Powerpoint Templates and Google slides for Securitize
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Firewall As A Service Fwaas Working And Security Features
Sase Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Deliver an outstanding presentation on the topic using this Sase Model Firewall As A Service Fwaas Working And Security Features. Dispense information and present a thorough explanation of Cloud Database, Email Cloud using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Pillars Of Cloud Access Security Broker
Sase Model Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using Sase Model Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Traditional Networking Security Problems And Sase Solutions
Sase Model Traditional Networking Security Problems And Sase SolutionsThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Present the topic in a bit more detail with this Sase Model Traditional Networking Security Problems And Sase Solutions. Use it as a tool for discussion and navigation on Traditional Networking Models. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Parameters, Comments, Comply Safe Communication Protocols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining Key Security Objectives Securing Blockchain Transactions A Beginners Guide BCT SS V
Defining Key Security Objectives Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Defining Key Security Objectives Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication, using this template. Grab it now to reap its full benefits.
-
 Committee National Security Systems In Powerpoint And Google Slides Cpb
Committee National Security Systems In Powerpoint And Google Slides CpbPresenting Committee National Security Systems In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Committee National Security Systems. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V
Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Database Marketing Practices To Increase MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Continuity And Disaster Recovery Plan For Information Security
Business Continuity And Disaster Recovery Plan For Information SecurityThis slide represents the disaster recovery and business continuity plan that help companies to resolve information security issues effectively. It includes various threats such as injection, broken authentication, etc. Introducing our Business Continuity And Disaster Recovery Plan For Information Security set of slides. The topics discussed in these slides are Injection, Authentication, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Disaster Recovery Icon For Business Continuity
Information Security Disaster Recovery Icon For Business ContinuityIntroducing our premium set of slides with Information Security Disaster Recovery Icon For Business Continuity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Recovery, Continuity. So download instantly and tailor it with your information.
-
 Security Computing Device Network Icon
Security Computing Device Network IconPresenting our set of slides with Security Computing Device Network Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Device, Security.
-
 Network Security Threats And Optimization Techniques
Network Security Threats And Optimization TechniquesThis slide presents optimization strategies to prevent network security attacks. The purpose of this slide is to help businesses in securing their digital infrastructure against security threats through these optimization techniques. It covers solutions to prevent threats such as malware, phishing, DDoS and social engineering attacks. Introducing our premium set of slides with Network Security Threats And Optimization Techniques. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure, Software, Employees. So download instantly and tailor it with your information.
-
 Teams Security Issues In Powerpoint And Google Slides Cpb
Teams Security Issues In Powerpoint And Google Slides CpbPresenting our Teams Security Issues In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases nine stages. It is useful to share insightful information on Teams Security Issues This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Securities Lending Business In Powerpoint And Google Slides Cpb
Securities Lending Business In Powerpoint And Google Slides CpbPresenting our Securities Lending Business In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Securities Lending Business This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Wireless Indoor Security Business In Powerpoint And Google Slides Cpb
Wireless Indoor Security Business In Powerpoint And Google Slides CpbPresenting Wireless Indoor Security Business In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Wireless Indoor Security Business. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Socioeconomic Status Financial Security In Powerpoint And Google Slides Cpb
Socioeconomic Status Financial Security In Powerpoint And Google Slides CpbPresenting Socioeconomic Status Financial Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Socioeconomic Status Financial Security This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Internship In Powerpoint And Google Slides Cpb
Cyber Security Internship In Powerpoint And Google Slides CpbPresenting our Cyber Security Internship In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Internship This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security
Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP SecurityThis slide represents the important attributes to contemplate DSP security. The purpose of this slide is to highlight the factors of DSPO security such as data encryption, Access control, secure communication, etc. Increase audience engagement and knowledge by dispensing information using Digital Signal Processing In Modern Important Factors To Contemplate Regarding DSP Security. This template helps you present information on twelve stages. You can also present information on Firmware Security, Physical Security, Secure Communication, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing Solve
Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing SolveThis slide showcases the solution to major security aspects of Digital Signal Processing in modern communication systems. The purpose of this slide is to highlight the security aspects such as encryption and data security, audio and speech authentication, biometric security, etc. Introducing Digital Signal Processing In Modern Major Security Aspects Digital Signal Processing Solve to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Audio And Speech Authentication, Biometric Security, Encryption And Data Security, Network Security And Intrusion Detection, using this template. Grab it now to reap its full benefits.
-
 Security And Trustworthiness Ppt Portrait Huawei Company Profile CP SS
Security And Trustworthiness Ppt Portrait Huawei Company Profile CP SSThis slide showcases sustainability strategy of Huawei company and its progress towards its goals to reduce its impact on environment. It outlines its progress towards security and trustworthiness. Introducing Security And Trustworthiness Ppt Portrait Huawei Company Profile CP SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Acknowledged, Corporate, Communications, using this template. Grab it now to reap its full benefits.
