Powerpoint Templates and Google slides for Security And Ethics
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Ethical Hacking And Network Security Powerpoint Presentation Slides
Ethical Hacking And Network Security Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Ethical Hacking And Network Security Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of eighty six slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors
Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different SectorsThis slide depicts the requirement of ethical hackers in different sectors such as the medical, military, government sector, and corporate sectors. Present the topic in a bit more detail with this Ethical Hacking And Network Security Requirement Of Ethical Hackers In Different Sectors. Use it as a tool for discussion and navigation on Requirement Of Ethical Hackers, Military, Government Sector, Corporate Sectors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker
Ethical Hacking And Network Security Skills And Certifications Required For Ethical HackerThis slide describes the skills and certifications required for ethical hacker, such as computer networking skills, computer skills, Linux skills, and so on. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Skills And Certifications Required For Ethical Hacker. Dispense information and present a thorough explanation of Skills And Certifications, Ethical Hacker, Computer Networking Skills, Computer Skills, Linux Skills using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security White Hat Hacker Vs Black Hat Hacker
Ethical Hacking And Network Security White Hat Hacker Vs Black Hat HackerThis slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security White Hat Hacker Vs Black Hat Hacker. Dispense information and present a thorough explanation of Hacker Vs Black Hat Hacker, Legality, Ownership, Tactics And Methodologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background Images
Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background ImagesIntroducing Table Of Contents For Ethical Hacking And Network Security Ppt Ideas Background Images to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Problems Ethical Hackers Can Solve, Ethical Hacking Training Program, Hacking And Ethical Hacking, Benefits And Limitations Of Ethical Hacking, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Dashboard For Ethical Hacking
Ethical Hacking And Network Security Dashboard For Ethical HackingThis slide depicts the dashboard for ethical hacking by covering the details of top priorities issues, exposure time, problems discovered, and critical threat level. Present the topic in a bit more detail with this Ethical Hacking And Network Security Dashboard For Ethical Hacking. Use it as a tool for discussion and navigation on Dashboard For Ethical Hacking, Top Priorities Issues, Exposure Time, Problems Discovered, Critical Threat Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Growth Of Ethical Hacking Profession
Ethical Hacking And Network Security Growth Of Ethical Hacking ProfessionThis slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Growth Of Ethical Hacking Profession. Dispense information and present a thorough explanation of Growth Of Ethical Hacking Profession, Computer Forensics Engineer, Ethical Hacker, Network Security Engineer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SS
Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SSThis slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property. Introducing Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Data Privacy, Cybersecurity, Intellectual Property using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Overview Of The Company
Ethical Hacking And Network Security Overview Of The CompanyThis slide describes the overview of the company including the number of countries in which services are provided, total number of certified experts, number of tools and technologies and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Overview Of The Company. This template helps you present information on four stages. You can also present information on Tools And Technologies, Subject Matter Professionals Engaged, Course Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Purpose Of Ethical Hacking
Ethical Hacking And Network Security Purpose Of Ethical HackingThis slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Introducing Ethical Hacking And Network Security Purpose Of Ethical Hacking to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Vulnerabilities To The Authorities, Security Or Protect Systems, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program
Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 ProgramThis slide depicts the reasons to pursue the certified ethical hacking program, including the number of available jobs, the average salary in US dollars, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program. This template helps you present information on three stages. You can also present information on Ethical Hacking Program, Reasons To Pursue, Certified Ethical Hacker, Baseline Certification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Roadmap For Ethical Hacking Program
Ethical Hacking And Network Security Roadmap For Ethical Hacking ProgramThis slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master. Introducing Ethical Hacking And Network Security Roadmap For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap For Ethical Hacking, Ethical Hacking Training Program, Ethical Hacking Master, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker
