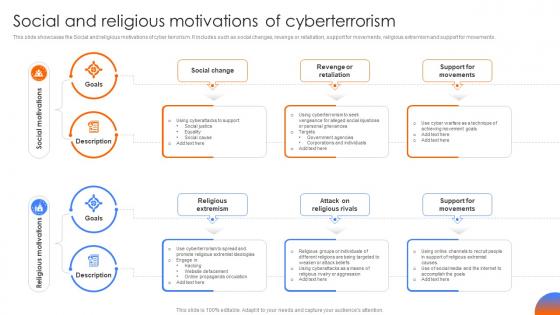 Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS
Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Social and religious motivations of cyber terrorism. It includes such as social changes, revenge or retaliation, support for movements, religious extremism and support for movements.Present the topic in a bit more detail with this Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Description, Goals, Social Change, Social Motivations, Religious Motivations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Spear phishing attack with mitigation strategies and its example. It also includes mitigation strategies such as email filtering, Multi-factor authentication MFA and network segmentation.Increase audience engagement and knowledge by dispensing information using Spear Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Presidential Election using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the SQL injection attack with mitigation strategies and example. It also includes mitigation strategies such as parameterized SQL statements, install a WAF and restrict the database users privileges.Introducing SQL Injection Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, Seize System Control, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS. This template helps you present information on eight stages. You can also present information on Motivations And Goals, Cyberterrorist Actors, Conclusion, Future Trends using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIntroducing Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intelligence Agencies, Cyber Security Initiatives, International Agreements, using this template. Grab it now to reap its full benefits.
-
 Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS
Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SSThis slide showcases the Techniques to prevent employee personal accounts. It includes strategies such as education and training, device security, two-factor authentication 2FA and secure Wi-Fi and networks.Increase audience engagement and knowledge by dispensing information using Techniques To Prevent Employee Personal Accounts Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Device Security, Education And Training, Two Factor Authentication, Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS
Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SSThis slide showcases an overview of thrill seekers. It includes its characteristics and activities such as motivation, intent, skill and knowledge, targets and impact.Introducing Thrill Seekers In Cyber Activities With Characteristics And Aspects Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Motivation, Intent, Skill And Knowledge, Targets, Impact, using this template. Grab it now to reap its full benefits.
-
 Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS
Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SSThis slide showcases the Train employees on cyber attack prevention. It includes techniques such as email impersonation, vigilance in clicking links, verification of email addresses and use of common sense.Present the topic in a bit more detail with this Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Threat Scenario, Description, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the Trojan horses attack with mitigation strategies and example. It includes mitigation strategies such as use updated version of antivirus and regular updates of operating systems.Introducing Trojan Horses Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Description, Mitigation Strategies, Example, using this template. Grab it now to reap its full benefits.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Whale phishing attack with mitigation strategies and its example. It includes mitigation strategies such as email filtering, Multi-factor authentication MFA and updates and patching.Increase audience engagement and knowledge by dispensing information using Whale Phishing Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Mitigation Strategies, Description, Example, Email Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS
Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SSThis slide showcases the Wi-Fi security to protect network and connected devices. It includes strategies such as strong passwords, encryption, firewall and intrusion detection systems IDS and two-factor authentication 2FA.Introducing Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two Factor Authentication, Intrusion Detection Systems, Encryption, Strong Passwords, using this template. Grab it now to reap its full benefits.
-
 XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases the XSS attack with mitigation strategies and example. It includes mitigation strategies such as content security policy and web application firewalls.Increase audience engagement and knowledge by dispensing information using XSS Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Description, Mitigation Strategies, Example, Content Security Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies For Implementing Holacracy In Powerpoint And Google Slides CPP
Strategies For Implementing Holacracy In Powerpoint And Google Slides CPPPresenting Strategies For Implementing Holacracy In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Strategies For Implementing Holacracy. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIntroducing Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Loopholes, Security Vulnerabilities, Vulnerabilities Mitigation Strategies, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide provides best practices for integrating patch management. It includes automating patch management, setting clear expectations, and scheduling auto-deployments.Increase audience engagement and knowledge by dispensing information using Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on three stages. You can also present information on Set Clear Expectations, Automate Patch Management, Schedule Auto Deployments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS
First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to first line of defense offered by implemented end to end encryption solution. It includes details related to process for device attestation.Introducing First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Device Management, Certificate Authority, Automatic Certificate Management Environment, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSPresenting our well crafted Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS
Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SSIntroducing Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Best Practices, Training Plan For Identification, using this template. Grab it now to reap its full benefits.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS
Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SSThis slide presents essential considerations for choosing an E2EE solution, including asymmetric encryption, key verification, complex cryptography, and ephemeral messaging.Introducing Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Asymmetric Encryption, Key Verification, Complex Cryptography, Ephemeral Messaging, using this template. Grab it now to reap its full benefits.
