Powerpoint Templates and Google slides for Securing Network
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Checklist To Enhance Cyber Security Of SCADA Networks
Checklist To Enhance Cyber Security Of SCADA NetworksThis slide represents checklist that assist IT companies to enhance their SCADA networks cyber security for improving data protection. It includes various elements such as recognizing connections, disconnecting irrelevant networks, etc. Introducing our Checklist To Enhance Cyber Security Of SCADA Networks set of slides. The topics discussed in these slides are Essential Connections, Inadvertent Disclosure, SCADA Network This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Security Gap In Network Business
Best Practices For Security Gap In Network BusinessThis slide showcases strategies for visualization security. The main purpose of this template is to showcase various methods used for visualization security. This includes establishing clear data access, prioritizing data encryption, regular security audits, etc. Presenting our set of slides with name Best Practices For Security Gap In Network Business. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prioritize Data Encryption, Regular Security Audits, Ensure Compliance.
-
 Strategies For Identifying Security Gap In Network
Strategies For Identifying Security Gap In NetworkThe following slide represents identifying tactics of gaps in security network for improving data structure. It further covers run network audit, analyse system log data and audit IT supply chain. Introducing our Strategies For Identifying Security Gap In Network set of slides. The topics discussed in these slides are Run Network Audit, Analyse System Log Data, Audit IT Supply Chain. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide
Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File GuideThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Introducing Zero Trust Architecture Traditional Perimeter Based Network Security Overview And Limitations Ppt File Guide to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Limitations, Solution, using this template. Grab it now to reap its full benefits.
-
 How Does Secure Blockchain Network Operates Ultimate Guide To Understand Role BCT SS
How Does Secure Blockchain Network Operates Ultimate Guide To Understand Role BCT SSThis slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Introducing How Does Secure Blockchain Network Operates Ultimate Guide To Understand Role BCT SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Transaction Requested, Network Of Nodes, Encryption Of Transaction, using this template. Grab it now to reap its full benefits.
-
 M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA
M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTAThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this M72 Traditional Security Models Vs Zero Trust Network Access Zero Trust Architecture ZTA. Dispense information and present a thorough explanation of Factors, Traditional Security Model, ZTNA using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Elements Of Computer Network Media Security
Key Elements Of Computer Network Media SecurityThis slide showcases major elements of network media security to minimize risk of unauthorized entry and protecting sensitive information from attackers. It involves elements such as firewalls, encryption, network segmentation etc. Introducing our premium set of slides with Key Elements Of Computer Network Media Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Prevention System, Network Segmentation, Network Access Control. So download instantly and tailor it with your information.
-
 Types Of Computer Network Security Software
Types Of Computer Network Security SoftwareThis slide covers categories of computer network security such as access control, antivirus, cloud security, firewall, and sandbox to safeguard digital assets and sensitive information by detecting, preventing, and mitigating cybersecurity threats. Introducing our premium set of slides with Types Of Computer Network Security Software. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Cloud Security, Security Software. So download instantly and tailor it with your information.
