Powerpoint Templates and Google slides for Security Architects
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Components Of Zero Trust Security Architecture
Components Of Zero Trust Security ArchitectureThis slide depicts the critical elements of a zero trust network architecture. The purpose of this slide is to help the business establish network security by safeguarding all components. It includes component such as zero trust architecture, micro segmentation, etc. Presenting our well structured Components Of Zero Trust Security Architecture. The topics discussed in this slide are Access Controls, Zero Trust Network Architecture, Real Time Monitoring. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Framework For Zero Trust Architecture Security
Framework For Zero Trust Architecture SecurityThis slide highlights the flowchart for a zero trust architecture. The purpose of this slide is to help the business establish an efficient zero trust architecture to protect its networks against cyberattacks. it includes elements such as access identities, endpoints, etc. Introducing our Framework For Zero Trust Architecture Security set of slides. The topics discussed in these slides are Access Identities, Execution Security Policy, Threat Assessment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Digital Security Through Zero Trust Architecture
Icon For Digital Security Through Zero Trust ArchitecturePresenting our well structured Icon For Digital Security Through Zero Trust Architecture. The topics discussed in this slide are Icon Digital Security, Zero Trust Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon For Network Security Through Zero Trust Architecture
Icon For Network Security Through Zero Trust ArchitecturePresenting our set of slides with Icon For Network Security Through Zero Trust Architecture. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Network Security, Zero Trust Architecture.
-
 Multiple Types Of Zero Trust Security Architecture
Multiple Types Of Zero Trust Security ArchitectureThis slide highlights the various zero trust security architecture. The purpose of this slide is to help develop a comprehensive zero trust architecture for reducing surfaces attacks. It includes architectures such as identity based, network based, data based, etc. Introducing our premium set of slides with Multiple Types Of Zero Trust Security Architecture. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Based Zero Trust, Data Based Zero Trust, Identity Based Zero Trust. So download instantly and tailor it with your information.
-
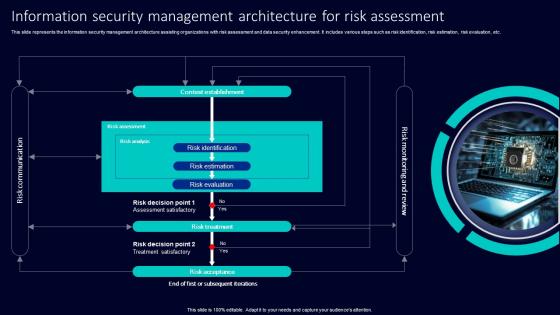 Information Security Management Architecture For Risk Assessment
Information Security Management Architecture For Risk AssessmentThis slide represents the information security management architecture assisting organizations with risk assessment and data security enhancement. It includes various steps such as risk identification, risk estimation, risk evaluation, etc. Presenting our set of slides with Information Security Management Architecture For Risk Assessment. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Identification, Risk Estimation, Risk Evaluation.