-
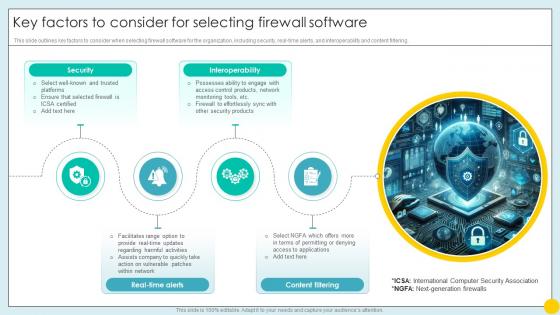 Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SS
Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines key factors to consider when selecting firewall software for the organization, including security, real-time alerts, and interoperability and content filtering.Increase audience engagement and knowledge by dispensing information using Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on four stages. You can also present information on Security, Interoperability, Real Time Alerts, Content Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
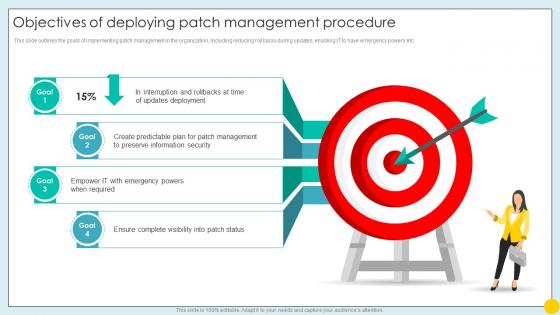 Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the goals of implementing patch management in the organization, including reducing rollbacks during updates, enabling IT to have emergency powers etc.Introducing Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Updates Deployment, Preserve Information Security, Ensure Complete Visibility, using this template. Grab it now to reap its full benefits.
-
 Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies to implement password authentication and mitigate threats from large-scale breaches. It includes strategies such as password hashing and salting.Introducing Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Consequence, Reasons, Password Authentication, using this template. Grab it now to reap its full benefits.
-
 Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies for IT teams to implement secure password authentication, including deploying multi-factor authentication systems, scanning all newly created passwords etc.Present the topic in a bit more detail with this Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Add Additional Layers, Compromised Credentials, Lower Case Letters, Symbols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
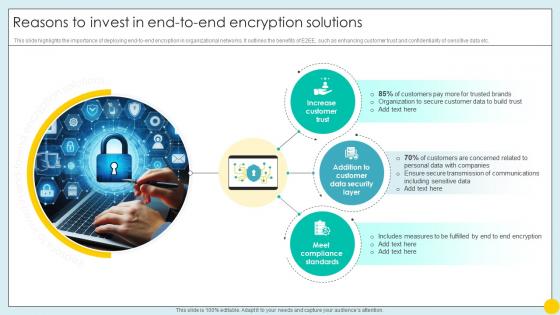 Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS
Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SSThis slide highlights the importance of deploying end-to-end encryption in organizational networks. It outlines the benefits of E2EE, such as enhancing customer trust and confidentiality of sensitive data etc.Introducing Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Increase Customer Trust, Meet Compliance Standards, Customer Data Security Layer, using this template. Grab it now to reap its full benefits.
-
 Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS
Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to second line of defense offered by implemented end to end encryption solution. It includes details related to process for certificate authentication.Increase audience engagement and knowledge by dispensing information using Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Certificate Authority, Client, Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS
Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SSThis slide presents statistical data highlighting the importance of patch management in organizational operations. It includes statistics related to breach detection time, prevention of cyber attacks, etc.Introducing Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organizations Possess, Documented Process, Patch Management, using this template. Grab it now to reap its full benefits.
