Powerpoint Templates and Google slides for Security Risk Incidents
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Blockchain security data protection risk control incident management
Blockchain security data protection risk control incident managementEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Security Data Protection Risk Control Incident Management is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS V
Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS VThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as Ronin, poly network, wormhole, BITMART, Venus, cream finance, along with key insights, etc. Present the topic in a bit more detail with this Top Ten Cryptocurrency Thefts Incidents By Amount Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Top Ten Cryptocurrency, Thefts Incidents By Amount. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Incident Escalation Response Flowchart Improving Cyber Security Risks Management
Cyber Incident Escalation Response Flowchart Improving Cyber Security Risks ManagementThe following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Present the topic in a bit more detail with this Cyber Incident Escalation Response Flowchart Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Incident Identified, Notify Security Team, Initial Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
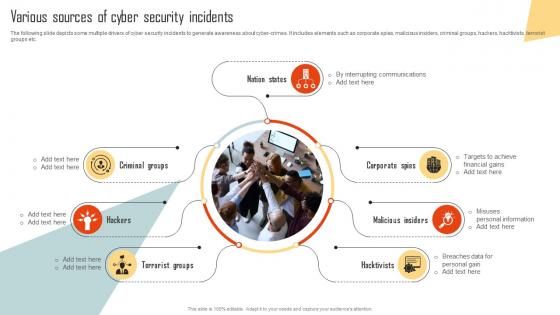 Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management
Various Sources Of Cyber Security Incidents Improving Cyber Security Risks ManagementThe following slide depicts some multiple drivers of cyber security incidents to generate awareness about cyber crimes. It includes elements such as corporate spies, malicious insiders, criminal groups, hackers, hacktivists, terrorist groups etc. Increase audience engagement and knowledge by dispensing information using Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management. This template helps you present information on seven stages. You can also present information on Criminal Groups, Terrorist Groups, Malicious Insiders, Corporate Spies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
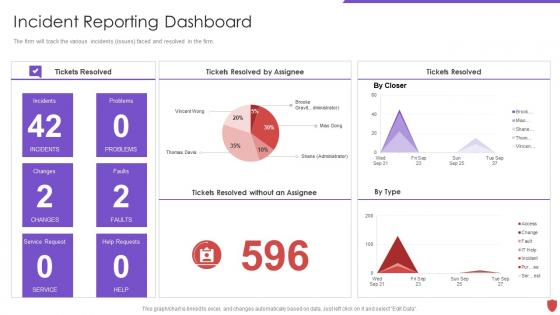 Cyber security risk management incident reporting dashboard
Cyber security risk management incident reporting dashboardThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Cyber Security Risk Management Incident Reporting Dashboard. Use it as a tool for discussion and navigation on Tickets Resolved, Tickets Resolved By Assignee, Tickets Resolved, Tickets Resolved Assignee. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incidents Risk Tracking Dashboard For Response
Cyber Security Incidents Risk Tracking Dashboard For ResponseThis slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map.Introducing our Cyber Security Incidents Risk Tracking Dashboard For Response set of slides. The topics discussed in these slides are Action Plan Breakdown, Risk Rating, Analysis Progress. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
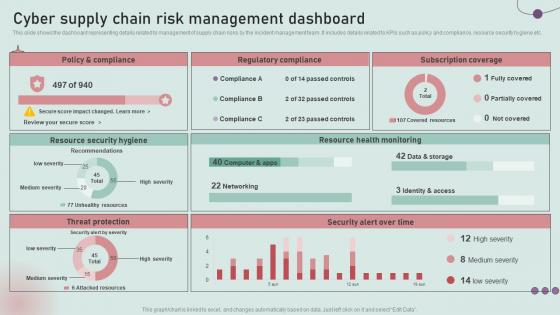 Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident
Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security IncidentThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Deliver an outstanding presentation on the topic using this Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Regulatory Compliance, Subscription Coverage, Resource Health using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
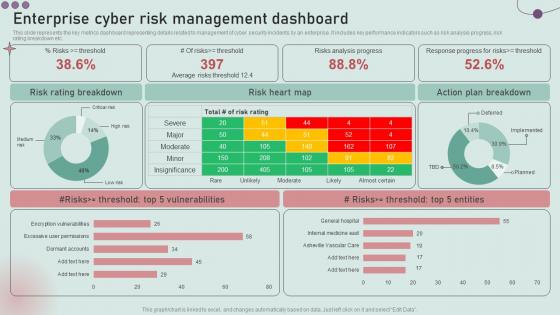 Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident
Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security IncidentThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heart Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management
Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc.Present the topic in a bit more detail with this Cyber Supply Chain Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Resource Security Hygiene, Subscription Coverage, Resource Health Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
