Powerpoint Templates and Google slides for Securing Network
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Firewall Network Security Firewall Network Security Awareness Training Schedule
Firewall Network Security Firewall Network Security Awareness Training ScheduleThis slide describes the training program for firewall network security awareness. The purpose of this slide is to highlight the training schedule for firewall security awareness, and the main components include agenda, system requirements, mode and cost of the training. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Network Security Awareness Training Schedule This template helps you present information on Four stages. You can also present information on Firewall Network Security Firewall Network Security Awareness Training Schedule using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Firewall Security Management Overview And Importance
Firewall Network Security Firewall Security Management Overview And ImportanceThis slide outlines the overview of firewall management in an organization and its significance. The purpose of this slide is to give an overview of firewall management and its importance, such as protecting against data breaches, enhancing network security, and so on. Introducing Firewall Network Security Firewall Security Management Overview And Importance to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Service Control, Direction Control, User Control using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Firewall Security Management Software Tools
Firewall Network Security Firewall Security Management Software ToolsThis slide highlights the top software solutions for firewall security management. The purpose of this slide is to showcase the different software tools for firewall security management, including their features and providers, such as Cisco Systems, Palo Alto Networks, Check Point, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Firewall Security Management Software Tools Dispense information and present a thorough explanation of General Features, Host-Level Features using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security
Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client SecurityThis slide outlines the many ways to control access and guarantee web client security policy. The purpose of this slide is to highlight the firewall techniques to limit user access and confirm web user security, such as service control, direction control, user control and behavior control. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security This template helps you present information on Four stages. You can also present information on Market By Deployment, Market By Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Generic And Host Level Features Of Software Firewall
Firewall Network Security Generic And Host Level Features Of Software FirewallThis slide outlines the general and host-level characteristics of software firewalls. The purpose of this slide is to showcase the different features of software firewalls, including small footprint, security, low costs, granular application-level access, integration with EDR, and device security. Present the topic in a bit more detail with this Firewall Network Security Generic And Host Level Features Of Software Firewall Use it as a tool for discussion and navigation on Oragnisation Size Segment Overview, Regional Analysis This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Hardware Firewall Overview And Benefits
Firewall Network Security Hardware Firewall Overview And BenefitsThis slide gives an overview of the hardware firewall along with its advantages. The purpose of this slide is to showcase the hardware firewall introduction and different benefits, such as consistent security, standalone protection, simplified management, improved security, and centralized visibility. Deliver an outstanding presentation on the topic using this Firewall Network Security Hardware Firewall Overview And Benefits Dispense information and present a thorough explanation of Untrusted Networks, Traditional Firewalls, Hardware Firewall using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security How Circuit Level Gateway Firewalls Work
Firewall Network Security How Circuit Level Gateway Firewalls WorkThis slide describes the working process of circuit-level gateways through the workflow. The purpose of this slide is to showcase how circuit-level gateway firewalls work with the help of a workflow diagram and explaining step by step procedures. Present the topic in a bit more detail with this Firewall Network Security How Circuit Level Gateway Firewalls Work Use it as a tool for discussion and navigation on Data Traffic, Web Application, Web Server This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security How Does A Hardware Firewall Works
Firewall Network Security How Does A Hardware Firewall WorksThis slide provides an overview of the working of hardware firewalls. The purpose of this slide is to showcase the various steps a hardware firewall takes to protect a network and devices from malicious activities. The components of a network containing hardware firewall include LAN, hardware firewall, and internet. Deliver an outstanding presentation on the topic using this Firewall Network Security How Does A Hardware Firewall Works Dispense information and present a thorough explanation of Security From Insider Attacks, Intrusion Detection, Service Exposure And Port Scanning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security How Does Web Application Firewall Works
