Powerpoint Templates and Google slides for Secure Sources
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
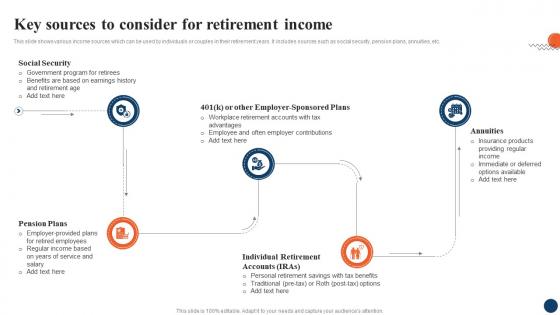 Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SS
Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SSThis slide shows various income sources which can be used by individuals or couples in their retirement years. It includes sources such as social security, pension plans, annuities, etc. Introducing Key Sources To Consider Strategic Retirement Planning To Build Secure Future Fin SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Security, Pension Plans, Annuities, using this template. Grab it now to reap its full benefits.
-
 Internal And External Sources Of Big Data In Cyber Security
Internal And External Sources Of Big Data In Cyber SecurityThis slide showcases the sources of the big data in cyber security. Its aim is to define the various sources of data internal and external. This slide includes transactions, log data, emails, social media, audio, photos, etc. Introducing our Internal And External Sources Of Big Data In Cyber Security set of slides. The topics discussed in these slides are Generate, Focused, Companies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Sources For Securing Finance In Real Estate Development
Sources For Securing Finance In Real Estate DevelopmentThis slide highlights real estate finance for development. The purpose of this slide is to assist organizations in reducing the chances of losses by allocating investments among various financial instruments. It includes sources such as equity investment, bank loan, etc. Introducing our Sources For Securing Finance In Real Estate Development set of slides. The topics discussed in these slides are Equity Investment, Private Investors. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
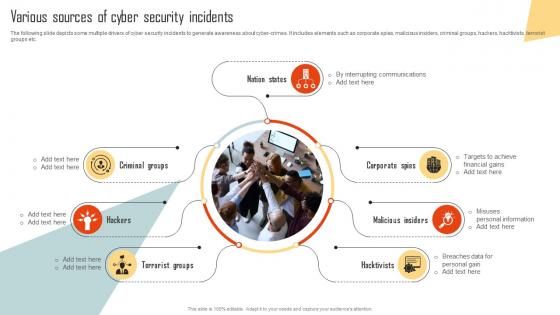 Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management
Various Sources Of Cyber Security Incidents Improving Cyber Security Risks ManagementThe following slide depicts some multiple drivers of cyber security incidents to generate awareness about cyber crimes. It includes elements such as corporate spies, malicious insiders, criminal groups, hackers, hacktivists, terrorist groups etc. Increase audience engagement and knowledge by dispensing information using Various Sources Of Cyber Security Incidents Improving Cyber Security Risks Management. This template helps you present information on seven stages. You can also present information on Criminal Groups, Terrorist Groups, Malicious Insiders, Corporate Spies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Locating Tracked Cryptocurrency Transactions Sources
Secure Your Digital Assets Locating Tracked Cryptocurrency Transactions SourcesThis Slide represents the ways we can track the transactions in the crypto market. The purpose of this slide is to locate the sources of tracked cryptocurrency transactions through transaction data and tracking various transactions. Present the topic in a bit more detail with this Secure Your Digital Assets Locating Tracked Cryptocurrency Transactions Sources. Use it as a tool for discussion and navigation on Crypto Market, Tracked Cryptocurrency Transactions, Data And Tracking Various Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Open Source Software Firewall Solutions
Firewall Network Security Open Source Software Firewall SolutionsThis slide highlights the different open source firewall options, including their features and providers. The purpose of this slide is to showcase the open source software firewall solutions, including iptables, pfSense, OPNsense, Shorewall, VyOS, Smoothwall, IPFire, and Untangle. Present the topic in a bit more detail with this Firewall Network Security Open Source Software Firewall Solutions Use it as a tool for discussion and navigation on Packet Filtering, DPI, Example This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Open Source Cloud Security Audit Tools
Comparative Analysis Of Open Source Cloud Security Audit ToolsThis slide showcases open source cloud security audit tools comparison to improve organizational position such as. Introducing our Comparative Analysis Of Open Source Cloud Security Audit Tools set of slides. The topics discussed in these slides are Comparative Analysis, Cloud Security Audit Tools, Audit Tools Comparison, Organizational Position. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Top Open Source Tools Among Security Testers
Top Open Source Tools Among Security TestersThis slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc. Increase audience engagement and knowledge by dispensing information using Top Open Source Tools Among Security Testers. This template helps you present information on four stages. You can also present information on Proof Based Scanning Technology, AI Enabled Penetration Testing, Flexible And Scalable Scanning using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Securing Food Safety In Online Ingredient Sourcing And Inspection To Deliver Quality
Securing Food Safety In Online Ingredient Sourcing And Inspection To Deliver QualityThis slide covers strategies to source ingredients effectively such as selecting right suppliers, integrating menu planning software and partnering with farmers. Introducing Securing Food Safety In Online Ingredient Sourcing And Inspection To Deliver Quality to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Select Right Suppliers, Integrate Menu Planning Tools, Involve Seasonal Menu Planning, using this template. Grab it now to reap its full benefits.
