Powerpoint Templates and Google slides for Secure Endpoints
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Endpoint Security Upgradation Proposal Our Proposed Endpoint
Endpoint Security Upgradation Proposal Our Proposed EndpointThis slide represents the proposed endpoint security for the organizations upgradation proposal, including its workstation and building management system. Introducing Endpoint Security Upgradation Proposal Our Proposed Endpoint to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Cylance Services, Saas Application, Active Directory, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Upgradation Proposal Project Context For Modern
Endpoint Security Upgradation Proposal Project Context For ModernThis slide highlights the project context for the endpoint security proposal which includes the requirements and the key deliverables by the service provider. Present the topic in a bit more detail with this Endpoint Security Upgradation Proposal Project Context For Modern. Use it as a tool for discussion and navigation on Scalability And Performance, Security Measures, Centralized Management System, Flexibility And Adaptability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Upgradation Proposal Proposed Endpoint Security
Endpoint Security Upgradation Proposal Proposed Endpoint SecurityThis slide represents the proposed network architecture for the end point upgradation proposal, including its workstation and building management system. Present the topic in a bit more detail with this Endpoint Security Upgradation Proposal Proposed Endpoint Security. Use it as a tool for discussion and navigation on Endpoint Protection, Management Platform, Automation And Orchestration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Upgradation Proposal Why Replacing Traditional
Endpoint Security Upgradation Proposal Why Replacing TraditionalThis slide gives an overview of why organizations need to replace their traditional endpoint security with modern endpoint security. Introducing Endpoint Security Upgradation Proposal Why Replacing Traditional to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Threat Detection, Adaptability, Centralized Cloud-Based Management, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Endpoint Security Upgradation Proposal
Icons Slide For Endpoint Security Upgradation ProposalIntroducing our well researched set of slides titled Icons Slide For Endpoint Security Upgradation Proposal. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Next Steps For Endpoint Security Upgradation Proposal
Next Steps For Endpoint Security Upgradation ProposalThis slide covers the next step after the proposal has been accepted. It highlights the various terms that should be followed to lay a solid foundation for collaboration. Introducing Next Steps For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Discuss Requirements And Changes, Acceptance Of Proposal, Finalization Of Proposal Signature From Parties, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Endpoint Security Upgradation Proposal
Table Of Contents For Endpoint Security Upgradation ProposalIntroducing Table Of Contents For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Pricing, Next Step, Terms And Conditions, Client Testimonials, using this template. Grab it now to reap its full benefits.
-
 Terms And Conditions For Endpoint Security Upgradation Proposal
Terms And Conditions For Endpoint Security Upgradation ProposalThis slide illustrates terms and conditions based on which the organization will sign a contract with the agreement party which covers service and payment, etc. Introducing Terms And Conditions For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Service And Payments, Contract Cancellation, Notice And Renewal, Liability, using this template. Grab it now to reap its full benefits.
-
 Timeline For Endpoint Security Upgradation Proposal
Timeline For Endpoint Security Upgradation ProposalThis slide shows the time framework for upgrading the endpoint security proposal the steps include identifying requirements, developing architecture design, etc. Introducing Timeline For Endpoint Security Upgradation Proposal to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Requirements Analysis, Developing Architecture Design, Creating Budget, Deployment, using this template. Grab it now to reap its full benefits.
-
 Addressing Current Challenges In Unified Endpoint Security
Addressing Current Challenges In Unified Endpoint SecurityThis slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Present the topic in a bit more detail with this Addressing Current Challenges In Unified Endpoint Security. Use it as a tool for discussion and navigation on Sensitive Corporate, Misplacing Device, Records Exposed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tracking Mobile Device Activities At Workplace Unified Endpoint Security
Tracking Mobile Device Activities At Workplace Unified Endpoint SecurityThis slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Present the topic in a bit more detail with this Tracking Mobile Device Activities At Workplace Unified Endpoint Security. Use it as a tool for discussion and navigation on Compromised, Ownership, Passcode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Current Scenario Of Unified Endpoint Security
Determine Current Scenario Of Unified Endpoint SecurityThis slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. Present the topic in a bit more detail with this Determine Current Scenario Of Unified Endpoint Security. Use it as a tool for discussion and navigation on Determine Frequency, Employees Consider, Employee Consider. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Standard Mobile Device Management Components Unified Endpoint Security
Determine Standard Mobile Device Management Components Unified Endpoint SecurityThis slide provides information regarding essential standard mobile device management components terms of central management console, registry.Increase audience engagement and knowledge by dispensing information using Determine Standard Mobile Device Management Components Unified Endpoint Security. This template helps you present information on two stages. You can also present information on Components Comprise, Devices Workplace, Provide Performance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security
Ensuring Checklist For Mobile Security Deployment Unified Endpoint SecurityThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Introducing Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Password Protection, Automatic Configuration, Patches Management, using this template. Grab it now to reap its full benefits.
