Powerpoint Templates and Google slides for Security Flow Chart
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Physical Security Process Flow Chart
Physical Security Process Flow ChartThis slide showcases flow chart of physical security that includes determining need, identifying threats, elements of protection system, verification, testing and handing over. Presenting our set of slides with Physical Security Process Flow Chart. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Security Need, Facility Characterization, Identify Potential Threats.
-
 SIEM Cyber Security Kill Chain Flow Chart
SIEM Cyber Security Kill Chain Flow ChartThis slide showcases the SIEM cyber security kill chai flow chart. Its aim is to show SIEM architecture and alert new messages. This slide includes ping scanning, telnet, DoS attack, malware, intrusion, etc. Presenting our set of slides with name SIEM Cyber Security Kill Chain Flow Chart. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ping Scanning, Nmap Scanning, Telnet Connection.
-
 Security Flow Chart In Powerpoint And Google Slides Cpp
Security Flow Chart In Powerpoint And Google Slides CppPresenting Security Flow Chart In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Flow Chart. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Business Application Security Testing Flow Chart
Business Application Security Testing Flow ChartThis slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing. Introducing our Business Application Security Testing Flow Chart set of slides. The topics discussed in these slides are Business Application, Security Testing, Flow Chart. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats
Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File FormatsThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Ppt Powerpoint Presentation Model File Formats. Dispense information and present a thorough explanation of Instrumentation, Agency User Reporting, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
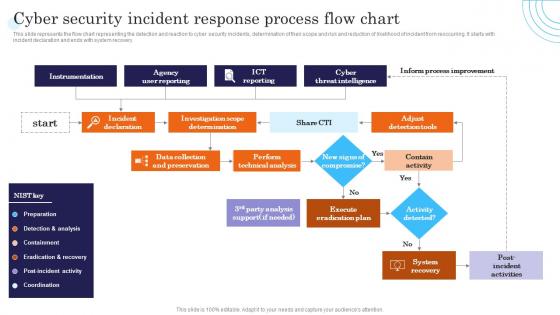 Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment
Cyber Security Incident Response Process Flow Chart Incident Response Strategies DeploymentThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Incident Response Strategies Deployment. This template helps you present information on one stages. You can also present information on Instrumentation, Agency, Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security
Cyber Security Incident Response Process Flow Chart Development And Implementation Of SecurityThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response Process Flow Chart Development And Implementation Of Security. Dispense information and present a thorough explanation of Data Collection And Preservation, Perform Technical Analysis, Incident Declaration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan
Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response PlanThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Present the topic in a bit more detail with this Cyber Security Incident Response Process Flow Chart Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Agency User Reporting, Instrumentation, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management
Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident ManagementThis slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery.Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Response Process Flow Chart Deploying Computer Security Incident Management. This template helps you present information on Two stages. You can also present information on Agency Reporting, Investigation Scope Determination, Collection Preservation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Threat Management Flow Chart
Cyber Security Threat Management Flow ChartThis slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Introducing our Cyber Security Threat Management Flow Chart set of slides. The topics discussed in these slides are Threat Analysis, Residual Risk Acceptable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Succession chart flow with financial security and plan dissemination
Succession chart flow with financial security and plan disseminationPresenting succession chart flow with financial security and plan dissemination. This is a succession chart flow with financial security and plan dissemination. This is a three stage process. The stages in this process are succession chart, succession graph, progression chart.
-
 Clock team leader security supervisor flow chart ppt icons graphics
Clock team leader security supervisor flow chart ppt icons graphicsPresenting clock team leader security supervisor flow chart ppt icons graphics. This Power Point icon template diagram has been crafted with graphic of clock, team and flow chart icons. This icon template diagram contains the concept of team leadership and security supervision. Use this icon template diagram for business and finance related presentations.
-
 Data loss prevention flow chart for enterprise security
Data loss prevention flow chart for enterprise securityPresenting this set of slides with name Data Loss Prevention Flow Chart For Enterprise Security. This is a one stage process. The stages in this process are Data, Statistics, Analyzer, Employees, Service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.



