Powerpoint Templates and Google slides for Security Deployment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Deploying Computer Security Incident Management Powerpoint Presentation Slides
Deploying Computer Security Incident Management Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Deploying Computer Security Incident Management Powerpoint Presentation Slides V is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Data security it prepare and deploy strong it policies ppt slides deck
Data security it prepare and deploy strong it policies ppt slides deckThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Data Security IT Prepare And Deploy Strong IT Policies Ppt Slides Deck. Use it as a tool for discussion and navigation on Build Strong, IT Policies, Required Security Software, Content Sharing, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
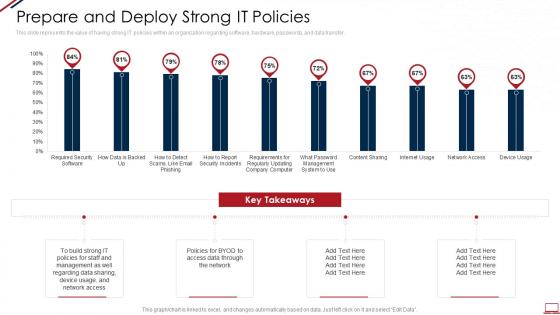 Computer system security prepare and deploy strong it policies
Computer system security prepare and deploy strong it policiesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Present the topic in a bit more detail with this Computer System Security Prepare And Deploy Strong It Policies. Use it as a tool for discussion and navigation on Prepare And Deploy Strong IT Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway
Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web GatewayThis slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Increase audience engagement and knowledge by dispensing information using Different Types Of Secure Web Gateway Deployment Network Security Using Secure Web Gateway. This template helps you present information on three stages. You can also present information on Deployment, Businesses, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V
Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS VThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents It covers details regarding issues by control type, risk categories, etc Deliver an outstanding presentation on the topic using this Ict Business Security Kpi Dashboard Comprehensive Guide For Deployment Strategy SS V Dispense information and present a thorough explanation of Risk Categories, Control Review Status, Standard Control Issues using the slides given This template can be altered and personalized to fit your needs It is also available for immediate download So grab it now
-
 Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS V
Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS VThis slide represents essential information and communication technology ICT security measures businesses use It covers strong password authentication, data backup, network access control, etc Presenting our well structured Key Ict Security Measures Used By Comprehensive Guide For Deployment Strategy SS V The topics discussed in this slide are Authentication Security, Most Businesses, Protect Against This is an instantly available PowerPoint presentation that can be edited conveniently Download it right away and captivate your audience
-
 Firewall Network Security Global Firewall Market Segmentation By Deployment And Solution
Firewall Network Security Global Firewall Market Segmentation By Deployment And SolutionThis slide provides an overview of global firewall market categorization based on deployment and solution type. The purpose of this slide is to showcase the firewall market share based on deployment types and solution type, such as software and hardware services. Deliver an outstanding presentation on the topic using this Firewall Network Security Global Firewall Market Segmentation By Deployment And Solution Dispense information and present a thorough explanation of Oragnisation Size Segment Overview, Regional Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Wireless Internet Security Us Market Size By Deployment
Wireless Internet Security Us Market Size By DeploymentThe following slide presents data on expected CAGR, deployment methods cloud, on-premise, security adoption trends, and more to depict the size and dynamics of the wireless internet security market in the United States, aiding in market analysis and decision-making. Presenting our well structured Wireless Internet Security Us Market Size By Deployment. The topics discussed in this slide are Deployment, Professional, Growth. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS
Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SSThis slide showcases secure socket layer SSL deployment which can help employees perform secure communication within businesses. It provides details about certificate authority, webmaster, etc. Present the topic in a bit more detail with this Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Message Forgery, Reduced Data Theft, Less Eavesdropping. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model
As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Present the topic in a bit more detail with this As A Service Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Other ZTNA Architecture Deployment Approaches Zero Trust Security Model
Other ZTNA Architecture Deployment Approaches Zero Trust Security ModelThis slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Deliver an outstanding presentation on the topic using this Other ZTNA Architecture Deployment Approaches Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced Identity Governance, Micro Segmentation, Software Defined Network Perimeters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present the topic in a bit more detail with this Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations
Cyber Security Risk Assessment And Technology Deployment Plan To Improve OrganizationsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations. Dispense information and present a thorough explanation of Consequences, Vulnerability, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations
Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve OrganizationsThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Malware, Application, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB Model
Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB ModelThis slide represents the 30-0-90 days plan to implement the Cloud Access Security Broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Introducing Cloud Access Security Broker CASB V2 30 60 90 Days Plan To Deploy CASB Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Scope, Current Security Architecture, Security Operations Center Functions, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based Deployment
Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based DeploymentThis slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Advantages And Disadvantages Of Proxy Based Deployment. This template helps you present information on two stages. You can also present information on Cloud Access Security Brokers, Cover Flexibility, Secure SaaS Applications, Enforcement Of Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB Deployment
Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB DeploymentThis slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 API Based Use Cases Of CASB Deployment. Dispense information and present a thorough explanation of Malware In Cloud Services, Data Transfer Policies, Cloud Services, Auditing User Access Provisioning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model
Cloud Access Security Broker CASB V2 API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Corporate Devices, Facilitate Communication, Real Time Protection, Non Intrusive Security Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components PricingThis slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Deployment With Optional Components Pricing. Dispense information and present a thorough explanation of Data Security Subscription, Threat Protection Subscription, Data Retention, Customer Relationship Admins using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing
Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components PricingThis slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 CASB Deployment With Standard Components Pricing. Use it as a tool for discussion and navigation on Pricing Of Classic Elements, Components Include Visibility, Threat Protection, Data Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use Cases
Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use CasesThis slide highlights the main use cases of forward proxy server CASB deployment. The main purpose of this slide is to showcase the primary use cases of the forward proxy, including implementing granular access and activity controls and detecting show IT in the network. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 CASB Forward Proxy Deployment Use Cases. This template helps you present information on two stages. You can also present information on Deploying Granular Access, Activity Controls, Detecting Shadow, IT In The Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 CASB Reverse Proxy Deployment Use Cases
Cloud Access Security Broker CASB V2 CASB Reverse Proxy Deployment Use CasesThis slide illustrates the use cases of reverse proxy server deployment of the Cloud Access Security Broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. Introducing Proxy to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Reverse Proxy Server Deployment, Cloud Access Security Broker, Reverse Proxy Deployment, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working. Use it as a tool for discussion and navigation on Deployment Overview And Working, Web Servers They Visit, Forward Proxy Method Is A Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models
Cloud Access Security Broker CASB V2 Overview Of CASB Deployment ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Unmanaged Gadgets, Inline Deployment, Scalable And Strong Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment
Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server DeploymentThis slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Introducing Cloud Access Security Broker CASB V2 Primary Types Of Reverse Proxy Server Deployment to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Regular Reverse Proxies, Load Balancers, Proxy Server Deployment, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment
Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB DeploymentThis slide outlines the advantages and disadvantages of the API scanning Cloud Access Security Broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pros And Cons Of API Scanning CASB Deployment. This template helps you present information on one stages. You can also present information on Cloud Access Security, Broker Deployment Model, Scanning Deployment Model, Security Policy Modifications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Proxy Based Implementation, Proxy Deployment, Proxy And Reverse Proxy, Operation Of Several using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB
Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASBThis slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Proxy Based Vs API Based Deployment Of CASB. Use it as a tool for discussion and navigation on Performance And Security, Proxy Based Deployment, Standalone Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model. This template helps you present information on five stages. You can also present information on Reverse Proxy, Cloud Access Security Model Broker, Web Server Anonymity, Websites With High Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security BrokerThis slide outlines the steps to implement a Cloud Access Security Broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Steps To Deploy Cloud Access Security Broker. This template helps you present information on one stages. You can also present information on Speedier Installation, Comprehensive Coverage, Cloud Access Security Broker using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment
Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server DeploymentThis slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment. Dispense information and present a thorough explanation of Proxy Server Deployment, Central Proxy Server, Proxy Server Implementation, Data Center Proxies Work using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management
Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks ManagementThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool name, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Determines Suspicious, Features, Cyber Security Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS V
Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS VThis slide represents key access security control models for organizations It includes discretionary access control, mandatory access control, role based access control and attributes based access control,Present the topic in a bit more detail with this Key Access Security Control Models Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Mandatory Access, Discretionary Access, Administrator Protected This template is free to edit as deemed fit for your organization Therefore download it now
-
 Most Commonly Types Of Ict Securities Used Comprehensive Guide For Deployment Strategy SS V
Most Commonly Types Of Ict Securities Used Comprehensive Guide For Deployment Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses It covers network security, endpoint security, access security, and data encryption Increase audience engagement and knowledge by dispensing information using Most Commonly Types Of Ict Securities Used Comprehensive Guide For Deployment Strategy SS V This template helps you present information on four stages You can also present information on Network Security, End Point Security, Access Security using this PPT design This layout is completely editable so personaize it now to meet your audiences expectations
-
 Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS V
Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS VThis slide represents the network security model for effective communication in the organization It covers information regarding security threats, firewalls, virtual private networks, etc Present the topic in a bit more detail with this Network Security Model To Effective Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Protection Computer, Components Detect, Information Channel This template is free to edit as deemed fit for your organization Therefore download it now
-
 Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V
Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS VThis slide represents overview of ICT information and communication technology business security It covers types and features for security such as network security, endpoint security etc Present the topic in a bit more detail with this Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Unauthorized Sources, Factor Authentication, Organizations Information This template is free to edit as deemed fit for your organization Therefore download it now
-
 Deploy Network Layer Firewall For Enforcing Security Policies
Deploy Network Layer Firewall For Enforcing Security PoliciesThis slide focuses on network layer firewall by controlling and monitoring cyber threats and enforcing access policies. It includes aspects such as non web attack, web attack, legitimate traffic, etc. Introducing our Deploy Network Layer Firewall For Enforcing Security Policies set of slides. The topics discussed in these slides are Operation Mode, Transparent Mode, Routed Mode. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Secure Continuous Deployment Pipeline
Best Practices To Secure Continuous Deployment PipelineThis slide represents continuous deployment pipeline best practices. It aims to conduct consistent comprehensive audits on system and code to control high level security and minimize risk of cyberattack. It includes various elements such as eliminating hardcoded credentials from tools, restricting access to non humans, etc. Presenting our set of slides with Best Practices To Secure Continuous Deployment Pipeline. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Reduce, Security, Human.
