Powerpoint Templates and Google slides for Security Detection
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides
Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Enterprise Mobile Security For On Device Threat Detection Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of sixty three slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Detective Controls In Application Security Training Ppt
Detective Controls In Application Security Training PptPresenting Detective Controls in Application Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Network Behavior Anomaly Detection As An Element Of Network Security Training Ppt
Network Behavior Anomaly Detection As An Element Of Network Security Training PptPresenting Network Behavior Anomaly Detection as an Element of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Intrusion Detection Systems IDS For Network Security Training Ppt
Intrusion Detection Systems IDS For Network Security Training PptPresenting Intrusion Detection Systems IDS for Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Detection As An Element Of Endpoint Security Training Ppt
Detection As An Element Of Endpoint Security Training PptPresenting Detection as an Element of Endpoint Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Three clusters parallel network detection security cloud native monetization digital capabilities
Three clusters parallel network detection security cloud native monetization digital capabilitiesIf you require a professional template with great design, then this Three Clusters Parallel Network Detection Security Cloud Native Monetization Digital Capabilities is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Triage Security Dashboard To Detect Cybersecurity Issues
Triage Security Dashboard To Detect Cybersecurity IssuesThis slide represents triage cyber security dashboard to detect cybersecurity issues which is utilized by organizations to investigate its endpoints and detect cyber threats. It includes key components such as total incidents count, level of threat, etc Introducing our Triage Security Dashboard To Detect Cybersecurity Issues set of slides. The topics discussed in these slides are Incident Trend By Level, Classification Of Incidents, Top Attackers. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
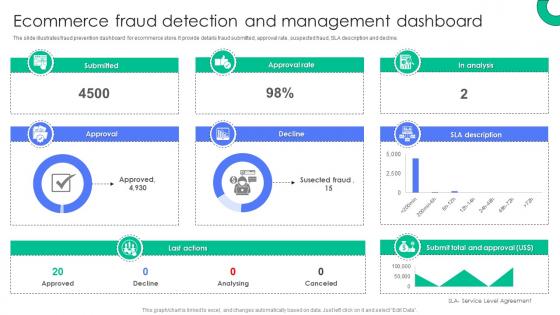 Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security MeasuresThe slide illustrates fraud prevention dashboard for ecommerce store. It provide details fraud submitted, approval rate, suspected fraud, SLA description and decline. Present the topic in a bit more detail with this Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Submitted, Approval, Approval Rate, Decline, Last Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
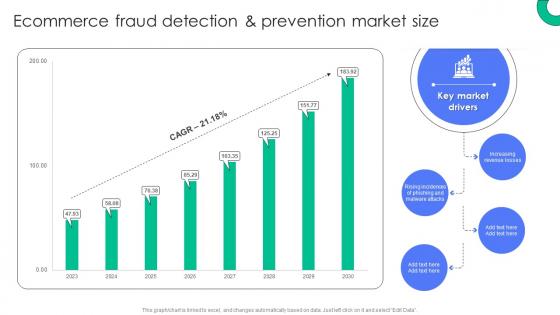 Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security MeasuresDeliver an outstanding presentation on the topic using this Ecommerce Fraud Detection And Prevention Market Size Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Increasing Revenue Losses, Key Market, Drivers, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
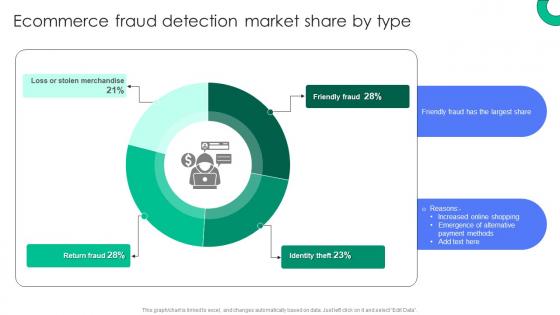 Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures
Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security MeasuresPresent the topic in a bit more detail with this Ecommerce Fraud Detection Market Share By Type Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Identity Theft, Friendly Fraud, Return Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS
Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SSThis slide showcases mobile malware threats globally faced by the users. It also sites key reasons for mobile malware that are lack of security awareness, inadequate security practices etc. Present the topic in a bit more detail with this Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Security Awareness, Exploitation Of Vulnerabilities, Inadequate Security Practices This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Dashboard For Threat Detection And Response
Network Security Dashboard For Threat Detection And ResponseThis slide illustrates KPI Dashboard of network security including attack type, authentication, firewall events, and attack rates. Introducing our Network Security Dashboard For Threat Detection And Response set of slides. The topics discussed in these slides are Attack Type, Authentication, Firewall Events. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Airport Security Detection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Airport Security Detection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for illustrating airport detection. It features a detailed image of an airport with a radar tower and a plane flying above it. It is ideal for presentations and other projects.
