Powerpoint Templates and Google slides for Security Assessments
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Assessment And Management Plan For Information Security Powerpoint Presentation Slides
Risk Assessment And Management Plan For Information Security Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy one slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Cybersecurity Risk Assessment Program To Strengthen Organization Security Complete Deck
Cybersecurity Risk Assessment Program To Strengthen Organization Security Complete DeckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cybersecurity Risk Assessment Program To Strengthen Organization Security Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the Thirty Eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Risk Assessment In Cyber Security Powerpoint Ppt Template Bundles
Risk Assessment In Cyber Security Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Risk Assessment In Cyber Security Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The eighteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Risk Assessment In Cyber Security Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Cloud Computing Security Organisation Assessments Service Categories Responsibility
Cloud Computing Security Organisation Assessments Service Categories ResponsibilityThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Cloud Computing Security Organisation Assessments Service Categories Responsibility and has templates with professional background images and relevant content. This deck consists of total of twelve slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Technology Security Process Framework Assessment Management Awareness
Technology Security Process Framework Assessment Management AwarenessThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Data Quality Icon Assessment Security Certificate Verification Evaluation
Data Quality Icon Assessment Security Certificate Verification EvaluationIf you require a professional template with great design, then this Data Quality Icon Assessment Security Certificate Verification Evaluation is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Security Management Plan Measures Strategy Framework Symbol Assessment Improving
Security Management Plan Measures Strategy Framework Symbol Assessment ImprovingEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Security Management Plan Measures Strategy Framework Symbol Assessment Improving is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
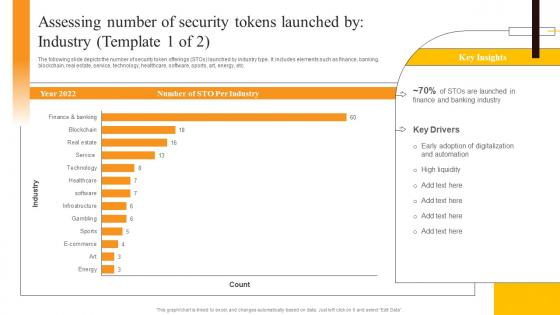 Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SSThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Industry Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Assessing Number, Security Tokens, Industry. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
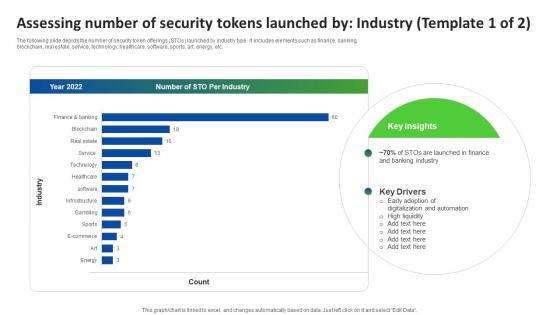 Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS V
Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS VThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Deliver an outstanding presentation on the topic using this Q142 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Industry BCT SS V. Dispense information and present a thorough explanation of Early Adoption, Digitalization And Automation, High Liquidity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security framework analysis management components organization assessment
Security framework analysis management components organization assessmentIf you require a professional template with great design, then this Security Framework Analysis Management Components Organization Assessment is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using eleven slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
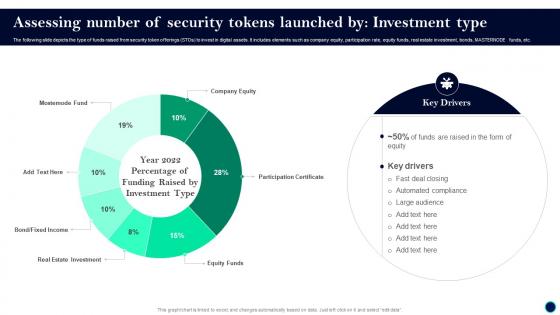
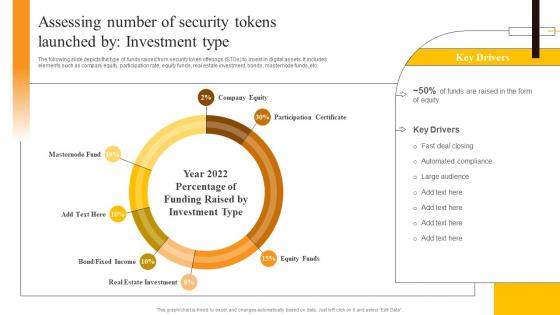 Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SSThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, masternode funds, etc. Deliver an outstanding presentation on the topic using this Assessing Number Of Security Tokens Launched By Investment Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Real Estate Investment, Participation Certificate, Company Equity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