-
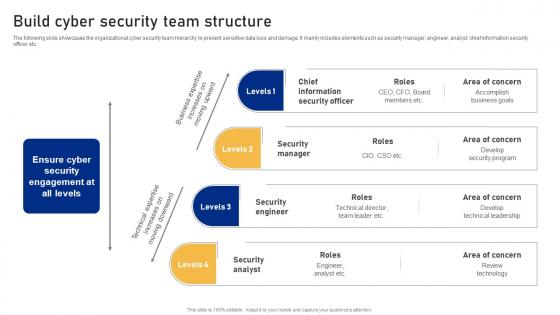 Build Cyber Security Team Structure Cyber Risk Assessment
Build Cyber Security Team Structure Cyber Risk AssessmentThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Increase audience engagement and knowledge by dispensing information using Build Cyber Security Team Structure Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Information Security Officer, Security Manager, Security Engineer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Facts And Statistics Cyber Risk Assessment
Cyber Security Awareness Facts And Statistics Cyber Risk AssessmentThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Facts And Statistics Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Malware Attacks, Company, Social Engineering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment
Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk AssessmentThe following slide depicts some figures to analyze the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Highlighting, Cyber Security Unawareness using this template. Grab it now to reap its full benefits.
-
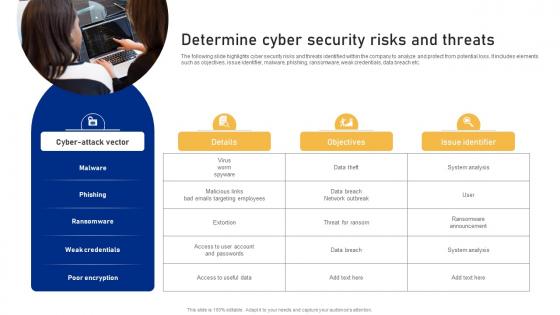 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Cyber Security Trend Analysis Cyber Risk Assessment
Global Cyber Security Trend Analysis Cyber Risk AssessmentThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Deliver an outstanding presentation on the topic using this Global Cyber Security Trend Analysis Cyber Risk Assessment Dispense information and present a thorough explanation of Global Cyber Security, Trend Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
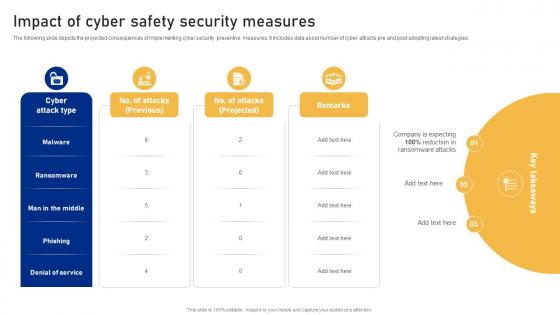 Impact Of Cyber Safety Security Measures Cyber Risk Assessment
Impact Of Cyber Safety Security Measures Cyber Risk AssessmentThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack, Ransomware, Projected This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Cyber Risk Assessment
Impact Of Cyber Security Policies And Practices Cyber Risk AssessmentThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Introducing Impact Of Cyber Security Policies And Practices Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Guidelines, Management, Privacy Policies using this template. Grab it now to reap its full benefits.
-
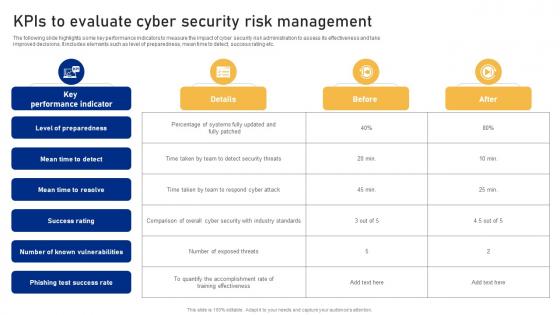 KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment
KPIS To Evaluate Cyber Security Risk Management Cyber Risk AssessmentThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment Use it as a tool for discussion and navigation on Performance Indicator, Success Rating, Risk Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment
Organize Cyber Security Training For Employees Regularly Cyber Risk AssessmentThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment Use it as a tool for discussion and navigation on Document Management, Passwords, Social Media Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment
Prioritize Cyber Security Risk With Severity Matrix Cyber Risk AssessmentThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment Use it as a tool for discussion and navigation on Prioritize, Cyber Security Risk, Severity Matrix This template is free to edit as deemed fit for your organization. Therefore download it now.