Firewall Network Security How Does Web Application Firewall WorksThis slide depicts the working process of the Web Application Firewall and how it analysis the web traffic and detects harmful traffic. The purpose of this slide is to showcase the working of WAF and how it prevents malicious traffic from reaching web application servers. Present the topic in a bit more detail with this Firewall Network Security How Does Web Application Firewall Works Use it as a tool for discussion and navigation on Importance, Functions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Importance And Benefits Of Distributed Firewall Management System
Firewall Network Security Importance And Benefits Of Distributed Firewall Management SystemThis slide outlines the importance of distributed firewall management system. It also includes the various advantages of distributed firewalls, including security from insider threats, intrusion detection, service exposure, and port scanning. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Importance And Benefits Of Distributed Firewall Management System This template helps you present information on Three stages. You can also present information on Network Address Translation, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Importance And Functions Of Firewall Network Security
Firewall Network Security Importance And Functions Of Firewall Network SecurityThis slide outlines the importance and functions performed by a firewall to protect a network. The purpose of this slide is to showcase the importance of a firewall by listing different features of it and functions performed by a firewall in a network, such as establishing a boundary, investigation, etc. Deliver an outstanding presentation on the topic using this Firewall Network Security Importance And Functions Of Firewall Network Security Dispense information and present a thorough explanation of Monitoring Network Traffic, Promotes Privacy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
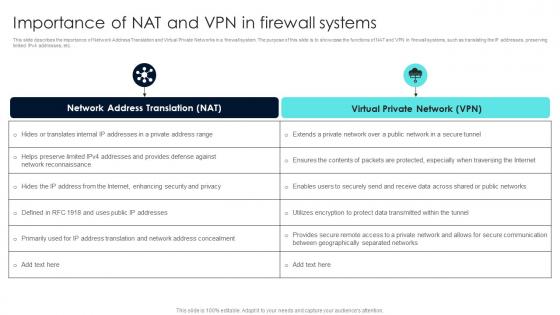 Firewall Network Security Importance Of NAT And VPN In Firewall Systems
Firewall Network Security Importance Of NAT And VPN In Firewall SystemsThis slide describes the importance of Network Address Translation and Virtual Private Networks in a firewall system. The purpose of this slide is to showcase the functions of NAT and VPN in firewall systems, such as translating the IP addresses, preserving limited IPv4 addresses, etc. Present the topic in a bit more detail with this Firewall Network Security Importance Of NAT And VPN In Firewall Systems Use it as a tool for discussion and navigation on Consistent Security, Statistical Anomaly Detection, Stateful Protocol Analysis Detection This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Importance Of Using Firewall Network Protection
Firewall Network Security Importance Of Using Firewall Network ProtectionThis slide outlines the benefits of using firewall protection in an organizational network. This slide aims to showcase some essential features of a firewall, including monitoring network traffic, promoting privacy, preventing hacks, and eliminating virus and malware attacks. Deliver an outstanding presentation on the topic using this Firewall Network Security Importance Of Using Firewall Network Protection Dispense information and present a thorough explanation of Enhance Security, IP Addresses, Malicious Content using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods
Firewall Network Security Intrusion Prevention Systems Ipss Overview And MethodsThis slide talks about the Intrusion Prevention System and its various methods for analyzing traffic. The purpose of this slide is to give an overview of Intrusion Prevention Systems and their methods, such as signature-based detection, statistical anomaly detection, and stateful protocol analysis detection. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Intrusion Prevention Systems Ipss Overview And Methods This template helps you present information on Three stages. You can also present information on Spyware Protection, Against Viruses, Prevents Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security IP Internet Protocol Reputation Function In NGFW
Firewall Network Security IP Internet Protocol Reputation Function In NGFWThis slide outlines the overview of the IP Reputation function used in Next Generation Firewalls. The purpose of this slide is to introduce the Internet Protocol IP reputation, including its features and limitations. This function blocks network traffic based on the reputation score of Ips. Introducing Firewall Network Security IP Internet Protocol Reputation Function In NGFW to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Network Visibility, Streamlined Adaptability using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Benefits Of Firewall Protection System
Firewall Network Security Key Benefits Of Firewall Protection SystemThis slide talks about the main advantages of a firewall security system. The purpose of this slide is to highlight the key benefits of a firewall for businesses, such as spyware protection, the significant barrier against viruses, protection against hacking, privacy promotion, and network traffic monitoring. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Benefits Of Firewall Protection System This template helps you present information on Five stages. You can also present information on Intelligent Protection, Traffic Filtering, Communication Protocol Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Characteristics Of Firewall As A Service FWaas