-
 Overview Of Virtual Private Network For Data Security
Overview Of Virtual Private Network For Data SecurityThis slide discusses the overview of virtual private network used for secure transfer of data through tunnelling protocols. Increase audience engagement and knowledge by dispensing information using Overview Of Virtual Private Network For Data Security. This template helps you present information on six stages. You can also present information on Public Network, Supporting Multiple Devices, Virtual Private Network, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Virtual Private Network Encryption For Security
Virtual Private Network Encryption For SecurityThis slide discusses the working process of encryption in virtual private network for secure transfer of data. Increase audience engagement and knowledge by dispensing information using Virtual Private Network Encryption For Security. This template helps you present information on ten stages. You can also present information on Data Packetization, Authentication Process, Encapsulation And Transmission using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
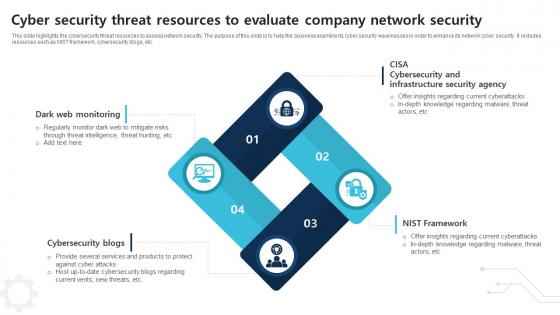 Cyber Security Threat Resources To Evaluate Company Network Security
Cyber Security Threat Resources To Evaluate Company Network SecurityThis slide highlights the cybersecurity threat resources to assess network security. The purpose of this slide is to help the business examine its cyber security weaknesses in order to enhance its network cyber security. It includes resources such as NIST framework, cybersecurity blogs, etc. Introducing our premium set of slides with Cyber Security Threat Resources To Evaluate Company Network Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Dark Web Monitoring, Cybersecurity Blogs, Nist Framework So download instantly and tailor it with your information.
-
 Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS
Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of cryptographic network protocols for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about secure connectivity, updates, etc. Increase audience engagement and knowledge by dispensing information using Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Secure Connectivity, Network Protocols Usage, Continuous Updates, Cryptographic Network Protocols using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Network Intrusion And Prevention Cyber Security Icon
Network Intrusion And Prevention Cyber Security IconPresenting our set of slides with Network Intrusion And Prevention Cyber Security Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Intrusion, Prevention Cyber Security Icon
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Security Features For Network Management
IoT Security Features For Network ManagementThis slide covers IoT security features introduced in PAN-OS 11.0 with an aim to protect connected devices and network in IoT system. Presenting our set of slides with IoT Security Features For Network Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Policy Rule, Traffic Visibility, Alto Networks.
-
 Network Security Breach Incident Report
Network Security Breach Incident ReportThe slide serves as a detailed overview, guiding the audience through the incidents context, impact, and the organizations proactive measures and future steps to address the security breach and protect customer privacy. Presenting our well structured Network Security Breach Incident Report. The topics discussed in this slide are Network Security Breach, Incident Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering
Creation Of Secure Networks Using MBSE Integrated Modelling And EngineeringThe purpose of this slide is to explain how MBSE principles can be applied to create secure networks and align with the criteria and models of information security management systems. This slide also highlights the steps involved, such as plan, do, check, and act. Present the topic in a bit more detail with this Creation Of Secure Networks Using MBSE Integrated Modelling And Engineering. Use it as a tool for discussion and navigation on Series Of Steps, Overview, Check. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Network Cyber Security Management
Enterprise Network Cyber Security ManagementFollowing slide represents cyber security management enterprise network for financial protection. It further covers network deployment, feature configuration, network security management, network monitoring and network maintenance, etc. Presenting our set of slides with Enterprise Network Cyber Security Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Deployment, Feature Configuration, Network Security Management.
-
 Network Encryption Protection Icon For Cyber Security Management
Network Encryption Protection Icon For Cyber Security ManagementPresenting our set of slides with Network Encryption Protection Icon For Cyber Security Management. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Encryption Protection Icon, Cyber Security Management.
-
 Strategies For Identifying Security Vulnerability In Network
Strategies For Identifying Security Vulnerability In NetworkFollowing slide represents identifying tactics of vulnerabilities in security network for improving data structure. It further covers run network audit, analyse system log data and audit IT supply chain. Presenting our set of slides with Strategies For Identifying Security Vulnerability In Network This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Run Network Audit, Analyse System Log Data, Audit IT Supply Chain
-
 Network SIEM Cyber Security Icon
Network SIEM Cyber Security IconIntroducing our Network SIEM Cyber Security Icon set of slides. The topics discussed in these slides are Network SIEM, Cyber Security, Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Blockchain Network Security
Best Practices For Blockchain Network SecurityThis slide discusses the best practices for blockchain network security which include comply with cyber security laws, prepare response plans, etc. Introducing our premium set of slides with Best Practices For Blockchain Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Comply Cybersecurity Laws, Rigorously Manage, Conduct Regular. So download instantly and tailor it with your information.
