Powerpoint Templates and Google slides for Security Authentication
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Authentication As A Type Of Application Security Training Ppt
Authentication As A Type Of Application Security Training PptPresenting Authentication as a Type of Application Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Seven petal secure authentication cloud communications process workflow
Seven petal secure authentication cloud communications process workflowIntroduce your topic and host expert discussion sessions with this Seven Petal Secure Authentication Cloud Communications Process Workflow. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the seventeen slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
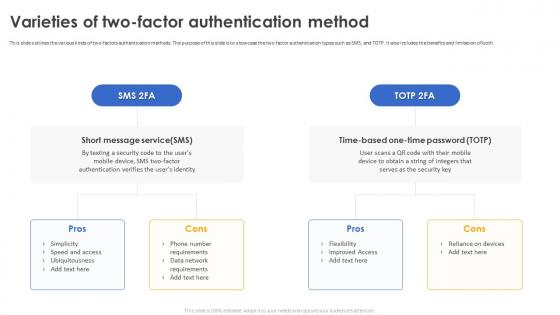 Secure Your Digital Assets Varieties Of Two Factor Authentication Method
Secure Your Digital Assets Varieties Of Two Factor Authentication MethodThis slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Varieties Of Two Factor Authentication Method. This template helps you present information on two stages. You can also present information on Phone Number Requirements, Data Network Requirements, Time Based One Time Password using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures
Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security MeasuresThe slide outlines major multifactor authentication methods to safeguard ecommerce stores. It include details about knowledge factors, possession factor along with potential impact. Present the topic in a bit more detail with this Key Multifactor Authentication Methods To Prevent Fraud Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Information Inherent, Potential Impact, Reduced Suspicious Logins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Security Authentication Encryption Illustration
Password Security Authentication Encryption IllustrationThis coloured powerpoint icon is a visual representation of password security. It features a padlock with a keyhole, a shield, and a key. It is perfect for illustrating the importance of secure passwords in presentations.
-
 Login Authentication Security Illustration
Login Authentication Security IllustrationThis Login icon is a bright and colourful PowerPoint graphic, perfect for adding a modern and professional touch to your presentation. It features a blue and green colour scheme, with a white arrow pointing to the right. Use this icon to signify login, sign in, or access.
-
 Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS
Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SSThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS. Use it as a tool for discussion and navigation on Possession Verification, Biometric Verification, Enter Username And Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User Authentication
Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User AuthenticationThis slide represents the improved user authentication method in Cloud Access Security Broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Cloud Access Security Broker And User Authentication. Dispense information and present a thorough explanation of Authentication Solutions, Creating Adaptive Authentication, Businesses To Dynamically using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V
Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Authentication Failed In Powerpoint And Google Slides Cpb
Secure Authentication Failed In Powerpoint And Google Slides CpbPresenting Secure Authentication Failed In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Authentication Failed. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V
Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Increase audience engagement and knowledge by dispensing information using Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V
NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V. Dispense information and present a thorough explanation of Authentication Process Flow, Enhanced Security, Verify Biometrics, Authentication Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Authentication Information Security In Powerpoint And Google Slides Cpb
Authentication Information Security In Powerpoint And Google Slides CpbPresenting Authentication Information Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Authentication Information Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Authentication Network Security In Powerpoint And Google Slides Cpb
Authentication Network Security In Powerpoint And Google Slides CpbPresenting our Authentication Network Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Authentication Network Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secure Your Digital Assets Overview And Working Of Two Factor Authentication
Secure Your Digital Assets Overview And Working Of Two Factor AuthenticationThis slide represents an overview and working of 2-factor authentication 2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security, it is user-friendly, etc. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Overview And Working Of Two Factor Authentication. Dispense information and present a thorough explanation of Phishing, Social Engineering, Password Brute Force Attacks, Prevents Attackers, Stolen Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And User Authentication Next Generation CASB
Cloud Access Security Broker And User Authentication Next Generation CASBThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication Next Generation CASB Use it as a tool for discussion and navigation on Cloud Apps, Transaction Detail, User Threat Data This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Authentication Techniques For Wireless Lan Security
Implement Authentication Techniques For Wireless Lan SecurityThis slide highlights wireless security LAN checklist for preventing security threats and compile standard authentication and encryption techniques. It includes elements such as wireless lan security recommendations, applicable, not applicable and notes. Introducing our Implement Authentication Techniques For Wireless Lan Security set of slides. The topics discussed in these slides are Authentication, Techniques, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ensure Secure Access Icon Using Multi Factor Authentication Tool
Ensure Secure Access Icon Using Multi Factor Authentication ToolPresenting our set of slides with Ensure Secure Access Icon Using Multi Factor Authentication Tool. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure, Factor, Authentication.
