Powerpoint Templates and Google slides for Security Data Protection
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CD
Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CDDitch the Dull templates and opt for our engaging Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CD deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 Implementing security management plan to reduce threats and protect sensitive company data complete deck
Implementing security management plan to reduce threats and protect sensitive company data complete deckThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Implementing Security Management Plan To Reduce Threats And Protect Sensitive Company Data Complete Deck and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Cloud Security Icon Security Computing Data Protection Digital Access
Cloud Security Icon Security Computing Data Protection Digital AccessKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Blockchain security data protection risk control incident management
Blockchain security data protection risk control incident managementEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Security Data Protection Risk Control Incident Management is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 US Cyber Security Solution Market Trend For Data Protection
US Cyber Security Solution Market Trend For Data ProtectionThis slide graphically represents market trend of US cyber security solutions for enhancing data protection and mitigating cyber attacks. It includes various growth drivers of solutions such as rising remote work culture, increasing cyber threats, etc. Introducing our US Cyber Security Solution Market Trend For Data Protection set of slides. The topics discussed in these slides are Key Insights, Market Size, Cybersecurity Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
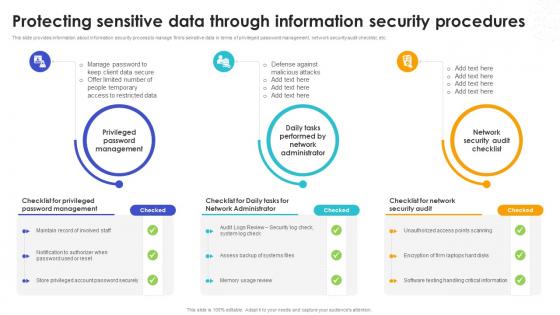 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
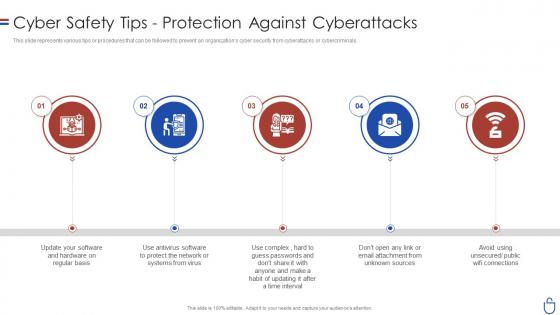 Data security it cyber safety tips protection against cyberattacks
Data security it cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Data Security IT Cyber Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Sources, Public Wifi Connections, Time Interval, Protect Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Protection Secure Backup Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Secure Backup Colored Icon In Powerpoint Pptx Png And Editable Eps FormatSecure Backup is a coloured powerpoint icon that ensures your data is backed up and stored securely. It offers a reliable and efficient way to protect your data and keep it safe from any potential loss or damage.
-
 Data Protection Secure Backup Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Secure Backup Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for presentations on secure backup. It features a shield with a check mark, representing the security and reliability of your backup system. Use this icon to illustrate the importance of secure data storage.
-
 Data Protection Web Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Web Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is the perfect visual representation of web security. It features a shield with a lock, a key, and a globe, symbolizing the protection of online data and resources.
-
 Data Protection Web Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Web Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for presentations on web security. It features a shield with a lock symbol, representing the protection of data from cyber threats. The icon is simple, yet powerful, and conveys the importance of web security.
-
 Data Breach Prevention Security Software To Protect Business From Data Breach
Data Breach Prevention Security Software To Protect Business From Data BreachThe purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Security Software To Protect Business From Data Breach. This template helps you present information on three stages. You can also present information on Security Information And Event Management, Amends Permissions As Needed, Security Software To Protect Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is a visual representation of a Cyber Security Action Plan for Data Protection. It illustrates the essential steps needed to ensure the safety of sensitive data and prevent cyber-attacks. Perfect for presentations, reports, and other documents.
-
 Cyber Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon depicts a comprehensive action plan for data protection and cyber security. It is a great visual aid to help organizations understand the steps needed to protect their data and ensure cyber security.