-
 Ai Network Security Open Source Tools
Ai Network Security Open Source ToolsThis slide depicts the top trending open-source artificial interline network security tools KeePass, Open VAS, Zed attack proxy, and VeraCrypt. Introducing our Ai Network Security Open Source Tools set of slides. The topics discussed in these slides are Identifies Security Weaknesses, Proxy Interception, Unique Passwords. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security information and event management siem logging sources
Security information and event management siem logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Security Information And Event Management SIEM Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing internal and external sources of threat data corporate security management
Addressing internal and external sources of threat data corporate security managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Introducing Addressing Internal And External Sources Of Threat Data Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Targeted Intelligence, Malware Intelligence, Reputation Intelligence, using this template. Grab it now to reap its full benefits.
-
 Real time analysis of security alerts logging sources
Real time analysis of security alerts logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Real Time Analysis Of Security Alerts Logging Sources. This template helps you present information on four stages. You can also present information on Siem Logging Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing internal and external sources data cyber security risk management
Addressing internal and external sources data cyber security risk managementThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Data Cyber Security Risk Management. Dispense information and present a thorough explanation of Internal Sources, External Sources, Targeted Intelligence, Malware Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability management logging sources
Improve it security with vulnerability management logging sourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Increase audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management Logging Sources. This template helps you present information on four stages. You can also present information on Security Devices, Network Devices, Servers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem For Security Analysis Logging Sources
Siem For Security Analysis Logging SourcesThis slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Introducing Siem For Security Analysis Logging Sources to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Siem Logging Sources, using this template. Grab it now to reap its full benefits.
-
 Common Sources Of Precursors And Indicators Implementing Cyber Security Ppt Inspiration
Common Sources Of Precursors And Indicators Implementing Cyber Security Ppt InspirationThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Deliver an outstanding presentation on the topic using this Common Sources Of Precursors And Indicators Implementing Cyber Security Ppt Inspiration. Dispense information and present a thorough explanation of Common Sources, Precursors And Indicators, Analytics using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Common Sources Of Precursors And Indicators Development And Implementation Of Security
Common Sources Of Precursors And Indicators Development And Implementation Of SecurityThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Present the topic in a bit more detail with this Common Sources Of Precursors And Indicators Development And Implementation Of Security. Use it as a tool for discussion and navigation on Identification And Recording, Suspicious Data, Uses Attack Signatures, Identify Malicious Activity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators
Cyber Security Attacks Response Plan Common Sources Of Precursors And IndicatorsThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators. Use it as a tool for discussion and navigation on Precursors And Indicators, Suspicious Data, Identify Malicious Activity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management
Common Sources Of Precursors And Indicators Deploying Computer Security Incident ManagementThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc.Present the topic in a bit more detail with this Common Sources Of Precursors And Indicators Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Antivirus Software, Based Guarantee, Operating System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SS
Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Present the topic in a bit more detail with this Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Potential, Cyberattack, Sources . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Billing customer security e source control circular process with icon in centre
Billing customer security e source control circular process with icon in centrePresenting billing customer security e source control circular process with icon in centre. This is a billing customer security e source control circular process with icon in centre. This is a seven stage process. The stages in this process are billing process, billing procedure, billing cycle.
-
 Global security cross reference manual sources logical view
Global security cross reference manual sources logical viewPresenting this set of slides with name - Global Security Cross Reference Manual Sources Logical View. This is an editable three stages graphic that deals with topics like -to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Sales force analysis social security crisis sourcing procurement cpb
Sales force analysis social security crisis sourcing procurement cpbThis is an editable three stages graphic that deals with topics like Sales Force Analysis Social Security Crisis Sourcing Procurement to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Sources threat intelligenc security teams ppt powerpoint presentation portfolio clipart cpb
Sources threat intelligenc security teams ppt powerpoint presentation portfolio clipart cpbPresenting this set of slides with name Sources Threat Intelligenc Security Teams Ppt Powerpoint Presentation Portfolio Clipart Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Sources Threat Intelligenc Security Teams to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Application source code security ppt powerpoint presentation ideas deck cpb
Application source code security ppt powerpoint presentation ideas deck cpbPresenting this set of slides with name Application Source Code Security Ppt Powerpoint Presentation Ideas Deck Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Application Source Code Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Open source cloud security tools ppt powerpoint presentation portfolio examples cpb
Open source cloud security tools ppt powerpoint presentation portfolio examples cpbPresenting this set of slides with name Open Source Cloud Security Tools Ppt Powerpoint Presentation Portfolio Examples Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Open Source Cloud Security Tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Open source security technology ppt powerpoint presentation model graphics download cpb
Open source security technology ppt powerpoint presentation model graphics download cpbPresenting Open Source Security Technology Ppt Powerpoint Presentation Model Graphics Download Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Open Source Security Technology. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Open source application security ppt powerpoint presentation professional graphics download cpb
Open source application security ppt powerpoint presentation professional graphics download cpbPresenting our Open Source Application Security Ppt Powerpoint Presentation Professional Graphics Download Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Open Source Application Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Open source security testing practices ppt powerpoint presentation infographics information cpb
Open source security testing practices ppt powerpoint presentation infographics information cpbPresenting Open Source Security Testing Practices Ppt Powerpoint Presentation Infographics Information Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Open Source Security Testing Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Hybrid cloud securing data stored from multiple source icon
Hybrid cloud securing data stored from multiple source iconPresenting our set of slides with Hybrid Cloud Securing Data Stored From Multiple Source Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hybrid Cloud Securing Data Stored From Multiple Source Icon.