-
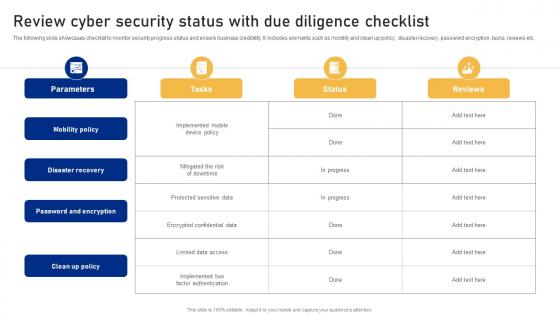 Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment
Review Cyber Security Status With Due Diligence Checklist Cyber Risk AssessmentThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment Use it as a tool for discussion and navigation on Mobility Policy, Disaster Recovery, Password And Encryption This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment
Select Tools To Reduce Cyber Security Failure Cyber Risk AssessmentThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Introducing Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities, Select Tools, Cyber Security Failure using this template. Grab it now to reap its full benefits.
-
 Orient Securities Company Limited In Powerpoint And Google Slides Cpb
Orient Securities Company Limited In Powerpoint And Google Slides CpbPresenting Orient Securities Company Limited In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Orient Securities Company Limited. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It
About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role and functionality of IPsec Internet Protocol Security in securing connections between devices. This slide also outlines the uses of IPsec such as protecting data during transmission over open networks, use in building VPNs, etc. Deliver an outstanding presentation on the topic using this About Internet Protocol Security Overview And Uses Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Overview, Protocol Security, Destination using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Corporation In Powerpoint And Google Slides Cpb
Information Security Corporation In Powerpoint And Google Slides CpbPresenting Information Security Corporation In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Corporation. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Benefits Of Virtual Desktop Infrastructure Security Architecture
Benefits Of Virtual Desktop Infrastructure Security ArchitectureThis slide highlights the virtual desktop infrastructure security architecture. The purpose of this slide is to help improve the business through installation of virtual desktop security architecture. It includes benefits such as unified management platform, real time compliance monitoring, etc.. Presenting our set of slides with Benefits Of Virtual Desktop Infrastructure Security Architecture. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Scanning, Prevention.
-
 Artificial Intelligence Based Voice Cloning In Cyber Security
Artificial Intelligence Based Voice Cloning In Cyber SecurityThis slide shows the process of AI ML based voice cloning and awareness suggestions to prevent these digital cyber crimes. It covers steps of voice cloning cyber crime such as recording analysis, speech recognition, waveform production, deceptive phone calls, etc. Presenting our set of slides with name Artificial Intelligence Based Voice Cloning In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Speech Recognition, Waveform Production, Deceptive Phone Calls.
-
 Card Cloning Fraud In Cyber Security
Card Cloning Fraud In Cyber SecurityThis slide shows technical working of card cloning and strategies to minimize these frauds. It covers four stages of credit card cloning that are skimmer installation, data capturing, information retrieval and illicit use of stolen card information. Introducing our premium set of slides with name Card Cloning Fraud In Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Skimmer Installation, Data Capture, Information Retrieval. So download instantly and tailor it with your information.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Cyber Security Icon Protecting Card Cloning Fraud
Cyber Security Icon Protecting Card Cloning FraudIntroducing our premium set of slides with name Cyber Security Icon Protecting Card Cloning Fraud. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Icon Protecting, Card Cloning Fraud. So download instantly and tailor it with your information.
-
 Disk Cloning Icon In Cyber Security
Disk Cloning Icon In Cyber SecurityPresenting our set of slides with name Disk Cloning Icon In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Disk Cloning, Icon In Cyber Security.
-
 Disk Cloning Software For Cyber Security
Disk Cloning Software For Cyber SecurityThis slide shows features, benefits and use cases of hard disk cloning software. The purpose of this slide is to optimize the technical process of reinstallation and reconfiguration of computers operating system. Introducing our Disk Cloning Software For Cyber Security set of slides. The topics discussed in these slides are Data Migration, Drive Recovery, Drive Recovery. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 MAC Cloning Attack In Cyber Security
MAC Cloning Attack In Cyber SecurityThis slide shows working and mitigating mechanism for MAC cloning attacks. It covers basic steps of MAC spoofing and effective strategies for its prevention that are MAC address filtering, implementing network control solutions, adopting intrusion detection and prevention systems. Presenting our well structured MAC Cloning Attack In Cyber Security. The topics discussed in this slide are Network Traffic, Traffic Signals, Confidential Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mitigating Cloning Risks In Cyber Security
Mitigating Cloning Risks In Cyber SecurityThis slide shows strategies to counter cloning attacks. The purpose of this slide is to help cybersecurity experts in identifying and preventing cybersecurity threats. It covers mitigating measures such as security awareness training, email credentials security, link authentication, etc. Introducing our premium set of slides with name Mitigating Cloning Risks In Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Awareness, Link Authentication, Security Solutions. So download instantly and tailor it with your information.