-
 Network Security Challenges And Solution For Protecting Data
Network Security Challenges And Solution For Protecting DataThis slide showcase solution and challenges for network security. The main purpose for this template is to save company data from getting into hands of rival businesses. This includes data theft, insider threat, password attack, etc. Presenting our set of slides with Network Security Challenges And Solution For Protecting Data. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Challenges, Solution.
-
 Network Security Highlighting Important Steps For Protecting Data
Network Security Highlighting Important Steps For Protecting DataThis slide showcase steps of network security. The main reason for this slide is showcasing management of network without any uninterrupted operations. This includes internal networks, protection security, cyber security, etc. Presenting our well structured Network Security Highlighting Important Steps For Protecting Data. The topics discussed in this slide are Internal Network, Protected Payment.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Security Icon For Protecting Data From Theft
Network Security Icon For Protecting Data From TheftIntroducing our Network Security Icon For Protecting Data From Theft set of slides. The topics discussed in these slides are Network Security Protecting Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Tips For Protecting Important Data
Network Security Tips For Protecting Important DataThese slide showcase ways of protecting network security. The main purpose of this template is how to keep office data safe from any kind of theft, this includes careful grant access, strong password, secure servers, text security. Presenting our set of slides with Network Security Tips For Protecting Important Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Careful Grant Access, Strong Password.
-
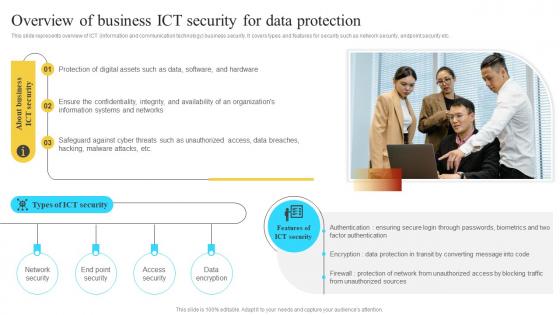 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Secured Data Protection For Online Security System Icon
Secured Data Protection For Online Security System IconPresenting our set of slides with Secured Data Protection For Online Security System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secured Data Protection, Online Security System Icon.
-
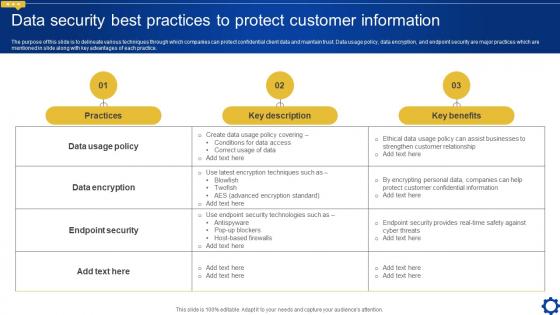 Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V
Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Present the topic in a bit more detail with this Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V. Use it as a tool for discussion and navigation on Practices, Key Description, Key Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
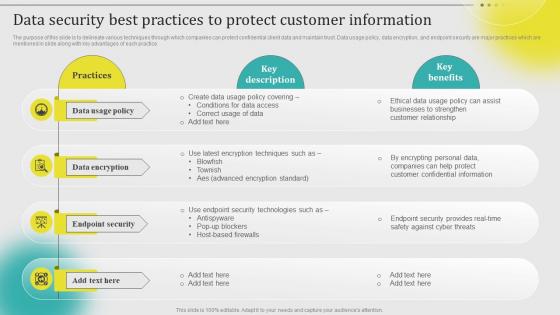 Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V
Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Data Security Best Practices To Protect Complete Introduction To Database MKT SS V
Data Security Best Practices To Protect Complete Introduction To Database MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Complete Introduction To Database MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V
Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Information Security Management Framework For Organization Data Protection
Information Security Management Framework For Organization Data ProtectionThis slide represents framework that assists organizations in developing information security management to enhance data protection. This model sets information security at tactical level, strategic level, and operational level. Introducing our Information Security Management Framework For Organization Data Protection set of slides. The topics discussed in these slides are Information Security Plan, Consciousness Management, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Management Icon For Data Protection
Information Security Management Icon For Data ProtectionPresenting our set of slides with Information Security Management Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Management Icon, Data Protection.