-
 Airport Security Detection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Airport Security Detection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon depicts an airport with a plane in the sky and a control tower in the background. It is perfect for presentations about air travel, air safety, or airport operations. It can also be used to represent the concept of detection or surveillance.
-
 Home Security Smoke Detector Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Home Security Smoke Detector Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of a smoke detector. It features a yellow and black design, with a smoke detector in the center. It is a great addition to presentations on safety, security and fire prevention.
-
 Home Security Smoke Detector Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Home Security Smoke Detector Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a perfect representation of a smoke detector. It features a black and white design with a smoke detector in the center, making it a great visual for presentations on fire safety and smoke detector maintenance.
-
 Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations
Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve OrganizationsThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Malware, Application, using this template. Grab it now to reap its full benefits.
-
 Smoke Security Detector Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Smoke Security Detector Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of a smoke detector. It features a yellow and black design, with a smoke detector in the center. It is a great addition to presentations on safety, security and fire prevention.
-
 Smoke Security Detector Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Smoke Security Detector Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon is a perfect representation of a smoke detector. It features a black and white design with a smoke detector in the center, making it a great visual for presentations on fire safety and smoke detector maintenance.
-
 Host Intrusion Detection System For Security
Host Intrusion Detection System For SecurityThis slide highlights security benefits for host intrusion detection system. This further includes benefits such as evaluate traffic, threat intelligence and intrusion notification. Introducing our Host Intrusion Detection System For Security set of slides. The topics discussed in these slides are Evaluate Traffic, Threat Intelligence, Intrusion Notification. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Layered Defence Security Icon For Threat Detection
Layered Defence Security Icon For Threat DetectionPresenting our set of slides with Layered Defence Security Icon For Threat Detection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Layered Defence Security, Icon For Threat Detection.
-
 Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS
Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SSThis slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities. It includes three stages such as monitoring stage, analysing stage and detection stage.Present the topic in a bit more detail with this Intrusion Detection Using Ai And Ml In IoT Ecosystem IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Features Extraction, Anomaly Detection, Pattern Signature. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS
Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SSThis slide exhibits two types of intrusion detection systems that may be deployed to provide layered security and enhance business operations. It includes two types of intrusion detection system such as network intrusion detection system and host intrusion detection system. Present the topic in a bit more detail with this Types Of Intrusion Detection System IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Network Intrusion, Best Suitable, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Big Data Attack Detection Model In Cyber Security
Big Data Attack Detection Model In Cyber SecurityThis slide visualises the detection models used in defending cyber security in big data. Its aim is to detect any malicious attack. This slide includes training data, data preparation, testing, attack detection model, etc. Introducing our Big Data Attack Detection Model In Cyber Security set of slides. The topics discussed in these slides are Network, Activity, Application. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ATP Cyber Security Threat Detection System
ATP Cyber Security Threat Detection SystemThis slide depicts the ATP cyber security detection system. Its aim is to use various approach to kill off any threats during cyber attack. This slide includes multilayer approach, behavioural analysis, machine learning, sand boxing, threat intelligence, etc. Presenting our set of slides with name ATP Cyber Security Threat Detection System. This exhibits information on Nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multilayered Approach, Behavioural Analysis, Machine Learning, Threat Intelligence, Endpoint Detection.
-
 Threat Detection Icon To Manage Security Gap
Threat Detection Icon To Manage Security GapPresenting our set of slides with name Threat Detection Icon To Manage Security Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Detection Icon, Manage Security Gap.
