Powerpoint Templates and Google slides for Security Plans
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
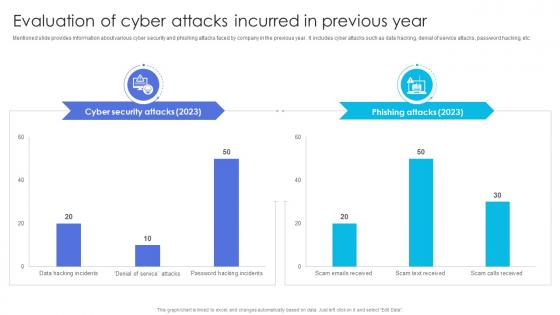 Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat
Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various cyber security and phishing attacks faced by company in the previous year. It includes cyber attacks such as data hacking, denial of service attacks, password hacking, etc. Deliver an outstanding presentation on the topic using this Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Information, Service, Evaluation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about incident status page leverage to communicate with internal stakeholders. It includes key elements such as target audience, incident page sample, and best practices. Present the topic in a bit more detail with this Incident Status Page For Internal Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Stakeholders, Resolution Adopted. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat
Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various strategies adopted by company for preventing cyber attacks. It includes key threats such as ransomware, malware, phishing, and denial of service. Deliver an outstanding presentation on the topic using this Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Strategies, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
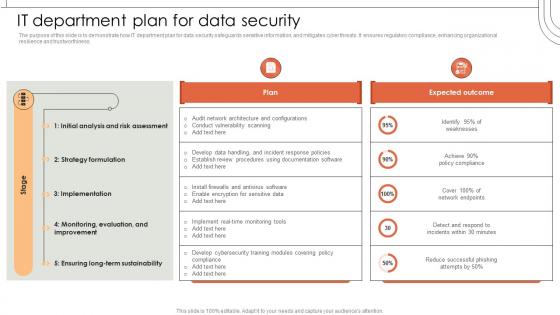 It Department Plan For Data Security
It Department Plan For Data SecurityThe purpose of this slide is to demonstrate how IT department plan for data security safeguards sensitive information, and mitigates cyber threats. It ensures regulatory compliance, enhancing organizational resilience and trustworthiness. Present the topic in a bit more detail with this It Department Plan For Data Security. Use it as a tool for discussion and navigation on Department, Organizational, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security budget plan for endpoint operations. It provides details about secure data transmission, frontline defense, external network threats, etc.Present the topic in a bit more detail with this Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Endpoint Operations, Secure Data Transmission, Frontline Defense, External Network Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
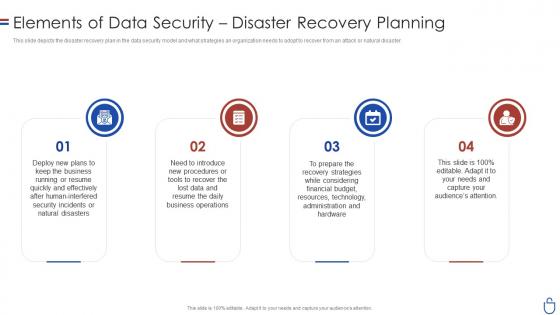 Data security it elements of data security disaster recovery planning
Data security it elements of data security disaster recovery planningThis slide depicts the disaster recovery plan in the data security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Introducing Data Security IT Elements Of Data Security Disaster Recovery Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Business, Natural Disasters, Human Interfered Security Incidents, Technology, using this template. Grab it now to reap its full benefits.
-
 30 60 90 days plan for security guard services proposal ppt slides backgrounds
30 60 90 days plan for security guard services proposal ppt slides backgroundsIntroducing 30 60 90 Days Plan For Security Guard Services Proposal Ppt Slides Backgrounds to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, Security Guard Services, using this template. Grab it now to reap its full benefits.