-
 Managing Information Security Threats To Enhance Data Protection
Managing Information Security Threats To Enhance Data ProtectionThis slide represents strategies that help businesses mitigate threats of information security management and reduce data loss incidents. It includes various threats such as social media attacks, social engineering, lack of encryption, etc. Presenting our well structured Managing Information Security Threats To Enhance Data Protection. The topics discussed in this slide are Social Media Attacks, Social Engineering, Malware On Endpoints. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS
Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Increase audience engagement and knowledge by dispensing information using Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS This template helps you present information on six stages. You can also present information on Customer Data Protection, Online Transactions, Management Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS
Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Present the topic in a bit more detail with this Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS. Use it as a tool for discussion and navigation on Online Transactions, Customer Data Protection, POS Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V
Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V
Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V
Data Security Best Practices To Protect Using Customer Data To Improve MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Using Customer Data To Improve MKT SS V. Dispense information and present a thorough explanation of Policy, Data, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Wireless Internet Security For Data Protection
Types Of Wireless Internet Security For Data ProtectionThe following slide highlights key points such as WEP, WPA, WPA2, and WPA3 protocols to show types of wireless internet security for privacy protection. It helps in understanding and comparing different safety procedures for effective data protection. Introducing our premium set of slides with Types Of Wireless Internet Security For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Wireless Internet. So download instantly and tailor it with your information.
-
 Csirt Cyber Security Icon For Protecting Data
Csirt Cyber Security Icon For Protecting DataIntroducing our premium set of slides with Csirt Cyber Security Icon For Protecting Data. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Csirt Cyber Security, Protecting Data. So download instantly and tailor it with your information.
-
 Data Protection Server Security Technology Icon
Data Protection Server Security Technology IconPresenting our set of slides with Data Protection Server Security Technology Icon. This exhibits information on threestages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Server Security Technology.
-
 Enhance Server Security Through Data Protection Storage Icon
Enhance Server Security Through Data Protection Storage IconPresenting our set of slides with Enhance Server Security Through Data Protection Storage Icon. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Server Security, Data Protection Storage.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Saas Cyber Security Icon To Protect Sensitive Data
Saas Cyber Security Icon To Protect Sensitive DataIntroducing our Saas Cyber Security, Icon To Protect Sensitive Data set of slides. The topics discussed in these slides are Saas Cyber Security, Icon To Protect Sensitive Data This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Security Management Icon To Protect Organizational Information
Data Security Management Icon To Protect Organizational InformationIntroducing our premium set of slides with Data Security Management Icon To Protect Organizational Information. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security Management, Icon, Protect Organizational Information. So download instantly and tailor it with your information.
-
 Security Management Framework For Enhancing Data Protection
Security Management Framework For Enhancing Data ProtectionThis slide presents the framework that helps businesses to manage data security against modern attack vectors and network vulnerabilities. It includes various elements such as govern, discover, insights, protect and monitor. Presenting our well structured Security Management Framework For Enhancing Data Protection. The topics discussed in this slide are Privacy Readiness, Risk And Security Analytics, Data Driven Outcomes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Measures To Protect Business Data
Cyber Security Measures To Protect Business DataThe highlighted slide underscores essential measures, including robust passwords, regular software updates, antivirus protection, multi factor authentication, and access control. These steps collectively enhance cybersecurity, fortifying defenses to safeguard critical business data against potential threats. Presenting our set of slides with Cyber Security Measures To Protect Business Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strong And Complex Passwords, Software Updates, Enhance Security.