-
 Components Of 5G Security Architecture To Prevent Cyberattacks
Components Of 5G Security Architecture To Prevent CyberattacksThis slide depicts the components of a 5 G security architecture utilized for preventing cyber attacks. The purpose of this slide is to help the business safeguard its networks through proper implementation of critical components such as network security, scaling security, etc. Presenting our set of slides with Components Of 5G Security Architecture To Prevent Cyberattacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Hardware, Security.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Cloud Access Security Broker Architecture Next Generation CASB
Overview Of Cloud Access Security Broker Architecture Next Generation CASBThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Present the topic in a bit more detail with this Overview Of Cloud Access Security Broker Architecture Next Generation CASB Use it as a tool for discussion and navigation on Organization, Direct To Cloud, Broker Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Standard Architectural Implementations Of Network Firewalls
Firewall Network Security Standard Architectural Implementations Of Network FirewallsThis slide outlines the common architectural deployments of network firewalls. The purpose of this slide is to showcase the different architectural implementations of firewalls, including packet filtering routers, screened host firewalls, dual-homed host, and screened subnet with DMZ. Present the topic in a bit more detail with this Firewall Network Security Standard Architectural Implementations Of Network Firewalls Use it as a tool for discussion and navigation on Access Control List, Workflow, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Architecture Of Web Application Firewall System
Firewall Network Security Architecture Of Web Application Firewall SystemThis slide represents the framework of the web application firewall. The purpose of this slide is to showcase the WAF architecture and its various parts such as core infrastructure, visibility, compliance, active threat monitoring, availability and support, and policy management. Present the topic in a bit more detail with this Firewall Network Security Architecture Of Web Application Firewall System Use it as a tool for discussion and navigation on Policy Management, Malicious Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Circuit Level Gateways Overview And Architecture
Firewall Network Security Circuit Level Gateways Overview And ArchitectureThis slide introduces the circuit-level gateways and their architecture. The purpose of this slide is to give an overview of the circuit-level gateway, including its features, providers and benefits, such as hiding the internal host from serving the host, lower processing than application-level gateways, inexpensive, and so on. Introducing Firewall Network Security Circuit Level Gateways Overview And Architecture to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Features, Providers, Benefits using this template. Grab it now to reap its full benefits.
-
 Saas Software Architectural Framework For Data Security
Saas Software Architectural Framework For Data SecurityThis slide demonstrates SaaS software architectural framework for contributing to design, development and operation of scalable and efficient cloud based applications. It includes basis such as autonomous management, user interface, operational processes, application layer, etc. Introducing our Saas Software Architectural Framework For Data Security set of slides. The topics discussed in these slides are Autonomous Management, Service Provider, Subscriber This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SD WAN Model Secure Access Service Edge Architecture Characteristics
SD WAN Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing SD WAN Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Architecture Characteristics, Cloud Native, Global Distribution, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Sase Architecture
SD WAN Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service Edge, Architecture And Its Goals, Geographic Distribution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Access Service Edge Architecture Characteristics
Sase Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing Sase Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identity Driven, Support For All Edges, Globally Distributed, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Sase Architecture
Sase Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE Architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this Sase Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service, Edge Sase Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Virtual Desktop Infrastructure Security Architecture
Benefits Of Virtual Desktop Infrastructure Security ArchitectureThis slide highlights the virtual desktop infrastructure security architecture. The purpose of this slide is to help improve the business through installation of virtual desktop security architecture. It includes benefits such as unified management platform, real time compliance monitoring, etc.. Presenting our set of slides with Benefits Of Virtual Desktop Infrastructure Security Architecture. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Scanning, Prevention.
-
 Security Architecture Document In Powerpoint And Google Slides Cpb
Security Architecture Document In Powerpoint And Google Slides CpbPresenting our Security Architecture Document In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Security Architecture Document. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It
Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Internet Protocol Security. The main components of IPsec architecture are ESP protocol, AH protocol, encryption algorithm, authentication algorithm, key management, etc. Present the topic in a bit more detail with this Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protocol Security, Architecture, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS
Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Present the topic in a bit more detail with this Blockchain Based IoT Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Storage Communication, Network Management, Routing Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SS
Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SSThis slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Present the topic in a bit more detail with this Categorization Of IoT Architecture Security Concerns IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Insecure Cloud Interface, Insecure Mobile Interface, Insecure Security Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SS
IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide showcases edge computing architecture that helps in improving performance and reduce latency through real time data processing. It includes three layers such as cloud layer, edge layer, and device layer. Deliver an outstanding presentation on the topic using this IoT Based Edge Computing Three Layer Architecture IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Data Processing, Data Catching, Critical Data Storage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS
IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SSThis slide exhibits a multi layer architecture aimed at enhancing data processing and communication. It includes layers such as the application layer, processing layer, transport layer, and perception layer.Increase audience engagement and knowledge by dispensing information using IoT Ecosystem Multi Layer Architecture IoT Security And Privacy Safeguarding IoT SS. This template helps you present information on four stages. You can also present information on Communication Technologies, Processing Layer, Network Layer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working And Architecture Of Firewall Security Technology Firewall Virtualization
Working And Architecture Of Firewall Security Technology Firewall VirtualizationThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Deliver an outstanding presentation on the topic using this Working And Architecture Of Firewall Security Technology Firewall Virtualization. Dispense information and present a thorough explanation of Firewall Architecture, Corporate Network, Control System Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway
Internet Gateway Security IT Architecture Of Citrix Secure Web GatewayThis slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Architecture Of Citrix Secure Web Gateway. Use it as a tool for discussion and navigation on Citrix ADC Appliance, URL Filtering, Policies, Citrix Application Delivery Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Integration Of Swg Inside Sase Architecture
Internet Gateway Security IT Integration Of Swg Inside Sase ArchitectureThis slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Introducing Internet Gateway Security IT Integration Of Swg Inside Sase Architecture to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Web Sites, Cloud Apps, Private Cloud, Corporate Datacenter, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Architecture And Working
Internet Gateway Security IT Secure Web Gateway Architecture And WorkingThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Introducing Internet Gateway Security IT Secure Web Gateway Architecture And Working to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Malware Detection, Web Proxy, Public Internet, using this template. Grab it now to reap its full benefits.