-
 Provide Adaptive Security Icon Based On Multi Factor Authentication
Provide Adaptive Security Icon Based On Multi Factor AuthenticationPresenting our set of slides with Provide Adaptive Security Icon Based On Multi Factor Authentication. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adaptive, Factor, Security.
-
 Reinforce Multi Factor Authentication Security For Unauthorized Use
Reinforce Multi Factor Authentication Security For Unauthorized UseThis slide showcases multi factor authentication practices for mitigating common security risks associated with relying solely on passwords. It includes aspects such as detailed multi factor authentication plan, configurable authentication factors, forgotten password plans, etc. Introducing our premium set of slides with Reinforce Multi Factor Authentication Security For Unauthorized Use. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Configurable, Compatibility. So download instantly and tailor it with your information.
-
 Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Introducing Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key, using this template. Grab it now to reap its full benefits.
-
 Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS
Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SSThis slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Increase audience engagement and knowledge by dispensing information using Methods For Deploying Strong Device Authentication IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Digital Certificates, Certificates Contains, Protect Cryptographic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Authentication For Web Page Security Icon
Authentication For Web Page Security IconPresenting our set of slides with name Authentication For Web Page Security Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication For Web Page, Security Icon.
-
 Password Authentication Process For Web Security
Password Authentication Process For Web SecurityThis slide highlights the working process of authentication for web security approaches which includes password verification. Introducing our Password Authentication Process For Web Security set of slides. The topics discussed in these slides are Create Mobile Agent, Password Authentication Process, Web Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Access Security Broker And User Authentication CASB Cloud Security
Cloud Access Security Broker And User Authentication CASB Cloud SecurityThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication CASB Cloud Security. Use it as a tool for discussion and navigation on Cloud Access Security Broker, User Authentication, Multifactor Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Security Icon For Implementing Authentication Measures
Mobile Security Icon For Implementing Authentication MeasuresPresenting our set of slides with name Mobile Security Icon For Implementing Authentication Measures. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mobile Security Icon For Implementing, Authentication Measures.
-
 Mobile Security Two Factor Authentication Process
Mobile Security Two Factor Authentication ProcessThis slide showcases roadmap for 2FA mobile security and includes assessment, select solutions, planning and integration, implementation, etc. Presenting our set of slides with name Mobile Security Two Factor Authentication Process. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment, Select Solution, Implementation, Testing And Optimization.
-
 Biometric Authentication For Mobile Security Icon
Biometric Authentication For Mobile Security IconIntroducing our premium set of slides with name Biometric Authentication For Mobile Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Biometric Authentication, Mobile Security Icon. So download instantly and tailor it with your information.
-
 Two Factor Authentication For Mobile Security Icon
Two Factor Authentication For Mobile Security IconIntroducing our premium set of slides with name Two Factor Authentication For Mobile Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Two Factor Authentication, Mobile Security Icon. So download instantly and tailor it with your information.
-
 Authentication In Application Security For Data Protection
Authentication In Application Security For Data ProtectionThis slide discusses about the overview of authentication in application security and the various elements of MFA. Increase audience engagement and knowledge by dispensing information using Authentication In Application Security For Data Protection. This template helps you present information on five stages. You can also present information on Knowledge Factor, Possession Factor, Biometric Factor, Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Difference Between Authentication And Authorization In Application Security
Difference Between Authentication And Authorization In Application SecurityThis slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. Deliver an outstanding presentation on the topic using this Difference Between Authentication And Authorization In Application Security. Dispense information and present a thorough explanation of Confirms Credentials, Authentication, Authorization, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Icon For Multifactor Authentication In Information Security
Icon For Multifactor Authentication In Information SecurityPresenting our set of slides with Icon For Multifactor Authentication In Information Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon For Multifactor, Authentication In Information Security
-
 Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS
Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of authentication and access control for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about trust boundaries, identity authentication, etc. Increase audience engagement and knowledge by dispensing information using Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Trust Boundaries, Identity Authentication, Access Protection Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Email Authentication And Security Working Process
Email Authentication And Security Working ProcessThis slide highlights the email authentication and security working process which includes sender establishes authentication rules, and sender configuration. Presenting our set of slides with Email Authentication And Security Working Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Infrastructure, Authentication Rules, Authentication Results.