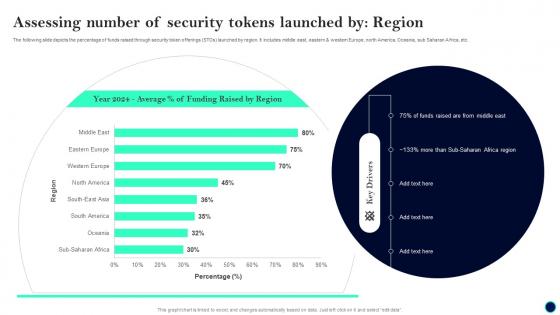
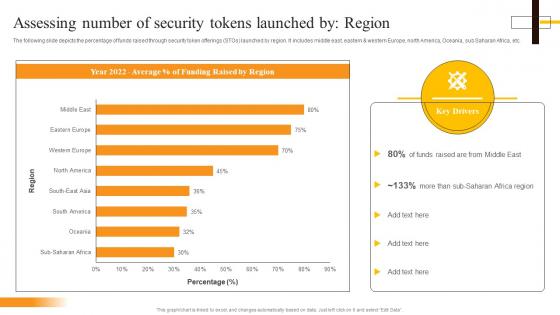 Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SS
Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SSThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Region Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Assessing Number, Security Tokens, Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
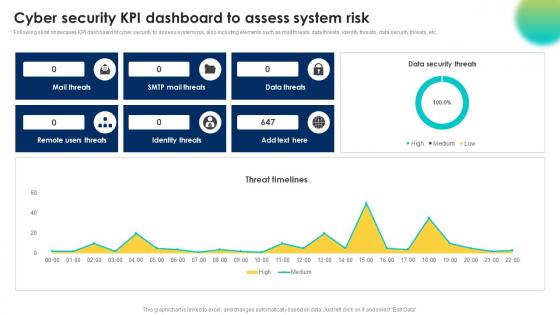 Cyber Security Kpi Dashboard To Assess System Risk
Cyber Security Kpi Dashboard To Assess System RiskFollowing slide showcases KPI dashboard of cyber security to assess system risk, also including elements such as mail threats, data threats, identity threats, data security threats, etc. Presenting our well structured Cyber Security Kpi Dashboard To Assess System Risk. The topics discussed in this slide are Identity Threats, Remote Users Threats, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Present the topic in a bit more detail with this Assessing Number Of Security Beginners Guide To Successfully Launch Security Token BCT SS V. Use it as a tool for discussion and navigation on Sto Per Industry, Banking Industry, Key Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V
Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Deliver an outstanding presentation on the topic using this Assessing Number Of Security Tokens Beginners Guide To Successfully Launch Security Token BCT SS V. Dispense information and present a thorough explanation of Assessing Number, Security Tokens Launched, Region using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V
Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, MASTERNODE funds, etc. Present the topic in a bit more detail with this Beginners Guide To Successfully Launch Security Token Assessing Number Of Security BCT SS V. Use it as a tool for discussion and navigation on Key Drivers, Deal Closing, Automated Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Security Threat Assessment Dashboard
Mobile Security Threat Assessment DashboardThis slide illustrates KPI or Dashboard of mobile security threat assessment and includes security incidents log, security compromised users or devices, and highly targeted networks. Introducing our Mobile Security Threat Assessment Dashboard set of slides. The topics discussed in these slides are Security Compromised Users Devices, Highly Targeted Networks, Security Incidents Log. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Testing Assessment And Vulnerabilities Dashboard
Security Testing Assessment And Vulnerabilities DashboardThis slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. Present the topic in a bit more detail with this Security Testing Assessment And Vulnerabilities Dashboard. Use it as a tool for discussion and navigation on Security Testing Assessment, Vulnerabilities Dashboard, Business Impact, Technical Impacts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App
Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery AppThis slide covers statistics to assess need of integrating third party platform for delivering food. It involves features such as free and fast delivery or discounts. Present the topic in a bit more detail with this Securing Food Safety In Online Statistics To Assess Need Of Outsourcing Food Delivery App. Use it as a tool for discussion and navigation on Statistics To Assess, Need Outsourcing Food Delivery App. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operation Center Risk Assessment Dashboard
Security Operation Center Risk Assessment DashboardThe following slide illustrates a risk assessment dashboard helps to understand the risk rating breakdown, action plan, top vulnerabilities, etc. of a business. Introducing our Security Operation Center Risk Assessment Dashboard set of slides. The topics discussed in these slides are Risk Assessment Progress, Solved, Action Plan, Risk Rating Breakdown. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Q143 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