-
 Wireless Internet Network Security Architecture
Wireless Internet Network Security ArchitectureThis slide delineates essential components, such as LAN, firewall, and WAN, elucidating the wireless internet network security architecture. It offers valuable insights crucial for organizational planning and strategizing security measures effectively. Introducing our Wireless Internet Network Security Architecture set of slides. The topics discussed in these slides are Network Security, Architecture, Confidentiality. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hybrid It Cloud Server Security Architecture
Hybrid It Cloud Server Security ArchitectureFollowing slide showcases architecture of hybrid IT cloud server security, also including elements such as IAAS provider A,B,C, on premises, mergers and acquisitions, etc. Presenting our set of slides with Hybrid It Cloud Server Security Architecture. This exhibits information on fourstages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on On Premises, Mergers And Acquisitions, Security Architecture.
-
 Architecture Of Cyber Security Monitoring
Architecture Of Cyber Security MonitoringFollowing slide showcases cyber security monitoring architecture for enhanced incident investigation. It further covers monitoring servers, wireless connections, web applications, web server, network monitoring, firewall configuration and allowed or blocked connections etc. Presenting our set of slides with Architecture Of Cyber Security Monitoring This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall Configurations, Network Monitoring, Web Server.
-
 Endpoint Encryption Architecture For Comprehensive Security
Endpoint Encryption Architecture For Comprehensive SecurityThis slide represents architecture of endpoint encryption which assists to provide advance levels of security to valuable corporate data and make it unreadable to unauthorised users. It includes endpoint architecture components such as server, database, manager, etc. Introducing our premium set of slides with name Endpoint Encryption Architecture For Comprehensive Security. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Endpoint Encryption Server, Endpoint Database, Security Center. So download instantly and tailor it with your information.
