Powerpoint Templates and Google slides for Securitize
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Emergency Response Planning
Cyber Security Emergency Response PlanningThis slide represents emergency response planning process for cyber risks including steps such as identify critical assets, assess risks, develop team, etc. Introducing our premium set of slides with Cyber Security Emergency Response Planning. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Critical Assets, Assess Risks, Develop Procedures. So download instantly and tailor it with your information.
-
 Best Practices Of Information Security For Small Businesses
Best Practices Of Information Security For Small BusinessesThis slide highlights information security strategies for small enterprises. The purpose of this slide is to help managers in safeguarding users data from breaches and theft for building their reputation in the market. It includes elements such as employee training, backup, etc. Presenting our set of slides with Best Practices Of Information Security For Small Businesses. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Regular Updates, Network Security
-
 Employee Training Plan For Information Security
Employee Training Plan For Information SecurityThis slide showcases workforce development plan for information security. The purpose of this template is to help businesses in educating employees for protecting information assets. It includes elements such as training type, training days, etc. Introducing our Employee Training Plan For Information Security set of slides. The topics discussed in these slides are Employee Training, Regular Updates, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Future Trends In Managing Information Security
Future Trends In Managing Information SecurityThis slide highlights future advances in information security management. The purpose of this slide is to provide businesses with innovative security strategies for staying competitive in the market. It includes elements such as cloud security, automation, etc.Introducing our premium set of slides with Future Trends In Managing Information Security. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Security, Automation, Privacy Regulations. So download instantly and tailor it with your information.
-
 Icon For Data Loss Prevention In Information Security
Icon For Data Loss Prevention In Information SecurityPresenting our set of slides with Icon For Data Loss Prevention In Information Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon For Data Loss, Prevention In Information Security
-
 Icon For Digital Forensics In Information Security
Icon For Digital Forensics In Information SecurityIntroducing our premium set of slides with Icon For Digital Forensics In Information Security. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Digital, Forensics In Information Security. So download instantly and tailor it with your information.
-
 Icon For Multifactor Authentication In Information Security
Icon For Multifactor Authentication In Information SecurityPresenting our set of slides with Icon For Multifactor Authentication In Information Security. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon For Multifactor, Authentication In Information Security
-
 Impact Of Emerging Technologies On Information Security
Impact Of Emerging Technologies On Information SecurityThis slide highlights influence of technology on information security. The purpose of this slide is to assist IT teams in assessing and measuring various factors for driving success of security initiatives. It includes elements such as zero trust architecture, IoT security, etc.Introducing our Impact Of Emerging Technologies On Information Security set of slides. The topics discussed in these slides are Artificial Intelligence, Zero Trust Architecture, Iot Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Incident Response Plan For Information Security
Incident Response Plan For Information SecurityThis slide highlights emergency response plan to maintain information security. The purpose of this slide is to enable organizations in minimizing damage and reducing the duration of incident. It includes elements such as aspect, responded by, etc. Presenting our well structured Incident Response Plan For Information Security. The topics discussed in this slide are Access Control, Password Policies, Employee Training. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Plan For Healthcare Organization
Information Security Plan For Healthcare OrganizationThis slide highlights strategy for medical organizations information security. The purpose of this template is to help professionals in minimizing business risk and maximize return from business opportunities. It includes elements such as access control, auditing, etc. Introducing our Information Security Plan For Healthcare Organization set of slides. The topics discussed in these slides are Network Security, Auditing, Risk Severity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Principles For Fostering Information Security
Key Principles For Fostering Information SecurityThis slide highlights the fundamentals of data safety. The purpose of this slide is to provide professionals with the guidance on implementing each principle effectively within IT organization. It includes elements such as confidentiality, integrity, etc. Introducing our premium set of slides with Key Principles For Fostering Information Security. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Confidentiality, Availability, Accountability. So download instantly and tailor it with your information.