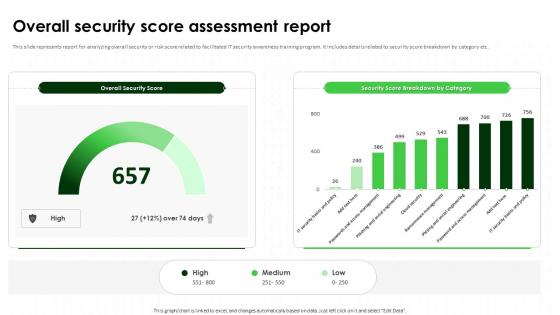 Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS
Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing overall security or risk score related to facilitated IT security awareness training program. It includes details related to security score breakdown by category etc. Deliver an outstanding presentation on the topic using this Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Overall Security Score, Assessment Report, Security Or Risk Score, Awareness Training Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V
Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS VThe following slide depicts the type of funds raised from security token offerings STOs to invest in digital assets. It includes elements such as company equity, participation rate, equity funds, real estate investment, bonds, masternode funds, etc. Present the topic in a bit more detail with this Assessing Number Of Security Tokens Launched By Ultimate Guide Smart BCT SS V. Use it as a tool for discussion and navigation on Fast Deal Closing, Automated Compliance, Large Audience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V
Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS VThe following slide depicts the percentage of funds raised through security token offerings STOs launched by region. It includes middle east, eastern and western Europe, north America, Oceania, sub Saharan Africa, etc. Present the topic in a bit more detail with this Ultimate Guide Smart Assessing Number Of Security Tokens Launched By Region BCT SS V. Use it as a tool for discussion and navigation on Funds Raised, Sub Saharan, Africa Region. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Dashboard
Information Technology Security Assessment DashboardThis slide represents dashboard for information technology security assessment which includes elements such as intrusion attempts, mean resolve time, mean detect time, etc. Introducing our Information Technology Security Assessment Dashboard set of slides. The topics discussed in these slides are Intrusion Attempts, IT Security Rating, Phishing Test Success Rate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security it assessment matrix of cyber risks ppt slides outline
Data security it assessment matrix of cyber risks ppt slides outlineThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Data Security IT Assessment Matrix Of Cyber Risks Ppt Slides Outline. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Mobile, Web Applications, Health Care. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security assessment matrix of cyber risks ppt grid
Computer system security assessment matrix of cyber risks ppt gridThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Increase audience engagement and knowledge by dispensing information using Computer System Security Assessment Matrix Of Cyber Risks Ppt Grid. This template helps you present information on one stages. You can also present information on Industrial, Data Center, Multifamily, Retail, Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Security Risk Assessments Exists In Powerpoint And Google Slides Cpb
Types Security Risk Assessments Exists In Powerpoint And Google Slides CpbPresenting our Types Security Risk Assessments Exists In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Types Security Risk Assessments Exists. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Steps For Digital Security Risk Assessment And Evaluation
Steps For Digital Security Risk Assessment And EvaluationThis slide showcase cyber risk assessment with standard risk identification to align organizational objective. It includes context establishment, risk identification, risk assessment and risk evaluation. Introducing our premium set of slides with Steps For Digital Security Risk Assessment And Evaluation. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Calculate, Penetration. So download instantly and tailor it with your information.