-
 Comparison Between Preventive And Detective Controls In Cyber Security
Comparison Between Preventive And Detective Controls In Cyber SecurityThis slide represents the comparison between preventative controls and detective controls in cyber security to prevent potential threats and secure data. It includes preventative controls and detective controls Presenting our set of slides with Comparison Between Preventive And Detective Controls In Cyber Security This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preventative Control, Detective Control
-
 Types Of Detective Controls Cyber Security
Types Of Detective Controls Cyber SecurityThis slide represents the types of detective controls used in cyber security to prevent data breach by unauthorized access or online attack. It includes various steps such as log monitoring, SIEM, trend analysis, etc. Introducing our premium set of slides with Types Of Detective Controls Cyber Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trend Analysis, Security Audits, Log Monitoring So download instantly and tailor it with your information.
-
 Intrusion Prevention VS Detection Under NIPS Cyber Security
Intrusion Prevention VS Detection Under NIPS Cyber SecurityThis slide highlights the comparison between intrusion detection systems and intrusion prevention systems. The purpose of this slide is to help the business determine its business needs and implement suitable processes. It includes comparison on the basis of location, use, etc. Presenting our well structured Intrusion Prevention VS Detection Under NIPS Cyber Security The topics discussed in this slide are Description, Location, False Positive This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Filter Spam Detection In Email Security
Filter Spam Detection In Email SecurityThis slide explains the process of filter spam detection which includes red flag analysis, bad IP address, poor domain reputation, bulk sending and suspicious languages. Introducing our premium set of slides with Filter Spam Detection In Email Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Flag Analysis, IP Address, Bulk Sending. So download instantly and tailor it with your information.
-
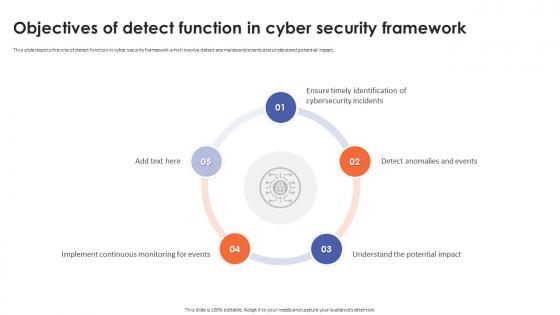 Objectives Of Detect Function In Cyber Security Framework
Objectives Of Detect Function In Cyber Security FrameworkThis slide depicts the role of detect function in cyber security framework which involve detect anomalies and events and understand potential impact. Introducing Objectives Of Detect Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Continuous Monitoring For Events, Understand The Potential Impact, Detect Anomalies And Events, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security
Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint SecurityThis slide highlights the introduction of Intrusion Detection and Prevention System IDPS in endpoint security for preventing threats. Increase audience engagement and knowledge by dispensing information using Endpoint Security Intrusion Detection And Prevention System Idps In Endpoint Security. This template helps you present information on six stages. You can also present information on Alerts And Remediates Threat, Stop Detected Threats, Monitors Networks For Threats, Intrusion Detection And Prevention System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Detection Icon Indicator Visualization Security
Threat Detection Icon Indicator Visualization SecurityIntroducing our premium set of slides with Threat Detection Icon Indicator Visualization Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection, Indicator Visualization Security. So download instantly and tailor it with your information.
-
 Detection Methods Utilized In Hids Cyber Security
Detection Methods Utilized In Hids Cyber SecurityThis slide represents detection methods utilized in HIDS cyber security which assists to log all activities and malicious activities. It includes detection methods utilized in HIDS cyber security such as signature based detection and anomaly based detection. Presenting our well structured Detection Methods Utilized In Hids Cyber Security. The topics discussed in this slide are Anomaly Based Detection, Signature Based Detection, Comprehensive. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Phases Of SIEM Cyber Security Detection
Phases Of SIEM Cyber Security DetectionThis slide showcases the phases of SIEM cyber security. Its objective is to detect and investigate data logs. This slide includes alerts, respond, data normalisation, investigation and evidence. Presenting our set of slides with name Phases Of SIEM Cyber Security Detection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Solutions, Problems, Business.