-
 Steps To Deploy Cloud Access Security Broker Next Generation CASB
Steps To Deploy Cloud Access Security Broker Next Generation CASBThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Introducing Steps To Deploy Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Location, Deployment Model, Release Model using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Deployment Methods Of Firewall Security System
Firewall Network Security Deployment Methods Of Firewall Security SystemThis slide represents the key applications of firewall security systems. The purpose of this slide is to showcase the different deployment options of firewall security systems, such as software-based applications, hardware-based applications, and cloud-based applications. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Deployment Methods Of Firewall Security System This template helps you present information on Three stages. You can also present information on Software Based Applications, Hardware Based Applications, Cloud Based Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Devsecops Pipeline Continuous Deployment Acceptance Stage
Devsecops Best Practices For Secure Devsecops Pipeline Continuous Deployment Acceptance StageThis slide discusses the continuous deployment acceptance stage of the DevSecOps pipeline. The purpose of this slide is to explain the acceptance phase and its security check, which includes thorough fuzz testing, dynamic application security testing, and so on. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Devsecops Pipeline Continuous Deployment Acceptance Stage. Dispense information and present a thorough explanation of Thorough Fuzz Testing, Dynamic Application Security Testing, In Depth Static Analysis, Manual Security Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Devsecops Pipeline Production Post Deployment Stage
Devsecops Best Practices For Secure Devsecops Pipeline Production Post Deployment StageThis slide discusses the production post-deployment stage of the DevSecOps pipeline. The purpose of this slide is to explain the post-deployment phase and the responsibility of the security team, which includes continuous monitoring, implementing runtime application self-protraction, and so on. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Devsecops Pipeline Production Post Deployment Stage. Use it as a tool for discussion and navigation on Engaging In Red Teaming Exercises, Managing Bug Bounty Programs, Conducting External Security Assessments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS
Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SSThis slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. Present the topic in a bit more detail with this Deploy Tools For Continuous Device Monitoring IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Vulnerability Scanning, Auditing Reporting, Anomaly Detection . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS
Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SSThis slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Increase audience engagement and knowledge by dispensing information using Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Digital Certificates, Certificates Contains, Protect Cryptographic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 30 60 90 Days Plan To Deploy CASB Model CASB Cloud Security
30 60 90 Days Plan To Deploy CASB Model CASB Cloud SecurityThis slide represents the 30-60-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Introducing 30 60 90 Days Plan To Deploy CASB Model CASB Cloud Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on 30 60 90 Days Plan, Cloud Access Security Broker, Connect To Current Security Architecture, Security Operations Center Functions, using this template. Grab it now to reap its full benefits.