-
 Methods To Provide Mobile Information Security
Methods To Provide Mobile Information SecurityThis slide showcases practices for ensuring mobile data protection. The purpose of this template is to help users in reducing the risk of data breaches and unauthorized access for their mobile device. It includes elements such as avoid rooting, manage permissions, etc. Presenting our set of slides with Methods To Provide Mobile Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Install Trusted Apps, Manage Permissions, Use VPN For Public WIFI
-
 Physical Measures For Ensuring Security Of Information
Physical Measures For Ensuring Security Of InformationThis slide highlights physical safety precautions for information protection. The purpose of this template is to help IT teams in ensuring the continuity of information systems and data integrity. It includes elements such as alarms, visitor management, etc.Introducing our premium set of slides with Physical Measures For Ensuring Security Of Information. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Surveillance Systems, Alarms, Secure Entry Points. So download instantly and tailor it with your information.
-
 Potential Threats Impacting Information Security
Potential Threats Impacting Information SecurityThis slide highlights possible vulnerabilities to data security. The purpose of this template is to help businesses in overcoming various challenges in protecting data for creating a safer environment. It includes elements such as malware, phishing, data breaches, etc. Introducing our Potential Threats Impacting Information Security set of slides. The topics discussed in these slides are General Data Protection, Health Insurance Portability, Security Management Act FISMA. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Regulatory Considerations For Managing Information Security
Regulatory Considerations For Managing Information SecurityThis slide highlights compliance aspects for safeguarding data security. The purpose of this template is to assist businesses in adhering to relevant laws and industry standards for building users trust and image in digital world. It includes elements such as GDPR, HIPAA, etc. Introducing our premium set of slides with Regulatory Considerations For Managing Information Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection, Predictive Analysis, Phishing Detection. So download instantly and tailor it with your information.
-
 Role Of Artificial Intelligence In Information Security
Role Of Artificial Intelligence In Information SecurityThis slide highlights the significance of AI in data security. The purpose of this template is to help organizations in enhancing their capacity for overcoming evolving threats and automating security tasks. It includes elements such as threat detection, automated response, etc. Presenting our set of slides with Role Of Artificial Intelligence In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Security, Network Segmentation, Security Audits
-
 Strategies To Ensure Information Security From Ransomware Attacks
Strategies To Ensure Information Security From Ransomware AttacksThis slide highlights techniques for securing information against ransomware attacks. The purpose of this slide is to assist professionals in ensuring business continuity and minimizing downtime. It includes elements such as email security, patch updates, network segmentation, etc. Introducing our premium set of slides with Strategies To Ensure Information Security From Ransomware Attacks. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Data Encryption, Awareness. So download instantly and tailor it with your information.
-
 Tactics For Information Privacy And Security
Tactics For Information Privacy And SecurityThis slide showcases methods for ensuring information security and confidentiality. The purpose of this slide is to aid IT teams in enhancing the organizations ability to protect sensitive information. It includes elements such as access control, data encryption, etc. Introducing our premium set of slides with Tactics For Information Privacy And Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strong Password Policies, Test Data Restoration Procedures. So download instantly and tailor it with your information.
-
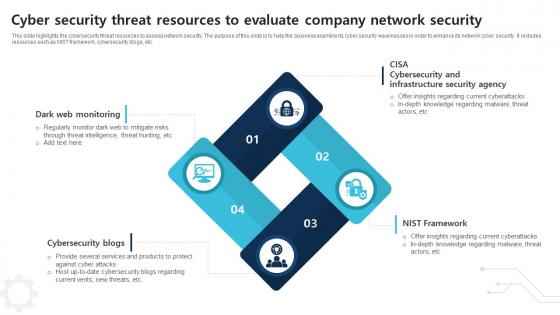 Cyber Security Threat Resources To Evaluate Company Network Security
Cyber Security Threat Resources To Evaluate Company Network SecurityThis slide highlights the cybersecurity threat resources to assess network security. The purpose of this slide is to help the business examine its cyber security weaknesses in order to enhance its network cyber security. It includes resources such as NIST framework, cybersecurity blogs, etc. Introducing our premium set of slides with Cyber Security Threat Resources To Evaluate Company Network Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Dark Web Monitoring, Cybersecurity Blogs, Nist Framework So download instantly and tailor it with your information.
-
 Comparison Between Preventive And Detective Controls In Cyber Security
Comparison Between Preventive And Detective Controls In Cyber SecurityThis slide represents the comparison between preventative controls and detective controls in cyber security to prevent potential threats and secure data. It includes preventative controls and detective controls Presenting our set of slides with Comparison Between Preventive And Detective Controls In Cyber Security This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preventative Control, Detective Control
-
 Cyber Security Attack Control Icon
Cyber Security Attack Control IconIntroducing our premium set of slides with Cyber Security Attack Control Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Attack Control Icon So download instantly and tailor it with your information.