-
 Key Features Associated To Mobile Device Management Unified Endpoint Security
Key Features Associated To Mobile Device Management Unified Endpoint SecurityThis slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. Introducing Key Features Associated To Mobile Device Management Unified Endpoint Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Device Enrolment, Profile Management, Device Management, using this template. Grab it now to reap its full benefits.
-
 Endpoint protection vs endpoint security ppt powerpoint presentation clipart cpb
Endpoint protection vs endpoint security ppt powerpoint presentation clipart cpbPresenting Endpoint Protection Vs Endpoint Security Ppt Powerpoint Presentation Clipart Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Endpoint Protection Vs Endpoint Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Types endpoint security ppt powerpoint presentation layouts templates cpb
Types endpoint security ppt powerpoint presentation layouts templates cpbPresenting Types Endpoint Security Ppt Powerpoint Presentation Layouts Templates Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Types Endpoint Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Endpoint security tools ppt powerpoint presentation gallery maker cpb
Endpoint security tools ppt powerpoint presentation gallery maker cpbPresenting Endpoint Security Tools Ppt Powerpoint Presentation Gallery Maker Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Endpoint Security Tools. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Endpoint security antivirus ppt powerpoint presentation summary sample cpb
Endpoint security antivirus ppt powerpoint presentation summary sample cpbPresenting our Endpoint Security Antivirus Ppt Powerpoint Presentation Summary Sample Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Endpoint Security Antivirus This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Endpoint security controls checklist ppt powerpoint presentation infographic template cpb
Endpoint security controls checklist ppt powerpoint presentation infographic template cpbPresenting our Endpoint Security Controls Checklist Ppt Powerpoint Presentation Infographic Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Endpoint Security Controls Checklist This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Endpoint Security Antivirus Ppt Powerpoint Presentation Infographics Graphics Download Cpb
Endpoint Security Antivirus Ppt Powerpoint Presentation Infographics Graphics Download CpbPresenting Endpoint Security Antivirus Ppt Powerpoint Presentation Infographics Graphics Download Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Endpoint Security Antivirus. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network endpoint security ppt powerpoint presentation layouts graphics tutorials cpb
Network endpoint security ppt powerpoint presentation layouts graphics tutorials cpbPresenting our Network Endpoint Security Ppt Powerpoint Presentation Layouts Graphics Tutorials Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Network Endpoint Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Difference Between Antivirus Endpoint Security Ppt Powerpoint Presentation Inspiration Slide Download Cpb
Difference Between Antivirus Endpoint Security Ppt Powerpoint Presentation Inspiration Slide Download CpbPresenting our Difference Between Antivirus Endpoint Security Ppt Powerpoint Presentation Inspiration Slide Download Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Difference Between Antivirus Endpoint Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
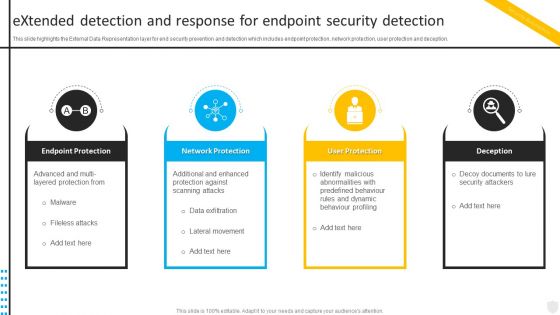 Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats
Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Introducing Extended Detection And Response For Endpoint Security Automation To Investigate And Remediate Cyberthreats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Protection, Network Protection, User Protection, using this template. Grab it now to reap its full benefits.
