Powerpoint Templates and Google slides for Security Method
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides
Risk Based Methodology To Cyber And Information Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Risk Based Methodology To Cyber And Information Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty four slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
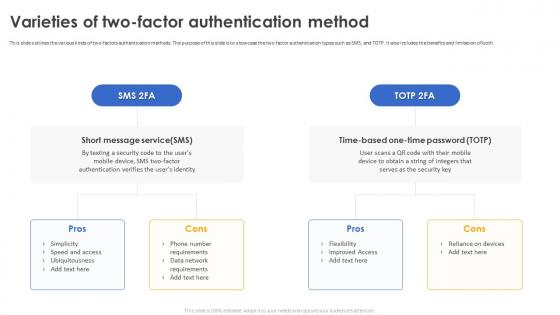 Secure Your Digital Assets Varieties Of Two Factor Authentication Method
Secure Your Digital Assets Varieties Of Two Factor Authentication MethodThis slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Varieties Of Two Factor Authentication Method. This template helps you present information on two stages. You can also present information on Phone Number Requirements, Data Network Requirements, Time Based One Time Password using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E Payment
Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E PaymentMentioned slide showcases various payment methods used by businesses for sales and purchase of goods and services. It includes payment methods such as debit cards, mobile wallet, credit card, cash, etc. Present the topic in a bit more detail with this Most Popular Methods Used In Businesses Transactions Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Service, Payment, Debit Cards This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures
Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security MeasuresThe slide outlines major multifactor authentication methods to safeguard ecommerce stores. It include details about knowledge factors, possession factor along with potential impact. Present the topic in a bit more detail with this Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Information Inherent, Potential Impact, Reduced Suspicious Logins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
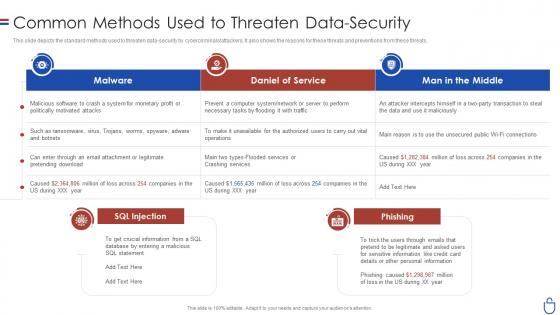 Data security it common methods used to threaten data security
Data security it common methods used to threaten data securityThis slide depicts the standard methods used to threaten data-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Present the topic in a bit more detail with this Data Security IT Common Methods Used To Threaten Data Security. Use it as a tool for discussion and navigation on Malware, Daniel Service, Man Middle, SQL Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security common methods used to threaten computer security
Computer system security common methods used to threaten computer securityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Increase audience engagement and knowledge by dispensing information using Computer System Security Common Methods Used To Threaten Computer Security. This template helps you present information on five stages. You can also present information on Malware, Daniel Of Service, Man In The Middle, SQL Injection, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Limitations Of Switched Port Analyzer Method Network Security Using Secure Web Gateway
Limitations Of Switched Port Analyzer Method Network Security Using Secure Web GatewayThis slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. Introducing Limitations Of Switched Port Analyzer Method Network Security Using Secure Web Gateway to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Problematic, Business, Architecture, using this template. Grab it now to reap its full benefits.
-
 Methods To Implement Security Policies On Network Security Using Secure Web Gateway
Methods To Implement Security Policies On Network Security Using Secure Web GatewayThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Deliver an outstanding presentation on the topic using this Methods To Implement Security Policies On Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Organizational, Examination, Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway
Secure Implementation Methodology Explicit Network Security Using Secure Web GatewayThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Deliver an outstanding presentation on the topic using this Secure Implementation Methodology Explicit Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Implementation, Methodology, Concentrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateway Methodology Inline Network Security Using Secure Web Gateway
Secure Web Gateway Methodology Inline Network Security Using Secure Web GatewayThis slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Present the topic in a bit more detail with this Secure Web Gateway Methodology Inline Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Implementation, Methodology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway
Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web GatewayThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Present the topic in a bit more detail with this Swg Implementation Methodology Port Analyzer Port Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Implementation, Methodology, Analyzer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking Operations
Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking OperationsThe purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Increase audience engagement and knowledge by dispensing information using Methods To Improve Online Banking Security For Customers Strategic Improvement In Banking Operations. This template helps you present information on four stages. You can also present information on Strong Authentication, Encryption And Secure Connections, Robust Backend Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Integrate Secops V2 Into Security Operations Soc
Methods To Integrate Secops V2 Into Security Operations SocThis slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Introducing Methods To Integrate Secops V2 Into Security Operations Soc to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Build Security Center Of Excellence, Establish Culture Of Collaboration, Security Operations, using this template. Grab it now to reap its full benefits.