-
 Cyber Security Controls Checklist For Business
Cyber Security Controls Checklist For BusinessThis slide highlights the checklist for cyber security controls to prevent business from cyber attacks and protect company confidential data. It includes various KPIs such as password management, privacy and security of sensitive data. Presenting our well structured Cyber Security Controls Checklist For Business The topics discussed in this slide are Password Management, Security Awareness This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Controls Software Comparative Analysis
Cyber Security Controls Software Comparative AnalysisThis slide highlights the comparative analysis of cyber security control software to protect confidential data and protection from data breach. It includes various factors such as features, ratings, etc Introducing our Cyber Security Controls Software Comparative Analysis set of slides. The topics discussed in these slides are Secpod Sanernow, Intruder, Solar Winds Security Event Manager This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Online Threat Control Icon
Cyber Security Online Threat Control IconPresenting our set of slides with Cyber Security Online Threat Control Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Online Threat Control Icon
-
 NIST Cyber Security Control Framework For Business
NIST Cyber Security Control Framework For BusinessThis slide represents cyber security control NIST framework to help business in identifying potential threats of attacks or data breach. It includes various steps such as identify, protect, detect, respond and recover. Introducing our premium set of slides with NIST Cyber Security Control Framework For Business Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Protect, Detect So download instantly and tailor it with your information.
-
 Process To Determine Adequate Cyber Security Control
Process To Determine Adequate Cyber Security ControlThis slide represents the process to identifying adequate cyber security control for business to prevent online threats and implement necessary steps. It includes various steps such as evaluate size of the company, identify scope of IT infrastructure, etc. Presenting our set of slides with Process To Determine Adequate Cyber Security Control This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Scope Of It Infrastructure, Evaluate Size Of Company, Investment In Cyber Security
-
 Types Of Detective Controls Cyber Security
Types Of Detective Controls Cyber SecurityThis slide represents the types of detective controls used in cyber security to prevent data breach by unauthorized access or online attack. It includes various steps such as log monitoring, SIEM, trend analysis, etc. Introducing our premium set of slides with Types Of Detective Controls Cyber Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trend Analysis, Security Audits, Log Monitoring So download instantly and tailor it with your information.
-
 Types Of Preventative Controls In Cyber Security
Types Of Preventative Controls In Cyber SecurityThis slide represents the different type of preventative controls in cyber security to prevent leakage of confidential data by unauthorized access. It includes various steps such as hardening, security awareness training, change management, etc. Presenting our set of slides with Types Of Preventative Controls In Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Awareness Training, Hardening, Change Management
-
 Types Of Technical Controls In Cyber Security
Types Of Technical Controls In Cyber SecurityThis slide represents the various types of technical control in cyber security to monitor and track potential threats and prevent data breach. It includes various types such as encryptions, firewalls, antivirus software, etc. Introducing our premium set of slides with Types Of Technical Controls In Cyber Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryptions, Firewalls, Antivirus Software So download instantly and tailor it with your information.