-
 Cloud Access Security Broker Architectural Components CASB Cloud Security
Cloud Access Security Broker Architectural Components CASB Cloud SecurityThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components CASB Cloud Security. Dispense information and present a thorough explanation of Secondary Enterprise Core, Bidirectional Integration, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Cloud Access Security Broker Architecture CASB Cloud Security
Overview Of Cloud Access Security Broker Architecture CASB Cloud SecurityThis slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Present the topic in a bit more detail with this Overview Of Cloud Access Security Broker Architecture CASB Cloud Security. Use it as a tool for discussion and navigation on Infrastructure As A Service, Bidirectional Integration, Connectivity Gateway. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Architectural Big Data In Cyber Security
Architectural Big Data In Cyber SecurityThis slide depicts the tactics used to protect cyber security network using big data analytics. Its aim is to use various tactics and secure the cyber network against the threats. This slide includes performance, accuracy, scalability, reliability, security, usability, etc. Introducing our Architectural Big Data In Cyber Security set of slides. The topics discussed in these slides are Performance, Accuracy, Scalability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mobile Security Architecture On Android Platform
Mobile Security Architecture On Android PlatformThis slide illustrates architectural diagram of mobile security for android users and includes tools, software framework, modules, and kernel space. Introducing our Mobile Security Architecture On Android Platform set of slides. The topics discussed in these slides are Tools, Software Framework, Modules, Kernel Space. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Mesh Architecture
Cyber Security Mesh ArchitectureThe following slide highlights components like centralized dashboard, alerting, investigation, reporting, users, robotics, and processes in the cybersecurity mesh architecture. It aids in illustrating the structure and functionalities of the system. Presenting our well structured Cyber Security Mesh Architecture The topics discussed in this slide are Centralized Dashboard, Centralized Alerting, Centralized Reporting This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ethical Hacking Architecture For Information Security
Ethical Hacking Architecture For Information SecurityThis slide lays out framework for ethical hacking to analyze software vulnerabilities using machine learning algorithms. The purpose of this slide is to help organizations in preventing insider threats. It covers elements such as threat factors, incidents, vulnerabilities, hacking risks, etc.Presenting our well structured Ethical Hacking Architecture For Information Security The topics discussed in this slide are Remediation Strategies, Potential Vulnerabilities, Network Security Testing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide
Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File GuideThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Introducing Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Limitations, Solution, using this template. Grab it now to reap its full benefits.
-
 Mobile Device Security Reference Architecture
Mobile Device Security Reference ArchitectureThis slide is a representation of architecture for mobile security reference which includes key components and displays the network traffic and log data. Presenting our well structured Mobile Device Security Reference Architecture. The topics discussed in this slide are Enterprise Mobile Services, Enterprise Core Services, External Facing Mobile Services. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mobile Security Access Server Architecture
Mobile Security Access Server ArchitectureThis slide is a representation of high level view of mobile security access server architecture which includes mobile security manager, business applications, etc. Introducing our Mobile Security Access Server Architecture set of slides. The topics discussed in these slides are Mobile Security Access, Server Architecture, Business Applications, Mobile Application Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Owasp Mobile Application Security Architecture
Owasp Mobile Application Security ArchitectureThis slide is a representation of architecture of mobile application security design which includes requirements, design, verification and rulebooks. Presenting our well structured Owasp Mobile Application Security Architecture. The topics discussed in this slide are Mobile Application, Security Architecture, Verification And Rulebooks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA
M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTAThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA. Dispense information and present a thorough explanation of Factors, Traditional Security Model, ZTNA using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Architecture Of Security Testing In Digital Landscape
Architecture Of Security Testing In Digital LandscapeThis slide highlights the architecture of security testing components such as user interface, controller, tester, test report, test case, etc. Present the topic in a bit more detail with this Architecture Of Security Testing In Digital Landscape. Use it as a tool for discussion and navigation on Source Code Analyzer, Web Application Scanner, Host Vulnerability, Scanner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internal Architecture Of Web Services Security
Internal Architecture Of Web Services SecurityThis slide lays out framework for web services security. The purpose of this slide is to help businesses in modeling security agents regarding authentication and authorization provided by web container. It covers components such as token service, provider plugin, client interface, etc. Presenting our well structured Internal Architecture Of Web Services Security The topics discussed in this slide are Provider Plugin, Web Security Service Client, Web Security Service Provider This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Secure Communications, Secure Cloud, Secure Device, Messaging Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Email Security Guard Gateway Architecture