Firewall Network Security Key Characteristics Of Firewall As A Service FWaasThis slide describes the critical features of a Firewall as a Service solution. The purpose of this slide is to highlight the key characteristics of a Firewall as a Service, including streamlined policy enforcement, incremented network visibility, streamlined adaptability, and improved dependability. Introducing Firewall Network Security Key Characteristics Of Firewall As A Service FWaas to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Graphical Interface, Device Management, Scalability using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Characteristics Of Stateful Inspection Firewalls
Firewall Network Security Key Characteristics Of Stateful Inspection FirewallsThis slide represents the salient features of stateful inspection firewalls. This slide aims to highlight the critical characteristics of stateful inspection firewalls, including policy execution and enforcement, intelligent protection, traffic filtering, network monitoring, communication protocol management, etc. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Characteristics Of Stateful Inspection Firewalls This template helps you present information on Six stages. You can also present information on Advanced Authentication, Packet Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Components Of Firewall Management System
Firewall Network Security Key Components Of Firewall Management SystemThis slide talks about the important elements of the firewall management system. The purpose of this slide is to showcase the vital components of a firewall management system, such as a graphical interface, policy control, threat management, device management, third-party integrations, and scalability. Introducing Firewall Network Security Key Components Of Firewall Management System to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service, Artificial Intelligence using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Components Of Firewall Protection System
Firewall Network Security Key Components Of Firewall Protection SystemThis slide talks about the primary elements of a firewall security system. The purpose of this slide is to showcase the different components of a firewall, such as network policy, advanced authentication, packet filtering, and application gateway. Present the topic in a bit more detail with this Firewall Network Security Key Components Of Firewall Protection System Use it as a tool for discussion and navigation on Misconfiguration, Software Vulnerabilities, Missing Firewall Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Key Emerging Trends In Network Security
Firewall Network Security Key Emerging Trends In Network SecurityThis slide talks about the critical emerging trends in network security. This slide aims to highlight the emerging trends in network security, including Secure Access Service Edge, Software-defined Perimeter, Zero-trust policy, Firewall as a Service, and Artificial Intelligence and automation. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Emerging Trends In Network Security This template helps you present information on Five stages. You can also present information on OWASP Vulnerabilities, Without Negative Impact, Unknown Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Factors To Contribute Firewall Failures
Firewall Network Security Key Factors To Contribute Firewall FailuresThis slide describes the prominent causes of firewall system failures. The purpose of this slide is to showcase the four main factors that contribute the firewall failures, such as misconfiguration, software vulnerabilities, missing firewall policy, and hardware bottlenecks. Introducing Firewall Network Security Key Factors To Contribute Firewall Failures to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Protect The Firewall, Firewall Configuration Testing using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Key Features Of Web Application Firewall WAF
Firewall Network Security Key Features Of Web Application Firewall WAFThis slide represents the features of a Web Application Firewall. The purpose of this slide is to showcase the different features of WAF solution such as protection against the OWASP attacks, protection against known and unknown attacks, application vulnerability prevention, and so on. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Key Features Of Web Application Firewall WAF This template helps you present information on Five stages. You can also present information on Cisco Firepower, Bitdefender BOX using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Key Steps To Configure A Firewall System
Firewall Network Security Key Steps To Configure A Firewall SystemThis slide outlines the critical steps for firewall system configuration. The purpose of this slide is to showcase the different steps businesses can take while configuring a firewall system, such as protecting the firewall, creating firewall zones in addition to an IP address structure, setup access control lists, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Key Steps To Configure A Firewall System Dispense information and present a thorough explanation of Complexity, False Sense Of Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Leading Firewall Hardware Devices For Network Security