-
 Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS V
Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS VThis slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Present the topic in a bit more detail with this Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Biometric, Technology, Iris Recognition. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS V
Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Measure, Transactions, Passwords Frequently. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Banking Application Security Testing Tools E Wallets As Emerging Payment Method Fin SS V
Mobile Banking Application Security Testing Tools E Wallets As Emerging Payment Method Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Present the topic in a bit more detail with this Mobile Banking Application Security Testing Tools E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Application, Evaluate, Analyze. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V
Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Database Encryption Methods For Business Security
Encryption Implementation Strategies Database Encryption Methods For Business SecurityThis slide discusses the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources. The database encryption levels are application-level encryption, plug-in method, TDE, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Database Encryption Methods For Business Security. Use it as a tool for discussion and navigation on Database Encryption Methods, Business Security, Sales And Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Introducing Methods Used By Asymmetric Algorithm To Provide Cloud Security Cloud Cryptography to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Digital Signatures, using this template. Grab it now to reap its full benefits.
-
 Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography
Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud CryptographyThis slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Increase audience engagement and knowledge by dispensing information using Methods Used By Symmetric Algorithm To Provide Cloud Security Cloud Cryptography. This template helps you present information on four stages. You can also present information on Encryption, Access Control, Key Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Integrating Security Principle With Dynamic System Development Method
Integrating Security Principle With Dynamic System Development MethodThis slide showcases incorporation of software security principles in DSDM model which helps in improving degree of project agility. It provides information regarding execution, functional model iteration, security design and security functional modulation. Introducing our Integrating Security Principle With Dynamic System Development Method set of slides. The topics discussed in these slides are Business Study, Integrating Security, Dynamic System Development. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS V
Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Methods To Ensure Smart Contract Security Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Review Fundamental Tradeoffs, using this template. Grab it now to reap its full benefits.
-
 Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS V
Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. Increase audience engagement and knowledge by dispensing information using Methods To Identify Crypto Phishing Scams Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Copycatting, Spelling, Ambiguous Links using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS V
Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Methods To Ensure Smart Contract Security BCT SS V This template helps you present information on Four stages. You can also present information on New Advancements, Careful Rolloutsm Review Fundamental Tradeoffs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Mitigation Methods Of Collaboration Tools
Cyber Security Risk Mitigation Methods Of Collaboration ToolsThe purpose of this slide is to highlight cyber security risk mitigation solutions of collaboration tools such as training employees on security awareness, contacting source, etc. Introducing our premium set of slides with Cyber Security Risk Mitigation Methods Of Collaboration Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Simulate Phishing Tests, Verify Senders Identity, Use Official Channels . So download instantly and tailor it with your information.
-
 Secure Your Digital Assets Secure Method For Storing Private Keys Offline In Paper Wallets
Secure Your Digital Assets Secure Method For Storing Private Keys Offline In Paper WalletsThis slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc. Introducing Secure Your Digital Assets Secure Method For Storing Private Keys Offline In Paper Wallets to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Paper Wallets, Crypto World, Unique Identifiers, Form Of Cold Storage, using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V
Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Monitor New Advancements using this template. Grab it now to reap its full benefits.