-
 Customized plan for security guard services proposal ppt slides portfolio
Customized plan for security guard services proposal ppt slides portfolioPresent the topic in a bit more detail with this Customized Plan For Security Guard Services Proposal Ppt Slides Portfolio. Use it as a tool for discussion and navigation on Discovery, Site Surveys, Security Analysis, Plan Presentation, Contract Signing, Staffing, Training, Implementation, Reporting And Review. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it managing data security 60 days plan ppt slides introduction
Data security it managing data security 60 days plan ppt slides introductionThis slide represents the plan for 60 days after implementing the data security model in the organization. Present the topic in a bit more detail with this Data Security IT Managing Data Security 60 Days Plan Ppt Slides Introduction. Use it as a tool for discussion and navigation on Time to Detect Incident, Policy Violations, Data Loss Incidents, Infected Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it managing data security 90 days plan ppt slides icons
Data security it managing data security 90 days plan ppt slides iconsThis slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Data Security IT Managing Data Security 90 Days Plan Ppt Slides Icons. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
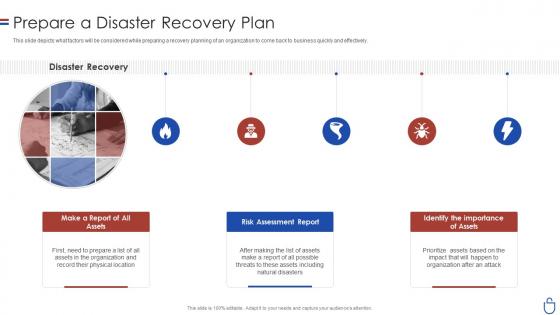 Data security it prepare a disaster recovery plan ppt slides rules
Data security it prepare a disaster recovery plan ppt slides rulesThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Data Security IT Prepare A Disaster Recovery Plan Ppt Slides Rules to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Disaster Recovery, Make Report Assets, Risk Assessment Report Assets, Identify importance, using this template. Grab it now to reap its full benefits.
-
 Data security it process of disaster recovery planning ppt slides download
Data security it process of disaster recovery planning ppt slides downloadThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Data Security IT Process Of Disaster Recovery Planning Ppt Slides Download to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Approval, Create Disaster, Recovery Team, Perform, Risk Analysis, Prioritize Procedures And Operations, Define Recovery Plans, using this template. Grab it now to reap its full benefits.
-
 Data security it types of disaster recovery plan ppt slides file formats
Data security it types of disaster recovery plan ppt slides file formatsThis slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Introducing Data Security IT Types Of Disaster Recovery Plan Ppt Slides File Formats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Based Disaster Recovery, Data Center Disaster Recovery, Virtualization Disaster Recovery, Disaster Recovery Service, using this template. Grab it now to reap its full benefits.
-
 Computer system security elements of computer security disaster recovery planning
Computer system security elements of computer security disaster recovery planningThis slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Introducing Computer System Security Elements Of Computer Security Disaster Recovery Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Business, Technology, Administration, Budget, Resources, Financial, using this template. Grab it now to reap its full benefits.
-
 Computer system security managing computer security 90 days plan
Computer system security managing computer security 90 days planThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Computer System Security Managing Computer Security 90 Days Plan. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
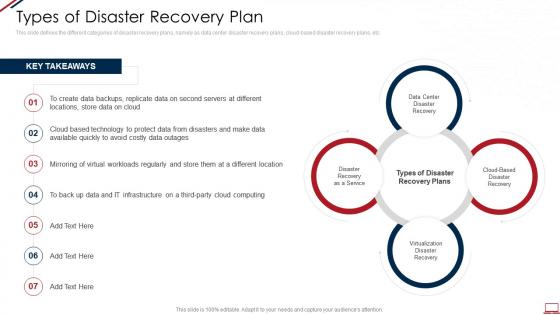 Computer system security types of disaster recovery plan
Computer system security types of disaster recovery planThis slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. Introducing Computer System Security Types Of Disaster Recovery Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Virtualization Disaster Recovery, Cloud Based Disaster Recovery, Data Center Disaster Recovery, Disaster Recovery As A Service, using this template. Grab it now to reap its full benefits.
-
 Computer system security managing computer security 60 days plan
Computer system security managing computer security 60 days planThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Computer System Security Managing Computer Security 60 Days Plan. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security process of disaster recovery planning
Computer system security process of disaster recovery planningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Computer System Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Plan Testing, Approval, Recovery Plans, Data Collection, Forming Data Recovery Plan, using this template. Grab it now to reap its full benefits.