-
 Methods Of NIDS Detection In Cyber Security
Methods Of NIDS Detection In Cyber SecurityThis slide represents approaches for identifying NIDS in cyber security. It aims to ensure that NIDS identify, analyze, and respond to cyber security threats within network Presenting our set of slides with Methods Of NIDS Detection In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detection Of Anomalies, Detection Based On Signatures, Hybrid Detection.
-
 NIDS Technologies To Detect Cyber Security Breach
NIDS Technologies To Detect Cyber Security BreachThis slide represents NIDS equipment used to identify cyber security vulnerabilities. It aims to detect, identify, and respond to security breaches and threats within network to mitigate risks. Introducing our premium set of slides with NIDS Technologies To Detect Cyber Security Breach. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Protocols, Applications, Operating Systems. So download instantly and tailor it with your information.
-
 Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SSThis slide represents details related to training plan to assist employees in detecting phishing attacks. It includes details related to training topics such as general signs of phishing attacks etc. Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Manufactured Rapport Or History, Manufactured Urgency, Sensitive Questions As Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS
Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SSThis slide represents training plan for detecting to malware that is designed to deny a user or organization access to files on their computer or networks. It includes details related to detection techniques etc. Deliver an outstanding presentation on the topic using this Training Plan For Detecting Ransomware Attacks IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Signature Based Detection, Detection Based On Traffic, Detection By Data Behavior using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Operations Dashboard For Detection And Response Effectiveness
Security Operations Dashboard For Detection And Response EffectivenessThis slide exhibits security operations dashboard. It include positive incidents, false positive incidents, false positive risk score, false positive security incident etc. Introducing our Security Operations Dashboard For Detection And Response Effectiveness set of slides. The topics discussed in these slides are Security Operations Dashboard, Detection, Response Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Detection security ppt powerpoint presentation portfolio ideas cpb
Detection security ppt powerpoint presentation portfolio ideas cpbPresenting Detection Security Ppt Powerpoint Presentation Portfolio Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Detection Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model Cpb
Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model CpbPresenting our Cyber Security Fraud Detection Ppt Powerpoint Presentation Layouts Model Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Fraud Detection. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Operational Technology Icon For Security Threat Detection
Operational Technology Icon For Security Threat DetectionIntroducing Operational Technology Icon For Security Threat Detection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Operational Technology Icon For Security Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Managed Security Service Threat Detection Process
Managed Security Service Threat Detection ProcessThe following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Introducing our premium set of slides with Managed Security Service Threat Detection Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Event Resolution, Operational Readiness Review, Email Notification, Security Analysis. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Detection And Prevention Of Management Security Controls
Enterprise Risk Management Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Increase audience engagement and knowledge by dispensing information using Enterprise Risk Management Detection And Prevention Of Management Security Controls. This template helps you present information on two stages. You can also present information on Preventive Management, Security Controls, Detection Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Management Response Steps After Detecting Security Event
Incident Management Response Steps After Detecting Security EventPresenting our set of slides with Incident Management Response Steps After Detecting Security Event. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assembling Team, Detecting And Ascertaining Source, Containing Damage.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
B132 Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionIntroducing B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Determine Standard, Various Configuration, Features Associated, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Enterprise Mobile Security For On Device Threat Detection
Icons Slide For Enterprise Mobile Security For On Device Threat DetectionPresenting our well crafted Icons Slide For Enterprise Mobile Security For On Device Threat Detection set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionPresent the topic in a bit more detail with this Table Of Contents For Enterprise Mobile Security For On Device Threat Detection. Use it as a tool for discussion and navigation on Impact Assessment, Dashboard Assessment, Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats
Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Introducing Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Network Protection, User Protection, using this template. Grab it now to reap its full benefits.