Firewall Network Security Leading Firewall Hardware Devices For Network SecurityThis slide outlines the various hardware firewall devices that can enhance network security. The purpose of this slide is to showcase the different hardware devices integrated firewall mechanisms, such as Cisco Firepower, Bitdefender BOX, Netgear ProSAFE, and so on. Present the topic in a bit more detail with this Firewall Network Security Leading Firewall Hardware Devices For Network Security Use it as a tool for discussion and navigation on Insider Attacks, Malware, Patching And Configuration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Limitations Of Firewall Network Security
Firewall Network Security Limitations Of Firewall Network SecurityThis slide talks about the disadvantages of firewall network security. The purpose of this slide is to showcase the different limitations of firewall security, including complexity, limited visibility, false sense of security, limited adaptability, performance impact, limited scalability, limited VPN support, and cost. Deliver an outstanding presentation on the topic using this Firewall Network Security Limitations Of Firewall Network Security Dispense information and present a thorough explanation of Techniques, Features, Security Benefits using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5G Private Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
5G Private Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with this vibrant 5G Security Network icon for PowerPoint. Featuring a bold and modern design, this icon represents the cutting-edge technology and advanced security measures of 5G networks. Perfect for showcasing the importance of secure communication in the digital age.
-
 5G Private Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
5G Private Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the cutting-edge technology of 5G Security Network. It features a sleek, modern design that conveys the strength and reliability of this advanced network. Use this icon to enhance your presentations and showcase the importance of 5G security in todays digital landscape.
-
 Ethical Hacking And Network Security Overview Of The Company
Ethical Hacking And Network Security Overview Of The CompanyThis slide describes the overview of the company including the number of countries in which services are provided, total number of certified experts, number of tools and technologies and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Overview Of The Company. This template helps you present information on four stages. You can also present information on Tools And Technologies, Subject Matter Professionals Engaged, Course Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Purpose Of Ethical Hacking
Ethical Hacking And Network Security Purpose Of Ethical HackingThis slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Introducing Ethical Hacking And Network Security Purpose Of Ethical Hacking to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Vulnerabilities To The Authorities, Security Or Protect Systems, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program
Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 ProgramThis slide depicts the reasons to pursue the certified ethical hacking program, including the number of available jobs, the average salary in US dollars, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program. This template helps you present information on three stages. You can also present information on Ethical Hacking Program, Reasons To Pursue, Certified Ethical Hacker, Baseline Certification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Roadmap For Ethical Hacking Program
Ethical Hacking And Network Security Roadmap For Ethical Hacking ProgramThis slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master. Introducing Ethical Hacking And Network Security Roadmap For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap For Ethical Hacking, Ethical Hacking Training Program, Ethical Hacking Master, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker
Ethical Hacking And Network Security Roles And Responsibilities Of Ethical HackerThis slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports, repairing the vulnerabilities of the system, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker. This template helps you present information on five stages. You can also present information on Roles And Responsibilities, Ethical Hacker, Vulnerabilities Of The System, Preventing Future Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks
Ethical Hacking And Network Security Security Measures To Prevent Phishing AttacksThis slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi-factor authentication, and so on. Introducing Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Phishing Attacks, Spam Filter, Updating Security Software Regularly, Utilization Of Multi Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool
Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking ToolThis slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy-to-use user interface, built-in compliance reports, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Solarwinds Security Event, Ethical Hacking Tool, Built In Compliance Reports using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Some Limitations Of Ethical Hacking