-
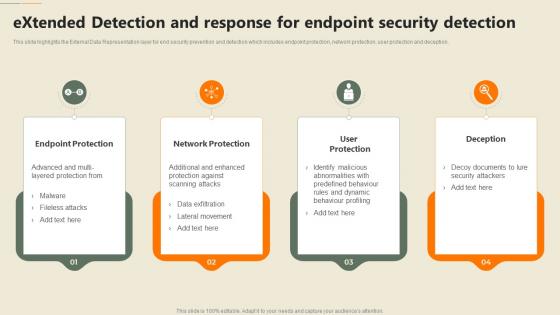 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Mobile Device Management Approach Unified Endpoint Security
Addressing Mobile Device Management Approach Unified Endpoint SecurityThis slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Introducing Addressing Mobile Device Management Approach Unified Endpoint Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Management Information, Critical Information, Ensuring Corporate, using this template. Grab it now to reap its full benefits.
-
 Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security
Addressing Mobile Device Management Model For Enterprise Unified Endpoint SecurityThis slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement. Increase audience engagement and knowledge by dispensing information using Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security. This template helps you present information on four stages. You can also present information on Equipment Personal, Devices Professional, Employees Personal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Staff Training Schedule With Cost Unified Endpoint Security
Addressing Staff Training Schedule With Cost Unified Endpoint SecurityThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Introducing Addressing Staff Training Schedule With Cost Unified Endpoint Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Software, Fundamentals Information, Threat Vulnerability, using this template. Grab it now to reap its full benefits.
-
 Addressing Timeframe For Incident Management At Mobile Device Unified Endpoint Security
Addressing Timeframe For Incident Management At Mobile Device Unified Endpoint SecurityThis slide provides information regarding entire duration of incident handling process which occur in various phases.Increase audience engagement and knowledge by dispensing information using Addressing Timeframe For Incident Management At Mobile Device Unified Endpoint Security. This template helps you present information on one stage. You can also present information on Incident Categorization, Incident Prioritization, Incident Resolution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyzing Budget For Effective Mobile Device Management Unified Endpoint Security
Analyzing Budget For Effective Mobile Device Management Unified Endpoint SecurityFirm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Analyzing Budget For Effective Mobile Device Management Unified Endpoint Security. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Information Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 B15 Table Of Contents For Unified Endpoint Security Management
B15 Table Of Contents For Unified Endpoint Security ManagementIntroducing B15 Table Of Contents For Unified Endpoint Security Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Current Scenario, Determine Current, Determine Various, using this template. Grab it now to reap its full benefits.
-
 Determine Incident Reporting By Mobile Devices In Different Unified Endpoint Security
Determine Incident Reporting By Mobile Devices In Different Unified Endpoint SecurityThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Present the topic in a bit more detail with this Determine Incident Reporting By Mobile Devices In Different Unified Endpoint Security. Use it as a tool for discussion and navigation on Person Involved, Average Cost, Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Mobile Device Maintenance Checklist Unified Endpoint Security
Determine Mobile Device Maintenance Checklist Unified Endpoint SecurityThis slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Introducing Determine Mobile Device Maintenance Checklist Unified Endpoint Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Preventive Maintenance, Virus Scanning, Executive Reporting, using this template. Grab it now to reap its full benefits.
-
 Determine Various Configuration Profiles Using MDM Technology Unified Endpoint Security
Determine Various Configuration Profiles Using MDM Technology Unified Endpoint SecurityThis slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Present the topic in a bit more detail with this Determine Various Configuration Profiles Using MDM Technology Unified Endpoint Security. Use it as a tool for discussion and navigation on Internet Settings, Processes Configuration, Profile Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Various Mobile Device Management Unified Endpoint Security
Determine Various Mobile Device Management Unified Endpoint SecurityThis slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Deliver an outstanding presentation on the topic using this Determine Various Mobile Device Management Unified Endpoint Security. Dispense information and present a thorough explanation of Security Requirement, Incidents Damaging, Security Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Various Unified Endpoint Security Unified Endpoint Security
Determine Various Unified Endpoint Security Unified Endpoint SecurityThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Present the topic in a bit more detail with this Determine Various Unified Endpoint Security Unified Endpoint Security. Use it as a tool for discussion and navigation on Allowed Employees, Devices Personal, Notebook Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining Roles And Responsibilities For Risk Handling Unified Endpoint Security
Determining Roles And Responsibilities For Risk Handling Unified Endpoint SecurityThis slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Introducing Determining Roles And Responsibilities For Risk Handling Unified Endpoint Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Chief Information, Executive Management, Development Implementation, using this template. Grab it now to reap its full benefits.