-
 Managing computer security 30 days plan computer system security
Managing computer security 30 days plan computer system securityPresent the topic in a bit more detail with this Managing Computer Security 30 Days Plan Computer System Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prepare a disaster recovery plan computer system security ppt powerpoint tipswd
Prepare a disaster recovery plan computer system security ppt powerpoint tipswdThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Prepare A Disaster Recovery Plan Computer System Security Ppt Powerpoint Tipswd to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Make A Report Of All Assets, Risk Assessment Report, Identify The Importance Of Assets, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Management Quarterly Action Plan
Cyber Security Management Quarterly Action PlanThis slide represents quarterly action plan of cyber security management for protecting customer data. It further includes steps such as evaluate cyber security risks, prioritize cyber risks, etc Presenting our well structured Cyber Security Management Quarterly Action Plan. The topics discussed in this slide are Quarter, Action Taken, Responsible Person, Impact. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Quarterly Action Plan For Cloud Security Threats
Quarterly Action Plan For Cloud Security ThreatsThis slide showcases quarterly action plan for resolving issues and threats of cloud security. It further includes cloud security threats such as unauthorized data access, DDoS, etc And respective action taken, date of completion, status, and add comments. Introducing our Quarterly Action Plan For Cloud Security Threats set of slides. The topics discussed in these slides are Quarter, Cloud Security Threats, Status. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Affiliate Marketing Plan To Generate More Leads Security Token Offerings BCT SS
Affiliate Marketing Plan To Generate More Leads Security Token Offerings BCT SSThe following slide depicts affiliate promotion plan for security token offerings STO to boost website traffic and conversion rate. It includes elements such as objectives, commission, performance tracking, offering incentives, etc. Introducing Affiliate Marketing Plan To Generate More Leads Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Commission, Affiliate Selection And On Boarding, using this template. Grab it now to reap its full benefits.
-
 Community Building Plan To Boost Conversions Security Token Offerings BCT SS
Community Building Plan To Boost Conversions Security Token Offerings BCT SSThe following slide depicts the community building program to build connections and develop trust. It includes elements such as objectives, target audience, platforms, initiatives, update about progress, encourage feedbacks, host events, etc. Introducing Community Building Plan To Boost Conversions Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Target Audience, Platforms, Initiatives, using this template. Grab it now to reap its full benefits.
-
 Competitive Pricing Plan Offered By STO Marketing Agency Security Token Offerings BCT SS
Competitive Pricing Plan Offered By STO Marketing Agency Security Token Offerings BCT SSThe following slide showcases sample pricing plan of security token offering marketing services. It includes elements such as community promotion, ICI listing, airdrop program, support services, basic, advanced, premium, etc. Present the topic in a bit more detail with this Competitive Pricing Plan Offered By STO Marketing Agency Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Community Marketing, Advanced, Airdrop Program, Marketing Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Develop Security Token Offering Plan Security Token Offerings BCT SS
Develop Security Token Offering Plan Security Token Offerings BCT SSThe following slide depicts sample security token offering STO plan to enable fundraising and crowd funding activities. It includes elements such as number of tokens, percentage allocated to public, private investors, pre-sale participants, project teams, reserve funds, etc. Introducing Develop Security Token Offering Plan Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Completion Of Tokenization Process, Offering Plan, using this template. Grab it now to reap its full benefits.
-
 Develop Token Distribution And Allocation Plan Security Token Offerings BCT SS
Develop Token Distribution And Allocation Plan Security Token Offerings BCT SSThe following slide depicts sample security token distribution plan to enhance community participation and engagement. It includes components such as number of tokens allocated, vesting period, utility offered, distribution timeline, etc. Increase audience engagement and knowledge by dispensing information using Develop Token Distribution And Allocation Plan Security Token Offerings BCT SS. This template helps you present information on two stages. You can also present information on Token Allocation, Vesting Period, Distribution Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
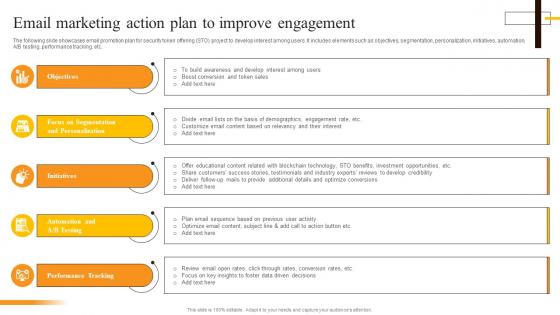 Email Marketing Action Plan To Improve Engagement Security Token Offerings BCT SS
Email Marketing Action Plan To Improve Engagement Security Token Offerings BCT SSThe following slide showcases email promotion plan for security token offering STO project to develop interest among users. It includes elements such as objectives, segmentation, personalization, initiatives, automation, A or B testing, performance tracking, etc. Introducing Email Marketing Action Plan To Improve Engagement Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Focus On Segmentation, Initiatives, Performance Tracking, using this template. Grab it now to reap its full benefits.