-
 Crypto Wallets Types And Applications Secure Method For Storing Private Keys Offline In Paper Wallets
Crypto Wallets Types And Applications Secure Method For Storing Private Keys Offline In Paper WalletsThis slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc. Increase audience engagement and knowledge by dispensing information using Crypto Wallets Types And Applications Secure Method For Storing Private Keys Offline In Paper Wallets. This template helps you present information on seven stages. You can also present information on Paper Wallets, Code For Transactions, Form Of Cold Storage, Fresh Addresses Offline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Deployment Methods Of Firewall Security System
Firewall Network Security Deployment Methods Of Firewall Security SystemThis slide represents the key applications of firewall security systems. The purpose of this slide is to showcase the different deployment options of firewall security systems, such as software-based applications, hardware-based applications, and cloud-based applications. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Deployment Methods Of Firewall Security System This template helps you present information on Three stages. You can also present information on Software Based Applications, Hardware Based Applications, Cloud Based Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods
Firewall Network Security Intrusion Prevention Systems Ipss Overview And MethodsThis slide talks about the Intrusion Prevention System and its various methods for analyzing traffic. The purpose of this slide is to give an overview of Intrusion Prevention Systems and their methods, such as signature-based detection, statistical anomaly detection, and stateful protocol analysis detection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods This template helps you present information on Three stages. You can also present information on Spyware Protection, Against Viruses, Prevents Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS V
Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Increase audience engagement and knowledge by dispensing information using Methods To Ensure Smart Contract Security Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Careful Rollouts, Contracts Simple, Fundamental Tradeoffs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Avoid Sybil Securing Blockchain Transactions A Beginners Guide BCT SS V
Methods To Avoid Sybil Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various ways to minimize and prevent Sybil attacks and ensure safe blockchain transactions. It includes elements such as identity validation, hierarchical, defense system, cost of new nodes, social trust graphs, etc. Introducing Methods To Avoid Sybil Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identity Validation, Establishing Hierarchical System, Defense System, using this template. Grab it now to reap its full benefits.
-
 Methods To Ensure Smart Securing Blockchain Transactions A Beginners Guide BCT SS V
Methods To Ensure Smart Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Increase audience engagement and knowledge by dispensing information using Methods To Ensure Smart Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Careful Rollouts, Ensure Keep Contracts Simple, Keep Updated Monitor using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Identify Crypto Securing Blockchain Transactions A Beginners Guide BCT SS V
Methods To Identify Crypto Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. Introducing Methods To Identify Crypto Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Copycatting, Spelling, Ambiguous Links, using this template. Grab it now to reap its full benefits.
-
 Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS
Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SSThis slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Increase audience engagement and knowledge by dispensing information using Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Digital Certificates, Certificates Contains, Protect Cryptographic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
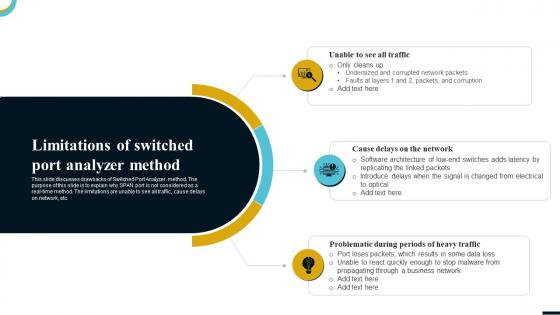 Internet Gateway Security IT Limitations Of Switched Port Analyzer Method
Internet Gateway Security IT Limitations Of Switched Port Analyzer MethodThis slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. Introducing Internet Gateway Security IT Limitations Of Switched Port Analyzer Method to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unable To See All Traffic, Cause Delays On The Network, Problematic During Periods Heavy Traffic, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Swg Implementation Methodology Span Switched
Internet Gateway Security IT Swg Implementation Methodology Span SwitchedThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Swg Implementation Methodology Span Switched to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway Rules, Deployment, Monitoring, Transparent Modes, using this template. Grab it now to reap its full benefits.
-
 Methods To Prevent And Mitigate Security Incidents
Methods To Prevent And Mitigate Security IncidentsThis slide depicts the multiple methods to prevent and mitigate security incidents. The purpose of this slide is to help the business identify a suitable approach to eliminate current and future security incidents. It includes security incident detection, tracking suspicious activity, etc. Presenting our set of slides with Methods To Prevent And Mitigate Security Incidents. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Incident, Account Behavior, Monitor Network Traffic.
-
 Methods For Enhancing Computer Server Security
Methods For Enhancing Computer Server SecurityFollowing slide showcases enhancing computer server security through different methods, also including elements such as firewalls, antivirus software, encryption, secure communications, etc. Presenting our set of slides with Methods For Enhancing Computer Server Security. This exhibits information on sevenstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intrusion Detection Systems, Antivirus Software, Secure Communications.