-
 Step 3 Assess The Environment Zero Trust Security Model
Step 3 Assess The Environment Zero Trust Security ModelThis slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Deliver an outstanding presentation on the topic using this Step 3 Assess The Environment Zero Trust Security Model. Dispense information and present a thorough explanation of Knowledge, Categorizations, Structures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations
Cyber Security Risk Assessment And Technology Deployment Plan To Improve OrganizationsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations. Dispense information and present a thorough explanation of Consequences, Vulnerability, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of Contents
Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of ContentsIntroducing Security Plan To Prevent Cyber Cybersecurity Risk Assessment Program For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risk, Assessment Program, Conduct Cybersecurity, Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk Assessment
Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Multistep Approach To Conduct Cybersecurity Risk Assessment. This template helps you present information on four stages. You can also present information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact
Security Plan To Prevent Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Security Risk Assessment Program Implementation Impact. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation Impact
Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
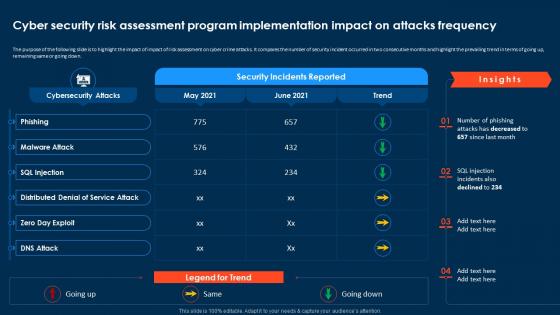 Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact
Compressive Planning Guide Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Compressive Planning Guide Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment Program, Attacks Frequency, Distributed Denial Of Service Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Security Compliance Tools
Comparative Assessment Of Security Compliance ToolsThis slide shows security compliance tools analysis and comparison which helps to determine best and effective tools for business. It further includes tools such as vanta, drata, sprinto etc. Presenting our well structured Comparative Assessment Of Security Compliance Tools. The topics discussed in this slide are Industries Involved, Market Segment.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Compliance Audits For Risk Assessment
Security Compliance Audits For Risk AssessmentThis slide shows risk and assessment audits of security compliance which helps to make penetration tests and vulnerability assessments. It further includes requirements such as performing regular risk assessments, carrying out audits and establishing remedition plan etc. Introducing our premium set of slides with Security Compliance Audits For Risk Assessment. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Performing Regular, Carrying Out Internal. So download instantly and tailor it with your information.
-
 Conduct Third Party Risks Assessment Improving Cyber Security Risks Management
Conduct Third Party Risks Assessment Improving Cyber Security Risks ManagementThe following slide illustrates the actions to perform third party risk analysis to eliminate unnecessary threats. It includes elements such as planning, selection, negotiation, monitoring, termination, tracking compliance, setting security standards etc. Introducing Conduct Third Party Risks Assessment Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Planning, Selection, Negotiation, Monitoring, Termination, using this template. Grab it now to reap its full benefits.
-
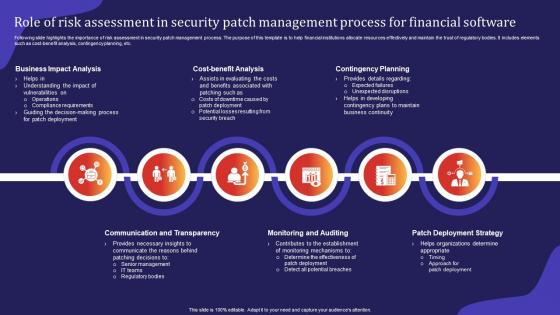 Role Of Risk Assessment In Security Patch Management Process For Financial Software
Role Of Risk Assessment In Security Patch Management Process For Financial SoftwareFollowing slide highlights the importance of risk assessment in security patch management process. The purpose of this template is to help financial institutions allocate resources effectively and maintain the trust of regulatory bodies. It includes elements such as cost benefit analysis, contingency planning, etc.Introducing our premium set of slides with Role Of Risk Assessment In Security Patch Management Process For Financial Software. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Contingency Planning, Communication Transparency, Monitoring Auditing. So download instantly and tailor it with your information.