-
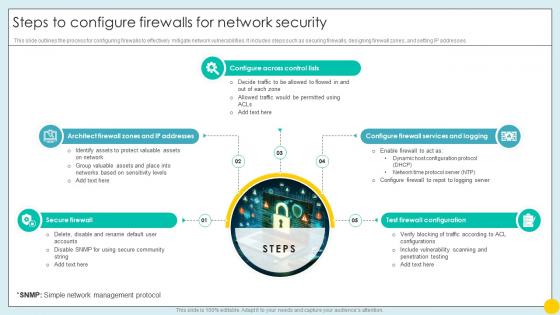 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
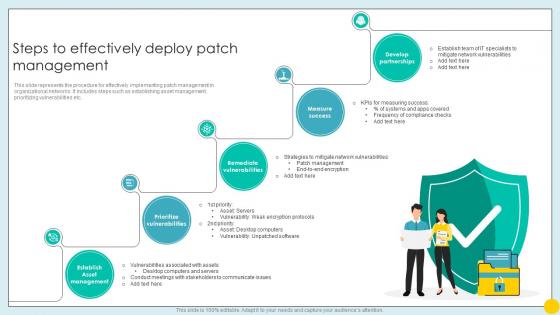 Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide represents the procedure for effectively implementing patch management in organizational networks. It includes steps such as establishing asset management, prioritizing vulnerabilities etc.Introducing Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prioritize Vulnerabilities, Remediate Vulnerabilities, Measure Success, Develop Partnerships, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Gap Analysis, Patch Management, Dashboard Tracking, Additional Slides using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide provides details about the training plan designed to help employees detect phishing attacks. It covers training topics such as identifying general signs of phishing attacks, signs of phishing in email etc.Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Training Sessions, Timeline, Trainer, Training Topic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a comprehensive training plan to help employees effectively identify various types of phishing attacks, including deceptive phishing, spear phishing, whaling, vishing and smishing.Deliver an outstanding presentation on the topic using this Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Sessions, Training Hours, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a training plan to help employees effectively prevent phishing attacks. It covers topics such as email communication, blocking popups and ads, report phishing attempts etc.Deliver an outstanding presentation on the topic using this Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Method, Expected Completion Date, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
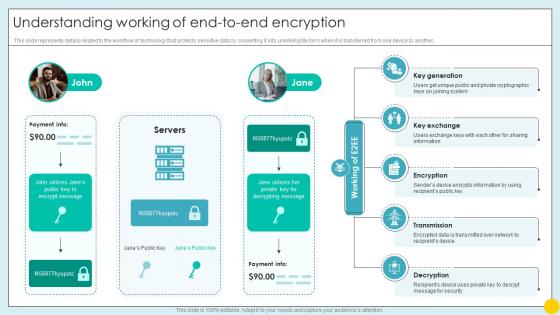 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Roadmap For Implementing Financial Strategy In Business
Roadmap For Implementing Financial Strategy In BusinessThis template showcases roadmap for implementing financial strategy in business helps to provide clear view of business financial health . It further includes details such as tax support , accounting operations , strategic advisory etc. Introducing our premium set of slides with Roadmap For Implementing Financial Strategy In Business Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Tax Support, Accounting Operations, Strategic Advisory So download instantly and tailor it with your information.
-
 Customer Service Training Implementation Challenges With Mitigation Strategies
Customer Service Training Implementation Challenges With Mitigation StrategiesThis slide represents various challenges of customer service training implementation which includes resistance to change, poor content delivery, and budget constraints. Presenting our set of slides with name Customer Service Training Implementation Challenges With Mitigation Strategies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Poor Content Delivery, Resistance To Change, Budget Constraints.