-
 Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls
Risk Assessment Of It Systems Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Present the topic in a bit more detail with this Risk Assessment Of It Systems Detection And Prevention Of Management Security Controls. Use it as a tool for discussion and navigation on Prevention, Management, Security Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
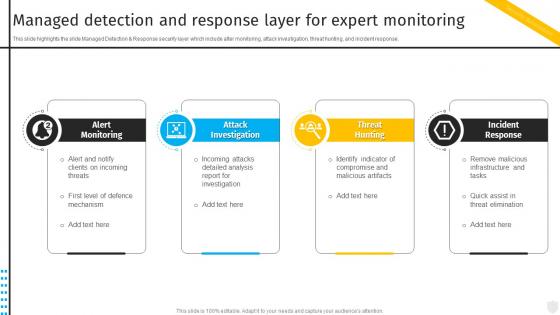 Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate Cyberthreats
Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Attack Investigation, Incident Response, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
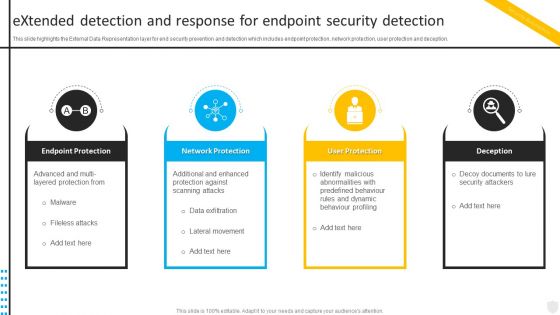
 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
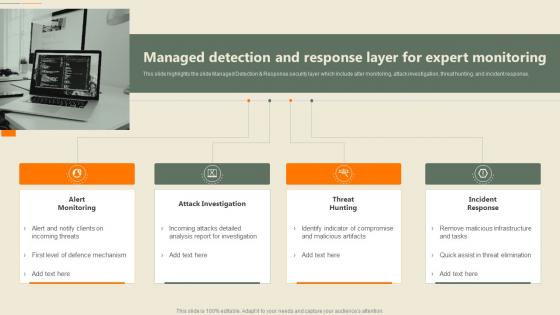 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional Background
Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional BackgroundThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Introducing Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional Background to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Threat Intelligence, Intruder Traps, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
 Implementing Cyber Security Ways To Detect Cyber Security Incidents Ppt Designs
Implementing Cyber Security Ways To Detect Cyber Security Incidents Ppt DesignsThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Implementing Cyber Security Ways To Detect Cyber Security Incidents Ppt Designs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Changes In Configuration, Unknown Locations, Cyber Security Incidents, using this template. Grab it now to reap its full benefits.
-
 Various Cyber Security Incidents Detected By It Department Ppt Themes
Various Cyber Security Incidents Detected By It Department Ppt ThemesThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Various Cyber Security Incidents Detected By It Department Ppt Themes. This template helps you present information on five stages. You can also present information on Phishing Attack, Malware Attack, Password Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
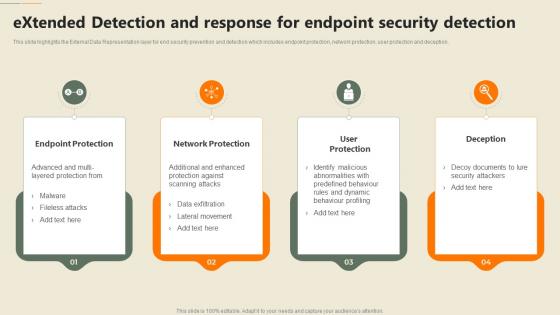
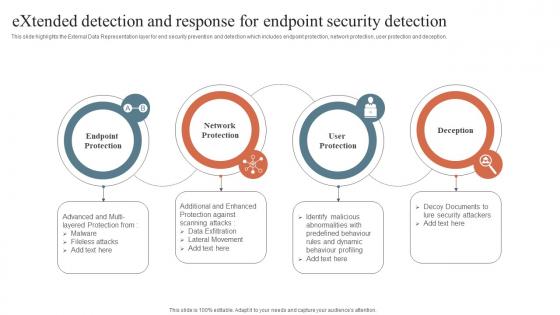 Security Orchestration Automation Extended Detection And Response For Endpoint Security Detection
Security Orchestration Automation Extended Detection And Response For Endpoint Security DetectionThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Introducing Security Orchestration Automation Extended Detection And Response For Endpoint Security Detection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Protection, Endpoint Protection, User Protection, using this template. Grab it now to reap its full benefits.