-
 Ai Network Security Icon Of Lock
Ai Network Security Icon Of LockPresenting our well structured Ai Network Security Icon Of Lock. The topics discussed in this slide are AI Network, Security Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Icon With Cloud Computing
Ai Network Security Icon With Cloud ComputingIntroducing our Ai Network Security Icon With Cloud Computing set of slides. The topics discussed in these slides are AI Network Security, Cloud Computing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Network Security Icon With Secure Database
Ai Network Security Icon With Secure DatabasePresenting our well structured Ai Network Security Icon With Secure Database. The topics discussed in this slide are AI Network Security, Secure Database. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Open Source Tools
Ai Network Security Open Source ToolsThis slide depicts the top trending open-source artificial interline network security tools KeePass, Open VAS, Zed attack proxy, and VeraCrypt. Introducing our Ai Network Security Open Source Tools set of slides. The topics discussed in these slides are Identifies Security Weaknesses, Proxy Interception, Unique Passwords. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Powered Network Security Threats
Ai Powered Network Security ThreatsThis slide shows the various threats faced by companies after deploying artificial intelligence in cloud computing security networks. The major threats organizations face are advanced phishing attacks, deep fake attacks, credential stuffing Presenting our set of slides with Ai Powered Network Security Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Advanced Phishing Attacks, Deepfake Attacks, Credential Stuffing .
-
 Ai Revolutionizing Network Security Systems In Organisation
Ai Revolutionizing Network Security Systems In OrganisationThis slide shows how AI benefits the organization in multiple ways. The major benefits are they provide real-time threat detection, increase automation, and behavioral analysis. Introducing our premium set of slides with Ai Revolutionizing Network Security Systems In Organisation. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Real Time Threat Detection, Email Filtering, Behavioural Analysis. So download instantly and tailor it with your information.
-
 Benefits Of Deploying Ai In Network Security
Benefits Of Deploying Ai In Network SecurityThis slide shows the major benefits of using artificial intelligence for security purposes. The major benefits are faster threat detection, improved accuracy, improved scalability and cost-saving Presenting our set of slides with Benefits Of Deploying Ai In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Faster Threat Detection, Improved Accuracy, Scalability And Cost Saving .
-
 Deploying Ai Network Security In Defence Sector
Deploying Ai Network Security In Defence SectorThis slide shows how artificial intelligence is deployed in the defense sector to build strong network security. The major reasons for deploying AI are to analyse network threats, malware detection, insider threat detection and mitigation Introducing our premium set of slides with Deploying Ai Network Security In Defence Sector. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Threat Analysis, Malware Detection, Insider Threat Detection And Mitigation. So download instantly and tailor it with your information.
-
 Future Of Artificial Intelligence In Network Security
Future Of Artificial Intelligence In Network SecurityThis slide shows the future perspective of deploying artificial intelligence in cyber security networks. It assists in multiple ways such as automating threat response, enhance encryption, and adaptive security framework. Presenting our set of slides with Future Of Artificial Intelligence In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automate Threat Response, Enhanced Encryption, Adaptive Security Framework.
-
 Malicious Uses Of Ai In Network Security
Malicious Uses Of Ai In Network SecurityThis slide shows the major activities that are malicious in natures face after deploying artificial intelligence for cyber security. The top malicious activities tracks are password cracking, defender-aware malware, data poisoning, and bots. Presenting our set of slides with Malicious Uses Of Ai In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Password Cracking, Data Poisoning And Bots, Defender Aware Malware.