-
 Various Types Of Cyber Security Controls
Various Types Of Cyber Security ControlsThis slide represents different types of cyber security controls to prevent from online threats and protect sensitive data. It includes various cyber security controls such as technical controls, preventative controls, detective controls, corrective controls, etc. Presenting our set of slides with Various Types Of Cyber Security Controls This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technical Controls, Preventative Controls, Detective Controls
-
 Features Of Web Related Security Solutions
Features Of Web Related Security SolutionsThis slide covers essential characteristics of web security solutions. The purpose of this slide is to help businesses in providing comprehensive protection to users against web application related cyber threats. It covers various features such as URL filtering, application control, data loss prevention and SSL introspection. Presenting our well structured Features Of Web Related Security Solutions The topics discussed in this slide are URL Filtering, Application Control, Data Loss Prevention This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Impact Of Web Security On Business Operations
Impact Of Web Security On Business OperationsThis template presents benefits and impact of ensuring web security. The purpose of this slide is to minimize organizational security risks by detecting and preventing cyber threats. It covers functional impact and various benefits such as improvement of security posture, protecting IT infrastructure, enhancement of security training programs, etc. Introducing our Impact Of Web Security On Business Operations set of slides. The topics discussed in these slides are Monitors Data Flow Security, Protects IT Infrastructure, Improves Security Posture This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Internal Architecture Of Web Services Security
Internal Architecture Of Web Services SecurityThis slide lays out framework for web services security. The purpose of this slide is to help businesses in modeling security agents regarding authentication and authorization provided by web container. It covers components such as token service, provider plugin, client interface, etc. Presenting our well structured Internal Architecture Of Web Services Security The topics discussed in this slide are Provider Plugin, Web Security Service Client, Web Security Service Provider This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Solutions To Overcome Website Security Audit Challenges
Solutions To Overcome Website Security Audit ChallengesThis template showcases solutions and technological stack to overcome challenges faced by organizations while conducting website security audit. The purpose of this slide is to help organizations streamline auditing process for maintaining data authenticity. It covers tools and strategies to reduce web security risks such as injections, broken authentication, and data exposure. Introducing our Solutions To Overcome Website Security Audit Challenges set of slides. The topics discussed in these slides are Challenges, Solutions This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Conduct Website Security Audit
Steps To Conduct Website Security AuditThis slide showcases website security audit process. The purpose of this slide is to ensure website safety by conducting deep analysis of server setups, application software and network configurations. It covers steps such as scoping, vulnerability assessment, penetration testing, risk assessment, remediation and monitoring. Presenting our set of slides with Steps To Conduct Website Security Audit This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scoping, Penetration Testing, Remediation
-
 Techniques To Achieve Web Application Security
Techniques To Achieve Web Application SecurityThis slide showcases approaches to ensure web application security. The purpose of this slide is to help businesses in protecting their data against cyber attacks. It covers techniques such as utilizing heuristic detection, implementing cybersecurity framework, adopting secure software development practices, etc. Introducing our premium set of slides with Techniques To Achieve Web Application Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Utilize Heuristic Detection, Implement Cybersecurity Framework, Security Measures So download instantly and tailor it with your information.
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Web Application Firewall Icon For Application Security
Web Application Firewall Icon For Application SecurityPresenting our well structured Web Application Firewall Icon For Application Security The topics discussed in this slide are Web Application Firewall Icon, Application Security This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Web Application Security Checklist Icon
Web Application Security Checklist IconIntroducing our premium set of slides with Web Application Security Checklist Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Application Security Checklist Icon So download instantly and tailor it with your information.
-
 Web Security Audit Controls To Reduce Threats
Web Security Audit Controls To Reduce ThreatsThis slide represents various security control methods to minimize threats to web security. The purpose of this slide is to help businesses in developing strategy for data protection. It provides techniques to minimize web security threats such as SQL injection, ransomware, denial of service attacks and phishing. Introducing our Web Security Audit Controls To Reduce Threats set of slides. The topics discussed in these slides are Ransomware, Service Attacks, Phishing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Web Security Icon To Prevent Cyber Attacks
Web Security Icon To Prevent Cyber AttacksPresenting our set of slides with Web Security Icon To Prevent Cyber Attacks This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Security Icon, Prevent Cyber Attacks
-
 Web Security Principles For Software Development Companies
Web Security Principles For Software Development CompaniesThis template covers four principles of web security followed by well established software development businesses. The purpose of this slide is to streamline business operations by preventing hackers from data manipulation. It includes principles such as authentication, confidentiality, integrity and availability. Introducing our premium set of slides with Web Security Principles For Software Development Companies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Confidentiality, Authentication, Integrity So download instantly and tailor it with your information.