-
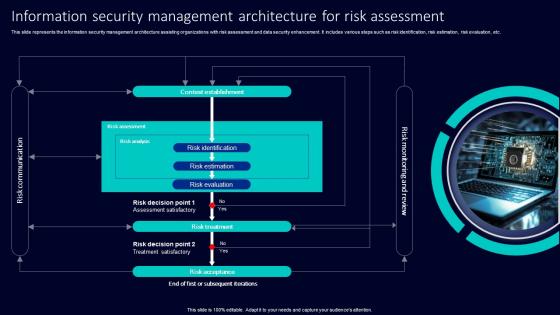 Information Security Management Architecture For Risk Assessment
Information Security Management Architecture For Risk AssessmentThis slide represents the information security management architecture assisting organizations with risk assessment and data security enhancement. It includes various steps such as risk identification, risk estimation, risk evaluation, etc. Presenting our set of slides with Information Security Management Architecture For Risk Assessment. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Identification, Risk Estimation, Risk Evaluation.
-
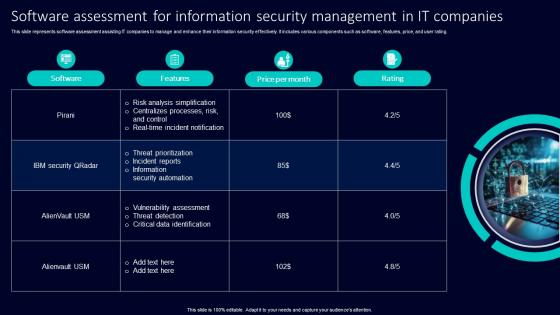 Software Assessment For Information Security Management In It Companies
Software Assessment For Information Security Management In It CompaniesThis slide represents software assessment assisting IT companies to manage and enhance their information security effectively. It includes various components such as software, features, price, and user rating. Presenting our set of slides with Software Assessment For Information Security Management In It Companies. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Analysis Simplification, Centralizes Processes, Risk Control, Real Time Incident Notification.
-
 Conducting Vulnerability Assessment To Respond And Recover Hands On Blockchain Security Risk BCT SS V
Conducting Vulnerability Assessment To Respond And Recover Hands On Blockchain Security Risk BCT SS VThe following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Present the topic in a bit more detail with this Conducting Vulnerability Assessment To Respond And Recover Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Identity, Protect, Detect, Respond. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V
Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Introducing Performing Threat Assessment For Cause Identification Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Attack Vectors, Causes, using this template. Grab it now to reap its full benefits.
-
 Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS
Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SSThis slide provides glimpse about comparative analysis of cyber security and risk management tools that can help the business in mitigating cyber threats. It includes key features, pricing, deployment, etc. Deliver an outstanding presentation on the topic using this Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS. Dispense information and present a thorough explanation of Management Software, Cybersecurity, Supported Platforms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Vulnerability Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V
Conducting Vulnerability Assessment Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity vulnerability assessment framework to optimize resilience and transparency. It includes key elements such as identify, protect, respond, recover, etc. Present the topic in a bit more detail with this Conducting Vulnerability Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Identity, Protect, Detect. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V
Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Increase audience engagement and knowledge by dispensing information using Performing Threat Assessment Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on one stages. You can also present information on Double Spending, Mining Threats, Wallet Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
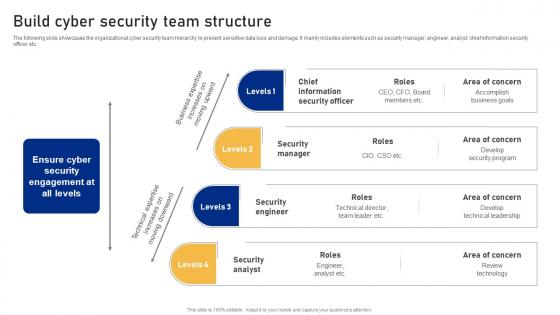 Build Cyber Security Team Structure Cyber Risk Assessment
Build Cyber Security Team Structure Cyber Risk AssessmentThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Increase audience engagement and knowledge by dispensing information using Build Cyber Security Team Structure Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Information Security Officer, Security Manager, Security Engineer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Facts And Statistics Cyber Risk Assessment
Cyber Security Awareness Facts And Statistics Cyber Risk AssessmentThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Facts And Statistics Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Malware Attacks, Company, Social Engineering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment
Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk AssessmentThe following slide depicts some figures to analyze the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Highlighting, Cyber Security Unawareness using this template. Grab it now to reap its full benefits.