-
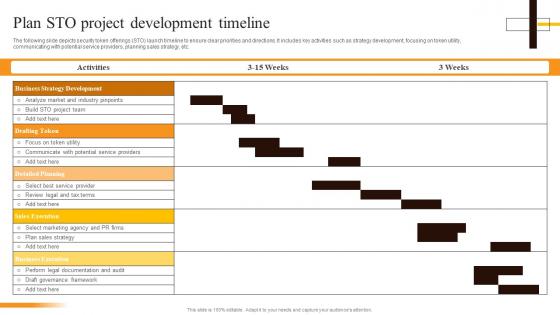 Plan STO Project Development Timeline Security Token Offerings BCT SS
Plan STO Project Development Timeline Security Token Offerings BCT SSThe following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. Present the topic in a bit more detail with this Plan STO Project Development Timeline Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Business Strategy Development, Drafting Token, Detailed Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Media Marketing Plan To Create Buzz Security Token Offerings BCT SS
Social Media Marketing Plan To Create Buzz Security Token Offerings BCT SSThe following slide showcases social media marketing plan for security token offering STO project to build awareness and boost conversion rate. It includes elements such as objectives, target audience, initiatives, performance monitoring, etc. Increase audience engagement and knowledge by dispensing information using Social Media Marketing Plan To Create Buzz Security Token Offerings BCT SS. This template helps you present information on five stages. You can also present information on Objectives, Target Audience, Platform, Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Content Marketing Plan To Engage Audience Security Token Offerings BCT SS
Strategic Content Marketing Plan To Engage Audience Security Token Offerings BCT SSThe following slide illustrates content marketing action plan for security token offerings STO to maximize reach. It includes elements such as objectives, target audience, content strategy, create blogs, determine areas of improvement, etc. Introducing Strategic Content Marketing Plan To Engage Audience Security Token Offerings BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Target Audience, Content Strategy, Monitor Performance, using this template. Grab it now to reap its full benefits.
-
 Strategic Influencer Marketing Plan To Create Awareness Security Token Offerings BCT SS
Strategic Influencer Marketing Plan To Create Awareness Security Token Offerings BCT SSThe following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Increase audience engagement and knowledge by dispensing information using Strategic Influencer Marketing Plan To Create Awareness Security Token Offerings BCT SS. This template helps you present information on five stages. You can also present information on Objectives, Budget, Engage With Influencers, Giveaways using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 EHR Security Implementation Plan Icon
EHR Security Implementation Plan IconIntroducing our EHR Security Implementation Plan Icon set of slides. The topics discussed in these slides are Ehr Security Implementation Plan Icon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches
Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data BreachesThis slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches. This template helps you present information on three stages. You can also present information on Strengthen Access Controls, Implement Continuous Monitoring, Implement Data Encryption, Continue Employee Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation
Data Breach Response Plan Secure Operations Data Breach Prevention And MitigationThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Secure Operations Data Breach Prevention And Mitigation. Use it as a tool for discussion and navigation on Assemble Expert Team, Consult With Legal Counsel, Secure Physical Areas. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Risk Treatment Action Plan Icon
Data Security Risk Treatment Action Plan IconPresenting our set of slides with Data Security Risk Treatment Action Plan Icon. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security Risk Treatment, Action Plan Icon.
-
 3 Star Hotel Security Plan Colored Icon In Powerpoint Pptx Png And Editable Eps Format
3 Star Hotel Security Plan Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Security Action Plan For Hotels icon is a vibrant and eye-catching way to visually represent your hotels security plan. The icon is perfect for presentations, websites, and other digital media. It is a great way to show your commitment to safety and security.
-
 3 Star Hotel Security Plan Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
3 Star Hotel Security Plan Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Security Action Plan For Hotels is a perfect visual aid for your presentations. It is an editable vector graphic that can be used to illustrate the steps needed for a hotel to create a comprehensive security action plan.