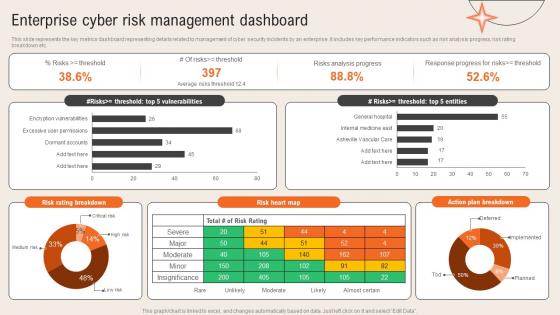 Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management
Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident ManagementThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc.Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Risks Analysis Progress, Response Progress, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident management tool effective information security risk management process
Incident management tool effective information security risk management processMentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Present the topic in a bit more detail with this Incident Management Tool Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Notify Employee, Message During Any Breach, Automated Workflow. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
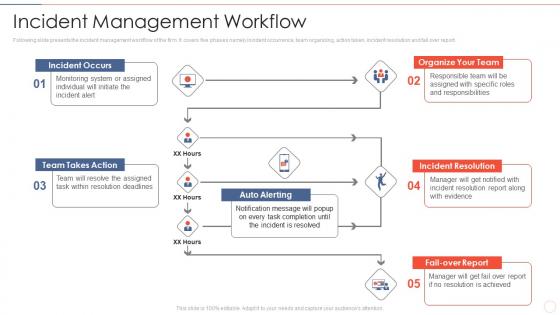 Incident management workflow effective information security risk management process
Incident management workflow effective information security risk management processFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report.Introducing Incident Management Workflow Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organize Your Team, Incident Resolution, Team Takes Action, using this template. Grab it now to reap its full benefits.
-
 Incidents effective information security risk management process
Incidents effective information security risk management processThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Present the topic in a bit more detail with this Incidents Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on Preform Primary Work Functions, Inconvenient, Medium Multiple. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
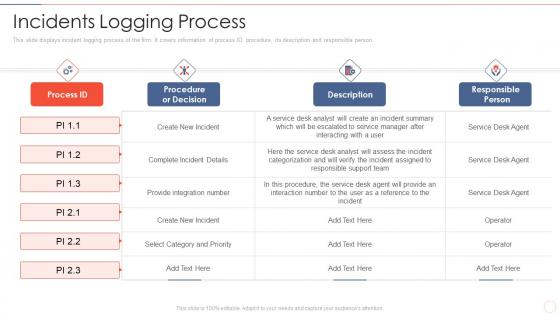 Incidents logging process effective information security risk management process
Incidents logging process effective information security risk management processThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver an outstanding presentation on the topic using this Incidents Logging Process Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Select Category And Priority, Procedure, The Service, Responsible Person using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security risk management process incidents prioritization matrix effective information
Security risk management process incidents prioritization matrix effective informationThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level Present the topic in a bit more detail with this Security Risk Management Process Incidents Prioritization Matrix Effective Information. Use it as a tool for discussion and navigation on Enterprise Or Multiple Segments, Single Segment Or Entire Site, Event Underway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security Addressing The Incidents Logging
Risk Management Framework For Information Security Addressing The Incidents LoggingThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Addressing The Incidents Logging. Dispense information and present a thorough explanation of Create New Incident, Complete Incident Details, Provide Integration Number using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Impact Urgency Matrix For Incidents
Risk Management Framework For Information Security Impact Urgency Matrix For IncidentsThis slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Present the topic in a bit more detail with this Risk Management Framework For Information Security Impact Urgency Matrix For Incidents. Use it as a tool for discussion and navigation on Business Unit, Department, Location, High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management incident reporting by different departments
Cyber security risk management incident reporting by different departmentsThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Introducing Cyber Security Risk Management Incident Reporting By Different Departments to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Number Incidents, Person Involved Incident, Average Cost Per Incident, using this template. Grab it now to reap its full benefits.