Ethical Hacking And Network Security Roles And Responsibilities Of Ethical HackerThis slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports, repairing the vulnerabilities of the system, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker. This template helps you present information on five stages. You can also present information on Roles And Responsibilities, Ethical Hacker, Vulnerabilities Of The System, Preventing Future Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks
Ethical Hacking And Network Security Security Measures To Prevent Phishing AttacksThis slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi-factor authentication, and so on. Introducing Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Phishing Attacks, Spam Filter, Updating Security Software Regularly, Utilization Of Multi Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool
Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking ToolThis slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy-to-use user interface, built-in compliance reports, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Solarwinds Security Event, Ethical Hacking Tool, Built In Compliance Reports using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Some Limitations Of Ethical Hacking
Ethical Hacking And Network Security Some Limitations Of Ethical HackingIntroducing Ethical Hacking And Network Security Some Limitations Of Ethical Hacking to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Resource Constraints, Restricted Methods, Ethical Hacking, Computing Power And Funding, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking
Ethical Hacking And Network Security Sql Injection Sqli Technique Of HackingThis slide depicts the SQL injection technique of hacking and how hackers can attack organizations critical information stored in databases through SQL queries. Present the topic in a bit more detail with this Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking. Use it as a tool for discussion and navigation on Injection Technique Of Hacking, Attack Organizations, Sql Injection, Credit Card Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Techniques Used In Ethical Hacking
Ethical Hacking And Network Security Techniques Used In Ethical HackingThis slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Techniques Used In Ethical Hacking. This template helps you present information on six stages. You can also present information on Techniques Of Ethical Hacking, Port Scanning, Sniffing Network Traffic, Patch Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
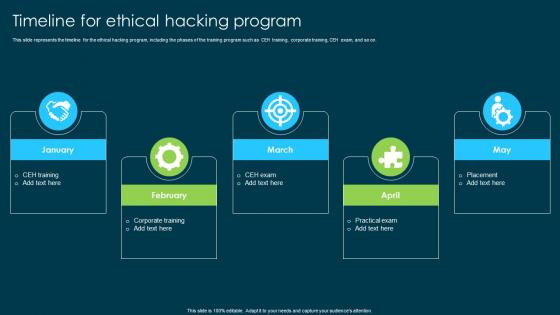 Ethical Hacking And Network Security Timeline For Ethical Hacking Program
Ethical Hacking And Network Security Timeline For Ethical Hacking ProgramThis slide represents the timeline for the ethical hacking program, including the phases of the training program such as CEH training, corporate training, CEH exam, and so on. Introducing Ethical Hacking And Network Security Timeline For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking Program, Training Program, Corporate Training, Placement, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications
Ethical Hacking And Network Security Top Ethical Hacking Courses And CertificationsThis slide depicts the top ethical hacking courses and certifications such as CEH, SANS GPEN, offensive security certified professional, Found stone ultimate hacking, and CREST. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications. Dispense information and present a thorough explanation of Offensive Security Certified Professional, Foundstone Ultimate Hacking, Certified Ethical Hacker using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program
Ethical Hacking And Network Security Traceroute Ng Ethical Hacking ProgramThis slide describes the Traceroute NG ethical hacking program, including its features such as TCP and ICMP network route analysis, txt logfile, IPv4 and IPv6 supported, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program. This template helps you present information on three stages. You can also present information on Network Route Analysis, Enables Precise Evaluation, Analyze Network Paths using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Types Of Ethical Hacking
Ethical Hacking And Network Security Types Of Ethical HackingThis slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Introducing Ethical Hacking And Network Security Types Of Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Hacking Wireless Network, Social Engineering, Web Application Hacking, System Hacking, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Types Of Phishing Attack
Ethical Hacking And Network Security Types Of Phishing AttackThis slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Types Of Phishing Attack. This template helps you present information on three stages. You can also present information on Business Email Compromise, Clone Phishing, Snowshoeing, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Do Ethical Hackers Do
Ethical Hacking And Network Security What Do Ethical Hackers DoThis slide depicts the tasks performed by ethical hackers including scope and goal setting, discovery, exploitation and documentation of the pen-test effort. Present the topic in a bit more detail with this Ethical Hacking And Network Security What Do Ethical Hackers Do. Use it as a tool for discussion and navigation on Ethical Hackers, Scope And Goal Setting, Exploitation And Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security What Is Ethical Hacking
Ethical Hacking And Network Security What Is Ethical HackingThis slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. Introducing Ethical Hacking And Network Security What Is Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Professionals, Security Flaws, Ethical Hacking, Computer System, Application, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas
Ethical Hacking And Network Security What Is Hacking Ppt Icon Format IdeasThis slide illustrates what hacking is and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas. This template helps you present information on five stages. You can also present information on Computer System Or Network, Circumvent Security, Personal Or Corporate Data, Password Cracking Technique using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Is Phishing Attack
Ethical Hacking And Network Security What Is Phishing AttackThis slide represents what phishing attacks are and how phishers hoax people through emails, SMS, phone calls, and social media platforms. Introducing Ethical Hacking And Network Security What Is Phishing Attack to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Phishers Hoax, Social Media Platforms, System Hacking, Corporate Or Personal Data, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Whats New In Cehv11
Ethical Hacking And Network Security Whats New In Cehv11This slide represents the new concepts added to the Certified Ethical Hacking program, including hacking challenges on a higher level, new attack techniques, enumeration, and others. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Whats New In Cehv11. This template helps you present information on eight stages. You can also present information on Operation Technology, Hacking Web Applications, Inverse Engineering Of Malware, Cloud Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security White Hat Or Ethical Hackers
Ethical Hacking And Network Security White Hat Or Ethical HackersThis slide represents the white hat or ethical hackers and how they test the information systems of the organizations with the techniques and methods of black hat hackers. Introducing Ethical Hacking And Network Security White Hat Or Ethical Hackers to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on White Hat Or Ethical Hackers, Malware Scans On Networks, Seek To Penetrate Information Systems, Malware Infections, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers
Ethical Hacking And Network Security Why Organizations Recruit Ethical HackersThis slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers. This template helps you present information on six stages. You can also present information on Organizations Recruit Ethical Hackers, Company Information Systems, Organization Security Posture, Network Protection Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait
Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide PortraitIntroducing our well researched set of slides titled Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Ethical Hacking And Network Security Is Ethical Hacking Legal
Ethical Hacking And Network Security Is Ethical Hacking LegalThis slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Is Ethical Hacking Legal. This template helps you present information on eight stages. You can also present information on Ethical Hacking, Computer Networks, Seek Potential Vulnerabilities, Inflict Unintended Loss using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide
Agenda For Ethical Hacking And Network Security Ppt Icon Master SlideIntroducing Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Network Security, Ethical Hacking Training Program, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Acunetix Ethical Hacking Tool
Ethical Hacking And Network Security Acunetix Ethical Hacking ToolThis slide represents the Acunetix tool used for ethical hacking, including its features such as scalable and fast, on-premise and cloud-based structure, and rapid speed of webpage scans. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Acunetix Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Acunetix Ethical Hacking Tool, Cloud Based Structure, Web Application Security Scanner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Advantages Of Ethical Hacking
Ethical Hacking And Network Security Advantages Of Ethical HackingThis slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance, transition to the cloud, and employment. Introducing Ethical Hacking And Network Security Advantages Of Ethical Hacking to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Unraveling The Hacker Mindset, Development And Quality Assurance, Transition To Cloud, Employment, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Benefits Of Ethical Hacking To Companies
Ethical Hacking And Network Security Benefits Of Ethical Hacking To CompaniesThis slide represents the benefits of ethical hacking to the companies, including testing security, identifying weaknesses, understanding hacker methods, and being ready for a hacker attack. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Benefits Of Ethical Hacking To Companies. This template helps you present information on four stages. You can also present information on Security Measures Testing, Identifying Weaknesses, Ethical Hacking, Understanding Hacker Methods using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Black Hat Hackers Crackers
Ethical Hacking And Network Security Black Hat Hackers CrackersThis slide describes the black hat hackers and how they can take advantage of a vulnerability in a software, network, and computer system. Introducing Ethical Hacking And Network Security Black Hat Hackers Crackers to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Weakness For Illegal Purposes, Black Hat Hackers, Computer System, Network, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Burp Suite Ethical Hacking Tool