-
 Top Ai Network Security Company Matrix
Top Ai Network Security Company MatrixThis slide shows the top AI cybersecurity network companies that provide safe AI algorithms. These companies are Darktrace, Cisco, Fortinet, CrowdStrike. Presenting our well structured Top Ai Network Security Company Matrix. The topics discussed in this slide are Customer Churn Rate, Palo Alto Networks, Crowdstrike. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices To Secure Blockchain Networks Using Devops
Best Practices To Secure Blockchain Networks Using DevopsThe slide highlights optimal strategies to secure blockchain networks using devOps. It cover points such as testing, automated deployment pipelines, immutable infrastructure, and patch management. Presenting our set of slides with name Best Practices To Secure Blockchain Networks Using Devops. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Patch Management, Network Security And Access Control, Immutable Infrastructure.
-
 Network Security Wire In Powerpoint And Google Slides CPP
Network Security Wire In Powerpoint And Google Slides CPPPresenting Network Security Wire In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Wire. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Mitigating Challenges Of Cyber Security On OT Network
Mitigating Challenges Of Cyber Security On OT NetworkThis slide represents various strategies that assist companies to mitigate various cyber security challenges on operational technology network effectively. It includes various challenges such as cloud and internet, IoT bots, DDoS attacks, etc. Introducing our premium set of slides with Mitigating Challenges Of Cyber Security On OT Network Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud And Internet, Ddos Attacks, Human Error And BYOD So download instantly and tailor it with your information.
-
 Introduction To Peer To Peer Network Security Revolutionizing Connectivity Exploring
Introduction To Peer To Peer Network Security Revolutionizing Connectivity ExploringThe mentioned slide gives an overview of firewalls, including their introduction, benefits, and various types. The purpose of this slide is to introduce firewalls, and their different types, such as host-based firewalls and network-based firewalls. Present the topic in a bit more detail with this Introduction To Peer To Peer Network Security Revolutionizing Connectivity Exploring Use it as a tool for discussion and navigation on Introduction, Benefits This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 NIDS Cyber Security Icon To Enhance Network Protection
NIDS Cyber Security Icon To Enhance Network ProtectionPresenting our set of slides with NIDS Cyber Security Icon To Enhance Network Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Protection, NIDS Cyber Security.
-
 Unsecured Wi Fi Network Security Risks Mobile Security
Unsecured Wi Fi Network Security Risks Mobile SecurityThis slide highlights the risks associated with unsecured Wi-Fi network which include free wi-fi risks, security threats and data exposure. Introducing Unsecured Wi Fi Network Security Risks Mobile Security to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Apps And Websites, Phishing using this template. Grab it now to reap its full benefits.
-
 Wireless Local Area Network Security Overview Wireless LAN Controller
Wireless Local Area Network Security Overview Wireless LAN ControllerThis slide is to highlight the wireless local network security such as data theft concerns, prevention measures, protection scope, etc. Increase audience engagement and knowledge by dispensing information using Wireless Local Area Network Security Overview Wireless LAN Controller. This template helps you present information on three stages. You can also present information on Theft Concerns, Preventive Measures, Protection Scope using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IOT Network Device Security Icon
IOT Network Device Security IconIntroducing our premium set of slides with name IOT Network Device Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IOT, Network Device Security. So download instantly and tailor it with your information.
-
 IOT Network Security Best Practices
IOT Network Security Best PracticesThis slide showcases best practices followed to secure IoT networks and devices. Major practices covered are managing devices, updating passwords, and using encryption protocols. Presenting our set of slides with name IOT Network Security Best Practices. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Manage Devices, Update Passwords, Use Encryption Protocols.