-
 Workplace incident summary report cyber security risk management
Workplace incident summary report cyber security risk managementThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver an outstanding presentation on the topic using this Workplace Incident Summary Report Cyber Security Risk Management. Dispense information and present a thorough explanation of Type Incident, Employees Involved, Time Incident, Assets Money Lost, Damaged using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Q70 Risk Management Framework For Information Security Incident Management Workflow Process
Q70 Risk Management Framework For Information Security Incident Management Workflow ProcessFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Q70 Risk Management Framework For Information Security Incident Management Workflow Process. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Auto Alerting, Fail Over Report, Organize Team, Incident Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware
Incident Response Playbook Security Controls To Reduce The Risk Of RansomwareMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware. Use it as a tool for discussion and navigation on Impact Category, Functional Impact, Informational Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Management Icon To Mitigate Risk
Security Incident Management Icon To Mitigate RiskIntroducing our premium set of slides with Security Incident Management Icon To Mitigate Risk. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Incident, Management Icon To Mitigate Risk. So download instantly and tailor it with your information.
-
 Security Controls To Reduce The Risk Of Ransomware Security Incident Response Playbook
Security Controls To Reduce The Risk Of Ransomware Security Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Security Controls To Reduce The Risk Of Ransomware Security Incident Response Playbook. Use it as a tool for discussion and navigation on Ransomwarem, Impacts Organization, Encrypts Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability
Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And VulnerabilityMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Deliver an outstanding presentation on the topic using this Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Gains Access, Takes Control, Impacts Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook
Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Ransomware, Informational Impact, Recoverability Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Matrix Incident Response Strategies DeploymentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Vulnerability, Consequences, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
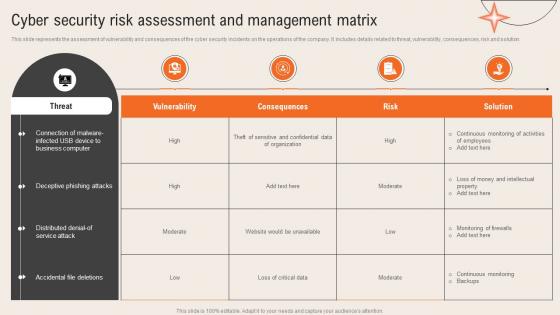 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk roadmap showing work safety information security and incident response
Risk roadmap showing work safety information security and incident responsePresenting this set of slides with name - Risk Roadmap Showing Work Safety Information Security And Incident Response. This is a five stage process. The stages in this process are Risk Roadmap, Risk Timeline, Risk Management.
-
 Incident security risk management plan for healthcare sector
Incident security risk management plan for healthcare sectorPresenting our well-structured Incident Security Risk Management Plan For Healthcare Sector. The topics discussed in this slide are Assessment, Management, Planning . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Addressing incidents logging information security risk management program
Addressing incidents logging information security risk management programThis slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Present the topic in a bit more detail with this Addressing Incidents Logging Information Security Risk Management Program. Use it as a tool for discussion and navigation on Procedure, Decision, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident management diagram information security risk management program
Incident management diagram information security risk management programFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Incident Management Diagram Information Security Risk Management Program. Use it as a tool for discussion and navigation on Incident Resolution, Organize, Incident Occurs, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.



