Powerpoint Templates and Google slides for Security Criteria
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 ERP Product Security Management Criteria Checklist
ERP Product Security Management Criteria ChecklistThis slide showcases the ERP management criteria checklist. Its aim is to check for the selection criteria features. This slide includes quality, investment, business process reengineering, etc. Presenting our well structured ERP Product Security Management Criteria Checklist. The topics discussed in this slide are Drivers, Criteria, Checklist. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Packet Filtering Firewalls Working And Packet Approval Criteria
Firewall Network Security Packet Filtering Firewalls Working And Packet Approval CriteriaThis slide outlines the working process of packet-filtering firewall type and packet approval criteria. The purpose of this slide is to showcase how packet-filtering firewall works and what parameters it uses to approve or deny a packet to secure the network. Deliver an outstanding presentation on the topic using this Firewall Network Security Packet Filtering Firewalls Working And Packet Approval Criteria Dispense information and present a thorough explanation of Provider, Services, Features And Suitable using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Criteria To Compare Firewall Management Systems
Firewall Network Security Criteria To Compare Firewall Management SystemsThis slide describes some key features to look for in a firewall management system. The purpose of this slide is to showcase some of the criteria to compare a firewall management system, including ease of use, efficiency, built-in integrations, and scalability. Introducing Firewall Network Security Criteria To Compare Firewall Management Systems to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Ease Of Use, Efficiency, Scalability using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Success Criteria For Devsecops Model Process
Devsecops Best Practices For Secure Success Criteria For Devsecops Model ProcessThis slide highlights the success criteria followed for the DevSecOps process. The purpose of this slide is to discuss the various standards, including open collaboration to shared objectives, security at source, reinforcement and elevations through automation, and so on. Introducing Devsecops Best Practices For Secure Success Criteria For Devsecops Model Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Proactive Monitoring And Recursive, Reinforce And Elevate Through Automation, Security At Source, using this template. Grab it now to reap its full benefits.
-
 Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria
Risk Management Framework For Information Security Defining Vulnerability Rating With CriteriaFollowing slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Defining Vulnerability Rating With Criteria. Use it as a tool for discussion and navigation on Vulnerability Ranking, Organization, High, Low, Medium. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Staff Recruiting Criteria And Training Centre Manpower Security Services Company Profile
Staff Recruiting Criteria And Training Centre Manpower Security Services Company ProfileThis slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Present the topic in a bit more detail with this Staff Recruiting Criteria And Training Centre Manpower Security Services Company Profile. Use it as a tool for discussion and navigation on Recruiting, Authorized, Training Centre. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Staff Recruiting Criteria And Training Centre Security Guard Service Company Profile
Staff Recruiting Criteria And Training Centre Security Guard Service Company ProfileThis slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Introducing Staff Recruiting Criteria And Training Centre Security Guard Service Company Profile to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Selection Criteria, Authorized Training Centre, Medical Category, using this template. Grab it now to reap its full benefits.
-
 Staff Recruiting Criteria And Training Centre Security Services Business Profile Ppt Template
Staff Recruiting Criteria And Training Centre Security Services Business Profile Ppt TemplateThis slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Introducing Staff Recruiting Criteria And Training Centre Security Services Business Profile Ppt Template to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Selection Criteria, Authorized Training Centre, using this template. Grab it now to reap its full benefits.
-
 Staff Recruiting Criteria And Training Centre Security And Manpower Services Company Profile
Staff Recruiting Criteria And Training Centre Security And Manpower Services Company ProfileThis slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Increase audience engagement and knowledge by dispensing information using Staff Recruiting Criteria And Training Centre Security And Manpower Services Company Profile. This template helps you present information on two stages. You can also present information on Selection Criteria, Authorized Training Centre using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Security Criteria And Control Measures For IT System Vulnerabilities
Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations
Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security OperationsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Intervention, Malware Analysis, Automate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities
Risk Assessment Of It Systems Security Criteria And Control Measures For It System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Deliver an outstanding presentation on the topic using this Risk Assessment Of It Systems Security Criteria And Control Measures For It System Vulnerabilities. Dispense information and present a thorough explanation of Management Security, Operational Security, Technical Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
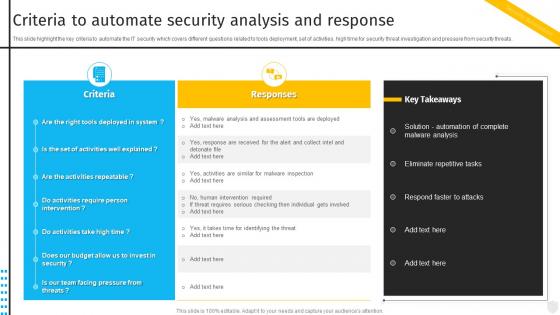 Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate Cyberthreats
Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate CyberthreatsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Analysis, Deployment, Investigation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
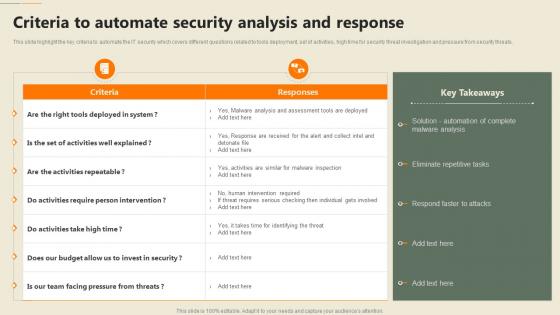 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criteria To Automate Security Analysis And Response Security Orchestration Automation
Criteria To Automate Security Analysis And Response Security Orchestration AutomationThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Increase audience engagement and knowledge by dispensing information using Criteria To Automate Security Analysis And Response Security Orchestration Automation. This template helps you present information on one stages. You can also present information on Malware Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Acceptance Criteria Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Network Security Acceptance Criteria Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a perfect visual representation of acceptance criteria. It is a bright and vibrant icon that can be used to help explain the concept of acceptance criteria in a presentation or document. The icon is available in multiple sizes and can be used for both personal and professional projects.
-
 Network Security Acceptance Criteria Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Network Security Acceptance Criteria Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a perfect visual representation of Acceptance Criteria. It is a simple yet effective way to convey the idea of quality assurance and meeting expectations in a professional setting. It is ideal for presentations, documents, and other visuals.
-
 Software selection criteria software costs installation security ppt powerpoint presentation ideas show
Software selection criteria software costs installation security ppt powerpoint presentation ideas showPresenting this set of slides with name Software Selection Criteria Software Costs Installation Security Ppt Powerpoint Presentation Ideas Show. This is a six process. The stages in this process are Process, Management, Marketing, Business, Strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Software selection criteria maintenance security ppt powerpoint presentation ideas gallery
Software selection criteria maintenance security ppt powerpoint presentation ideas galleryPresenting this set of slides with name Software Selection Criteria Maintenance Security Ppt Powerpoint Presentation Ideas Gallery. This is a six stage process. The stages in this process are Contract, Maintenance, Installation, Software Costs, Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Five criteria visual for mobile security infographic template
Five criteria visual for mobile security infographic templateThis is our Five Criteria Visual For Mobile Security Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully editable visual content.
-
 Smart criteria software security ppt powerpoint presentation show rules cpb
Smart criteria software security ppt powerpoint presentation show rules cpbPresenting Smart Criteria Software Security Ppt Powerpoint Presentation Show Rules Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Smart Criteria Software Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.