-
 Web Security Solutions For SQL Injection Attacks
Web Security Solutions For SQL Injection AttacksThis template presents solutions to tackle web security issue of SQL injection attacks. The purpose of this slide is to help businesses in managing and securing information stored in SQL database. It covers illustration of SQL injection attack and its web security solutions such as restricting searches, setting legitimate format, performing data validation, etc. Introducing our Web Security Solutions For SQL Injection Attacks set of slides. The topics discussed in these slides are Creates Profile, Web Server, Processes Malicious Commands This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Web Security Solutions To Prevent Misconfiguration Related Issues
Web Security Solutions To Prevent Misconfiguration Related IssuesThis slide covers solutions to prevent issues related with website configuration. The purpose of this slide is to help organizations in securing their networks and web applications safe from cyberthreats. It covers solutions such as verifying security procedures, updating software and hardware policies, conducting regular audits, etc. Presenting our well structured Web Security Solutions To Prevent Misconfiguration Related Issues The topics discussed in this slide are Verify Security Procedures, Conduct Regular Audits, Change Login Information This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Web Security Solutions To Prevent XSS Attacks
Web Security Solutions To Prevent XSS AttacksThis template presents various tips to minimize cross site scripting attacks. The purpose of this slide is to help businesses in preventing malicious executions and patching vulnerabilities. It covers web security solutions such as checking client side inputs, using firewall configurations, utilizing content security policy an updating software. Presenting our set of slides with Web Security Solutions To Prevent XSS Attacks This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Client Side Inputs, Firewall Configuration, Content Security Policy
-
 Web Security Vulnerabilities And Their Prevention Strategies
Web Security Vulnerabilities And Their Prevention StrategiesThis slide covers common web security pitfalls and their mitigation strategies. The purpose of this slide is to help businesses in minimizing web related IT security pitfalls. It covers various prevention strategies to address web security vulnerabilities such as injection flaws, broken authentication, cross site scripting and security misconfiguration. Introducing our premium set of slides with Web Security Vulnerabilities And Their Prevention Strategies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Injection Flaws, Broken Authentication, Cross Site Scripting So download instantly and tailor it with your information.
-
 Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SS
Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SSIntroducing Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Worldwide, Implementing Strategies, Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS
Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of authentication and access control for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about trust boundaries, identity authentication, etc. Increase audience engagement and knowledge by dispensing information using Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Trust Boundaries, Identity Authentication, Access Protection Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SS
Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SSPresent the topic in a bit more detail with this Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Management, Service Organization, Communication, Cyber Security Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SS
Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SSThis slide showcases comparative analysis for internet of things IoT security tools. It provides details about secure cryptographic key provisioning, identity, access and relationship management, IoT device provisioning, etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Comparative Analysis, IoT Security Software, IoT Device Provisioning, Secure Cryptographic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS
Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases comparative analysis for internet of things IoT security tools. It provides details about secure cryptographic key provisioning, identity, access and relationship management, IoT device provisioning, etc. Introducing Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Secure Deployment, Cryptographic Protocols, Automated Security Update Deployment, Monitoring And Response Mechanisms, using this template. Grab it now to reap its full benefits.
-
 Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS
Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security challenges faced by businesses. It provides details about IoT malware and ransomware, user privacy risks, insecure interfaces, remove work environments, etc. Deliver an outstanding presentation on the topic using this Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Security Business Challenges, Internet Of Things, IoT Malware And Ransomware, User Privacy Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SS
Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SSThis slide showcases cybersecurity team hierarchy chart specific for internet of things IoT operations. It provides details about CEO, CISO, director, manager, security engineer, etc. Present the topic in a bit more detail with this Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cybersecurity Team, Organizational Chart, Security Engineer, Hierarchy Chart. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SS
Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SSPresenting our well crafted Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Internet Of Things IoT Security For Table Of Contents Cybersecurity SS
Internet Of Things IoT Security For Table Of Contents Cybersecurity SSIntroducing Internet Of Things IoT Security For Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Business Success, IoT Security, Market Size Analysis, Overview With Key Benefits, using this template. Grab it now to reap its full benefits.
-
 IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Secure Communications, Secure Cloud, Secure Device, Messaging Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS
IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT device identity platform deployment, referable for businesses in developing mitigation process. It provides details about APIs, architecture, device client, etc. Deliver an outstanding presentation on the topic using this IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Device, Platform Deployment, Developing Mitigation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SS
IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security gap analysis for organization, referable for related businesses wanting to improve operations. It provides details about single factor authentication, data in transit, incident response, etc. Deliver an outstanding presentation on the topic using this IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Comprehensive Security Training, Upgrade Encryption Protocols, Gap Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS
IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security introduction with its major benefits, referable for companies dealing with related vulnerabilities. It provides details about security protocols, device protection, encryption, etc. Increase audience engagement and knowledge by dispensing information using IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Protection Of Devices, Encryption Of Networks, Secured Data Handling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





