Powerpoint Templates and Google slides for Security Brokers
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security BrokerThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Training Program For Cloud Access Security Broker. Use it as a tool for discussion and navigation on Training Program For Cloud, Access Security Broker, System Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment
Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server DeploymentThis slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Types Of Forward Proxy Server Deployment. Dispense information and present a thorough explanation of Proxy Server Deployment, Central Proxy Server, Proxy Server Implementation, Data Center Proxies Work using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security BrokerPresent the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Use Cases Of Cloud Access Security Broker. Use it as a tool for discussion and navigation on Threats And Exploited Accounts, Unmanaged Devices, Label And Protect Sensitive, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Why CASB Is Important For Businesses
Cloud Access Security Broker CASB V2 Why CASB Is Important For BusinessesThis slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the Cloud Access Security Broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. Introducing Cloud Access Security Broker CASB V2 Why CASB Is Important For Businesses to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Cloud Adoption, Better Security, Compliance, Centralized Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example Introduction
Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example IntroductionIntroducing our well researched set of slides titled Icons Slide For Cloud Access Security Broker CASB V2 Ppt Ideas Example Introduction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Overview Cloud Security Model
Cloud Access Security Broker CASB Overview Cloud Security ModelThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing Cloud Access Security Broker CASB Overview Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility, Prevention, Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Implementation Models Cloud Security Model
Cloud Access Security Broker Implementation Models Cloud Security ModelThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Scanning, Forward, Reverse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Use Cases Cloud Security Model
Cloud Access Security Broker Use Cases Cloud Security ModelThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Cloud Security Model. Dispense information and present a thorough explanation of Protection, Govern, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Access Security Broker Cloud Security Model
Pillars Of Cloud Access Security Broker Cloud Security ModelThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Pillars Of Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Visibility, Security, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Cloud Access Security Broker Cloud Security Model
Timeline To Implement Cloud Access Security Broker Cloud Security ModelThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Identify, Removal, using this template. Grab it now to reap its full benefits.
-
 Sase Security Best Practices To Implement Cloud Access Security Broker
Sase Security Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Sase Security Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Implementing, Solutions, Consumption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Cloud Access Security Broker Working Process
Sase Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, an remediation. Deliver an outstanding presentation on the topic using this Sase Security Cloud Access Security Broker Working Process. Dispense information and present a thorough explanation of Remediation, Classification, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Cloud Broker Casb Overview Ppt Show Graphics Pictures
Sase Security Cloud Broker Casb Overview Ppt Show Graphics PicturesThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Present the topic in a bit more detail with this Sase Security Cloud Broker Casb Overview Ppt Show Graphics Pictures. Use it as a tool for discussion and navigation on Threat Prevention, Risk Visibility, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Cloud Broker Use Cases Ppt Show Graphics Template
Sase Security Cloud Broker Use Cases Ppt Show Graphics TemplateThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Sase Security Cloud Broker Use Cases Ppt Show Graphics Template. Dispense information and present a thorough explanation of Identifications, Ransomware, Transparency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials
Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics TutorialsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Present the topic in a bit more detail with this Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials. Use it as a tool for discussion and navigation on Implementation, Technique, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Pillars Of Cloud Access Security Broker
Sase Security Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Present the topic in a bit more detail with this Sase Security Pillars Of Cloud Access Security Broker. Use it as a tool for discussion and navigation on Compliance, Threat Protection, Data Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Timeline To Implement Cloud Access Security Broker
Sase Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Security Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Timeline, Applications, Environments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase
Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge SaseThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Consumption, Implementing, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Broker Use Cases Secure Access Service Edge Sase
Cloud Access Broker Use Cases Secure Access Service Edge SaseThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Cloud Access Broker Use Cases Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Transparency, Intelligence, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Secure Access Service Edge Sase
Cloud Access Security Broker Working Process Secure Access Service Edge SaseThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Information, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Broker Casb Overview Secure Access Service Edge Sase
Cloud Broker Casb Overview Secure Access Service Edge SaseThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing Cloud Broker Casb Overview Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Assessment, Threat Prevention, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Broker Implementation Models Secure Access Service Edge Sase
Cloud Security Broker Implementation Models Secure Access Service Edge SaseThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Security Broker Implementation Models Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Implementation, Applications, Inline Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Access Security Broker Secure Access Service Edge Sase
Pillars Of Cloud Access Security Broker Secure Access Service Edge SaseThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Pillars Of Cloud Access Security Broker Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Threat Protection, Data Security , using this template. Grab it now to reap its full benefits.