-
 Advantages And Disadvantages Of Proxy Based Deployment CASB Cloud Security
Advantages And Disadvantages Of Proxy Based Deployment CASB Cloud SecurityThis slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. Increase audience engagement and knowledge by dispensing information using Advantages And Disadvantages Of Proxy Based Deployment CASB Cloud Security. This template helps you present information on two stages. You can also present information on Proxy Based Cloud Access Security, Advantages Cover Flexibility, Proxy Based Deployment, Encrypted Connections Or Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Api Based Use Cases Of CASB Deployment CASB Cloud Security
Api Based Use Cases Of CASB Deployment CASB Cloud SecurityThis slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on. Present the topic in a bit more detail with this Api Based Use Cases Of CASB Deployment CASB Cloud Security. Use it as a tool for discussion and navigation on Cloud Services, Data Transfer Policies, Auditing User Access Provisioning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Api Scanning CASB Deployment Model CASB Cloud Security
Api Scanning CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Deliver an outstanding presentation on the topic using this Api Scanning CASB Deployment Model CASB Cloud Security. Dispense information and present a thorough explanation of Deployment Works, Mobile And Corporate Devices, Submitting Queries Or Commands using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 CASB Deployment With Optional Components Pricing CASB Cloud Security
CASB Deployment With Optional Components Pricing CASB Cloud SecurityThis slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Present the topic in a bit more detail with this CASB Deployment With Optional Components Pricing CASB Cloud Security. Use it as a tool for discussion and navigation on Threat Protection Subscription, Optional Components Pricing, Annual Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 CASB Deployment With Standard Components Pricing CASB Cloud Security
CASB Deployment With Standard Components Pricing CASB Cloud SecurityThis slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Deliver an outstanding presentation on the topic using this CASB Deployment With Standard Components Pricing CASB Cloud Security. Dispense information and present a thorough explanation of Standard Components Pricing, Data Security With Salesforce, Deployment In An Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 CASB Forward Proxy Deployment Use Cases CASB Cloud Security
CASB Forward Proxy Deployment Use Cases CASB Cloud SecurityThis slide highlights the main use cases of forward proxy server CASB deployment. The main purpose of this slide is to showcase the primary use cases of the forward proxy, including implementing granular access and activity controls and detecting show IT in the network. Increase audience engagement and knowledge by dispensing information using CASB Forward Proxy Deployment Use Cases CASB Cloud Security. This template helps you present information on two stages. You can also present information on Deploying Granular Access, Proxy Deployment Use Cases, Potential Security Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 CASB Reverse Proxy Deployment Use Cases CASB Cloud Security
CASB Reverse Proxy Deployment Use Cases CASB Cloud SecurityThis slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. Deliver an outstanding presentation on the topic using this CASB Reverse Proxy Deployment Use Cases CASB Cloud Security. Dispense information and present a thorough explanation of Enforce Access Constraints, Controlling Download Data Access, Prevent Data Exfiltration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Forward Proxy Deployment Overview And Working CASB Cloud Security
Forward Proxy Deployment Overview And Working CASB Cloud SecurityThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Increase audience engagement and knowledge by dispensing information using Forward Proxy Deployment Overview And Working CASB Cloud Security. This template helps you present information on eight stages. You can also present information on Forward Proxy Deployment, Internet And Origin Server, According To The Internet Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of CASB Deployment Models CASB Cloud Security
Overview Of CASB Deployment Models CASB Cloud SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Overview Of CASB Deployment Models CASB Cloud Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Out Of Band Deployment, Inline Deployment, Terms Of Development And Operations, using this template. Grab it now to reap its full benefits.
-
 Primary Types Of Reverse Proxy Server Deployment CASB Cloud Security
Primary Types Of Reverse Proxy Server Deployment CASB Cloud SecurityThis slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Increase audience engagement and knowledge by dispensing information using Primary Types Of Reverse Proxy Server Deployment CASB Cloud Security. This template helps you present information on two stages. You can also present information on Regular Reverse Proxies, Load Balancers, Primary Types Of Reverse, Proxy Server Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pros And Cons Of Api Scanning CASB Deployment CASB Cloud Security
Pros And Cons Of Api Scanning CASB Deployment CASB Cloud SecurityThis slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Introducing Pros And Cons Of Api Scanning CASB Deployment CASB Cloud Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Scanning Cloud Access Security, Broker Deployment Model, Scanning Deployment Model, using this template. Grab it now to reap its full benefits.
-
 Proxy Based CASB Deployment Model CASB Cloud Security
Proxy Based CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Increase audience engagement and knowledge by dispensing information using Proxy Based CASB Deployment Model CASB Cloud Security. This template helps you present information on two stages. You can also present information on Forward Proxy Mode, Reverse Proxy Mode, Login Attempts, Access Efforts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proxy Based Vs Api Based Deployment Of CASB Cloud Security
Proxy Based Vs Api Based Deployment Of CASB Cloud SecurityThis slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Present the topic in a bit more detail with this Proxy Based Vs Api Based Deployment Of CASB Cloud Security. Use it as a tool for discussion and navigation on Proxy Based Deployment, Requires Implementation, Security Filtering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reverse Proxy CASB Deployment Model CASB Cloud Security
Reverse Proxy CASB Deployment Model CASB Cloud SecurityThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Reverse Proxy CASB Deployment Model CASB Cloud Security. This template helps you present information on five stages. You can also present information on Reverse Proxy Cloud, Access Security Model Broker, Proxies And Load Balancers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Deploy Cloud Access Security Broker CASB Cloud Security
Steps To Deploy Cloud Access Security Broker CASB Cloud SecurityThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Deliver an outstanding presentation on the topic using this Steps To Deploy Cloud Access Security Broker CASB Cloud Security. Dispense information and present a thorough explanation of Deployment Location, Deployment Model, Release Model, Cloud Access Security Broker using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