Ethical Hacking And Network Security Burp Suite Ethical Hacking ToolThis slide depicts the burp suite ethical hacking tool, including its features such as open-source and custom-built software, easy-to-use login sequence recorder, crawl, and scan automation, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Burp Suite Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Sophisticated Scanning Logic, Crawl And Scan Automation, Custom Built Software, Comprehensive Scanning Capabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Common Types Of Cyber Crime
Ethical Hacking And Network Security Common Types Of Cyber CrimeThis slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Introducing Ethical Hacking And Network Security Common Types Of Cyber Crime to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Electronic Money Laundering, Electronic Funds Transfer, Denial Of Service Attacks, Sharing Copyrighted Files Or Data, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Cookie Theft Technique Of Hacking
Ethical Hacking And Network Security Cookie Theft Technique Of HackingThis slide depicts the cookie theft technique of hacking and how cookies are used to steal user sessions and use their information to perform malicious activities. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Cookie Theft Technique Of Hacking. This template helps you present information on four stages. You can also present information on Technique Of Hacking, Perform Malicious Activities, Customized Website, Session Hijacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking Xss
Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking XssThis slide represents the cross-site scripting technique of hacking, its architecture, and how it works by modifying weak websites through malicious code. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Crosssite Scripting Technique Of Hacking Xss. Dispense information and present a thorough explanation of Cross Site Scripting, Technique Of Hacking, Modifying Weak Websites, Susceptible Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Domain Name System Dns Spoofing
Ethical Hacking And Network Security Domain Name System Dns SpoofingThis slide represents the domain name system spoofing, including its methods such as man in the middle and DNS server compromise and how it is done through altered DNS records. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Domain Name System Dns Spoofing. Dispense information and present a thorough explanation of Domain Name System Spoofing, Server Compromise, Confidential Data, Technique For Gathering Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 1 Reconnaissance
Ethical Hacking And Network Security Ethical Hacking Phase 1 ReconnaissanceThis slide illustrates the reconnaissance phase of ethical hacking and how attackers use the foot printing technique to collect user information before the attack. Introducing Ethical Hacking And Network Security Ethical Hacking Phase 1 Reconnaissance to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Target To Gain Information, Hackers Can Exploit Social Media, Public Websites, Public Resources, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 2 Scanning
Ethical Hacking And Network Security Ethical Hacking Phase 2 ScanningThis slide describes the scanning phase of ethical hacking, and the four types of scans are running in this phase such as pre-attack, port scanning, vulnerability scanning, and data extraction. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Ethical Hacking Phase 2 Scanning. This template helps you present information on five stages. You can also present information on Scanning Phase Of Ethical Hacking, Port Scanning, Vulnerability Scanning, Data Extraction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining Access
Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining AccessThis slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. Introducing Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attack, Brute Force Attack, Spoofing Attack, Dos Attack, Buffer Overflow Attack, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining Access
Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining AccessThis slide represents the maintaining access phase of ethical hacking and how ethical hackers take advantage of it to detect any malicious activities and prevent them. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining Access. This template helps you present information on six stages. You can also present information on Whole Firms Infrastructure, Malicious Activity, Prevent The Systems, Ethical Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 5 Clearing Tracks
Ethical Hacking And Network Security Ethical Hacking Phase 5 Clearing TracksThis slide depicts the clearing tracks phase of ethical hacking and how experienced hackers remove their traces from the system so that no one can follow them. Introducing Ethical Hacking And Network Security Ethical Hacking Phase 5 Clearing Tracks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Delete The Cache And Cookies, Changing Registry Values, Getting Rid Of Sent Emails, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Ethical Hacking Training Options
Ethical Hacking And Network Security Ethical Hacking Training OptionsThis slide represents the ethical hacking training options including online bootcamp and corporate training and their prices options, availability of support and date of the class. Present the topic in a bit more detail with this Ethical Hacking And Network Security Ethical Hacking Training Options. Use it as a tool for discussion and navigation on Ethical Hacking Training Options, Bootcamp And Corporate Training, Learning Management System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Ethical Hacking Vs Penetration Testing