Email Security Guard Gateway ArchitectureThis slide is an overview of architecture of email security guard gateway which include components like cloud protection layer, message center, internet, etc. Introducing our Email Security Guard Gateway Architecture set of slides. The topics discussed in these slides are Email Security, Guard Gateway, Architecture. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Reference Architecture For Next Generation Cyber Security Framework
Reference Architecture For Next Generation Cyber Security FrameworkThis slide illustrates the reference architecture for next generation cyber security framework which includes identity management, user interface, etc. Deliver an outstanding presentation on the topic using this Reference Architecture For Next Generation Cyber Security Framework. Dispense information and present a thorough explanation of Reference Architecture, Cyber Security Framework, Identity Management, Context Repository using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IP Security Architecture For Key Management
IP Security Architecture For Key ManagementThis slide showcase model IP security. The main purpose of this template is to showcase encryption algorithm. This includes architecture, ESP protocol, AH Protocol, encryption algorithm, key management, etc. Presenting our well structured IP Security Architecture For Key Management. The topics discussed in this slide are Encryption Algorithm, Authentication Algorithm, Key Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Hids Cyber Security Architecture And Working
Hids Cyber Security Architecture And WorkingThis slide represents HIDS cyber security architecture and working which operates in encrypted network environment and prevents network based attacks. It includes ley components such as touter, firewall, IDS, etc Presenting our well structured Hids Cyber Security Architecture And Working. The topics discussed in this slide are Architecture, Administrator, Computers. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Architecture For Security Vulnerability In Iot
Architecture For Security Vulnerability In IotFollowing slide higlhights security vulnerability in IOT for protecting company sensitive data. It further covers personal and public network and also includes IoT devices, IoT gateway. Presenting our well structured Architecture For Security Vulnerability In Iot The topics discussed in this slide are Abstraction Level, Technical Details, Perception LayerThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 SIEM Cyber Security Architecture Platform
SIEM Cyber Security Architecture PlatformThis slide showcases the SIEM cyber security architecture. Its aim is to investigate security incidents and detect attacks. This slide includes network traffic, firewall, logs, reports, analyse and investigate. Presenting our set of slides with name SIEM Cyber Security Architecture Platform. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Investigate, Analyse, Reports.
-
 Multilayer Blockchain Based Security Architecture
Multilayer Blockchain Based Security ArchitectureIntroducing our premium set of slides with Multilayer Blockchain Based Security Architecture. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Postman Configure, Hyperledger Fabric Network, Rest Server. So download instantly and tailor it with your information.
-
 Benefits Of Desktop As A Service Security Architecture
Benefits Of Desktop As A Service Security ArchitectureThis slide highlights the benefits of installing a desktop as a service security architecture. The purpose of this slide is to help the business leverage DaaS to improve its efficiency and profitability. It includes DRaaS, MFA for additional security, etc. Introducing our premium set of slides with Benefits Of Desktop As A Service Security Architecture Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Additional Security, Updates And Security Patches So download instantly and tailor it with your information.
-
 SaaS Architecture For Security Icon
SaaS Architecture For Security IconIntroducing our premium set of slides with name SaaS Architecture For Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like SaaS Architecture, Security. So download instantly and tailor it with your information.
-
 Architecture Of Identity And Access Management Process Securing Systems With Identity
Architecture Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the architecture structure of the Identity and Access Management process. The purpose of this slide is to explain the architecture of IAM that is capable of offering multiple data views and enables single sign-on. Present the topic in a bit more detail with this Architecture Of Identity And Access Management Process Securing Systems With Identity Use it as a tool for discussion and navigation on Internet, Corporate Demilitarized Zone, Customers Partners This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Platform Driven Security Operations Center Architecture
Platform Driven Security Operations Center ArchitectureThis slide represents a platform driven architecture for security operations that shows the insights related to security environments, platforms, and services. Introducing our Platform Driven Security Operations Center Architecture set of slides. The topics discussed in these slides are Data Lake, Cloud, Application, Endpoint. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Generic Database Architecture Of Mobile Security Mobile Security
Generic Database Architecture Of Mobile Security Mobile SecurityThis slide illustrates the key database architecture of mobile security which include mobile worker, internet, mobile server, firewall and database server. Present the topic in a bit more detail with this Generic Database Architecture Of Mobile Security Mobile Security Use it as a tool for discussion and navigation on Logical Device Access, Mobile Functions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSDeliver an outstanding presentation on the topic using this Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Process, Output, Input using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Management, Contact Distribution, Endpoint Protection Clients. This template is free to edit as deemed fit for your organization. Therefore download it now.