-
 Methods To Improve Organizational Server Security
Methods To Improve Organizational Server SecurityFollowing slide showcases improving server security in organization through various methods, also including elements such as regularly update programs, website server backup, etc. Presenting our well structured Methods To Improve Organizational Server Security. The topics discussed in this slide are Regularly Update Programs, Website Server Backup, Digital Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Different Encryption Methods To Secure Business Data
Different Encryption Methods To Secure Business DataThis slide represents various types of encryption method which assists businesses to protect data and maintain regulatory compliances. It includes different encryption methods to secure business data such as advance encryption standards, rivest shamir adleman, etc. Introducing our premium set of slides with name Different Encryption Methods To Secure Business Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Format Preserving Encryption, Blowfish, Advance Encryption Standards. So download instantly and tailor it with your information.
-
 Gamification Training Methods In Cyber Security
Gamification Training Methods In Cyber SecurityThis slide showcases the gamification training topics used in cyber security. It include details such as cybersecurity simulations, scavenger hunts, etc. Introducing our Gamification Training Methods In Cyber Security set of slides. The topics discussed in these slides are Cybersecurity Simulations, Scavenger Hunts, Cybersecurity Trivia This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Shift Left Testing Security Implementation Methods
Shift Left Testing Security Implementation MethodsThis slide showcases the tools for shift left testing.Its aim is to deploy and reinforce security code base and increase security.This slide includes static application system testing, dynamic application security.Presenting our set of slides with Shift Left Testing Security Implementation Methods This exhibits information on four stages of the process.This is an easy to edit and innovatively designed PowerPoint template.So download immediately and highlight information on Remediate Seamlessly, Immediate Remediation, Environment.
-
 Mobile Device Security Methods For Advanced Protection
Mobile Device Security Methods For Advanced ProtectionThis slide displays mobile device security methods to protect networks and includes CASB, endpoint protection, VPN, and secure web gateway. Presenting our set of slides with name Mobile Device Security Methods For Advanced Protection. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Endpoint Protection, Casb, Vpn, Secure Web Gateway.
-
 Methods To Test Security Gaps For Enhanced Safety
Methods To Test Security Gaps For Enhanced SafetyThis slide covers slide showcases security gap analysis test methods for enhanced safety. It further covers testing techniques such as active, passive, network and distributed testing. Presenting our set of slides with name Methods To Test Security Gaps For Enhanced Safety. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Active Testing, Network Testing, Passive Testing, Distributed Testing.
-
 ACH Payment Method Overview With Key Benefits Enhancing Transaction Security With E Payment
ACH Payment Method Overview With Key Benefits Enhancing Transaction Security With E PaymentFollowing slide provides overview of ACH Automated Clearing House payment methods leveraged by organisations to make recurring business transactions. It includes key components such as description, types and advantages of ACH payment. Increase audience engagement and knowledge by dispensing information using ACH Payment Method Overview With Key Benefits Enhancing Transaction Security With E Payment This template helps you present information on four stages. You can also present information on Business Bank, Customer Bank, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ACH Payment Methods Key Statistics Enhancing Transaction Security With E Payment
ACH Payment Methods Key Statistics Enhancing Transaction Security With E PaymentFollowing slide provides key insights into key statistics associated with Automated clearing house which refer to ACH payment growth in market. It includes key points such as payment transfer, transaction value, b2b transaction, and number of transactions made. Introducing ACH Payment Methods Key Statistics Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Salaries And Pensions, Transaction using this template. Grab it now to reap its full benefits.
-
 Buy Now Pay Later Payment Method Overview Enhancing Transaction Security With E Payment
Buy Now Pay Later Payment Method Overview Enhancing Transaction Security With E PaymentMentioned slide provides summary of BNPL Buy Now Pay Later cashless payment option which can be leverages by business to increase product sales. It includes key components such as description, types and popular BNPL software solutions. Increase audience engagement and knowledge by dispensing information using Buy Now Pay Later Payment Method Overview Enhancing Transaction Security With E Payment This template helps you present information on six stages. You can also present information on Popular BNPL Software, BNPL Option using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cashless Payments Methods Offered By Business Enhancing Transaction Security With E Payment
Cashless Payments Methods Offered By Business Enhancing Transaction Security With E PaymentMentioned slide provides information about various cashless payment methods which can be adopted by businesses to increase organizational revenue. It includes various payments such as cheque and demand draft, net banking, cards, mobile wallet, QR codes, ACH, cryptocurrency, etc. Introducing Cashless Payments Methods Offered By Business Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cheque, Credit And Debit Card, Mobile Wallet using this template. Grab it now to reap its full benefits.