-
 Checklist To Optimize Security Of Wireless Lan Network
Checklist To Optimize Security Of Wireless Lan NetworkThis slide represents checklist that helps network and security teams of companies enhance wireless LAN protection efficiently. It includes various points such as preferring 802.1x authentication, conducting wireless scan, etc. Introducing our Checklist To Optimize Security Of Wireless Lan Network set of slides. The topics discussed in these slides are Checklist, Status, CommentsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 How To Build Organizational Network Security System
How To Build Organizational Network Security SystemThis slide showcases the effective guidelines for creating organizational network security system which helps them to ensure continuity of operations and protect sensitive enterprise data. It include details such as run regular audit networks,develop firewalls,etc. Introducing our premium set of slides with How To Build Organizational Network Security System. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Provide Information,Develop Firewalls,Employ Multi Factor Authentication. So download instantly and tailor it with your information.
-
 Overview Of Network Layer In Web Security Solution
Overview Of Network Layer In Web Security SolutionThis slide outlines the introduction of network layer in web security. It also includes the encompassed measures. Introducing Overview Of Network Layer In Web Security Solution to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Encompasses Safeguarding Network Infrastructure, Refers To Interconnected Devices, Involves The Establishment Of Security Policies, using this template. Grab it now to reap its full benefits.
-
 Cloud Network Security Service Partnership Architecture
Cloud Network Security Service Partnership ArchitectureThe following slide illustrates the cloud technology architecture to enhance cybersecurity that helps to protect and optimize the operations. Key components are frontend, shared services, etc. Presenting our well structured Cloud Network Security Service Partnership Architecture The topics discussed in this slide are Frontend, Shared Service, Prevents Internet AttacksThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Configuration Management Solutions In Cyber Network
Security Configuration Management Solutions In Cyber NetworkThis slide depicts the management solution for security configuration in cyber network. Its objective is to find the weak points of the company and fix them fast to safeguard them from attacks. This slide includes vulnerability assessment, remediation phase, etc. Introducing our premium set of slides with name Security Configuration Management Solutions In Cyber Network. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability, Automated Remediation, Configuration Assessment. So download instantly and tailor it with your information.
-
 Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response capabilities with our vibrant PowerPoint icon, representing the power of EDR solutions. With its eye-catching color and design, this icon is the perfect addition to your presentation on facilitating incident response trends. Grab your audiences attention and showcase the importance of EDR in handling security incidents.
-
 Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Protection Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your incident response strategy with our Monotone PowerPoint icon. This sleek and modern design represents the power of EDR solutions in facilitating efficient and effective response to security incidents. Perfect for presentations on cybersecurity and risk management, this icon will elevate your content and captivate your audience.
-
 Management Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Management Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents Mitigate EDR incidents, a cutting-edge cybersecurity technology. It is designed to help businesses prevent and respond to advanced cyber threats and attacks. With its intuitive interface and powerful features, this technology is a must-have for any organization looking to enhance their cybersecurity measures.
-
 Management Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Management Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatIntroducing the Monotone PowerPoint icon, designed specifically for Mitigate EDR incidents in cybersecurity technology. This sleek and modern icon represents the powerful capabilities of Mitigate EDR in detecting and responding to potential threats. With its minimalist design, it is the perfect addition to any cybersecurity presentation.
-
 Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS
Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SSThis slide showcases comparison of various VPN solutions available in market. Its key elements are mobile VPN, simultaneous connections, ratings, free trial and starting price Introducing Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Simultaneous Connections, Free Trial, Starting Price using this template. Grab it now to reap its full benefits.
-
 Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS
Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SSThis slide showcases the Wi-Fi security to protect network and connected devices. It includes strategies such as strong passwords, encryption, firewall and intrusion detection systems IDS and two-factor authentication 2FA.Introducing Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two Factor Authentication, Intrusion Detection Systems, Encryption, Strong Passwords, using this template. Grab it now to reap its full benefits.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Effective Network Security
Best Practices Of Effective Network SecurityThis slide displays best practices for companies to deploy network security including multi factor authentication, security awareness training, and cybersecurity risk assessment. Presenting our set of slides with name Best Practices Of Effective Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multi Factor Authentication, Security Awareness Training, Cybersecurity Risk Assessment.