-
 Effective Mobile Device Security Management Unified Endpoint Security
Effective Mobile Device Security Management Unified Endpoint SecurityThis slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Present the topic in a bit more detail with this Effective Mobile Device Security Management Unified Endpoint Security. Use it as a tool for discussion and navigation on Security Requirement, Rights Authorized, Actual Access . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Mobile Device Compliance And Policy Enforcement Unified Endpoint Security
Ensuring Mobile Device Compliance And Policy Enforcement Unified Endpoint SecurityThis slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Increase audience engagement and knowledge by dispensing information using Ensuring Mobile Device Compliance And Policy Enforcement Unified Endpoint Security. This template helps you present information on three stages. You can also present information on Enforcement Automation, Dynamic Workflows, Device Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slides For Unified Endpoint Security Management
Icons Slides For Unified Endpoint Security ManagementPresenting our premium Icons Slides For Unified Endpoint Security Management set of slides with flexible icons. The icons are designed by our group of professionals. Add these Icons Slides For Unified Endpoint Security Management to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Implementing Mobile Device Security Framework Roadmap Unified Endpoint Security
Implementing Mobile Device Security Framework Roadmap Unified Endpoint SecurityThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an outstanding presentation on the topic using this Implementing Mobile Device Security Framework Roadmap Unified Endpoint Security. Dispense information and present a thorough explanation of Control Environment, Security Processes, Security Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Steps Involved In Mobile Device Management Deployment Unified Endpoint Security
Key Steps Involved In Mobile Device Management Deployment Unified Endpoint SecurityThis slide provides information regarding key steps involved in deploying mobile device management system. Increase audience engagement and knowledge by dispensing information using Key Steps Involved In Mobile Device Management Deployment Unified Endpoint Security. This template helps you present information on five stages. You can also present information on Profile Configuration, Device Enrollment, Successful Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Management Action Plan Unified Endpoint Security
Mobile Device Management Action Plan Unified Endpoint SecurityThe risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Deliver an outstanding presentation on the topic using this Mobile Device Management Action Plan Unified Endpoint Security. Dispense information and present a thorough explanation of Compliance Obligations, Develop Implement, Implement Receivables using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Device Management Assistance To Employees Unified Endpoint Security
Mobile Device Management Assistance To Employees Unified Endpoint SecurityThis slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Introducing Mobile Device Management Assistance To Employees Unified Endpoint Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Rendering Appropriate, Processes Automation, Enforce Security, using this template. Grab it now to reap its full benefits.