-
 Impact Of Implementing Gift Card Method Enhancing Transaction Security With E Payment
Impact Of Implementing Gift Card Method Enhancing Transaction Security With E PaymentFollowing slide provides information about key impacts of leveraging gift card cashless payment options on business growth. It includes key metrices such as brand awareness, business revenue, customer engagement, stock clearance, and cash flow ratio. Deliver an outstanding presentation on the topic using this Impact Of Implementing Gift Card Method Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Brand Awareness, Business Revenue, Customer Engagement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Categories Of ACH Payment Method Enhancing Transaction Security With E Payment
Major Categories Of ACH Payment Method Enhancing Transaction Security With E PaymentMentioned slide provides information about two types of Automated Clearing House ACH which can be leveraged by businesses. It includes major categories such as ACH direct payment and ACH direct deposit. Increase audience engagement and knowledge by dispensing information using Major Categories Of ACH Payment Method Enhancing Transaction Security With E Payment This template helps you present information on two stages. You can also present information on Pull Payment, Funds Are Pulled Bank Accounts, Electronically Payment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of QR Code Payment Methods Enhancing Transaction Security With E Payment
Overview Of QR Code Payment Methods Enhancing Transaction Security With E PaymentMentioned slide provides summary of Quick Response code payment methods which can be used by businesses to improve payment speed. It includes key components such as description, types, and used cade of QR code payment. Introducing Overview Of QR Code Payment Methods Enhancing Transaction Security With E Payment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on E Commerce Purchase, E Ticket Booking, Park Payment using this template. Grab it now to reap its full benefits.
-
 Preferred Cashless Payment Method By Target Audience Enhancing Transaction Security With E Payment
Preferred Cashless Payment Method By Target Audience Enhancing Transaction Security With E PaymentMentioned slide provides information about cashless payment methods used by customers of different age group which can be used by businesses for selection appropriate payment system. It includes key component such as age range, generation, preferred payment and method, and comments. Present the topic in a bit more detail with this Preferred Cashless Payment Method By Target Audience Enhancing Transaction Security With E Payment Use it as a tool for discussion and navigation on Generation, Payment Method, Technologies This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of QR Code Methods For Online Payment Enhancing Transaction Security With E Payment
Types Of QR Code Methods For Online Payment Enhancing Transaction Security With E PaymentMentioned slide illustrates multiple types of QR code payment which can be used by businesses to offer touchfree payment solutions to customers. It includes key types such as static QR codes, and dynamic QR codes Deliver an outstanding presentation on the topic using this Types Of QR Code Methods For Online Payment Enhancing Transaction Security With E Payment Dispense information and present a thorough explanation of Description, Application, Static QR Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Encryption Method In Application Security
Data Encryption Method In Application SecurityThis slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Increase audience engagement and knowledge by dispensing information using Data Encryption Method In Application Security. This template helps you present information on five stages. You can also present information on Encodes Plaintext To Ciphertext, Decryption Needs Specific Keys, Create Cryptographic Models using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Provide Mobile Information Security
Methods To Provide Mobile Information SecurityThis slide showcases practices for ensuring mobile data protection. The purpose of this template is to help users in reducing the risk of data breaches and unauthorized access for their mobile device. It includes elements such as avoid rooting, manage permissions, etc. Presenting our set of slides with Methods To Provide Mobile Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Install Trusted Apps, Manage Permissions, Use VPN For Public WIFI
-
 Third Party Risk Management Methods In Information Security
Third Party Risk Management Methods In Information SecurityThis slide highlights strategies to control third-party risk in information security. The purpose of this slide is to aid organizations in identifying areas for improvement in their security practices. It includes elements such as vendor assessment, risk classification, etc. Presenting our set of slides with Third Party Risk Management Methods In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Assessment, Contractual Agreements, Maintain Records, Risk Classification
-
 Security Methods For Implementing Email Encryption
Security Methods For Implementing Email EncryptionThis slide outlines the security methods for implementing email encryption which includes encrypted PDFs secure attachments, web portal encryption, etc. Introducing our premium set of slides with Security Methods For Implementing Email Encryption. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Attachments, Web Portal, Gateway Software. So download instantly and tailor it with your information.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