-
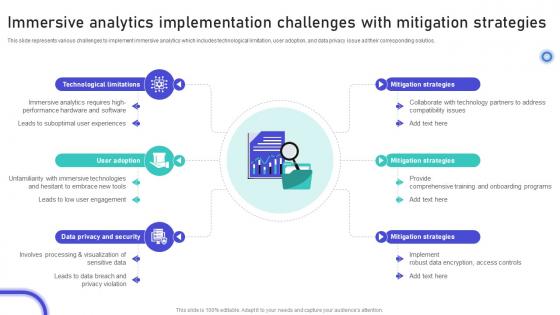 Immersive Analytics Implementation Challenges With Mitigation Strategies
Immersive Analytics Implementation Challenges With Mitigation StrategiesThis slide represents various challenges to implement immersive analytics which includes technological limitation, user adoption, and data privacy issue ad their corresponding solutios. Introducing our premium set of slides with Immersive Analytics Implementation Challenges With Mitigation Strategies Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Technological Limitations, User Adoption, Data Privacy And Security So download instantly and tailor it with your information.
-
 Budget Allocation For Implementing Conversational Marketing Strategies To Improve
Budget Allocation For Implementing Conversational Marketing Strategies To ImproveThis slide showcases the budget allocated to implement strategies such as incorporate live chat, use whatsapp business and leverage social media direct messaging. It includes expense areas such as promotional campaigns, incentives, etc.Present the topic in a bit more detail with this Budget Allocation For Implementing Conversational Marketing Strategies To Improve. Use it as a tool for discussion and navigation on Incorporate Live Chat, Leverage Social Media Direct Messaging, Estimated Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Allocation For Implementing Cosmetics Digital Marketing Strategies To Improve Cosmetics
Budget Allocation For Implementing Cosmetics Digital Marketing Strategies To Improve CosmeticsThis slide showcases the budget allocated to implement strategies such as hyper-personalization, create omnichannel experience, promotions and giveaways on social media, collaborate with beauty influencers, etc. Deliver an outstanding presentation on the topic using this Budget Allocation For Implementing Cosmetics Digital Marketing Strategies To Improve Cosmetics. Dispense information and present a thorough explanation of Hyper Personalization, Create Omnichannel Experience, Social Media using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Benefits Of Implementing Conversational Marketing Conversational Marketing Strategies To Improve
Key Benefits Of Implementing Conversational Marketing Conversational Marketing Strategies To ImproveIntroducing Key Benefits Of Implementing Conversational Marketing Conversational Marketing Strategies To Improve to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Customer Connection, Improved Customer Support, Personalized Solutions, using this template. Grab it now to reap its full benefits.
-
 Key Benefits Of Implementing Cosmetics Marketing Digital Marketing Strategies To Improve Cosmetics
Key Benefits Of Implementing Cosmetics Marketing Digital Marketing Strategies To Improve CosmeticsThis slide showcases the importance of developing marketing plan for cosmetics company. It includes authentic recommendations, engaged community and advocacy and personalized customer experience. Increase audience engagement and knowledge by dispensing information using Key Benefits Of Implementing Cosmetics Marketing Digital Marketing Strategies To Improve Cosmetics. This template helps you present information on three stages. You can also present information on Authentic Recommendations, Engaged Community And Advocacy, Personalized Customer Experience using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ecommerce Customer Service Strategy Implementation Timeline Effective Ecommerce Customer Service
Ecommerce Customer Service Strategy Implementation Timeline Effective Ecommerce Customer ServiceThe following slide depicts timeline to implement ecommerce customer service improvement strategies. It includes elements such as multichannel services, proactive support, live chat, automation, personalized solutions, KPI monitoring, etc. Increase audience engagement and knowledge by dispensing information using Ecommerce Customer Service Strategy Implementation Timeline Effective Ecommerce Customer Service. This template helps you present information on seven stages. You can also present information on Ecommerce Customer Service, Strategy Implementation Timeline, Multichannel Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 HRMS Implementation Strategy Dashboard For Tracking Employee Information Through HRMS
HRMS Implementation Strategy Dashboard For Tracking Employee Information Through HRMSThis slide covers dashboard for analysing workforce data using the new HRMS. It includes talent management KPIs such as employees, monthly salary, vacancies, hiring stats, talent turnover rate, talent satisfaction, etc. Present the topic in a bit more detail with this HRMS Implementation Strategy Dashboard For Tracking Employee Information Through HRMS. Use it as a tool for discussion and navigation on Talent Management, Employment Period, Department, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Broken Process Business Strategy Organization Operations Implement
Broken Process Business Strategy Organization Operations ImplementThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Broken Process Business Strategy Organization Operations Implement and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of eight slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.