-
 Authentication In Application Security For Data Protection
Authentication In Application Security For Data ProtectionThis slide discusses about the overview of authentication in application security and the various elements of MFA. Increase audience engagement and knowledge by dispensing information using Authentication In Application Security For Data Protection. This template helps you present information on five stages. You can also present information on Knowledge Factor, Possession Factor, Biometric Factor, Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Audit Procedure Icon To Verify Company Data Protection
Security Audit Procedure Icon To Verify Company Data ProtectionPresenting our set of slides with Security Audit Procedure Icon To Verify Company Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Audit Procedure, Verify Company, Data Protection.
-
 SaaS Security Icon For Protecting Confidential Data
SaaS Security Icon For Protecting Confidential DataPresenting our set of slides with SaaS Security Icon For Protecting Confidential Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SaaS Security, Protecting Confidential Data.
-
 Different Types Of Visualization Security For Protecting Data
Different Types Of Visualization Security For Protecting DataThis slides showcases various types of visualization data. The main purpose of this template is to showcase data encryption for shared data. This includes role based access control, encrypted file sharing, regular security audits, etc. Introducing our premium set of slides with Different Types Of Visualization Security For Protecting Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Methods, Regular Security Audits, Encrypted File Sharing. So download instantly and tailor it with your information.
-
 Visualization Security Icon For Data Protection
Visualization Security Icon For Data ProtectionPresenting our set of slides with Visualization Security Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualization Security, Data Protection.
-
 Major Components Of IP Security To Protect Sensitive Data
Major Components Of IP Security To Protect Sensitive DataThis slide showcases key elements of IP security for protecting data. The main purpose of this template is to showcase protection and trustworthiness of data. This includes encapsulating security payload, authentication header, and internet key exchange. Presenting our set of slides with name Major Components Of IP Security To Protect Sensitive Data. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Internet Key Exchange, Authentication Header, Encapsulating Security Payload.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 NIDS Cyber Security Icon For Sensitive Data Protection
NIDS Cyber Security Icon For Sensitive Data ProtectionIntroducing our premium set of slides with NIDS Cyber Security Icon For Sensitive Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Sensitive, Cyber Security. So download instantly and tailor it with your information.
-
 Pam Framework For Optimizing Cyber Security And Data Protection
Pam Framework For Optimizing Cyber Security And Data ProtectionThis slide represents framework that assists companies to implement PAM cybersecurity to enhance their data protection and risk management. It includes various components such as use cases, defining requirements, architecture development, etc. Presenting our well structured Pam Framework For Optimizing Cyber Security And Data Protection. The topics discussed in this slide are Determine Use Cases, Define Requirements, Develop Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security In Banking Icon To Protect Customer Data
Cyber Security In Banking Icon To Protect Customer DataIntroducing our premium set of slides with Cyber Security In Banking Icon To Protect Customer Data. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security In Banking, Icon To Protect, Customer Data. So download instantly and tailor it with your information.
-
 Email Security Best Practices Email Data Protection Overview And Features
Email Security Best Practices Email Data Protection Overview And FeaturesThe purpose of this slide is to discuss the Email Data Protection EDP solutions of email security. This slide highlights the features of Email Data Protection EDP , such as content-based email control, recipient authentication, data anonymization, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Data Protection Overview And Features. Use it as a tool for discussion and navigation on Content-Based Email Control, Recipient Authentication, Two-Factor Authentication, Data Anonymization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Mechanism To Protect Data Gathered From IOT Devices
Cloud Security Mechanism To Protect Data Gathered From IOT DevicesThis slide showcases AWS IoT security diagram for secure data transfer. It includes user, IoT devices, Cognito ID, lambda, DynamicDB and kinesis. Presenting our well structured Cloud Security Mechanism To Protect Data Gathered From IOT Devices. The topics discussed in this slide are Security Credentials, Identity And Access, Management Policies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IOT Security System Tools For Data Protection
IOT Security System Tools For Data ProtectionThis slide showcases methods to secure IoT security systems. It includes digital certificates, network and application programming interface security. Presenting our set of slides with name IOT Security System Tools For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, API Security, Digital Certificates.