Ethical Hacking And Network Security Some Limitations Of Ethical HackingIntroducing Ethical Hacking And Network Security Some Limitations Of Ethical Hacking to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Resource Constraints, Restricted Methods, Ethical Hacking, Computing Power And Funding, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking
Ethical Hacking And Network Security Sql Injection Sqli Technique Of HackingThis slide depicts the SQL injection technique of hacking and how hackers can attack organizations critical information stored in databases through SQL queries. Present the topic in a bit more detail with this Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking. Use it as a tool for discussion and navigation on Injection Technique Of Hacking, Attack Organizations, Sql Injection, Credit Card Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Techniques Used In Ethical Hacking
Ethical Hacking And Network Security Techniques Used In Ethical HackingThis slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Techniques Used In Ethical Hacking. This template helps you present information on six stages. You can also present information on Techniques Of Ethical Hacking, Port Scanning, Sniffing Network Traffic, Patch Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
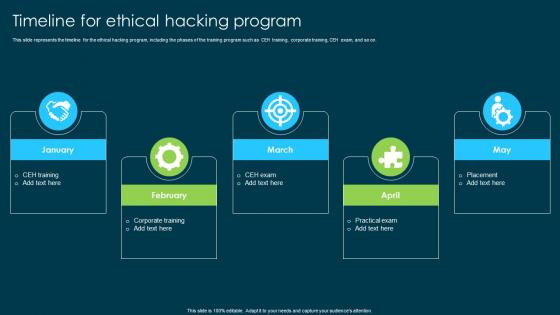 Ethical Hacking And Network Security Timeline For Ethical Hacking Program
Ethical Hacking And Network Security Timeline For Ethical Hacking ProgramThis slide represents the timeline for the ethical hacking program, including the phases of the training program such as CEH training, corporate training, CEH exam, and so on. Introducing Ethical Hacking And Network Security Timeline For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking Program, Training Program, Corporate Training, Placement, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications
Ethical Hacking And Network Security Top Ethical Hacking Courses And CertificationsThis slide depicts the top ethical hacking courses and certifications such as CEH, SANS GPEN, offensive security certified professional, Found stone ultimate hacking, and CREST. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications. Dispense information and present a thorough explanation of Offensive Security Certified Professional, Foundstone Ultimate Hacking, Certified Ethical Hacker using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program
Ethical Hacking And Network Security Traceroute Ng Ethical Hacking ProgramThis slide describes the Traceroute NG ethical hacking program, including its features such as TCP and ICMP network route analysis, txt logfile, IPv4 and IPv6 supported, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program. This template helps you present information on three stages. You can also present information on Network Route Analysis, Enables Precise Evaluation, Analyze Network Paths using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Types Of Ethical Hacking
Ethical Hacking And Network Security Types Of Ethical HackingThis slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Introducing Ethical Hacking And Network Security Types Of Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Hacking Wireless Network, Social Engineering, Web Application Hacking, System Hacking, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Types Of Phishing Attack
Ethical Hacking And Network Security Types Of Phishing AttackThis slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Types Of Phishing Attack. This template helps you present information on three stages. You can also present information on Business Email Compromise, Clone Phishing, Snowshoeing, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Do Ethical Hackers Do
Ethical Hacking And Network Security What Do Ethical Hackers DoThis slide depicts the tasks performed by ethical hackers including scope and goal setting, discovery, exploitation and documentation of the pen-test effort. Present the topic in a bit more detail with this Ethical Hacking And Network Security What Do Ethical Hackers Do. Use it as a tool for discussion and navigation on Ethical Hackers, Scope And Goal Setting, Exploitation And Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security What Is Ethical Hacking
Ethical Hacking And Network Security What Is Ethical HackingThis slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. Introducing Ethical Hacking And Network Security What Is Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Professionals, Security Flaws, Ethical Hacking, Computer System, Application, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas
Ethical Hacking And Network Security What Is Hacking Ppt Icon Format IdeasThis slide illustrates what hacking is and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas. This template helps you present information on five stages. You can also present information on Computer System Or Network, Circumvent Security, Personal Or Corporate Data, Password Cracking Technique using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Is Phishing Attack
Ethical Hacking And Network Security What Is Phishing AttackThis slide represents what phishing attacks are and how phishers hoax people through emails, SMS, phone calls, and social media platforms. Introducing Ethical Hacking And Network Security What Is Phishing Attack to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Phishers Hoax, Social Media Platforms, System Hacking, Corporate Or Personal Data, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Whats New In Cehv11