-
 Mobile Phone Cloning In Cyber Security
Mobile Phone Cloning In Cyber SecurityThis slide shows various tips to recognize mobile phone cloning and strategies to ensure protection against information and monetary losses. It covers awareness tips such as checking for viruses, creating strong passwords, etc. Presenting our set of slides with name Mobile Phone Cloning In Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ensure Protection, Phone Cloning, Check Viruses.
-
 Prevention Strategies For Website Cloning To Ensure Cyber Security
Prevention Strategies For Website Cloning To Ensure Cyber SecurityThis slide shows various ways to ensure protection against website cloning. It covers tips to recognize clone websites and strategies to prevent website cloning to achieve cyber security. Introducing our premium set of slides with name Prevention Strategies For Website Cloning To Ensure Cyber Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevention Strategies, Grammatical Errors, Clone Websites. So download instantly and tailor it with your information.
-
 Response Plan To Cloning Attacks In Cyber Security
Response Plan To Cloning Attacks In Cyber SecurityThis slide shows an incident response and recovery plan for cloning attacks. The purpose of this slide is to ensure cybersecurity for safeguarding business assets and customers trust. It covers four essential responses such as identification of threat, isolating affected systems, recovery, etc. Presenting our set of slides with name Response Plan To Cloning Attacks In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloning Attack, Malicious Elements, Security Measures.
-
 Types And Techniques Of Cloning Risks In Cyber Security
Types And Techniques Of Cloning Risks In Cyber SecurityThis slide covers different types of cloning and techniques that provides attackers an unauthorized access to confidential data. It covers three types of cloning such as device, software and identity cloning. Introducing our Types And Techniques Of Cloning Risks In Cyber Security set of slides. The topics discussed in these slides are Device Cloning, Software Cloning, Identity Cloning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Navigating The Banking Industry Banking Industry Framework For Economic Financial Security
Navigating The Banking Industry Banking Industry Framework For Economic Financial SecurityThis slide showcases conceptualisation of bank operations. This template focuses on providing an easy way for people to pay for goods and services and save their money. It includes information related to customer relationship management, etc. Present the topic in a bit more detail with this Navigating The Banking Industry Banking Industry Framework For Economic Financial Security. Use it as a tool for discussion and navigation on Contact Management, Customer Risk, Customer Relationship Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Architecture Document In Powerpoint And Google Slides Cpb
Security Architecture Document In Powerpoint And Google Slides CpbPresenting our Security Architecture Document In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases eight stages. It is useful to share insightful information on Security Architecture Document. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Money Market Securities Characteristics In Powerpoint And Google Slides Cpb
Money Market Securities Characteristics In Powerpoint And Google Slides CpbPresenting Money Market Securities Characteristics In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Money Market Securities Characteristics. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Municipal Securities Examples In Powerpoint And Google Slides Cpb
Municipal Securities Examples In Powerpoint And Google Slides CpbPresenting our Municipal Securities Examples In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Municipal Securities Examples This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Loan Backed Security In Powerpoint And Google Slides Cpb
Loan Backed Security In Powerpoint And Google Slides CpbPresenting Loan Backed Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Loan Backed Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It
Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Internet protocol Security IPsec technology. The various benefits explained in this slide are strong security, broad compatibility, flexibility, scalability and efficient network performance. Deliver an outstanding presentation on the topic using this Benefits Of Internet Protocol Security Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Key Management, Performance Impact, Compatibility Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It
Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various features of Internet Protocol Security IPsec mechanism. The properties of IPsec include authentication, privacy, integrity, key management, tunnelling, flexibility and interoperability. Introducing Characteristics Of Internet Protocol Security Technique Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Key Management, Interoperability, using this template. Grab it now to reap its full benefits.
-
 Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It
Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age ItThis slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Introducing Emerging Trends In Cryptographic Cloud Security Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Quantum Safe Cryptography, Secure Multi Party Computation, using this template. Grab it now to reap its full benefits.
-
 Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It
Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age ItThis slide discusses about the increasing adoption of encryption to solve current cyber security issues. The key points discussed are more use of cloud encryption in banking sector, introduction of homomorphic encryption, increase in BYOE adoption, etc. Increase audience engagement and knowledge by dispensing information using Encryption Adaptability To Tackle Recent Security Challenges Encryption For Data Privacy In Digital Age It. This template helps you present information on five stages. You can also present information on Homomorphic, Encryption, Introduction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It
Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. Introducing Factors Responsible For Cloud Security Failures Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Poor Key Management, Software Engineers, using this template. Grab it now to reap its full benefits.