Ethical Hacking And Network Security Ethical Hacking Vs Penetration TestingThis slide depicts a comparison between ethical hacking and penetration testing based on required skills, time is taken to complete paperwork, and so on. Introducing Ethical Hacking And Network Security Ethical Hacking Vs Penetration Testing to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Penetration Testing, Extensive Paperwork, Mandatory Ethical Hacking Certification, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Five Phases Of Ethical Hacking
Ethical Hacking And Network Security Five Phases Of Ethical HackingThis slide represents the five phases of ethical hacking such as reconnaissance, scanning, gaining access, maintaining access, and clearing the track of system hacking. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Five Phases Of Ethical Hacking. This template helps you present information on five stages. You can also present information on Reconnaissance, Scanning, Maintaining Access, Clearing Track using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security For Table Of Contents Ppt Icon Graphics Pictures
Ethical Hacking And Network Security For Table Of Contents Ppt Icon Graphics PicturesIntroducing Ethical Hacking And Network Security For Table Of Contents Ppt Icon Graphics Pictures to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Ethical Hacking, Scanning, Gaining Access, Maintaining Access, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Fundamental Concepts Of Ethical Hacking
Ethical Hacking And Network Security Fundamental Concepts Of Ethical HackingThis slide represents the fundamental concepts of ethical hacking, such as staying legal, defining the scope, reporting vulnerabilities, and respecting data sensitivity. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Fundamental Concepts Of Ethical Hacking. This template helps you present information on four stages. You can also present information on Fundamental Concepts, Ethical Hacking, Staying Legal, Reporting Vulnerabilities, Respecting Data Sensitivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Grey Hat Hackers Ppt Icon Graphics Tutorials
Ethical Hacking And Network Security Grey Hat Hackers Ppt Icon Graphics TutorialsThis slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission. Introducing Ethical Hacking And Network Security Grey Hat Hackers Ppt Icon Graphics Tutorials to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Grey Hat Hackers, Software Or Network, Investigating A Company Systems, Security Vulnerability, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious Hackers
Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious HackersThis slide represents how ethical hackers are different from malicious hackers based on their purpose of hacking for organizational benefit and personal advantage. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security How Are Ethical Hackers Different Than Malicious Hackers. This template helps you present information on two stages. You can also present information on Ethical Hackers, Malicious Hackers, Organizational Benefit, Organizations Security Posture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Importance Of Ethical Hacking
Ethical Hacking And Network Security Importance Of Ethical HackingThis slide shows the importance of ethical hacking and how ethical hackers can help observe the organizational systems from the hackers viewpoint. Introducing Ethical Hacking And Network Security Importance Of Ethical Hacking to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Government Organizations, Sensitive And Essential Data Daily, Terrorist Organizations, Hacking Teams, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Key Vulnerabilities That Ethical Hackers Check
Ethical Hacking And Network Security Key Vulnerabilities That Ethical Hackers CheckThis slide describes the critical vulnerabilities that ethical hackers check, such as injection attacks, modification in security configuration, exposure of critical information, and so on. Introducing Ethical Hacking And Network Security Key Vulnerabilities That Ethical Hackers Check to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Modification In Security Configurations, Exposure Of Critical Information, Authentication Standard Breach, Ethical Hackers Check, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Need For Ethical Hacking
Ethical Hacking And Network Security Need For Ethical HackingThis slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the company security and regulatory compliance. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Need For Ethical Hacking. This template helps you present information on three stages. You can also present information on Identifying And Correcting Security Flaws, Development And Quality Control, Security And Regulatory Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Netsparker Ethical Hacking Tool
Ethical Hacking And Network Security Netsparker Ethical Hacking ToolThis slide depicts the Netsparker tool used for ethical hacking and its features such as less configuration, proof-based scanning, smooth interface, and so on. Introducing Ethical Hacking And Network Security Netsparker Ethical Hacking Tool to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Less Configuration, Proof Based Scanning, Smooth Interface, Simple Online Application, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Overview Of Ethical Hacking Course
Ethical Hacking And Network Security Overview Of Ethical Hacking CourseThis slide represents the overview of the ethical hacking course, including the significant benefits, skills covered and the key features of a certified ethical hacking course. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Overview Of Ethical Hacking Course. Dispense information and present a thorough explanation of Investigation Of Network Packets, Advanced Log Tracking, Principles Of Advanced Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