Ethical Hacking And Network Security Whats New In Cehv11This slide represents the new concepts added to the Certified Ethical Hacking program, including hacking challenges on a higher level, new attack techniques, enumeration, and others. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Whats New In Cehv11. This template helps you present information on eight stages. You can also present information on Operation Technology, Hacking Web Applications, Inverse Engineering Of Malware, Cloud Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security White Hat Or Ethical Hackers
Ethical Hacking And Network Security White Hat Or Ethical HackersThis slide represents the white hat or ethical hackers and how they test the information systems of the organizations with the techniques and methods of black hat hackers. Introducing Ethical Hacking And Network Security White Hat Or Ethical Hackers to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on White Hat Or Ethical Hackers, Malware Scans On Networks, Seek To Penetrate Information Systems, Malware Infections, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers
Ethical Hacking And Network Security Why Organizations Recruit Ethical HackersThis slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers. This template helps you present information on six stages. You can also present information on Organizations Recruit Ethical Hackers, Company Information Systems, Organization Security Posture, Network Protection Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait
Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide PortraitIntroducing our well researched set of slides titled Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Wireless Lan Network Icon For Data Security
Wireless Lan Network Icon For Data SecurityPresenting our well structured Wireless Lan Network Icon For Data Security. The topics discussed in this slide are Wireless, Data Security . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ethical Hacking And Network Security Is Ethical Hacking Legal
Ethical Hacking And Network Security Is Ethical Hacking LegalThis slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Is Ethical Hacking Legal. This template helps you present information on eight stages. You can also present information on Ethical Hacking, Computer Networks, Seek Potential Vulnerabilities, Inflict Unintended Loss using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Challenges With Traditional Network Security Approaches
SD WAN Model Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Challenges With Traditional Network Security Approaches. Dispense information and present a thorough explanation of Challenges With Traditional Network, Security Approaches, Including Disjoint Management, Workload, Slower Cloud Adoption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Traditional Networking Security Problems And Sase Solutions
SD WAN Model Traditional Networking Security Problems And Sase SolutionsThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Deliver an outstanding presentation on the topic using this SD WAN Model Traditional Networking Security Problems And Sase Solutions. Dispense information and present a thorough explanation of Traditional Networking Security Problems, On Premises Resources, Access To Cloud Resources, Network Access Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Audit For Ensuring Network Infrastructure Security
Firewall Audit For Ensuring Network Infrastructure SecurityThis slide shows reasons for implementing firewall audit in an organization. The purpose of this slide is to help security professionals in maintaining integrity and security of network infrastructure. It covers various reasons such as ensuring network security, risk management, rules optimization and access control mechanism.Introducing our premium set of slides with Firewall Audit For Ensuring Network Infrastructure Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Risk Management, Access Control Mechanism. So download instantly and tailor it with your information.
-
 Firewall Audit Icon For Network Security
Firewall Audit Icon For Network SecurityIntroducing our Firewall Audit Icon For Network Security set of slides. The topics discussed in these slides are Firewall Audit Icon, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Iot 5g Security Network Icon
Iot 5g Security Network IconPresenting our set of slides with Iot 5g Security Network Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Icon, Security.
-
 Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide
Agenda For Ethical Hacking And Network Security Ppt Icon Master SlideIntroducing Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Network Security, Ethical Hacking Training Program, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Acunetix Ethical Hacking Tool
Ethical Hacking And Network Security Acunetix Ethical Hacking ToolThis slide represents the Acunetix tool used for ethical hacking, including its features such as scalable and fast, on-premise and cloud-based structure, and rapid speed of webpage scans. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Acunetix Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Acunetix Ethical Hacking Tool, Cloud Based Structure, Web Application Security Scanner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