-
 Mobile Device Management For Android Platform Unified Endpoint Security
Mobile Device Management For Android Platform Unified Endpoint SecurityThe risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Present the topic in a bit more detail with this Mobile Device Management For Android Platform Unified Endpoint Security. Use it as a tool for discussion and navigation on Device Security, Remote Management, Mandatary Installed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Device Management For Ios Platform Unified Endpoint Security
Mobile Device Management For Ios Platform Unified Endpoint SecurityThis slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Deliver an outstanding presentation on the topic using this Mobile Device Management For Ios Platform Unified Endpoint Security. Dispense information and present a thorough explanation of Enrollment Program, Removal Automatic, Installing Prohibited using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Selecting Suitable Mobile Device Management Solutions Unified Endpoint Security
Selecting Suitable Mobile Device Management Solutions Unified Endpoint SecurityThis slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Deliver an outstanding presentation on the topic using this Selecting Suitable Mobile Device Management Solutions Unified Endpoint Security. Dispense information and present a thorough explanation of Experience Management, Geofencing, Platforms Supported using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Unified Endpoint Security Management
Table Of Contents For Unified Endpoint Security ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Unified Endpoint Security Management. This template helps you present information on one stage. You can also present information on Device Management, Policy Enforcement, Management Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
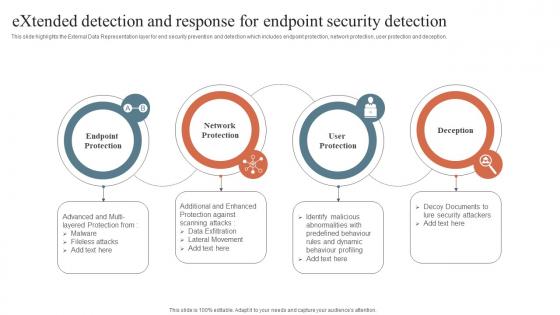 Security Orchestration Automation Extended Detection And Response For Endpoint Security Detection
Security Orchestration Automation Extended Detection And Response For Endpoint Security DetectionThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Introducing Security Orchestration Automation Extended Detection And Response For Endpoint Security Detection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Protection, Endpoint Protection, User Protection, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SS
Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SSThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems.Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security Implementation Of ICT Strategic Plan Strategy SS. This template helps you present information on three stages. You can also present information on Such Business, Operating System, Frequent Basis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 CASB As A Streamline Endpoint Protection Solution Cloud Access Security Broker CASB
CASB As A Streamline Endpoint Protection Solution Cloud Access Security Broker CASBThis slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Deliver an outstanding presentation on the topic using this CASB As A Streamline Endpoint Protection Solution Cloud Access Security Broker CASB. Dispense information and present a thorough explanation of Cloud Apps, Endpoint Manager, Roaming Users using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS V
Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Best Practices For Effective Endpoint Security ICT Strategic Framework Strategy SS V. This template helps you present information on three stages. You can also present information on Educate Users, Find And Track Devices, Installation And Maintenance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business endpoint security ppt powerpoint presentation pictures example introduction cpb
Business endpoint security ppt powerpoint presentation pictures example introduction cpbPresenting this set of slides with name - Business Endpoint Security Ppt Powerpoint Presentation Pictures Example Introduction Cpb. This is an editable five stages graphic that deals with topics like Business Endpoint Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Endpoint security platform ppt powerpoint presentation portfolio gallery cpb
Endpoint security platform ppt powerpoint presentation portfolio gallery cpbPresenting this set of slides with name Endpoint Security Platform Ppt Powerpoint Presentation Portfolio Gallery Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Endpoint Security Platform to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Elements endpoint security ppt powerpoint presentation layouts layout ideas cpb
Elements endpoint security ppt powerpoint presentation layouts layout ideas cpbPresenting this set of slides with name Elements Endpoint Security Ppt Powerpoint Presentation Layouts Layout Ideas Cpb. This is an editable Powerpoint nine stages graphic that deals with topics like Elements Endpoint Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Endpoint security threats ppt powerpoint presentation pictures templates cpb
Endpoint security threats ppt powerpoint presentation pictures templates cpbPresenting this set of slides with name Endpoint Security Threats Ppt Powerpoint Presentation Pictures Templates Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Endpoint Security Threats to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Difference endpoint network security ppt powerpoint presentation inspiration clipart cpb
Difference endpoint network security ppt powerpoint presentation inspiration clipart cpbPresenting this set of slides with name Difference Endpoint Network Security Ppt Powerpoint Presentation Inspiration Clipart Cpb. This is an editable Powerpoint eight stages graphic that deals with topics like Difference Endpoint Network Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Endpoint security platform ppt powerpoint presentation inspiration samples cpb
Endpoint security platform ppt powerpoint presentation inspiration samples cpbPresenting this set of slides with name Endpoint Security Platform Ppt Powerpoint Presentation Inspiration Samples Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Endpoint Security Platform to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Endpoint security management ppt powerpoint presentation model example cpb
Endpoint security management ppt powerpoint presentation model example cpbPresenting this set of slides with name Endpoint Security Management Ppt Powerpoint Presentation Model Example Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Endpoint Security Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