-
 Timeline To Cloud Access Security Broker Secure Access Service Edge Sase
Timeline To Cloud Access Security Broker Secure Access Service Edge SaseThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Cloud Access Security Broker Secure Access Service Edge Sase. This template helps you present information on seven stages. You can also present information on Timeline, Implement, Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Overview SASE Network Security
Cloud Access Security Broker CASB Overview SASE Network SecurityThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB Overview SASE Network Security. This template helps you present information on five stages. You can also present information on Visibility, Prevention, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Implementation Models SASE Network Security
Cloud Access Security Broker Implementation Models SASE Network SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Cloud Access Security Broker Implementation Models SASE Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward, Reverse, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Use Cases SASE Network Security
Cloud Access Security Broker Use Cases SASE Network SecurityThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases SASE Network Security. Dispense information and present a thorough explanation of Protection, Secure, Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Pillars Of Cloud Access Security Broker
SASE Network Security Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SASE Network Security Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Security, Prevention, Visibility using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB
Benefits Of Cloud Access Security Broker 2 0 Next Generation CASBThis slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Introducing Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Coverage, Cost Effective, Improved Visibility using this template. Grab it now to reap its full benefits.
-
 Benefits Of Cloud Access Security Broker Next Generation CASB
Benefits Of Cloud Access Security Broker Next Generation CASBThis slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Present the topic in a bit more detail with this Benefits Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Risk Visibility, Threat Prevention, Assessment And Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Next Generation CASB
Best Practices To Implement Cloud Access Security Broker Next Generation CASBThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB, Best Practices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Adopt A Cloud Access Security Broker Next Generation CASB
Checklist To Adopt A Cloud Access Security Broker Next Generation CASBThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Deliver an outstanding presentation on the topic using this Checklist To Adopt A Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Vendor Landscape, Conduct A Trial, Functionalities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And Encryption Next Generation CASB
Cloud Access Security Broker And Encryption Next Generation CASBThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Present the topic in a bit more detail with this Cloud Access Security Broker And Encryption Next Generation CASB Use it as a tool for discussion and navigation on Security That Tracks Data, Terminated Moment, Content Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker And Secure Web Gateway Next Generation CASB
Cloud Access Security Broker And Secure Web Gateway Next Generation CASBThis slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker And Secure Web Gateway Next Generation CASB Dispense information and present a thorough explanation of Cloud App Data, Get Dynamic Control, Simplify Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And User Authentication Next Generation CASB
Cloud Access Security Broker And User Authentication Next Generation CASBThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication Next Generation CASB Use it as a tool for discussion and navigation on Cloud Apps, Transaction Detail, User Threat Data This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Introduction Next Generation CASB
Cloud Access Security Broker CASB Introduction Next Generation CASBThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Present the topic in a bit more detail with this Cloud Access Security Broker CASB Introduction Next Generation CASB Use it as a tool for discussion and navigation on Deployment Models, Out Of Band Deployment, Inline Deployment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Implementation Roadmap Next Generation CASB
Cloud Access Security Broker Implementation Roadmap Next Generation CASBThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Implementation Roadmap Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Portfolio, Cloud Application, Systems using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Life Cycle Protection Next Generation CASB