-
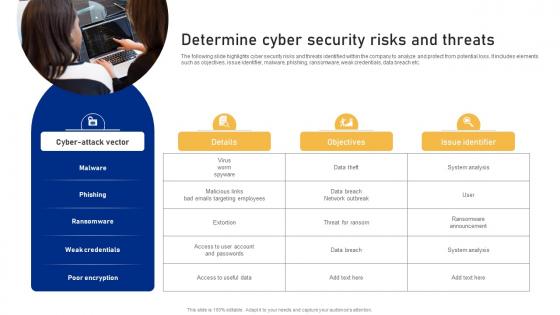 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Cyber Security Trend Analysis Cyber Risk Assessment
Global Cyber Security Trend Analysis Cyber Risk AssessmentThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Deliver an outstanding presentation on the topic using this Global Cyber Security Trend Analysis Cyber Risk Assessment Dispense information and present a thorough explanation of Global Cyber Security, Trend Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
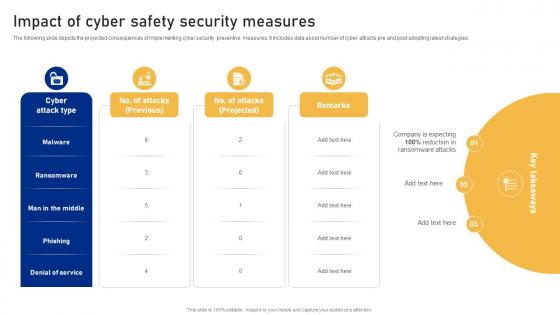 Impact Of Cyber Safety Security Measures Cyber Risk Assessment
Impact Of Cyber Safety Security Measures Cyber Risk AssessmentThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack, Ransomware, Projected This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Cyber Risk Assessment
Impact Of Cyber Security Policies And Practices Cyber Risk AssessmentThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Introducing Impact Of Cyber Security Policies And Practices Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Guidelines, Management, Privacy Policies using this template. Grab it now to reap its full benefits.
-
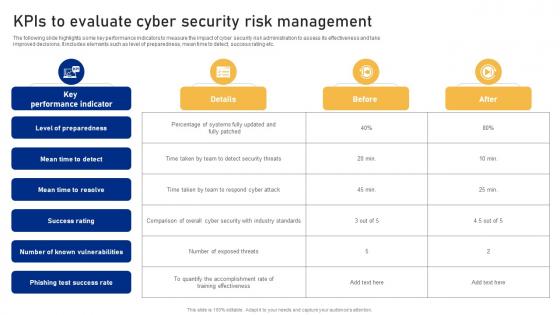 KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment
KPIS To Evaluate Cyber Security Risk Management Cyber Risk AssessmentThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment Use it as a tool for discussion and navigation on Performance Indicator, Success Rating, Risk Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment
Organize Cyber Security Training For Employees Regularly Cyber Risk AssessmentThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment Use it as a tool for discussion and navigation on Document Management, Passwords, Social Media Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment
Prioritize Cyber Security Risk With Severity Matrix Cyber Risk AssessmentThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment Use it as a tool for discussion and navigation on Prioritize, Cyber Security Risk, Severity Matrix This template is free to edit as deemed fit for your organization. Therefore download it now.
-
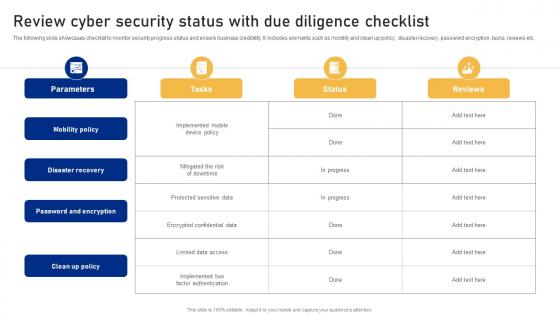 Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment
Review Cyber Security Status With Due Diligence Checklist Cyber Risk AssessmentThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment Use it as a tool for discussion and navigation on Mobility Policy, Disaster Recovery, Password And Encryption This template is free to edit as deemed fit for your organization. Therefore download it now.