-
 Email Security Encryption And Authentication Icon
Email Security Encryption And Authentication IconIntroducing our premium set of slides with Email Security Encryption And Authentication Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Email Security, Encryption And Authentication, Icon. So download instantly and tailor it with your information.
-
 Application Security Implementation Plan Process Phases For Effective Authentication Implementation
Application Security Implementation Plan Process Phases For Effective Authentication ImplementationThis slide showcases the steps for deploying effective authentication which include defining requirements, selecting authentication method, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Process Phases For Effective Authentication Implementation. This template helps you present information on seven stages. You can also present information on Implement Login Mechanism, Choose Authentication Method, Secure Storage Of Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Encryption And Authentication In Automotive Cyber Security
Data Encryption And Authentication In Automotive Cyber SecurityThis slide highlights data privacy and encryption in automotive cybersecurity. The purpose of this slide is to aid organizations in implementing measures for securing sensitive data from possible manipulation. It includes various measures for authentication and data encryption. Presenting our set of slides with Data Encryption And Authentication In Automotive Cyber Security This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication, Data Encryption, Authenticity Of Software
-
 Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SS
Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SSThis slide presents various use case of voice recognition technology for security and authentication in various areas. It includes mobile applications, call centers and IVR systems,and web applications. Increase audience engagement and knowledge by dispensing information using Voice Recognition For Enhancing Security And Authentication Next Gen Business Transformation With Voice TC SS. This template helps you present information on four stages. You can also present information on Mobile Applications, Web Applications, Voice Commands using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Management Components Authentication Securing Systems With Identity
Access Management Components Authentication Securing Systems With IdentityThis slide gives an overview of access management of the Identity and Access Management process. The purpose of this slide is to explain access management that primarily focuses on authentication and authorization. Increase audience engagement and knowledge by dispensing information using Access Management Components Authentication Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IAM Authentication And Authorization Workflow Process Securing Systems With Identity
IAM Authentication And Authorization Workflow Process Securing Systems With IdentityThis slide showcases the workflow of IAM authentication and authorization. The purpose of this slide is to explain the process, starting with user authentication and authorization, that often uses a single sign-on solution that incorporates multi-factor authentication and assigns access rights to resources. Increase audience engagement and knowledge by dispensing information using IAM Authentication And Authorization Workflow Process Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Digital Authentication With IAM Securing Systems With Identity
Steps To Implement Digital Authentication With IAM Securing Systems With IdentityThis slide discusses the IAM implementing digital authentication. The purpose of this slide is to highlight the various types of digital authentication done by IAM, which are unique passwords, pre-shared keys, Behavioral authentication, and biometrics. Increase audience engagement and knowledge by dispensing information using Steps To Implement Digital Authentication With IAM Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Unique Passwords, Biometrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Biometric Authentication With IAM Securing Systems With Identity
Various Types Of Biometric Authentication With IAM Securing Systems With IdentityIncrease audience engagement and knowledge by dispensing information using Various Types Of Biometric Authentication With IAM Securing Systems With Identity This template helps you present information on One stages. You can also present information on Iris Recognition, Dna Matching, Privacy Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advantages Of Biometric Authentication For Mobile Devices Mobile Security
Advantages Of Biometric Authentication For Mobile Devices Mobile SecurityThis slide represents the advantages of biometric authentication for mobile devices which include enhanced security, personalized experience and efficiency. Increase audience engagement and knowledge by dispensing information using Advantages Of Biometric Authentication For Mobile Devices Mobile Security This template helps you present information on Five stages. You can also present information on Enhanced Security, Personalized Experience using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Using SMS In Two Factor Authentication Mobile Security
Benefits Of Using SMS In Two Factor Authentication Mobile SecurityThis slide represents the benefits of using SMS in two factor authentication in mobile security which includes security, speed and access and wide availability. Introducing Benefits Of Using SMS In Two Factor Authentication Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Policy, Mobile Security using this template. Grab it now to reap its full benefits.
-
 Biometric Authentication In Mobile Device Security Mobile Security
Biometric Authentication In Mobile Device Security Mobile SecurityThis slide gives an overview of biometric authentication in mobile device security which includes enable authentication in app and support unlocking, etc. Introducing Biometric Authentication In Mobile Device Security Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Budget Category, Estimated Cost, Actual Cost using this template. Grab it now to reap its full benefits.