Cloud Access Security Broker Life Cycle Protection Next Generation CASBIncrease audience engagement and knowledge by dispensing information using Cloud Access Security Broker Life Cycle Protection Next Generation CASB This template helps you present information on four stages. You can also present information on Identify Needs, Control Usage, Adaptive Access, Verify Usage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Compliance Next Generation CASB
Cloud Access Security Broker Pillar Compliance Next Generation CASBThis slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Introducing Cloud Access Security Broker Pillar Compliance Next Generation CASB to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Financial Services, Risk Domains, Costly Breaches using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Data Security Next Generation CASB
Cloud Access Security Broker Pillar Data Security Next Generation CASBThis slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Data Security Next Generation CASB This template helps you present information on five stages. You can also present information on Complex Cloud, Sensitive Material, Risk Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Overview Next Generation CASB
Cloud Access Security Broker Pillar Overview Next Generation CASBThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Introducing Cloud Access Security Broker Pillar Overview Next Generation CASB to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Data Security, Threat Protection, Visibility using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Pillar Threat Protection Next Generation CASB
Cloud Access Security Broker Pillar Threat Protection Next Generation CASBThis slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Pillar Threat Protection Next Generation CASB This template helps you present information on five stages. You can also present information on Services, Cloud Storage, Compromised Accounts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Pillar Visibility Next Generation CASB
Cloud Access Security Broker Pillar Visibility Next Generation CASBThis slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Present the topic in a bit more detail with this Cloud Access Security Broker Pillar Visibility Next Generation CASB Use it as a tool for discussion and navigation on Visibility Topography, Working Process, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB
Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASBThis slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Introducing Future Of Cloud Access Security Broker CASB 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Encryption, Benefits using this template. Grab it now to reap its full benefits.
-
 Leading Cloud Access Security Broker Platforms Next Generation CASB
Leading Cloud Access Security Broker Platforms Next Generation CASBThis slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Introducing Leading Cloud Access Security Broker Platforms Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Amazon Web Services, Cloud Access, Broker Platforms using this template. Grab it now to reap its full benefits.
-
 Overview Of Cloud Access Security Broker Architecture Next Generation CASB
Overview Of Cloud Access Security Broker Architecture Next Generation CASBThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Present the topic in a bit more detail with this Overview Of Cloud Access Security Broker Architecture Next Generation CASB Use it as a tool for discussion and navigation on Organization, Direct To Cloud, Broker Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Popular Cloud Access Security Broker Vendors Next Generation CASB
Popular Cloud Access Security Broker Vendors Next Generation CASBThis slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Deliver an outstanding presentation on the topic using this Popular Cloud Access Security Broker Vendors Next Generation CASB Dispense information and present a thorough explanation of Forcepoint, Cisco Systems, Microsoft, Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Deploy Cloud Access Security Broker Next Generation CASB
Steps To Deploy Cloud Access Security Broker Next Generation CASBThis slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Introducing Steps To Deploy Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Deployment Location, Deployment Model, Release Model using this template. Grab it now to reap its full benefits.
-
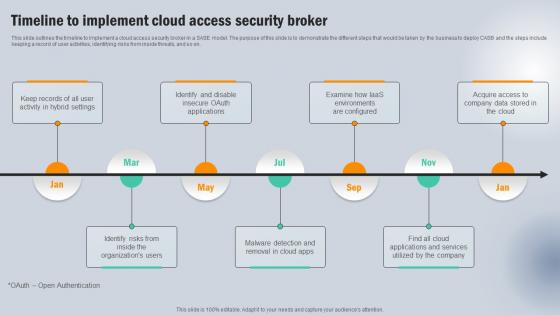 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
 Training Program For Cloud Access Security Broker Next Generation CASB
Training Program For Cloud Access Security Broker Next Generation CASBThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Training Program For Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Agenda, System Requirements, Deployment Options This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Cases Of Cloud Access Security Broker Next Generation CASB
Use Cases Of Cloud Access Security Broker Next Generation CASBPresent the topic in a bit more detail with this Use Cases Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Unsanctioned Apps, Sanctioned Apps, Cloud Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