-
 Security Action Plan For Hotel Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Action Plan For Hotel Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Security Action Plan For Hotels icon is a vibrant and eye-catching way to visually represent your hotels security plan. The icon is perfect for presentations, websites, and other digital media. It is a great way to show your commitment to safety and security.
-
 Security Action Plan For Hotel Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Action Plan For Hotel Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Security Action Plan For Hotels is a perfect visual aid for your presentations. It is an editable vector graphic that can be used to illustrate the steps needed for a hotel to create a comprehensive security action plan.
-
 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway
30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web GatewayThis slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Introducing 30 60 90 Days Plan To Integrate Secure Web Network Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Compatible, Performance, Production, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Planning And Preparation Network Security Using Secure Web Gateway
Secure Web Gateway Planning And Preparation Network Security Using Secure Web GatewayThis slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Introducing Secure Web Gateway Planning And Preparation Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identify Network Architecture, Define Scope Of Project, Define Security Policy, using this template. Grab it now to reap its full benefits.
-
 Website Security Management Action Plan Virtual Shop Designing For Attracting Customers
Website Security Management Action Plan Virtual Shop Designing For Attracting CustomersMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Introducing Website Security Management Action Plan Virtual Shop Designing For Attracting Customers to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Criteria, Description, Priority, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations
Cyber Security Risk Assessment And Technology Deployment Plan To Improve OrganizationsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations. Dispense information and present a thorough explanation of Consequences, Vulnerability, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations
Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve OrganizationsThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Malware, Application, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Various Banks To Secure Best Planning Successful Opening Of New Retail
Comparative Analysis Of Various Banks To Secure Best Planning Successful Opening Of New RetailThe following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. Deliver an outstanding presentation on the topic using this Comparative Analysis Of Various Banks To Secure Best Planning Successful Opening Of New Retail. Dispense information and present a thorough explanation of Banks, Secure, Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration
Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design InspirationIntroducing Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Attacks Frequency, Assessment Program For Organization, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements
Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon ElementsPresenting our well crafted Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of Contents
Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of ContentsIntroducing Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risk, Assessment Program, Conduct Cybersecurity, Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber Framework For Cybersecurity Risk Management
Security Plan To Prevent Cyber Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Cyber Security Communities, Information Sharing, Private Organizations, IT Governance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks
Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Use Multifactor Authentication, Regularly Track Network Intrusions, Control Accounts Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization
Security Plan To Prevent Cyber Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Introducing Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network And Application Infrastructure, Database Servers, Cause Operational Disruption, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks, Risk Occurrence, Attacks Segmentation, Monitor And Mitigate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Monetary Losses Due To Cyber Crime Events
Security Plan To Prevent Cyber Monetary Losses Due To Cyber Crime EventsThis slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Monetary Losses Due To Cyber Crime Events. Use it as a tool for discussion and navigation on Financial Losses, Multiple Regions Across, Cyber Crime Incidents, Operational And Revenue Loss, Cybersecurity Program, Risk Assessment Module. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk Assessment
Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk Assessment. This template helps you present information on four stages. You can also present information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Plan To Prevent Cyber Need Of Cybersecurity Program For Organization
Security Plan To Prevent Cyber Need Of Cybersecurity Program For OrganizationThis slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Introducing Security Plan To Prevent Cyber Need Of Cybersecurity Program For Organization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Actionable And Prioritized, List Of Cybersecurity Risks, Mitigation Plan, Tackle Future Threats, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber NIST Cybersecurity Framework With Subcategories
Security Plan To Prevent Cyber NIST Cybersecurity Framework With SubcategoriesThis slide represents the NIST cybersecurity framework with subcategories. It also contains information regarding the software which fulfill multiple compliance requirements of NIST cybersecurity framework. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber NIST Cybersecurity Framework With Subcategories. Dispense information and present a thorough explanation of Anomalies And Events, Security Continuous Monitoring, Protective Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities
Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Financial Transactions, Credentials Compromised, Cloud Network, Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact
Security Plan To Prevent Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks
Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks. This template helps you present information on four stages. You can also present information on Cybersecurity Attacks, Recommended Mitigation Strategy, Strategy Implementation Time Required using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