-
 Common Threats Addressed By Two Factor Authentication Mobile Security
Common Threats Addressed By Two Factor Authentication Mobile SecurityThis slide discusses the common threats addressed by two factor authentication which includes stolen passwords, social engineering, key logging, etc. Increase audience engagement and knowledge by dispensing information using Common Threats Addressed By Two Factor Authentication Mobile Security This template helps you present information on Six stages. You can also present information on Sandbox Isolation, Robust Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Factors Of Authentication In Mobile Security Mobile Security
Key Factors Of Authentication In Mobile Security Mobile SecurityThis slide highlights the key factors of authentication in mobile security which include knowledge factor, inherence factor, time factor and possession factor. Increase audience engagement and knowledge by dispensing information using Key Factors Of Authentication In Mobile Security Mobile Security This template helps you present information on Six stages. You can also present information on Security Broker, Email Security, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Two Factor Authentication In Mobile Security Mobile Security
Two Factor Authentication In Mobile Security Mobile SecurityThis slide gives an overview of two factor authentication in mobile security and is defined as specific type of multi-factor authentication which strengthens access. Increase audience engagement and knowledge by dispensing information using Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Spear Phishing, Voice Phishing, Credential Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Two Factor Authentication In Mobile Security Mobile Security
Types Of Two Factor Authentication In Mobile Security Mobile SecurityThis slide discusses the types of two factor authentication in mobile security which includes SMS 2FA, push based 2FA, web authentication API and so on. Increase audience engagement and knowledge by dispensing information using Types Of Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on No Authentication, Hacker Access, Security Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Biometric Authentication For User Implementing E Commerce Security Measures
Steps To Implement Biometric Authentication For User Implementing E Commerce Security MeasuresThe slide highlights steps to implement biometric authentication systems effectively for buisness. Key steps include biometric assessment, integration, data security, user enrollment, testing and fallback mechanism etc. Increase audience engagement and knowledge by dispensing information using Steps To Implement Biometric Authentication For User Implementing E Commerce Security Measures. This template helps you present information on six stages. You can also present information on Choose Biometric Method, Fallback Mechanism, User Enrollment, Testing And Evaluation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS
Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SSThis slide represents training plan for verifying identity of user accessing a digital system. It includes details related to password authentication methods, training sessions etc. Deliver an outstanding presentation on the topic using this Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Token Authentication, Biometric Authentication, Strategic Password, Authentication Training Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multifactor Authentication Methods For Chatbot Security
Multifactor Authentication Methods For Chatbot SecurityThis slide shows information regarding various types of authentication techniques that can be used by organizations to verify a users identity. These techniques are one-time passwords, biometric authentication, and hardware tokens. Presenting our set of slides with Multifactor Authentication Methods For Chatbot Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hardware Tokens, Biometric Authentication, One Time Passwords.
-
 Two Factor Authentication To Enhance Chatbot Security
Two Factor Authentication To Enhance Chatbot SecurityThis slide shows a process that can be used to highlight how companies can use two-factor authentication to protect their chatbots against various security threats or vulnerabilities. It include three stages which are user enters credentials, OTP is sent to the user and user uses OTP to verify hi identity. Presenting our set of slides with Two Factor Authentication To Enhance Chatbot Security. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Key, Username, Email.
-
 User Authentication Techniques To Enhance Organizational Security
User Authentication Techniques To Enhance Organizational SecurityThis slide shows the different user authentication and authorization techniques that help to protect sensitive data. The various techniques explained are password-based, multi-factor, biometric, token-based, etc. Introducing our premium set of slides with User Authentication Techniques To Enhance Organizational Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Password Based, Multi Factor, Biometric, Token Based. So download instantly and tailor it with your information.
-
 Hypertext Transfer Protocol Authentication In Web Security Solution
Hypertext Transfer Protocol Authentication In Web Security SolutionThis slide showcases the HTTP authentication in web security which include HTTP Basic Authentication, HTTP Digest Authentication, etc. Introducing Hypertext Transfer Protocol Authentication In Web Security Solution to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Http Basic Authentication, Http Digest Authentication, Https Client Authentication, Form Based Authentication, using this template. Grab it now to reap its full benefits.
-
 Authentication For Web Application Security Icon
Authentication For Web Application Security IconPresenting our set of slides with Authentication For Web Application Security Icon This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication For Web, Application Security Icon
-
 Secure internet banking authentication ppt powerpoint presentation gallery portrait cpb
Secure internet banking authentication ppt powerpoint presentation gallery portrait cpbPresenting our Secure Internet Banking Authentication Ppt Powerpoint Presentation Gallery Portrait Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Student Loan Default This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Mobile Data Security Authentication Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Authentication Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Mobile data security authentication colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Mobile Data Security Authentication Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Mobile Data Security Authentication Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Mobile data security authentication monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.




